当前位置:网站首页>[buuctf.reverse] 152-154
[buuctf.reverse] 152-154
2022-07-05 13:57:00 【Shi Shi Shi Shi Shi Shi Shi Shi Shi Shi Shi Shi Shi Shi Shi Shi】
Catalog
152_[watevrCTF 2019]Hacking For Vodka
152_[watevrCTF 2019]Hacking For Vodka
main Just two functions
void __fastcall __noreturn main(int a1, char **a2, char **a3)
{
if ( ptrace(PTRACE_TRACEME, 0LL, 1LL, 0LL) < 0 )
sub_102E();
sub_12BF();
exit(0);
}Open and see that the two functions are basically the same , XOR values
__int64 sub_C6D()
{
char v1[56]; // [rsp+20h] [rbp-40h] BYREF
unsigned __int64 v2; // [rsp+58h] [rbp-8h]
v2 = __readfsqword(0x28u);
v1[0] = aWabcdefglhijkm[0];
v1[2] = aWabcdefglhijkm[21] ^ 2;
v1[3] = aWabcdefglhijkm[5] ^ 3;
v1[6] = aWabcdefglhijkm[28] ^ 6;
v1[13] = aWabcdefglhijkm[26] ^ 0xD;
v1[8] = aWabcdefglhijkm[9] ^ 8;
v1[5] = aWabcdefglhijkm[18] ^ 5;
v1[11] = aWabcdefglhijkm[12] ^ 0xB;
v1[1] = aWabcdefglhijkm[1] ^ 1;
v1[10] = aWabcdefglhijkm[15] ^ 0xA;
v1[9] = aWabcdefglhijkm[34] ^ 9;
v1[12] = aWabcdefglhijkm[35] ^ 0xC;
v1[47] = aWabcdefglhijkm[5] ^ 0x2F;
v1[16] = aWabcdefglhijkm[3] ^ 0x10;
v1[15] = aWabcdefglhijkm[34] ^ 0xF;
v1[4] = aWabcdefglhijkm[19] ^ 4;
v1[20] = aWabcdefglhijkm[7] ^ 0x14;
v1[23] = aWabcdefglhijkm[16] ^ 0x17;
v1[32] = aWabcdefglhijkm[1] ^ 0x20;
v1[24] = aWabcdefglhijkm[18] ^ 0x18;
v1[14] = aWabcdefglhijkm[9] ^ 0xE;
v1[18] = aWabcdefglhijkm[31] ^ 0x12;
v1[21] = aWabcdefglhijkm[26] ^ 0x15;
v1[31] = aWabcdefglhijkm[9] ^ 0x1F;
v1[22] = aWabcdefglhijkm[6] ^ 0x16;
v1[7] = aWabcdefglhijkm[21] ^ 7;
v1[34] = aWabcdefglhijkm[12] ^ 0x22;
v1[17] = aWabcdefglhijkm[12] ^ 0x11;
v1[19] = aWabcdefglhijkm[15] ^ 0x13;
v1[40] = aWabcdefglhijkm[18] ^ 0x28;
v1[26] = aWabcdefglhijkm[20] ^ 0x1A;
v1[33] = aWabcdefglhijkm[3] ^ 0x21;
v1[25] = aWabcdefglhijkm[26] ^ 0x19;
v1[29] = aWabcdefglhijkm[22] ^ 0x1D;
v1[27] = aWabcdefglhijkm[40] ^ 0x1B;
v1[42] = aWabcdefglhijkm[16] ^ 0x2A;
v1[37] = aWabcdefglhijkm[7] ^ 0x25;
v1[28] = aWabcdefglhijkm[11] ^ 0x1C;
v1[39] = aWabcdefglhijkm[16] ^ 0x27;
v1[35] = aWabcdefglhijkm[10] ^ 0x23;
v1[36] = aWabcdefglhijkm[15] ^ 0x24;
v1[48] = aWabcdefglhijkm[1] ^ 0x30;
v1[30] = aWabcdefglhijkm[26] ^ 0x1E;
v1[51] = 0;
v1[43] = aWabcdefglhijkm[11] ^ 0x2B;
v1[44] = aWabcdefglhijkm[22] ^ 0x2C;
v1[45] = aWabcdefglhijkm[30] ^ 0x2D;
v1[38] = aWabcdefglhijkm[6] ^ 0x26;
v1[50] = aWabcdefglhijkm[29] ^ 0x32;
v1[49] = aWabcdefglhijkm[13] ^ 0x31;
v1[41] = aWabcdefglhijkm[20] ^ 0x29;
v1[46] = aWabcdefglhijkm[21] ^ 0x2E;
sub_92A((__int64)"wabcdefglhijkmqnoprvstuzxy_!{}.1234567890 ", (__int64)v1, 51);
return 1LL;
}then Just deal with it
aWabcdefglhijkm = b'wabcdefglhijkmqnoprvstuzxy_!{}.1234567890 '
v1 = [0]*60
v1[0] = aWabcdefglhijkm[0]
v1[2] = aWabcdefglhijkm[21] ^ 2
v1[3] = aWabcdefglhijkm[5] ^ 3
v1[6] = aWabcdefglhijkm[28] ^ 6
v1[13] = aWabcdefglhijkm[26] ^ 0xD
v1[8] = aWabcdefglhijkm[9] ^ 8
v1[5] = aWabcdefglhijkm[18] ^ 5
v1[11] = aWabcdefglhijkm[12] ^ 0xB
v1[1] = aWabcdefglhijkm[1] ^ 1
v1[10] = aWabcdefglhijkm[15] ^ 0xA
v1[9] = aWabcdefglhijkm[34] ^ 9
v1[12] = aWabcdefglhijkm[35] ^ 0xC
v1[47] = aWabcdefglhijkm[5] ^ 0x2F
v1[16] = aWabcdefglhijkm[3] ^ 0x10
v1[15] = aWabcdefglhijkm[34] ^ 0xF
v1[4] = aWabcdefglhijkm[19] ^ 4
v1[20] = aWabcdefglhijkm[7] ^ 0x14
v1[23] = aWabcdefglhijkm[16] ^ 0x17
v1[32] = aWabcdefglhijkm[1] ^ 0x20
v1[24] = aWabcdefglhijkm[18] ^ 0x18
v1[14] = aWabcdefglhijkm[9] ^ 0xE
v1[18] = aWabcdefglhijkm[31] ^ 0x12
v1[21] = aWabcdefglhijkm[26] ^ 0x15
v1[31] = aWabcdefglhijkm[9] ^ 0x1F
v1[22] = aWabcdefglhijkm[6] ^ 0x16
v1[7] = aWabcdefglhijkm[21] ^ 7
v1[34] = aWabcdefglhijkm[12] ^ 0x22
v1[17] = aWabcdefglhijkm[12] ^ 0x11
v1[19] = aWabcdefglhijkm[15] ^ 0x13
v1[40] = aWabcdefglhijkm[18] ^ 0x28
v1[26] = aWabcdefglhijkm[20] ^ 0x1A
v1[33] = aWabcdefglhijkm[3] ^ 0x21
v1[25] = aWabcdefglhijkm[26] ^ 0x19
v1[29] = aWabcdefglhijkm[22] ^ 0x1D
v1[27] = aWabcdefglhijkm[40] ^ 0x1B
v1[42] = aWabcdefglhijkm[16] ^ 0x2A
v1[37] = aWabcdefglhijkm[7] ^ 0x25
v1[28] = aWabcdefglhijkm[11] ^ 0x1C
v1[39] = aWabcdefglhijkm[16] ^ 0x27
v1[35] = aWabcdefglhijkm[10] ^ 0x23
v1[36] = aWabcdefglhijkm[15] ^ 0x24
v1[48] = aWabcdefglhijkm[1] ^ 0x30
v1[30] = aWabcdefglhijkm[26] ^ 0x1E
v1[51] = 0
v1[43] = aWabcdefglhijkm[11] ^ 0x2B
v1[44] = aWabcdefglhijkm[22] ^ 0x2C
v1[45] = aWabcdefglhijkm[30] ^ 0x2D
v1[38] = aWabcdefglhijkm[6] ^ 0x26
v1[50] = aWabcdefglhijkm[29] ^ 0x32
v1[49] = aWabcdefglhijkm[13] ^ 0x31
v1[41] = aWabcdefglhijkm[20] ^ 0x29
v1[46] = aWabcdefglhijkm[21] ^ 0x2E
flag = [0]*52
for i in range(52):
flag[i] = v1[i]^i
print(bytes(flag))
#watevr{th4nk5_h4ck1ng_for_s0ju_hackingforsoju.team}
#flag{th4nk5_h4ck1ng_for_s0ju_hackingforsoju.team} The first 2 Correct paragraph 153_[watevrCTF 2019]sabataD
The program makes a rot13 And then divide it into 3 A comparison
unsigned __int64 sub_B7A()
{
int i; // [rsp+0h] [rbp-310h]
int v2; // [rsp+4h] [rbp-30Ch]
int j; // [rsp+4h] [rbp-30Ch]
int v4; // [rsp+8h] [rbp-308h]
int v5; // [rsp+Ch] [rbp-304h]
int v6; // [rsp+10h] [rbp-300h]
int v7; // [rsp+14h] [rbp-2FCh]
FILE *stream; // [rsp+18h] [rbp-2F8h]
glob_t pglob; // [rsp+20h] [rbp-2F0h] BYREF
char nptr[6]; // [rsp+6Ah] [rbp-2A6h] BYREF
char s1[64]; // [rsp+70h] [rbp-2A0h] BYREF
char s2[64]; // [rsp+B0h] [rbp-260h] BYREF
char pattern[64]; // [rsp+F0h] [rbp-220h] BYREF
char s[208]; // [rsp+130h] [rbp-1E0h] BYREF
char v15[264]; // [rsp+200h] [rbp-110h] BYREF
unsigned __int64 v16; // [rsp+308h] [rbp-8h]
v16 = __readfsqword(0x28u);
while ( strcmp(s1, "terminate") )
{
fflush(stdin);
fflush(stdout);
bzero(s, 0xC8uLL);
bzero(s1, 0x32uLL);
bzero(nptr, 6uLL);
fgets(s, 200, stdin);
v2 = 0;
v4 = 0;
v5 = 0;
v6 = 0;
for ( i = 0; i <= 154; ++i )
{
s[i] = sub_AEA(s[i]); // rot13, Upper and lower case characters , The rest is the same
if ( i <= 150 )
{
if ( i % 3 )
{
if ( i % 3 == 1 )
{
if ( s[i] != 95 ) // Underline _
s2[v4] = s[i];
++v4;
}
else if ( i % 3 == 2 )
{
if ( s[i] != 95 )
pattern[v5] = s[i];
++v5;
}
}
else
{
if ( s[i] != 95 )
s1[v2] = s[i];
++v2;
}
}
else
{
nptr[v6++] = s[i];
}
}
v7 = atoi(nptr);
if ( strcmp("watevr-admin", s2) || !strcmp("/home/ctf/flag.txt", pattern) )
{
puts("Unauthorized access! This has been logged.");
exit(0);
}
fflush(stdout);
if ( !strcmp("Fetch from file with index", s1) )
{
glob(pattern, 0, 0LL, &pglob);
stream = fopen(*(const char **)pglob.gl_pathv, "r");
if ( stream )
{
for ( j = 0; fgets(v15, 256, stream) && j != v7; ++j )
;
globfree(&pglob);
printf("Found %s\n", v15);
fclose(stream);
}
else
{
puts("Tried to open non-existing file!");
}
}
}
puts("Terminated connection");
return __readfsqword(0x28u) ^ v16;
}It's just flag Use a wildcard
def rot13(s):
t = ''
for i in s:
if ord(i)>=ord('A') and ord(i)<=ord('Z'):
t += chr((ord(i) - 65 + 13)%26 + 65)
elif ord(i)>=ord('a') and ord(i)<=ord('z'):
t += chr((ord(i) - 97 + 13)%26 + 97)
else:
t += i
return t
s1 = "Fetch from file with index\0"
s2 = "watevr-admin".ljust(27,'\0')
pattern = "/home/ctf/fl?g.txt".ljust(27,'\0')
s = ''
for i in range(27):
s+=s1[i]+s2[i]+pattern[i]
s = rot13(s)
from pwn import *
p = remote('node4.buuoj.cn', 27845)
#p = process('./service')
context.log_level = 'debug'
p.sendline(s.encode())
p.recv()
#flag{1eaae55e-3119-4a10-83f4-b1836d9f26b5}
154_[HackIM2020]returminator
The program is very short , Just a read , But there is overflow
__int64 __fastcall main(int a1, char **a2, char **a3)
{
char s[40]; // [rsp+0h] [rbp-30h] BYREF
FILE *stream; // [rsp+28h] [rbp-8h]
puts("Hello world!");
stream = fopen("flag", "r");
if ( !stream )
exit(1);
fgets(s, 35, stream);
fclose(stream);
memset(dest, 0, 0x23uLL);
strcpy(dest, s);
read(0, s, 0x400uLL);
return 0LL;
}And then there's a deploy.py Read in payload Get the return value ( It looks like pwn The question is rop)
import subprocess
o = [296, 272, 272, 272, 296, 360, 272, 424, 272, 208, 120, 120, 120, 96, 120, 120, 120, 120, 120, 120, 120, 208, 120, 120, 208, 208, 208, 208, 208, 272, 120, 208, 208]
r = [208, 225, 237, 20, 214, 183, 79, 105, 207, 217, 125, 66, 123, 104, 97, 99, 107 , 105, 109, 50, 48, 202, 111, 111, 29, 63, 223, 36, 0, 124, 100, 219, 32]
cmd = ['./main']
rets = []
with open('blob', 'rb') as f:
for offset in o:
data = f.read(offset)
p = subprocess.Popen(cmd, stdin=subprocess.PIPE)
p.stdin.write(data)
p.communicate()
rets.append(p.returncode)
if all([rets[i] == r[i] for i in range(len(r))]):
print('Yes!')
else:
print('No!')
and blob Inside is his payload, The first payload Restore
from pwn import *
dic ={0x40119a: 'pop rdi', 0x40119c: 'pop rsi', 0x40119e: 'pop rdx', 0x4011a0: 'pop rcx', 0x4011a2: 'pop rax',
0x4011a4: 'add rax,rdi', 0x4011a8: 'add rax,rsi', 0x4011ac: 'add rax,rdx', 0x4011b0: 'add rax,rcx', 0x4011b4: 'add rax,rax',
0x4011b8: 'add rax,1', 0x4011bd: 'xor rax,rax',
0x4011c1: 'sub rax,rdi', 0x4011c5: 'sub rax,rsi', 0x4011c9: 'sub rax,rdx', 0x4011cd: 'sub rax,rcx',
0x4011d1: 'sub rax,1',
0x4011d6: 'movzx rdi,[rdi]', 0x4011db: 'movzx rsi,[rsi]', 0x4011e0: 'movzx rdx,[rdx]', 0x4011e5: 'movzx rcx,[rcx]',
0x4011ea: 'mov rdi,rax', 0x4011ee: 'mov rsi,rax', 0x4011f2: 'mov rdx,rax', 0x4011f6: 'mov rcx,rax', 0x4011fa: 'mov rdi,0;call exit()',
0x4011ff: 'call exit()'}
f = open('blob', 'rb')
txt = ''
i = 0
while True:
v = f.read(8)
i+=8
if v == b'aaaaaaaa':
txt += '----------\n'
i+=0x30
v = f.read(0x30)
continue
else:
if 'pop' in dic[u64(v)]:
txt += dic[u64(v)]+ ';' +str(u64(f.read(8))) + '\n'
i+=8
else:
txt += dic[u64(v)]+'\n'
#print(hex(i),v)
if i>=0x1988:
break
print(txt)
Translate the result again , Get some formulas
----------f[0]+f[2]+f[4] -100 == r[0]
pop rax;4210848
pop rdi;0
add rax,rdi
mov rdi,rax
movzx rdi,[rdi]
pop rax;4210848
pop rsi;2
add rax,rsi
mov rsi,rax
movzx rsi,[rsi]
pop rax;4210848
pop rdx;4
add rax,rdx
mov rdx,rax
movzx rdx,[rdx]
xor rax,rax
add rax,rdi
add rax,rsi
add rax,rdx
pop rdi;100
sub rax,rdi
mov rdi,rax
call exit()
----------f[6]+f[8]+f[10] == r[1]
pop rax;4210848
pop rdi;6
add rax,rdi
mov rdi,rax
movzx rdi,[rdi]
pop rax;4210848
pop rsi;8
add rax,rsi
mov rsi,rax
movzx rsi,[rsi]
pop rax;4210848
pop rdx;10
add rax,rdx
mov rdx,rax
movzx rdx,[rdx]
xor rax,rax
add rax,rdi
add rax,rsi
add rax,rdx
mov rdi,rax
call exit()
----------f[12]+f[14]+f[16] == r[2]
pop rax;4210848
pop rdi;12
add rax,rdi
mov rdi,rax
movzx rdi,[rdi]
pop rax;4210848
pop rsi;14
add rax,rsi
mov rsi,rax
movzx rsi,[rsi]
pop rax;4210848
pop rdx;16
add rax,rdx
mov rdx,rax
movzx rdx,[rdx]
xor rax,rax
add rax,rdi
add rax,rsi
add rax,rdx
mov rdi,rax
call exit()
----------f[18]+f[1]-f[30] == r[3]
pop rax;4210848
pop rdi;18
add rax,rdi
mov rdi,rax
movzx rdi,[rdi]
pop rax;4210848
pop rsi;1
add rax,rsi
mov rsi,rax
movzx rsi,[rsi]
pop rax;4210848
pop rdx;30
add rax,rdx
mov rdx,rax
movzx rdx,[rdx]
xor rax,rax
add rax,rdi
add rax,rsi
sub rax,rdx
mov rdi,rax
call exit()
----------f[3]+f[22]+f[3]-100 == r[4]
pop rax;4210848
pop rdi;3
add rax,rdi
mov rdi,rax
movzx rdi,[rdi]
pop rax;4210848
pop rsi;22
add rax,rsi
mov rsi,rax
movzx rsi,[rsi]
pop rax;4210848
pop rdx;3
add rax,rdx
mov rdx,rax
movzx rdx,[rdx]
xor rax,rax
add rax,rdi
add rax,rsi
add rax,rdx
pop rdi;100
sub rax,rdi
mov rdi,rax
call exit()
----------f[5]+f[29]+f[28]-f[7]-100 == r[5]
pop rax;4210848
pop rdi;5
add rax,rdi
mov rdi,rax
movzx rdi,[rdi]
pop rax;4210848
pop rsi;29
add rax,rsi
mov rsi,rax
movzx rsi,[rsi]
pop rax;4210848
pop rdx;28
add rax,rdx
mov rdx,rax
movzx rdx,[rdx]
pop rax;4210848
pop rcx;7
add rax,rcx
mov rcx,rax
movzx rcx,[rcx]
xor rax,rax
add rax,rdi
add rax,rsi
add rax,rdx
sub rax,rcx
pop rdi;100
sub rax,rdi
mov rdi,rax
call exit()
----------f[9]+f[17]-f[11] == r[6]
pop rax;4210848
pop rdi;9
add rax,rdi
mov rdi,rax
movzx rdi,[rdi]
pop rax;4210848
pop rsi;17
add rax,rsi
mov rsi,rax
movzx rsi,[rsi]
pop rax;4210848
pop rdx;11
add rax,rdx
mov rdx,rax
movzx rdx,[rdx]
xor rax,rax
add rax,rdi
add rax,rsi
sub rax,rdx
mov rdi,rax
call exit()
----------f[13]+f[15]+f[20]-f[19]+f[27] == r[7]
pop rax;4210848
pop rdi;19
add rax,rdi
mov rdi,rax
movzx rdi,[rdi]
pop rax;4210848
pop rsi;27
add rax,rsi
mov rsi,rax
movzx rsi,[rsi]
xor rax,rax
add rax,rdi
add rax,rsi
mov rcx,rax
pop rax;4210848
pop rdi;13
add rax,rdi
mov rdi,rax
movzx rdi,[rdi]
pop rax;4210848
pop rsi;15
add rax,rsi
mov rsi,rax
movzx rsi,[rsi]
pop rax;4210848
pop rdx;20
add rax,rdx
mov rdx,rax
movzx rdx,[rdx]
xor rax,rax
add rax,rdi
add rax,rsi
add rax,rdx
sub rax,rcx
mov rdi,rax
call exit()
----------
pop rax;4210848
pop rdi;21
add rax,rdi
mov rdi,rax
movzx rdi,[rdi]
pop rax;4210848
pop rsi;23
add rax,rsi
mov rsi,rax
movzx rsi,[rsi]
pop rax;4210848
pop rdx;23
add rax,rdx
mov rdx,rax
movzx rdx,[rdx]
xor rax,rax
add rax,rdi
add rax,rsi
add rax,rdx
mov rdi,rax
call exit()
----------
pop rax;4210848
pop rdi;25
add rax,rdi
mov rdi,rax
movzx rdi,[rdi]
pop rax;4210848
pop rsi;26
add rax,rsi
mov rsi,rax
movzx rsi,[rsi]
xor rax,rax
add rax,rdi
add rax,rsi
mov rdi,rax
call exit()
----------
pop rax;4210848
pop rdi;30
add rax,rdi
mov rdi,rax
movzx rdi,[rdi]
call exit()
----------
pop rax;4210848
pop rdi;9
add rax,rdi
mov rdi,rax
movzx rdi,[rdi]
call exit()
----------
pop rax;4210848
pop rdi;8
add rax,rdi
mov rdi,rax
movzx rdi,[rdi]
call exit()
----------
pop rax;4210848
mov rdi,rax
movzx rdi,[rdi]
call exit()
----------
pop rax;4210848
pop rdi;1
add rax,rdi
mov rdi,rax
movzx rdi,[rdi]
call exit()
----------
pop rax;4210848
pop rdi;2
add rax,rdi
mov rdi,rax
movzx rdi,[rdi]
call exit()
----------
pop rax;4210848
pop rdi;3
add rax,rdi
mov rdi,rax
movzx rdi,[rdi]
call exit()
----------
pop rax;4210848
pop rdi;4
add rax,rdi
mov rdi,rax
movzx rdi,[rdi]
call exit()
----------
pop rax;4210848
pop rdi;5
add rax,rdi
mov rdi,rax
movzx rdi,[rdi]
call exit()
----------
pop rax;4210848
pop rdi;6
add rax,rdi
mov rdi,rax
movzx rdi,[rdi]
call exit()
----------
pop rax;4210848
pop rdi;7
add rax,rdi
mov rdi,rax
movzx rdi,[rdi]
call exit()
----------
pop rax;4210848
pop rdi;11
add rax,rdi
mov rdi,rax
movzx rdi,[rdi]
pop rax;4210848
pop rsi;0
add rax,rsi
mov rsi,rax
movzx rsi,[rsi]
xor rax,rax
add rax,rdi
add rax,rsi
mov rdi,rax
call exit()
----------
pop rax;4210848
pop rdi;29
add rax,rdi
mov rdi,rax
movzx rdi,[rdi]
call exit()
----------
pop rax;4210848
pop rdi;29
add rax,rdi
mov rdi,rax
movzx rdi,[rdi]
call exit()
----------
pop rax;4210848
pop rdi;29
add rax,rdi
mov rdi,rax
movzx rdi,[rdi]
pop rax;4210848
pop rsi;13
add rax,rsi
mov rsi,rax
movzx rsi,[rsi]
xor rax,rax
add rax,rdi
sub rax,rsi
mov rdi,rax
call exit()
----------
pop rax;4210848
pop rdi;28
add rax,rdi
mov rdi,rax
movzx rdi,[rdi]
pop rax;4210848
pop rsi;14
add rax,rsi
mov rsi,rax
movzx rsi,[rsi]
xor rax,rax
add rax,rdi
sub rax,rsi
mov rdi,rax
call exit()
----------
pop rax;4210848
pop rdi;28
add rax,rdi
mov rdi,rax
movzx rdi,[rdi]
pop rax;4210848
pop rsi;15
add rax,rsi
mov rsi,rax
movzx rsi,[rsi]
xor rax,rax
add rax,rdi
add rax,rsi
mov rdi,rax
call exit()
----------
pop rax;4210848
pop rdi;0
add rax,rdi
mov rdi,rax
movzx rdi,[rdi]
pop rax;4210848
pop rsi;27
add rax,rsi
mov rsi,rax
movzx rsi,[rsi]
xor rax,rax
add rax,rdi
sub rax,rsi
mov rdi,rax
call exit()
----------
pop rax;4210848
pop rdi;23
add rax,rdi
mov rdi,rax
movzx rdi,[rdi]
pop rax;4210848
pop rsi;24
add rax,rsi
mov rsi,rax
movzx rsi,[rsi]
xor rax,rax
add rax,rdi
sub rax,rsi
mov rdi,rax
call exit()
----------
pop rax;4210848
pop rdi;26
add rax,rdi
mov rdi,rax
movzx rdi,[rdi]
pop rax;4210848
pop rsi;0
add rax,rsi
mov rsi,rax
movzx rsi,[rsi]
pop rax;4210848
pop rdx;1
add rax,rdx
mov rdx,rax
movzx rdx,[rdx]
xor rax,rax
add rax,rdi
add rax,rsi
sub rax,rdx
mov rdi,rax
call exit()
----------
pop rax;4210848
pop rdi;19
add rax,rdi
mov rdi,rax
movzx rdi,[rdi]
call exit()
----------
pop rax;4210848
pop rdi;11
add rax,rdi
mov rdi,rax
movzx rdi,[rdi]
pop rax;4210848
pop rsi;12
add rax,rsi
mov rsi,rax
movzx rsi,[rsi]
xor rax,rax
add rax,rdi
add rax,rsi
mov rdi,rax
call exit()
----------
pop rax;4210848
pop rdi;21
add rax,rdi
mov rdi,rax
movzx rdi,[rdi]
pop rax;4210848
pop rsi;20
add rax,rsi
mov rsi,rax
movzx rsi,[rsi]
xor rax,rax
add rax,rdi
sub rax,rsi
mov rdi,rax
call exit()
Then put the formula z3
from z3 import *
r = [208, 225, 237, 20, 214, 183, 79, 105, 207, 217,
125, 66, 123, 104, 97, 99, 107 , 105, 109, 50,
48, 202, 111, 111, 29, 63, 223, 36, 0, 124,
100, 219, 32]
f = [Int(f'f_{i}') for i in range(31)]
s = Solver()
for i in range(31):
s.add([f[i]>0x20, f[i]<0x7f])
s.add(f[0]+f[2]+f[4] -100 == r[0])
s.add(f[6]+f[8]+f[10] == r[1])
s.add(f[12]+f[14]+f[16] == r[2])
s.add(f[18]+f[1]-f[30] == r[3])
s.add(f[3]+f[22]+f[3]-100 == r[4])
s.add(f[5]+f[29]+f[28]-f[7]-100 == r[5])
s.add(f[9]+f[17]-f[11] == r[6])
s.add(f[13]+f[15]+f[20]-f[19]-f[27] == r[7])
s.add(f[21]+f[23]+f[23] == r[8])
s.add(f[25]+f[26] == r[9])
s.add(f[30] == r[10])
s.add(f[9] == r[11])
s.add(f[8] == r[12])
s.add(f[0] == r[13])
s.add(f[1] == r[14])
s.add(f[2] == r[15])
s.add(f[3] == r[16])
s.add(f[4] == r[17])
s.add(f[5] == r[18])
s.add(f[6] == r[19])
s.add(f[7] == r[20])
s.add(f[11]+f[0] == r[21])
s.add(f[29] == r[22])
s.add(f[29] == r[23])
s.add(f[29]-f[13] == r[24])
s.add(f[28]-f[14] == r[25])
s.add(f[28]+f[15] == r[26])
s.add(f[0]-f[27] == r[27])
s.add(f[23]-f[24] == r[28])
s.add(f[26]+f[0]-f[1] == r[29])
s.add(f[19] == r[30])
s.add(f[11]+f[12] == r[31])
s.add(f[21]-f[20] == r[32])
if s.check() == sat:
d = s.model()
print(d)
for i in range(31):
print(chr(d[f[i]].as_long()), end='')
#hackim20{B4byR0pDo0dOod00duDoo}
#flag{B4byR0pDo0dOod00duDoo}
边栏推荐
- These 18 websites can make your page background cool
- kafaka 日志收集
- Idea remote debugging agent
- When using Tencent cloud for the first time, you can only use webshell connection instead of SSH connection.
- leetcode 10. Regular expression matching regular expression matching (difficult)
- redis6数据类型及操作总结
- About the problem and solution of 403 error in wampserver
- 昆仑太科冲刺科创板:年营收1.3亿拟募资5亿 电科太极持股40%
- Jetpack Compose入门到精通
- 内网穿透工具 netapp
猜你喜欢
Jetpack compose introduction to mastery
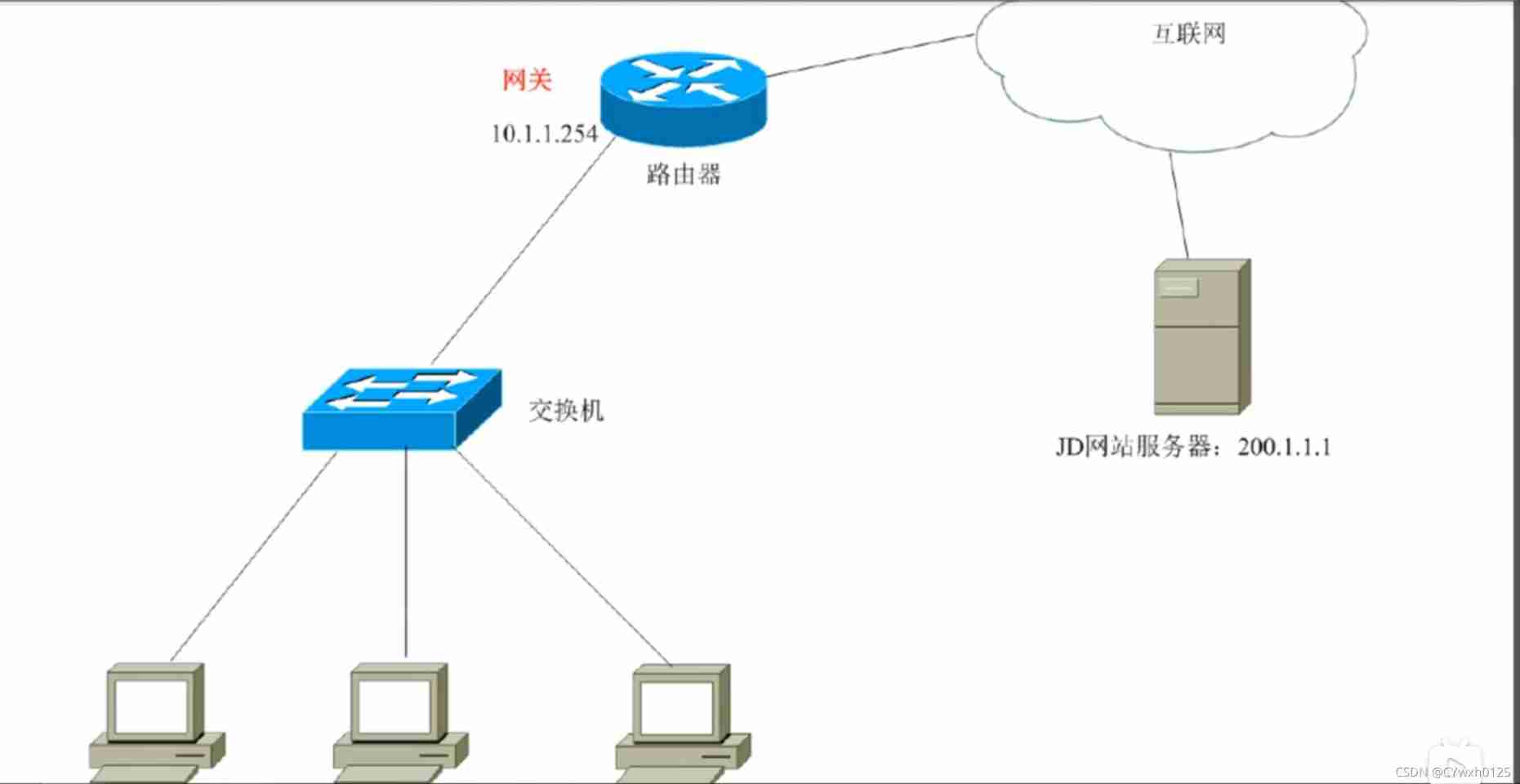
Detailed explanation of IP address and preparation of DOS basic commands and batch processing
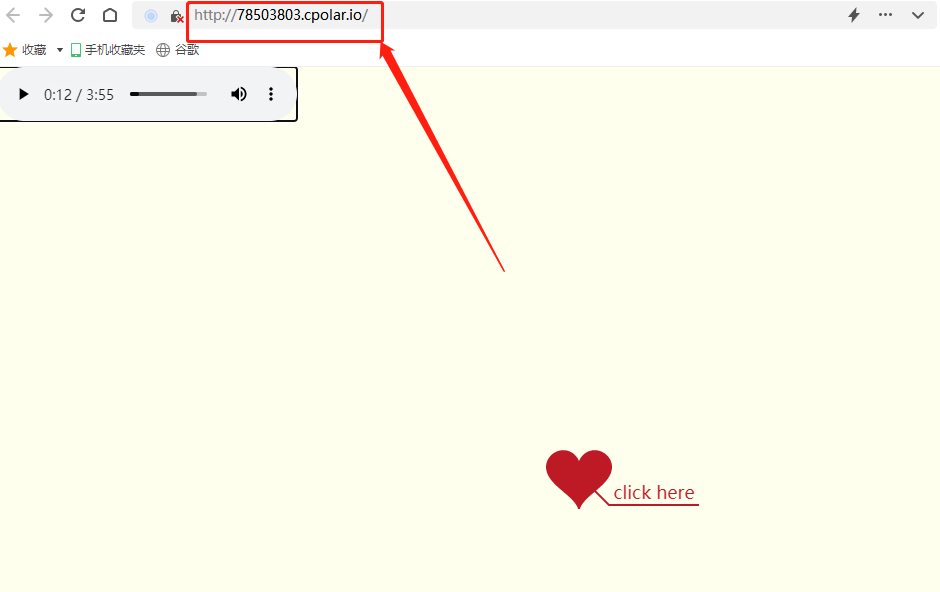
Set up a website with a sense of ceremony, and post it to the public 2/2 through the intranet
![[South China University of technology] information sharing of postgraduate entrance examination and re examination](/img/a8/41e62a7a8d0a2e901e06c751c30291.jpg)
[South China University of technology] information sharing of postgraduate entrance examination and re examination

锚点导航小demo
![UE源码阅读[1]---由问题入手UE中的延迟渲染](/img/fa/f33242b01e4da973fa36c2c6f23db6.png)
UE源码阅读[1]---由问题入手UE中的延迟渲染

PHP basic syntax
Idea remote debugging agent
Solve the problem of invalid uni app configuration page and tabbar

【华南理工大学】考研初试复试资料分享
随机推荐
Laravel - view (new and output views)
Recommendation number | what are interesting people looking at?
Comparison of several distributed databases
内网穿透工具 netapp
Network security - Novice introduction
搭建一个仪式感点满的网站,并内网穿透发布到公网 2/2
aspx 简单的用户登录
Those things I didn't know until I took the postgraduate entrance examination
OSI and tcp/ip protocol cluster
Jasypt configuration file encryption | quick start | actual combat
uplad_ Labs first three levels
RK3566添加LED
Matlab learning 2022.7.4
2022 driller (drilling) examination question bank and simulation examination
LeetCode_3(无重复字符的最长子串)
matlab学习2022.7.4
Hide Chinese name
Address book (linked list implementation)
2022建筑焊工(建筑特殊工种)特种作业证考试题库及在线模拟考试
2022 machine fitter (Advanced) test question simulation test question bank simulation test platform operation