当前位置:网站首页>Information Security Experiment 4: implementation of IP packet monitoring program
Information Security Experiment 4: implementation of IP packet monitoring program
2022-07-07 09:23:00 【Not enough to eat】
One 、 Purpose and requirements of the experiment
Students are familiar with the principle of network data communication as well as TCP/IP Principle of protocol structure On the basis of , Network packet monitoring technology realized by socket programming , Effectively detect the packet information transmitted on the network , Through the analysis and utilization of these information, it is helpful to maintain network security . requirement :
1. Familiar with the principle of network data communication as well as TCP/IP Principle of protocol structure .
2. master Ip Packet sending and receiving process .
3. Determine the experimental scheme on the basis of the learned knowledge , Draw a flow chart , Independent programming , Realize network listener .
4. Simply analyze the obtained data packets .
Two 、 Experimental content
Set the working mode of the network card to mixed mode . Get one in the LAN ( More than one ) The host MAC Address , Capture all packets passing through the network card , And the agreement can be analyzed 、IP source address 、IP Destination address 、TCP Source port number 、TCP Target port number, packet length and other information .
3、 ... and 、 Experimental environment
function windows Of PC machine , have JAVA、VC(windows) And other language compilation environments .
Four 、 Experimental steps and result analysis
1. Download and install WinPcap,WinPcap It can provide applications with the ability to access the bottom of the network . It is used for windows Direct network programming under the system .
2. download Jpcap.jar package , Used for the operation of packet capturing experiment ,jpcap In fact, it is not a real way to control the data link layer , It's a middleware ,JPCAP call winpcap/libpcap, And give JAVA Language provides a common interface , Thus, platform independence is realized
3. according to Jpcap.jar Package related classes and methods for experimental preparation
Bind network devices
NetworkInterface[] devices = JpcapCaptor.getDeviceList();
for (NetworkInterface n : devices) {
System.out.println(n.name + " | " + n.description);
}
Carry out the bag
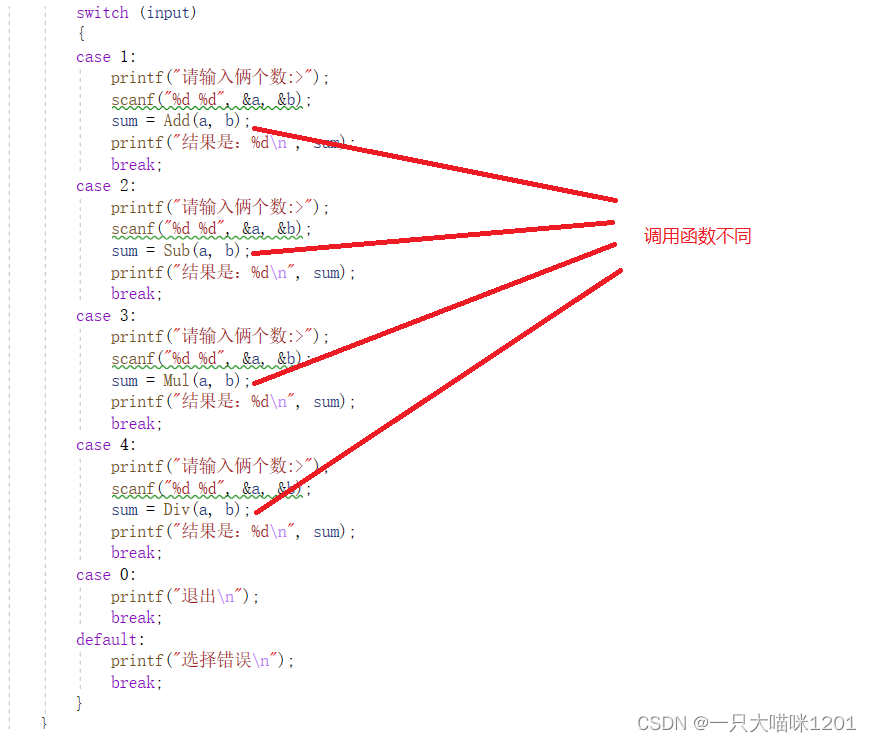
int i = 0; while (i < 10) { Packet packet = jpcap.getPacket(); if (packet instanceof IPPacket && ((IPPacket) packet).version == 4) { i++; IPPacket ip = (IPPacket) packet;// Strong go System.out.println(" edition :IPv4"); System.out.println(" Priority :" + ip.priority); System.out.println(" Distinguish between service : Maximum throughput : " + ip.t_flag); System.out.println(" Distinguish between service : Highest reliability :" + ip.r_flag); System.out.println(" length :" + ip.length); System.out.println(" identification :" + ip.ident); System.out.println("DF:Don't Fragment: " + ip.dont_frag); System.out.println("NF:Nore Fragment: " + ip.more_frag); System.out.println(" Slice offset :" + ip.offset); System.out.println(" Time to live :" + ip.hop_limit); String protocol = ""; switch (new Integer(ip.protocol)) { case 1: protocol = "ICMP"; break; case 2: protocol = "IGMP"; break; case 6: protocol = "TCP"; break; case 8: protocol = "EGP"; break; case 9: protocol = "IGP"; break; case 17: protocol = "UDP"; break; case 41: protocol = "IPv6"; break; case 89: protocol = "OSPF"; break; default: break; } System.out.println(" agreement :" + protocol); System.out.println(" Source IP " + ip.src_ip.getHostAddress()); System.out.println(" Purpose IP " + ip.dst_ip.getHostAddress()); System.out.println(" Source host name : " + ip.src_ip); System.out.println(" Destination hostname : " + ip.dst_ip); System.out.println("----------------------------------------------"); } }4. experimental result
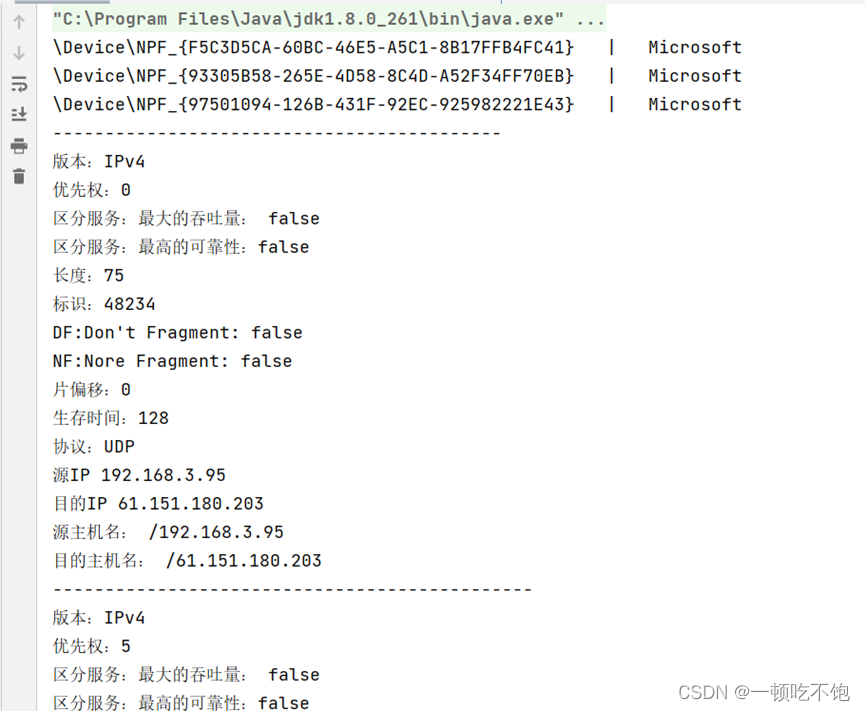
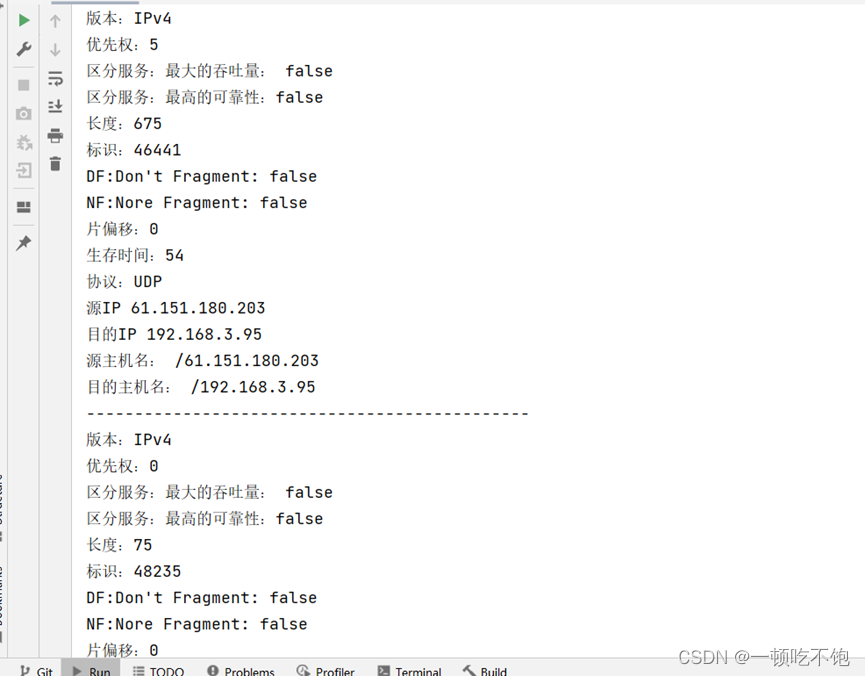
Summary of the experiment : Through this experiment , I understand the principle of network data communication , Master master Ip Packet sending and receiving process , And pass Jpcap.jar Package call winpacp Realize the ability to access the bottom of the network , Reference... In a program jpcap The method in the class implements a pair of IP Package monitoring and analysis
边栏推荐
- C language pointer (exercises)
- Locust performance test 2 (interface request)
- C语言指针(特别篇)
- MySQL common statements
- stm32和电机开发(从单机版到网络化)
- How can I apply for a PMP certificate?
- C语言指针(下篇)
- Some pit avoidance guidelines for using Huawei ECS
- Pytest+request+allure+excel interface automatic construction from 0 to 1 [five nails / flying Book notice]
- Pytest installation (command line installation)
猜你喜欢
随机推荐
Confitest of fixture py
sqlplus乱码问题,求解答
Connecting mobile phone with ADB
Variable parameter of variable length function
Mysql:select ... for update
Yapi test plug-in -- cross request
JVM 垃圾回收 详细学习笔记(二)
PMP certificate preparation experience sharing
What are the suggestions for PMP candidates?
Difference between interface iterator and iteratable
Interface test API case, data and interface separation
NVIC interrupt priority management
Unity shader (to achieve a simple material effect with adjustable color attributes only)
Why is access to the external network prohibited for internal services of the company?
How does the project manager write the weekly summary and weekly plan?
Locust performance test 4 (custom load Policy)
数据在内存中的存储
What is MD5
Summary of PMP learning materials
Pycharm create a new file and add author information