当前位置:网站首页>[buuctf.reverse] 159_ [watevrCTF 2019]Watshell
[buuctf.reverse] 159_ [watevrCTF 2019]Watshell
2022-07-06 04:46:00 【Shi Shi Shi Shi Shi Shi Shi Shi Shi Shi Shi Shi Shi Shi Shi Shi】
This question should be called c Introduction to language
__int64 __fastcall main(int a1, char **a2, char **a3)
{
int v4; // [rsp+Ch] [rbp-3A4h]
const char *nptr; // [rsp+18h] [rbp-398h]
char *s1; // [rsp+20h] [rbp-390h]
FILE *stream; // [rsp+28h] [rbp-388h]
char v8[32]; // [rsp+30h] [rbp-380h] BYREF
char v9[32]; // [rsp+50h] [rbp-360h] BYREF
__int64 v10[25]; // [rsp+70h] [rbp-340h] BYREF
char delim[2]; // [rsp+13Eh] [rbp-272h] BYREF
char v12[80]; // [rsp+140h] [rbp-270h] BYREF
char s[504]; // [rsp+190h] [rbp-220h] BYREF
unsigned __int64 v14; // [rsp+388h] [rbp-28h]
v14 = __readfsqword(0x28u);
signal(14, handler);
alarm(0x3Cu);
strcpy(delim, " ");
v4 = 0;
sub_13A5();
sub_157F();
puts("Welcome to watshell, we ofcourse use our own super secure cryptographic functions to ensure user privacy!");
printf("%s", "Command: ");
fflush(stdout);
fgets(s, 500, stdin);
strlen(s);
for ( nptr = strtok(s, delim); nptr && v4 != 25; nptr = strtok(0LL, delim) )// Space separated numbers
v10[v4++] = atol(nptr);
sub_EB7(v8, v9);
s1 = (char *)sub_11AF(v10, 8 * (v4 + 1), (__int64)(8 * (v4 + 1)) >> 63, v9);
if ( !strcmp(s1, "give_me_the_flag_please") )
{
stream = fopen("/home/ctf/flag.txt", "r");
if ( !stream )
printf("The file does not exist!");
fgets(v12, 74, stream);
printf("Alright, alright %s\n", v12);
fclose(stream);
}
free(s1);
return 0LL;
}stay main Directly separate the input with spaces , Then convert to integer . It uses a function that is not commonly used but is introductory strok, This function will space ( Separator ) The position of is changed to 0 And return the pointer of the previous paragraph each time .
then sub_EB7() Can't understand , But because the input content is not used , So it must be a fixed value , use gdb Follow here and you will get the result .
And then call 11AF To encrypt , Process the integer just transferred one by one
for ( i = 0uLL; size >> 3 > i; i += 1uLL )
ptr[i] = sub_DC3(*(_QWORD *)(8 * i + a1), a4[2], *a4);// encryption pow(n,0x71,0x8f)sub_DC3 It is also an entry-level Algorithm : Fast power reduction method
__int64 __fastcall sub_DC3(__int64 a1, __int64 a2, __int64 a3)
{
__int64 result; // rax
__int64 v4; // [rsp+18h] [rbp-8h]
if ( a1 < 0 || a2 < 0 || a3 <= 0 )
exit(1);
v4 = a1 % a3;
if ( !a2 )
return 1LL;
if ( a2 == 1 )
return a1 % a3;
if ( (a2 & 1) == 0 )
return sub_DC3(v4 * v4 % a3, a2 / 2, a3) % a3;
result = a2 % 2;
if ( a2 % 2 == 1 )
return v4 * sub_DC3(v4, a2 - 1, a3) % a3;
return result;
}The method of program encryption is very clear : You are required to enter a string of numbers separated by spaces , Then each number is Rsa encryption (e:0x71,n:0x8f) Get a string "give_me_the_flag_please" Then the backstage will flag Give it out .
The sparrow is all ready .
边栏推荐
- 11. Intranet penetration and automatic refresh
- Dry goods collection | Vulkan game engine video tutorial
- [NOIP2009 普及组] 分数线划定
- Basic knowledge and examples of binary tree
- Postman前置脚本-全局变量和环境变量
- Visio draw fan
- The underlying structure of five data types in redis
- 树莓派3.5寸屏幕白屏显示连接
- coreldraw2022新版本新功能介绍cdr2022
- Introduction of several RS485 isolated communication schemes
猜你喜欢
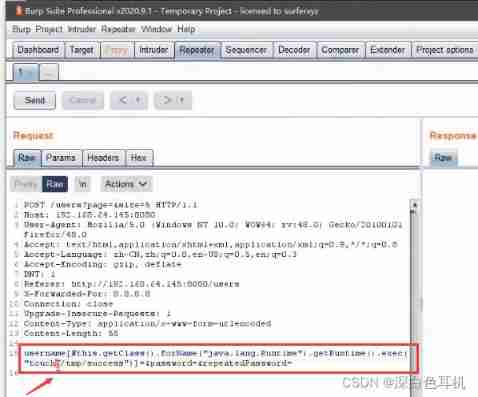
Vulnerability discovery - vulnerability probe type utilization and repair of web applications
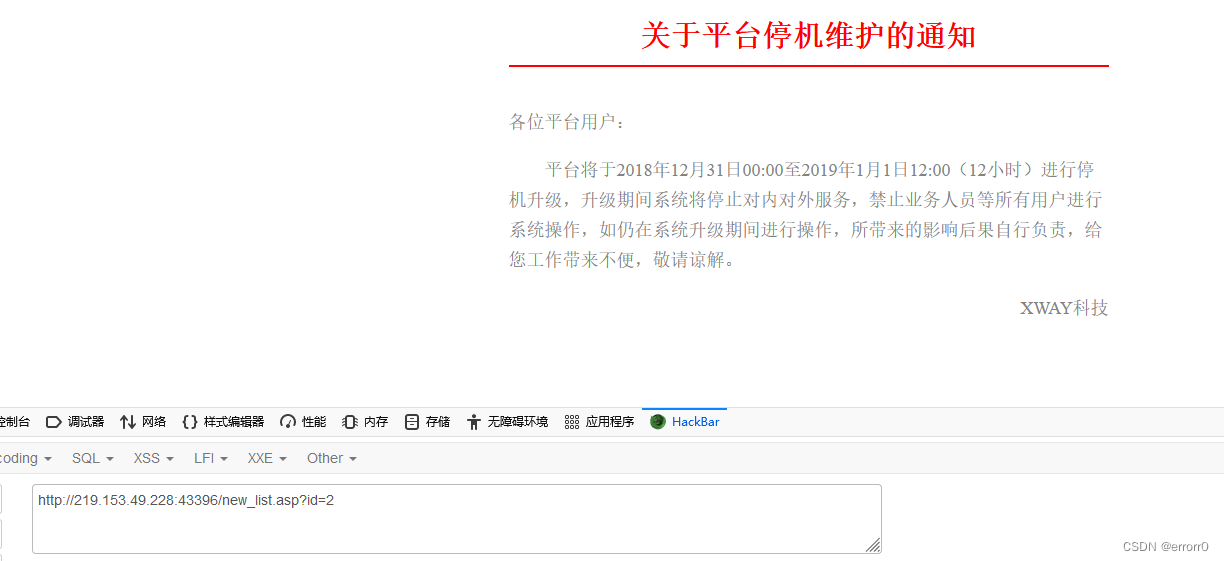
SQL注入漏洞(MSSQL注入)
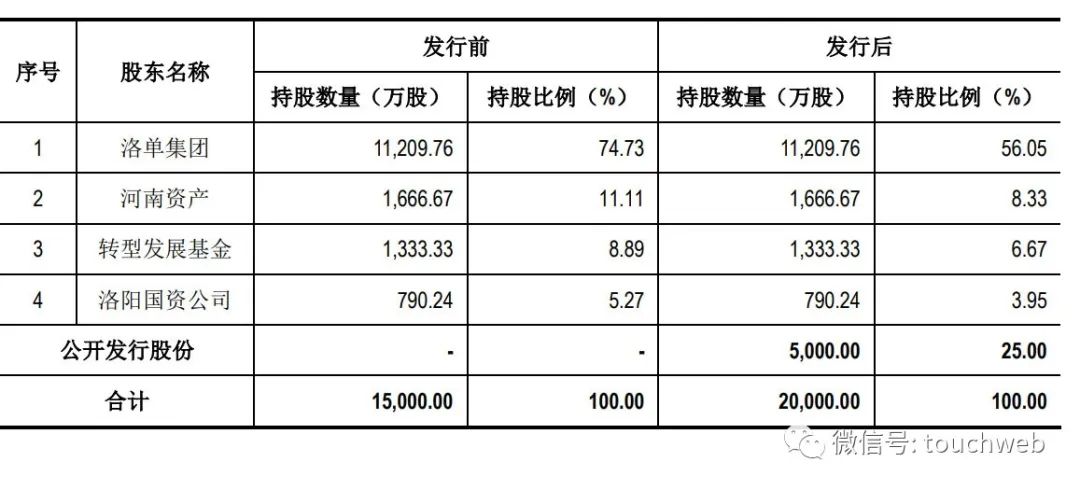
麥斯克電子IPO被終止:曾擬募資8億 河南資產是股東

L'introduction en bourse de MSK Electronics a pris fin: 800 millions de RMB d'actifs de Henan étaient des actionnaires
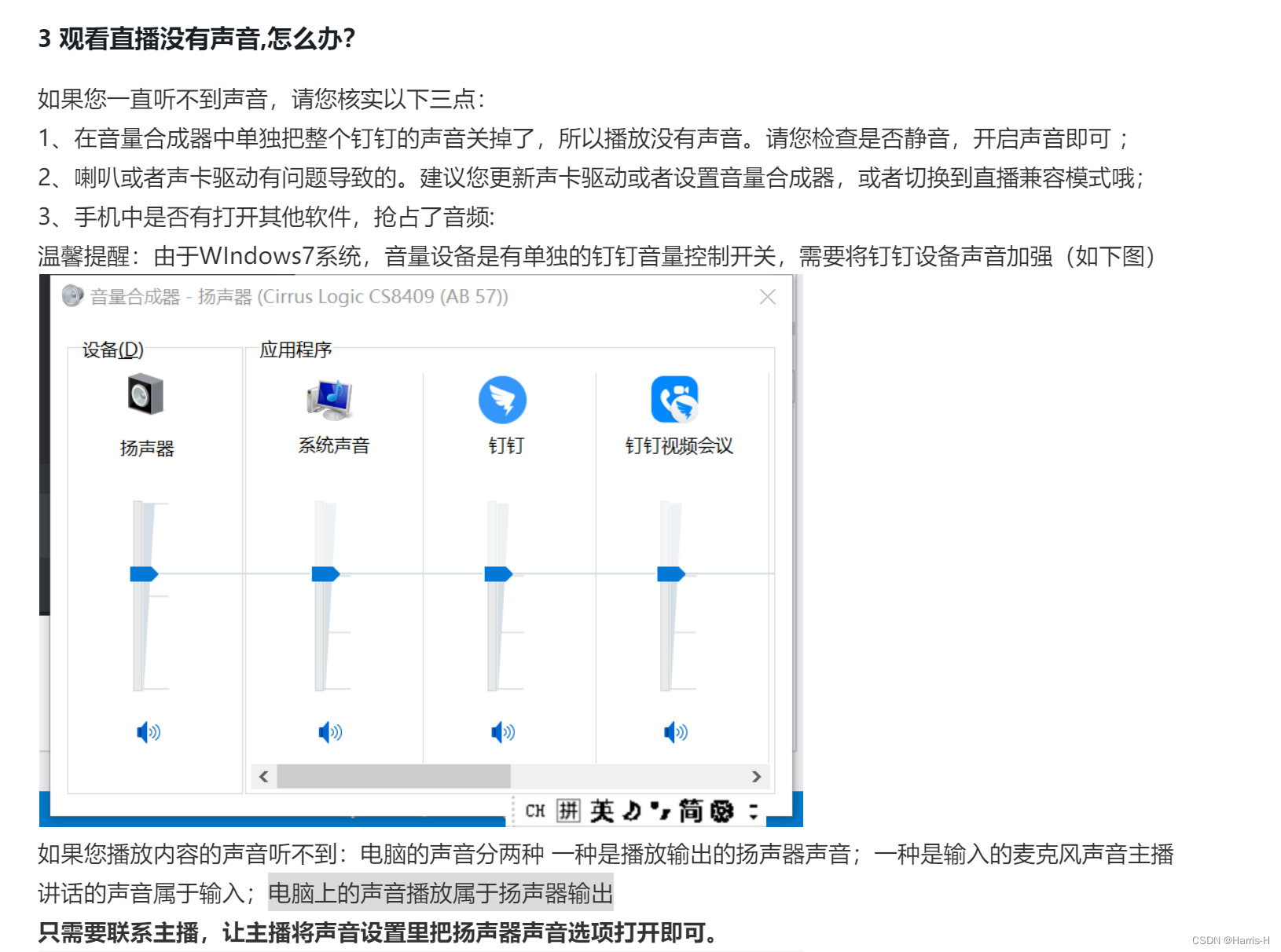
How does computer nail adjust sound
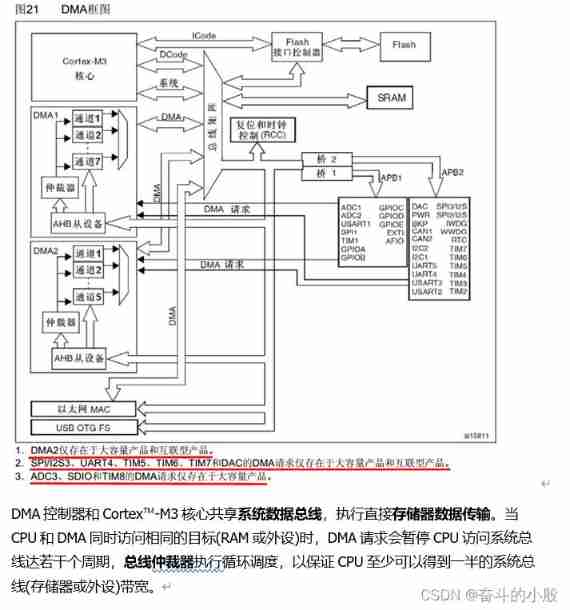
DMA use of stm32

Uva1592 Database

SQL injection vulnerability (MSSQL injection)
CADD course learning (8) -- virtual screening of Compound Library

Bill Gates posted his 18-year-old resume and expected an annual salary of $12000 48 years ago
随机推荐
Can CDC pull the Oracle table in full
Implementation of knowledge consolidation source code 2: TCP server receives and processes half packets and sticky packets
[NOIP2008 提高组] 笨小猴
ORM aggregate query and native database operation
Can Flink SQL read multiple topics at the same time. How to write in with
Case of Jiecode empowerment: professional training, technical support, and multiple measures to promote graduates to build smart campus completion system
也算是學習中的小總結
Finance online homework
How to realize automatic playback of H5 video
[FreeRTOS interrupt experiment]
SQL injection vulnerability (MSSQL injection)
Redis - redis in action - redis actual combat - actual combat Chapter 1 - SMS login function based on redis - redis + token shared session application - with code
麦斯克电子IPO被终止:曾拟募资8亿 河南资产是股东
How does computer nail adjust sound
麥斯克電子IPO被終止:曾擬募資8億 河南資產是股東
我想问一下 按照现在mysql-cdc的设计,全量阶段,如果某一个chunk的binlog回填阶段,
Supreme Court, judgment standard of divorce cases
拉格朗日插值法
Use sentinel to interface locally
Visio draws Tai Chi