当前位置:网站首页>[how to connect the network] Chapter 5 explore the server
[how to connect the network] Chapter 5 explore the server
2022-07-02 17:40:00 【Currybeefer】
1.Web Where the server is deployed
Web Servers can be deployed in the company , It can also be directly placed in the data center managed by the network operator , Or directly rent the server provided by the operator .
Put it in the company , The server can be accessed directly from the Internet . In this case , Network packet through the nearest POP Router in 、 After accessing the network and server-side router , Directly to the server . In the past, such server deployment methods were very common , But now it's not the mainstream way . There are several reasons . The first reason is IP Insufficient address . This approach needs to be for all devices in the company network , Including server and client computers , All assigned their own public addresses . However, now the public address is not enough , Therefore, it is unrealistic to adopt this method .
Put it in the data center directly with NOC Connect , Or the hub with operators , That is to say IX Direct connection . In this way, the access speed will be very fast , Besides , Data centers are generally located in buildings with seismic structures , It also has autonomous power generation equipment , And implement 24 Hourly access control , It can be said that it has higher security than putting it in the company . Besides , The data center not only provides a place for servers , It also provides various additional services , Such as server working state monitoring 、 Firewall configuration and operation 、 Illegal intrusion monitoring , From this point of view , Its security is also higher .
2. Structure and principle of firewall
The basic principle of firewall is to allow only packets sent to specific applications in specific servers to pass , Then shield other packages . To do this , The rules of packet filtering must be set correctly .


The firewall can set the rules of packet filtering according to the items listed in the above figure ,** The firewall of packet filtering can be based on the receiver IP Address 、 The sender IP Address 、 Slogan of receiver 、 Sender's slogan 、 Control bits and other information to determine whether a packet is allowed to pass .** Here's the picture
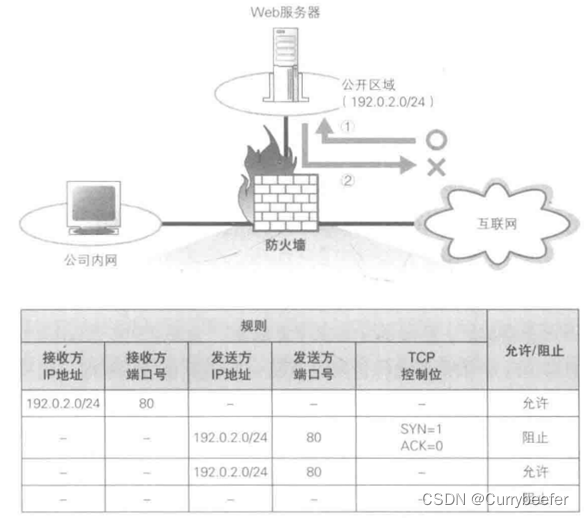
hypothesis Web The server will cause downtime when receiving a package with specific data . But the firewall only cares about the beginning and end of the package , So even if the package contains specific data , The firewall can't find , So the bag was released . then , When the bag arrives Web Server time , It will cause server downtime .
There are two ways to deal with this situation . The root of the problem lies in Web Of the server program Bug, So fix Bug Preventing downtime is one way .
Another way is to deploy devices or software outside the firewall to check the contents of packages and prevent harmful packages . Of course , Even this method is not perfect , Because whether the contents of the package are risky , By Web Does the server have Bug Decisive , So when there is potential in the server program Bug And has not yet been discovered , We can't judge the risks in the package , Can't stop such a package .
4. How to balance the load of the server
When the number of visits to the server goes up , It is effective to increase the bandwidth of the server line , But not all problems can be solved when the network becomes faster . High speed lines transmit a large number of network packets , This will cause the performance of the server to fall behind .
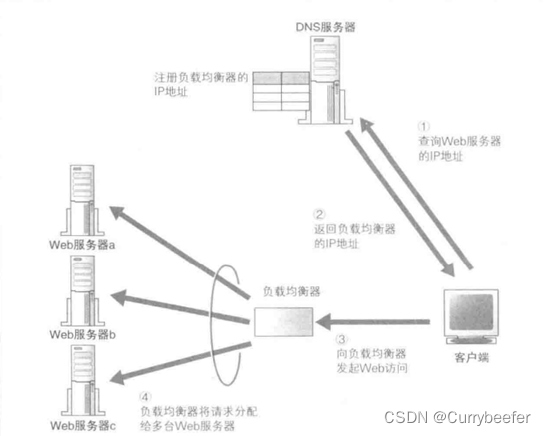
under these circumstances , Using multiple servers to share the load is more effective . This architecture is collectively referred to as distributed architecture , There are several ways to share the load , The simplest way is to use multiple Web The server , Reduce the number of visits per server . Suppose now we have 3 Servers , Then the traffic of each server will be reduced to one third , The load is reduced . Use this method , There must be a mechanism to allocate the requests sent by the client to each server . There are many specific methods , The simplest one is through DNS Server to assign . When accessing the server , The client needs to report to DNS The server queries the server IP Address , If in DNS Fill in multiple records with the same name in the server , Then every time you query DNS The server will return different IP Address . In this way, each server can be accessed equally .

besides , You can also use a load balancer to achieve load balanced access .. When using a load balancer , First use the load balancer IP Address substitution Web The actual address of the server is registered to DNS Server . Suppose there is a domain name www.lab.glasscom.com, We will match this domain name with IP The address is set to... Of the load balancer IP Address and register to DNS Server . therefore , The client will think of the load balancer as a Web The server , And send it a request , The load balancer then decides which one to forward the request to Web The server . The key points here are self-evident , That is how to determine which one to forward the request to Web The server .
5. Use the cache server to share the load
In addition to using multiple computers with the same function Web The server shares the load , There is another way , It is to divide the whole system into different servers according to functions , Such as Web The server 、 database server . The cache server is a way to share the load by function .
Cache server is a server that caches data through proxy mechanism . The agent is between Web Between server and client , Have right Web Server access for transfer . When transferring , It can be Web The data returned by the server is saved in the disk , And can replace Web The server returns the data in the disk to the client . This kind of saved data is called cache , Cache server refers to such functions .
Web The server needs to check the URL and access rights , And the internal operation process of filling data on the page , Therefore, it takes a long time to return the page data to the client . relatively , The cache server only needs to read the data saved on the disk and send it to the client , So you can compare Web Server returns data faster . Of course, the cache is temporary , Need to follow web Updated by .
The cache server is the same as the load balancer , Need to replace Web Server is registered to DNS Server . Then the client will send to the cache server HTTP The request message . At this time , The cache server will receive the request message , This receive operation and Web The servers are the same . Simply put, create a socket to wait for a connection , Perform connection operation when the client connects , Then receive the request message sent by the client . From the client side , The cache server is equivalent to Web The server . Next , The cache server will check the contents of the request message , See if the requested data has been saved in the cache . If kept , Then return directly , Otherwise, the cache server will send to the target as the client Web Server sends request message . in other words , It will first create a socket , Then connect to Web Socket for server , And send a request message .

边栏推荐
- Niuke js3 separator
- IPtables中SNAT、DNAT和MASQUERADE的含义
- Solution to the problem that the easycvr kernel of intelligent video analysis platform cannot be started as a service
- Listing of chaozhuo Aviation Technology Co., Ltd.: raising 900million yuan, with a market value of more than 6billion yuan, becoming the first science and technology innovation board enterprise in Xia
- si446使用记录(一):基本资料获取
- SSB threshold_ SSB modulation "suggestions collection"
- chrome浏览器快速访问stackoverflow
- MATLAB中nexttile函数使用
- 书包网小说多线程爬虫[通俗易懂]
- VirtualLab基础实验教程-7.偏振(1)
猜你喜欢
![List summation [dummy+ tail interpolation + function processing list reference common pit]](/img/08/30e8ca2376104d648a82dca8a72c42.png)
List summation [dummy+ tail interpolation + function processing list reference common pit]

Eye of depth (III) -- determinant of matrix

Si446 usage record (II): generate header files using wds3
USB interface powered Bluetooth color light strip controller

RK1126平台项目总结
Microservice architecture practice: using Jenkins to realize automatic construction

Simple linear programming problem

Sword finger offer 25 Merge two sorted linked lists

easyswoole3.2重启不成功
VirtualLab基础实验教程-7.偏振(1)
随机推荐
Microservice architecture practice: Construction of highly available distributed file system fastdfs architecture
关于我
SAP Commerce Cloud Storefront 框架选型:Accelerator 还是 Spartacus?
Alibaba Tianchi SQL learning notes - Day3
什么是敏捷开发流程
[非线性控制理论]7_High gain and High Frequency
Uniapp H5 page calls wechat payment
Si446 usage record (I): basic data acquisition
Introduction to Hisilicon hi3798mv100 set top box chip [easy to understand]
Schoolbag novel multithreaded crawler [easy to understand]
The construction of scalable distributed database cluster and the partition design of oneproxy sub database
POJ - 1458 Common Subsequence(最长公共子序列)
阿里天池SQL学习笔记——DAY3
简单线性规划问题
每日一题——“水仙花数”
CEPH principle
Visibilitychange – refresh the page data when the specified tab is visible
ssb门限_SSB调制「建议收藏」
选择 SAP Spartacus 作为 SAP Commerce Cloud Storefront 实现框架的五个理由
How openharmony starts fa (local and remote)