当前位置:网站首页>Data governance: Data Governance under microservice architecture
Data governance: Data Governance under microservice architecture
2022-07-06 07:45:00 【Freedom3568】
List of articles
brief introduction
Some time ago , One of my little partners jumped to a large state-owned enterprise , Just arrived at the company , The boss gave him an important project —— The data center planning of the company .
Boss explained :“ We should build a data middle platform architecture , Covering data asset management 、 Data governance 、 Data analysis, etc , At the same time, this data center , To reflect decentralization , Even the idea of decentralization ”.
My buddy has many years of experience in data warehouse architecture , It also refers to the mainstream data midrange architecture in the industry , Soon “ Copy sth. without catching its spirit ” I made a data center architecture diagram .
When he takes his own “ favourite work ”, When reporting to the boss , I didn't expect the boss only glanced , He scolded him directly , The main reason is that it doesn't reflect “ De centralization ” Thought .
My companion complained to me :“ The data center doesn't have to
边栏推荐
- WebRTC系列-H.264预估码率计算
- Inspiration from the recruitment of bioinformatics analysts in the Department of laboratory medicine, Zhujiang Hospital, Southern Medical University
- 数据治理:元数据管理篇
- Compliance and efficiency, accelerate the digital transformation of pharmaceutical enterprises, and create a new document resource center for pharmaceutical enterprises
- 数据治理:误区梳理篇
- Scala language learning-08-abstract classes
- MEX有关的学习
- Select all the lines with a symbol in word and change them to titles
- 数据治理:微服务架构下的数据治理
- [CF Gym101196-I] Waif Until Dark 网络最大流
猜你喜欢
opencv学习笔记九--背景建模+光流估计
![[MySQL learning notes 30] lock (non tutorial)](/img/9b/1e27575d83ff40bebde118b925f609.png)
[MySQL learning notes 30] lock (non tutorial)
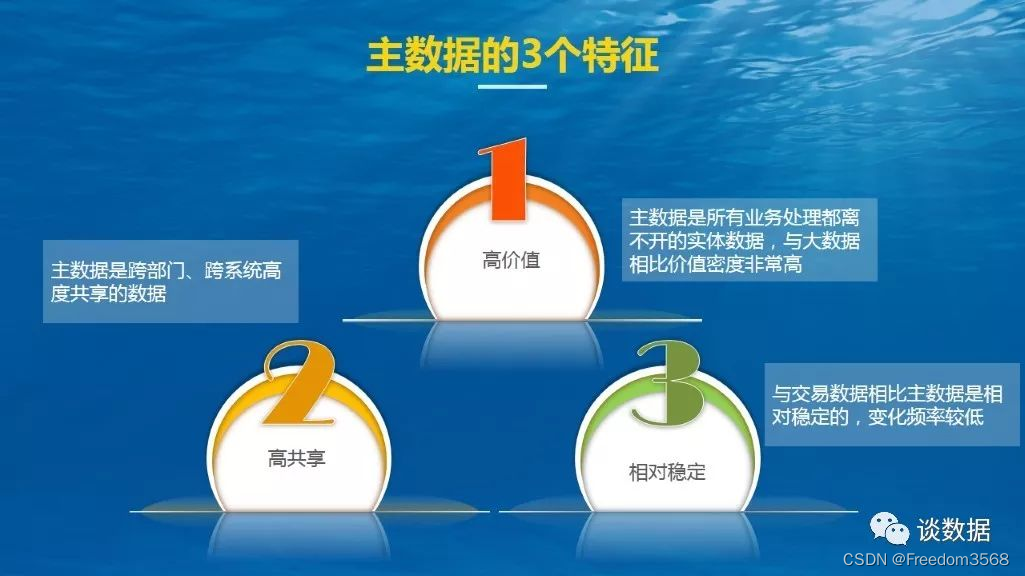
数据治理:主数据的3特征、4超越和3二八原则

Interview Reply of Zhuhai Jinshan

opencv学习笔记八--答题卡识别
Mise en œuvre du langage leecode - C - 15. Somme des trois chiffres - - - - - idées à améliorer
Esrally domestic installation and use pit avoidance Guide - the latest in the whole network
【Redis】NoSQL数据库和redis简介
![Ble of Jerry [chapter]](/img/00/27486ad68bf491997d10e387c32dd4.png)
Ble of Jerry [chapter]
![[CF Gym101196-I] Waif Until Dark 网络最大流](/img/66/6b339fc23146b5fbdcd2a1fa0a2349.png)
[CF Gym101196-I] Waif Until Dark 网络最大流
随机推荐
软件开发的一点随记
Summary of Digital IC design written examination questions (I)
Hackathon ifm
洛谷P4127 [AHOI2009]同类分布 题解
If Jerry's Bluetooth device wants to send data to the mobile phone, the mobile phone needs to open the notify channel first [article]
Scala language learning-08-abstract classes
HTTP cache, forced cache, negotiated cache
When the Jericho development board is powered on, you can open the NRF app with your mobile phone [article]
解决方案:智慧工地智能巡檢方案視頻監控系統
[window] when the Microsoft Store is deleted locally, how to reinstall it in three steps
edge瀏覽器 路徑獲得
TS 类型体操 之 循环中的键值判断,as 关键字使用
jmeter性能测试步骤实战教程
Select all the lines with a symbol in word and change them to titles
Ble of Jerry [chapter]
Sélectionnez toutes les lignes avec un symbole dans Word et changez - les en titre
Typescript interface and the use of generics
Inspiration from the recruitment of bioinformatics analysts in the Department of laboratory medicine, Zhujiang Hospital, Southern Medical University
Description of octomap averagenodecolor function
[MySQL learning notes 30] lock (non tutorial)