当前位置:网站首页>[CTF] AWDP summary (WEB)
[CTF] AWDP summary (WEB)
2022-07-05 01:14:00 【Sunlight_ three hundred and sixteen】
Catalog
【CTF】AWDP summary (Web)
What is? adwp?
AWDP It is a comprehensive assessment of team attack 、 Defense technology capability 、 The game mode of both attack and defense with real-time strategy . Each team is an attacker and a defender , Fully reflect the actual combat of the game 、 Real time and confrontation , Comprehensively consider the penetration ability and protection ability of the participating team .
In the game , Each team has the same virtual target machine , Team members should be responsible for GameBox attack , And submit the correct flag( Prove that you have the ability to attack the problem ); in the meantime , The platform launches an attack on the target aircraft of the team in a round system , Check whether the vulnerabilities of other players are successfully repaired , If the repair is successful, it is considered that the team has the defense ability of the vulnerability .
The scoring rules are as follows : During the competition, each team has the same starting score (10000 branch ), Score by the end of the game , Score as each team , From high to low in the ranking .
The participating team can obtain points in the following two ways :
1) Conquered : Submit GameBox Stored in flag;
2) defense : Successfully defend the attack of the platform on each target , And the service is normal .
At the same time, they will lose points in the following two ways :
1) Service exception : The team cannot maintain a GameBox The normal service of , Platform inspection failed ;
2) Violations, : The referee awarded a penalty for violating the competition discipline and discovering violations .
Six states
– Attacked , It means that this question has been typed , Delivered flag, The attack is successful . The attack process is actually ordinary ctf. Some topics will first give you all the source code for you to type , This is the white box , But there are still many problems in the white box. The defense is successful, but it can't be solved flag ha-ha . You can only type some questions in black box flag coming , The successful attack will give you the source code , Let you defend .
– Defended , After you get the source code , Put the vulnerability of this problem through modifying the source code , It has been completed , The referee's poc I can't solve this problem , Even if the defense is successful .
– Abnormal defense , Explain the process of defense , You have lost the services that the website should provide , It may be over defense , Or you may have deleted the key functions . If the defense is abnormal , Be sure to reset the environment at the first time , Otherwise, points will be deducted after the end of a round , The deduction of points is particularly hurt .
defense
Prepare for the game
1. Be fully prepared before the game , Put some loopholes waf All ready , for example :
function wafrce($str){
return !preg_match("/openlog|syslog|readlink|symlink|popepassthru|stream_socket_server|scandir|assert|pcntl_exec|fwrite|curl|system|eval|assert|flag|passthru|exec|chroot|chgrp|chown|shell_exec|proc_open|proc_get_status|popen|ini_alter|ini_restore/i", $str);
}
function wafsqli($str){
return !preg_match("/select|and|\*|\x09|\x0a|\x0b|\x0c|\x0d|\xa0|\x00|\x26|\x7c|or|into|from|where|join|sleexml|extractvalue|+|regex|copy|read|file|create|grand|dir|insert|link|server|drop|=|>|<|;|\"|\'|\^|\|/i", $str);
}
function wafxss($str){
return !preg_match("/\'|http|\"|\`|cookie|<|>|script/i", $str);
}
these waf It's a little crude , It's because we should ensure that the environment of the topic can't go wrong , The topic should provide normal services .
This is very important, very important , Directly decide whether you can quickly win the defense of the problem .
2.XFTP
The file upload tool should be ready
download :
link :https://pan.baidu.com/s/1eabfwy7b8TlM-0fquWAYxw
Extraction code :g32d
3.phpstudy etc. web Environmental Science
Configure local web Environmental Science , The more convenient, the better , Namely After getting the source code, you should be able to run locally very quickly , Don't be in a hurry when it comes to the game , All of a sudden, the domain name went wrong, and all of a sudden, the database went wrong . In the game , Time is minutes !!
4. Code audit tools
Seay Source code audit system and so on .
It can play an auxiliary role , Not very important .
For the first time waf
about awdp Come on , Defense is far more important than attack , Because it is a rotation system , Each round of successful defense or attack will add corresponding points , The more successful people , The less points you add in each round , And points are cumulative ,** There are fewer questions , I won't deduct the points I got before .** So time is particularly important . Some people's questions have just appeared 5 Defense succeeded in minutes , I've been eating a problem for a whole day , Add... From the first round 500 Add to the last round 50, It adds up to thousands of points .
So our strategy is , One topic , First analyze the general knowledge points , Command execution ?sql Inject ? Upload files ? then Add... To the source code at the first time waf.
waf The form of is not limited to the example shown above , Filter keywords , It can also be directly to input things Length limit , For example, limit the length of input and execution commands to less than 2. It can achieve the purpose of repairing the loopholes without damaging the problem environment . But it also depends on the specific topic , Some topics may be shorter than 2 It's destroying web Service led to defense failure .
Pay attention to the path of file upload
This question is very important !!!
During defense, we need to upload the files to be repaired to the server , Replace the file in the original server , So we need to know the specific path of the file , But generally speaking, the topic will not be given directly , The directories of different development languages and frameworks are also different .
This time we need a small tips:
Give examples :
mv -f explorer.php /www/html/
The file we want to replace is probably not in the root directory /www/html, So this example is chicken ribs
Then look in the root directory :
mv -f explorer.php $(dirname `find / -name 'explorer.php' 2>/dev/null`)/explorer.php
use find The command looks up the root directory named explorer.php The file of , Then return his pathname (dirname)
2>/dev/null The function of is to avoid returning some wrong information , For example, the search process will return errors such as insufficient permissions .
attack
There is nothing to say about attacks , Just fight ctf, Some questions are white boxes , You have to type out some questions first flag Only then has the source code .
That's all I thought of for the moment , It took so long to record , Because I have been taking exams .
Here's a tribute to the studio bosses who took me to fight awdp!
边栏推荐
- Nebula Importer 数据导入实践
- There is a new Post-00 exam king in the testing department. I really can't do it in my old age. I have
- Yyds dry goods inventory [Gan Di's one week summary: the most complete and detailed in the whole network]; detailed explanation of MySQL index data structure and index optimization; remember collectio
- Take you ten days to easily complete the go micro service series (IX. link tracking)
- Global and Chinese market of nutrient analyzer 2022-2028: Research Report on technology, participants, trends, market size and share
- Discrete mathematics: Main Normal Form (main disjunctive normal form, main conjunctive normal form)
- Arbitrum: two-dimensional cost
- When the industrial Internet era is truly developed and improved, it will witness the birth of giants in every scene
- 【海浪建模2】三维海浪建模以及海浪发电机建模matlab仿真
- dotnet-exec 0.6.0 released
猜你喜欢
![[wave modeling 3] three dimensional random real wave modeling and wave generator modeling matlab simulation](/img/22/6d3867015811aae29b8a7df5ee3d0b.png)
[wave modeling 3] three dimensional random real wave modeling and wave generator modeling matlab simulation
Detailed explanation of multi-mode input event distribution mechanism
![Yyds dry goods inventory [Gan Di's one week summary: the most complete and detailed in the whole network]; detailed explanation of MySQL index data structure and index optimization; remember collectio](/img/e8/de158982788fc5bc42f842b07ff9a8.jpg)
Yyds dry goods inventory [Gan Di's one week summary: the most complete and detailed in the whole network]; detailed explanation of MySQL index data structure and index optimization; remember collectio

Innovation leads the direction. Huawei Smart Life launches new products in the whole scene

26.2 billion! These universities in Guangdong Province have received heavy support
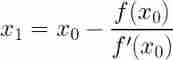
Visual explanation of Newton iteration method
Playwright recording
揭露测试外包公司,关于外包,你或许听到过这样的声音
Take you ten days to easily complete the go micro service series (IX. link tracking)
Basic operation of database and table ----- phased test II
随机推荐
Delaying wages to force people to leave, and the layoffs of small Internet companies are a little too much!
User login function: simple but difficult
Database postragesql client connection default
创新引领方向 华为智慧生活全场景新品齐发
全网最全正则实战指南,拿走不谢
What you learned in the eleventh week
实战模拟│JWT 登录认证
Which financial products with stable income are good
Global and Chinese market of optical densitometers 2022-2028: Research Report on technology, participants, trends, market size and share
“薪资倒挂”、“毕业生平替” 这些现象说明测试行业已经...
107. SAP UI5 OverflowToolbar 容器控件以及 resize 事件处理的一些细节介绍
Jcenter () cannot find Alibaba cloud proxy address
微信小程序:全网独家小程序版本独立微信社群人脉
Robley's global and Chinese markets 2022-2028: technology, participants, trends, market size and share Research Report
抓包整理外篇——————状态栏[ 四]
POAP:NFT的采用入口?
Redis master-slave replication cluster and recovery ideas for abnormal data loss # yyds dry goods inventory #
微信小程序:星宿UI V1.5 wordpress系统资讯资源博客下载小程序微信QQ双端源码支持wordpress二级分类 加载动画优化
Introduction to redis (1)
RB technology stack