当前位置:网站首页>[PHP features - variable coverage] improper use, improper configuration and code logic vulnerability of the function
[PHP features - variable coverage] improper use, improper configuration and code logic vulnerability of the function
2022-07-05 03:47:00 【Black zone (rise)】
Catalog
3、 ... and 、parse_str function
Four 、import_request_variables function
5、 ... and 、 Improper configuration
6、 ... and 、 Code logic vulnerability
$$ The resulting variable overrides
One 、 executive summary
Find the way :
Code audit
The reasons causing :
Improper use of functions 、 Improper configuration 、 Code logic vulnerability
utilize :
Overwrite local variables or global variables in the program through the value passed in from the front end , So as to achieve variable coverage
Use scenarios :
$$ Improper use
extract() 、parse_str() Improper use of functions
import_request_variables() Improper use , Global variable registration is enabled (PHP 4 >= 4.1.0, PHP 5 < 5.4.0)
……
Two 、extract function
grammar :
extract(array,extract_rules,prefix)
Parameters describe array It's necessary . Specify the array to use . extract_rules Optional .extract() The function checks that each key name is a valid variable name , It also checks whether it conflicts with the existing variable names in the symbol table . Handling illegal and conflicting key names will be determined by this parameter .
Possible value :
- EXTR_OVERWRITE - Default . If there is a conflict , Overwrite existing variables .
- EXTR_SKIP - If there is a conflict , Do not overwrite existing variables .
- EXTR_PREFIX_SAME - If there is a conflict , Prefix variable names prefix.
- EXTR_PREFIX_ALL - Prefix all variable names prefix.
- EXTR_PREFIX_INVALID - Prefix only illegal or numeric variable names prefix.
- EXTR_IF_EXISTS - Only when a variable with the same name already exists in the current symbol table , Override their values . Nothing else .
- EXTR_PREFIX_IF_EXISTS - Only when a variable with the same name already exists in the current symbol table , Create variable names with prefixes attached , Nothing else .
- EXTR_REFS - Extract variables as references . The imported variable still references the value of the array parameter .
prefix Optional . Please note that prefix Only in extract_type The value of is EXTR_PREFIX_SAME,EXTR_PREFIX_ALL,EXTR_PREFIX_INVALID or EXTR_PREFIX_IF_EXISTS The need when . If the result after prefixing is not a legal variable name , Will not be imported into the symbol table .
An underscore is automatically added between the prefix and the array key name .
Example :
<?php
$a = false;
extract($_GET);
if ($a) {
echo "flag{...}";
} else {
echo "……";
}
?>extract Function will GET The incoming data is converted into variable name and value
Input ?a=1 Can be $a The value of a true-----> get flag
3、 ... and 、parse_str function
grammar :
parse_str(string,array)
Parameters describe string It's necessary . Specify the string to parse . array Optional . Specifies the name of the array where the variables are stored . This parameter indicates that the variable will be stored in the array . Not set array Parameters , The variable set by this function will overwrite the existing variable with the same name
parse_str The() function parses a string and registers it as a variable
The existence of the current variable will not be verified before registering the variable , Directly overwrite the existing variables
That is to change the input string into a variable
Example :
<?php
$a = false;
parse_str($_SERVER['QUERY_STRING']);
if ($a) {
echo "flag{...}";
} else {
echo "……";
}
?>Input ?a=1
Four 、import_request_variables function
grammar :
bool import_request_variables ( string $types [, string $prefix ] )
Parameters describe $types Specify the variables to import , It can be used Letter G、P and C respectively GET、POST and Cookie, These letters are case insensitive , So you can use g 、 p and c Any combination of .POST It includes passing through POST Method to upload file information . Notice the order of the letters , When using gp when ,POST Variables will be overridden with the same name GET Variable . whatever GPC Letters other than will be ignored $prefix Prefix of variable name , Before all variables that are imported into the global scope . So if you have one called userid Of GET Variable , It also provides pref_ As a prefix , Then you will get a name $pref_userid Global variable of . although prefix Parameters are optional , But if you don't specify a prefix , Or specify an empty string as the prefix , You will get a E_NOTICE Level error PHP 4 >= 4.1.0, PHP 5 < 5.4.0
Example :
<?php
$a = false;
import_request_variables('G');
if ($a) {
echo "flag{...}";
} else {
echo "……";
}
?>The first character will overwrite the value of the parameter passed in by the last character , if “GP”, And GET and POST It's also passed in a Parameters , be POST Incoming a Will be ignored
5、 ... and 、 Improper configuration
Premise :
When PHP To configure register_globals=ON when , utilize register_globals Characteristics of , Duplicate global variable coverage vulnerability
Example :
<?php
if ($a) {
echo "flag{...}";
} else {
echo "……";
}
?>Parameters passed in by the user auth=1 You can enter if Sentence block
If in if Initialization before statement $a Variable , It won't trigger
6、 ... and 、 Code logic vulnerability
$$ The resulting variable overrides
$$( Volatile variables )
The variable name of a variable can be set and used dynamically
This variable gets the value of a common variable as the variable name of this variable
<?php
$a="hello";// assignment
$$a="everybody";
// send a The value of the variable is used as the variable name
echo "$a ${$a}";
// Output :hello everybody
echo "$a $hello";
// The same output :hello everybody
?>Example :
<?php
$a = false;
foreach($_GET as $key => $value){
$$key = $value;
}
if ($a) {
echo "flag{...}";
} else {
echo "……";
}
?>adopt foreach Loop through groups ( Such as ,$_GET、$_POST etc. ), There will be GET The passed in parameters are registered as variables , User input “?auth=1” Successfully bypassed the judgment , To obtain the flag
边栏推荐
- Solve the problem that sqlyog does not have a schema Designer
- DMX parameter exploration of grandma2 onpc 3.1.2.5
- Multimedia query
- Kubernetes - identity and authority authentication
- glibc strlen 实现方式分析
- Learning notes of raspberry pie 4B - IO communication (I2C)
- UE4 DMX和grandMA2 onPC 3.1.2.5的操作流程
- When sqlacodegen generates a model, how to solve the problem that the password contains special characters?
- How to learn to get the embedding matrix e # yyds dry goods inventory #
- [software reverse analysis tool] disassembly and decompilation tool
猜你喜欢
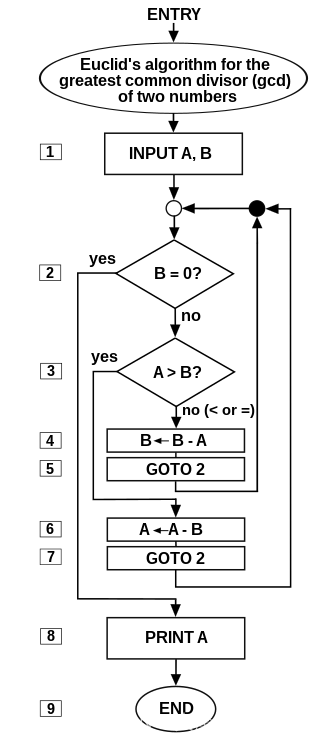
An elegant program for Euclid‘s algorithm
Easy processing of ten-year futures and stock market data -- Application of tdengine in Tongxinyuan fund
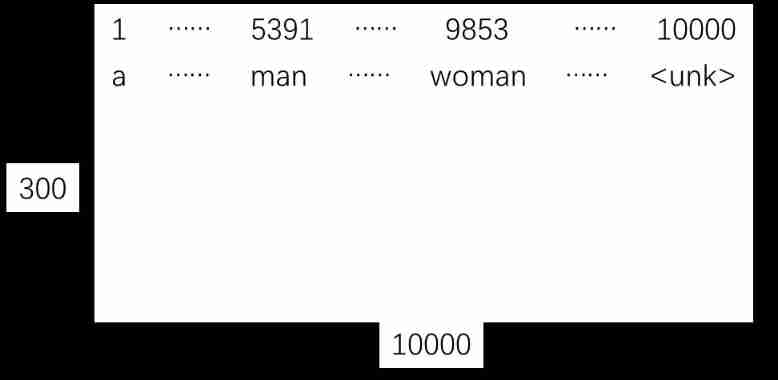
Yyds dry goods inventory embedded matrix
![[wp]bmzclub几道题的writeup](/img/15/2838b93a605b09d3e2996f6067775c.png)
[wp]bmzclub几道题的writeup
![Quick start of UI component development of phantom engine [umg/slate]](/img/8b/cee092ec1ab105a7e234143bd56861.jpg)
Quick start of UI component development of phantom engine [umg/slate]
![[positioning in JS]](/img/f1/02ce74fadc1f7524c7abca9db66c71.jpg)
[positioning in JS]

An elegant program for Euclid‘s algorithm
Some enterprise interview questions of unity interview
Operation flow of UE4 DMX and grandma2 onpc 3.1.2.5
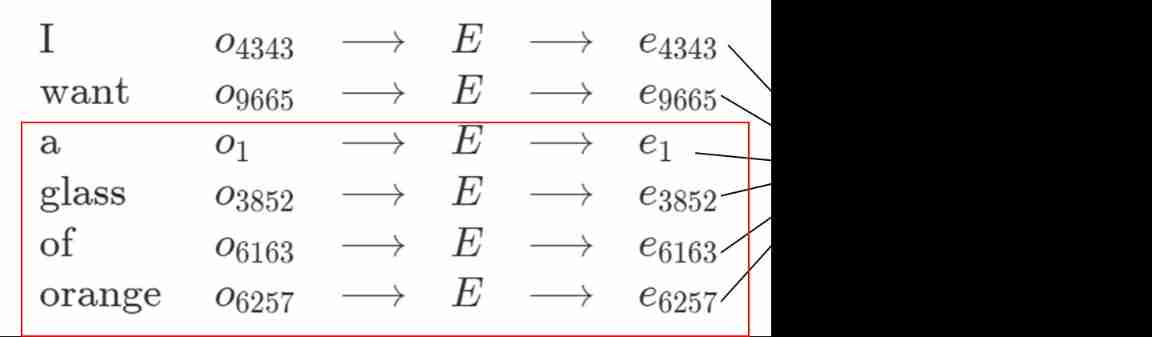
How to learn to get the embedding matrix e # yyds dry goods inventory #
随机推荐
Web components series (VII) -- life cycle of custom components
ICSI213/IECE213 Data Structures
Use of kubesphere configuration set (configmap)
【软件逆向-基础知识】分析方法、汇编指令体系结构
When sqlacodegen generates a model, how to solve the problem that the password contains special characters?
深度学习——LSTM基础
Basic function learning 02
Zero foundation uses paddlepaddle to build lenet-5 network
[groovy] string (string splicing | multi line string)
LeetCode 237. Delete nodes in the linked list
Leetcode42. connect rainwater
[105] Baidu brain map - Online mind mapping tool
speed or tempo in classical music
Kubernetes - Multi cluster management
Nmap user manual learning records
NEW:Devart dotConnect ADO.NET
@Transactional 注解导致跨库查询失效的问题
Installation of postman and postman interceptor
【无标题】
DECLARE_ WAIT_ QUEUE_ HEAD、wake_ up_ Interruptible macro analysis