当前位置:网站首页>2022 information security engineer examination outline
2022 information security engineer examination outline
2022-07-07 03:07:00 【weixin_ forty-six million six hundred and nineteen thousand two】
Many candidates are ready to sign up 2022 Information security engineer examination , We have sorted out the outline of the soft exam for information security engineers , For your reference .
The information security engineer examination outline is in 2020 Revised in , Candidates can buy a new version of the exam outline for review , The following is a summary of the exam outline for information security engineers in previous years , For your reference .
One 、 Test instructions
1. Test objectives
Qualified personnel who pass this examination can master the basic knowledge and technical principles of network information security ; According to relevant laws and regulations on network information security and business security requirements , Be able to plan 、 Design information system security scheme , Be able to configure and maintain common network security equipment and systems ; Be able to monitor and analyze the network security risks of information systems , And give rectification suggestions for network security risks ; Be able to assist relevant departments in network security audit and network security incident investigation of the unit's information system ; Be able to carry out emergency response to network information security incidents ; Have the actual working ability and professional level of Engineers .
2. Examination requirements
(1) Be familiar with the confidentiality of network information security 、 Usability 、 Basic knowledge such as integrity , Understand the concept of personal information privacy protection ;
(2) Familiar with identity authentication of network information system 、 Access control 、 Log audit 、 Working mechanism and technical principle of safety monitoring ;
(3) Master the password system 、 cryptographic algorithm 、 Password threat 、 Basic knowledge and technology such as password Application , Familiar with data encryption 、SSL、VPN、 digital signature 、PKI Wait for password application to work ;
(4) Master the working principle of network security threats , Understand port scanning 、 Password cracking 、 out of buffer 、 Computer virus 、 Internet worms 、 Trojan horse 、 Botnet 、 Website counterfeiting 、 Denial of service 、 Network sniffer 、SQL Inject knowledge about network security threats such as ;
(5) Master firewall 、 Vulnerability scanning 、VPN、 Physical isolation 、 Intrusion detection 、 Intrusion Prevention 、 System security enhancements 、 Security audit 、 Trusted computing 、 Privacy protection 、 Digital watermark 、 Security risk assessment 、 Principles and applications of network security technologies such as security emergency response ;
(6) Familiar with the working mechanism of network information security risk assessment , Understand the physical environment 、 Computer 、 operating system 、 database 、 Application system 、 Website 、 A smart phone 、 Internet 、 Mobile application 、 Cloud computing 、 The Internet of things 、 Industrial control 、 big data 、 Smart devices 、 Security risks in areas such as machine learning , Be able to propose network information security technology and management solutions , Be able to understand, analyze and evaluate the product technical solutions of network security manufacturers ;
(7) Be able to read network information security level protection standards and related specifications , Be able to understand the requirements of relevant technical standards ;
(8) Be able to read and understand laws and regulations related to network information security 、 Management regulations ;
(9) Proficient in reading and correctly understanding scientific and technical English materials in the field of network information security , Understand the Internet of things 、 Cloud computing 、 Artificial intelligence 、 Network security risks of emerging technologies such as big data .
3. Examination subject setting
(1) Basic knowledge and technology of network information security , The examination time is 150 minute , written examination , choice question ;
(2) Network information security engineering and comprehensive application practice , The examination time is 150 minute , written examination , Q & A questions .
Two 、 Examination scope
Examination subjects 1: Basic knowledge and technology of network information security
1. Overview of network information security
1.1 Basic attributes of network information security
1.2 Current situation and problems of network information security
1.3 Objectives and functions of network information security
1.4 Basic technical requirements of network information security
1.5 Contents and methods of network information security management
1.6 Legal and policy documents on network information security
1.7 Network information security technology information acquisition
2. Principles and common methods of network attack
2.1 Overview of cyber attacks
2.2 The general process of network attack
2.3 Common techniques and methods of network attack
2.4 Hacker commonly used software
2.5 Network attack cases
3. Basic theory of cryptography
3.1 Overview of cryptography
3.2 Cryptosystem classification
3.3 Common cryptographic algorithms
3.4 Hash Functions and digital signatures
3.5 Password management and digital certificate
3.6 Security protocols
3.7 Cryptography network security applications
4. Network security system and network security model
4.1 Overview of network security system
4.2 Related security models of network security system
4.3 Network security system construction principles and security strategies
4.4 Network security system framework composition and construction content
4.5 Network security system construction reference case
5. Physical and environmental security technology
5.1 Physical security concepts and requirements
5.2 Security analysis and protection of physical environment
5.3 Safety analysis and protection of computer room
5.4 Security analysis and protection of network communication lines
5.5 Equipment physical safety analysis and protection
5.6 Security analysis and protection of storage media
6. Principle and application of certification technology
6.1 Certification overview
6.2 Certification type and certification process
6.3 Certification techniques and methods
6.4 Certification of main technical indicators and products
6.5 Application of certification technology
7. Principle and application of access control technology
7.1 Overview of access control
7.2 Access control model
7.3 Access control type
7.4 Design and implementation of access control policy
7.5 Access control process and security management
7.6 Main technical indicators and products of access control
7.7 Application of access control technology
8. Firewall technology principle and Application
8.1 Firewall Overview
8.2 Firewall type and Implementation Technology
8.3 Main technical indicators and products of firewall
8.4 Application of firewall technology
9.VPN Technical principle and application
9.1 VPN summary
9.2 VPN Types and implementation techniques
9.3 VPN Main technical indicators and products
9.4 VPN Technology application
10. Principle and application of Intrusion Detection Technology
10.1 Intrusion detection overview
10.2 Intrusion Detection Technology
10.3 Composition and classification of intrusion detection system
10.4 Main technical indicators and products of intrusion detection system
10.5 Application of intrusion detection system
11. Principle and application of network physical isolation technology
11.1 Overview of network physical isolation
11.2 Network physical isolation system and type
11.3 Network physical isolation mechanism and Implementation Technology
11.4 Main technical indicators and products of network physical isolation
11.5 Network physical isolation Application
12. Principles and application of network audit technology
12.1 Overview of network security audit
12.2 Composition and type of network security audit system
12.3 Network security audit mechanism and implementation technology
12.4 Main technical indicators and products of network security audit
12.5 Network security audit application
13. Principle and application of network security vulnerability protection technology
13.1 Overview of network security vulnerabilities
13.2 Classification and management of network security vulnerabilities
13.3 Network security vulnerability scanning technology and application
13.4 Network security vulnerability disposal technology and application
13.5 Main technical indicators and products of network security vulnerability protection
14. Principle of malicious code prevention technology
14.1 Overview of malicious code
14.2 Computer virus analysis and protection
14.3 Trojan horse analysis and protection
14.4 Analysis and protection of network worms
14.5 Botnet analysis and protection
14.6 Other malicious code analysis and protection
14.7 Main technical indicators and products of malicious code protection
14.8 Application of malicious code protection technology
15. Principle and application of network security active defense technology
15.1 Intrusion blocking technology and application
15.2 Software whitelist technology and application
15.3 Network traffic cleaning technology and application
15.4 Trusted computing technology and application
15.5 Digital watermarking technology and application
15.6 Network attack trap technology and application
15.7 Intrusion tolerance and system survival technology and application
15.8 Privacy protection technology and application
15.9 The development trend of network security frontier technology
16. Principle and application of network security risk assessment technology
16.1 Overview of network security risk assessment
16.2 Network security risk assessment process
16.3 Technical methods and tools for network security risk assessment
16.4 Network security risk assessment process and work content
16.5 Application of network security risk assessment technology
17. Principle and application of network security emergency response technology
17.1 Overview of network security emergency response
17.2 Establishment and working mechanism of network security emergency response organization
17.3 Content and type of network security emergency response plan
17.4 Common network security emergency scenarios and handling processes
17.5 Network security emergency response technology and common tools
17.6 Network security emergency response reference case
18. Network security evaluation technology and standards
18.1 Overview of network security evaluation
18.2 Type of network security evaluation
18.3 Network security evaluation process and content
18.4 Network security evaluation technology and tools
18.5 Network security evaluation quality management and Standards
19. Operating system security
19.1 Operating system security overview
19.2 Windows Operating system security analysis and protection
19.3 UNIXLinux Operating system security analysis and protection
19.4 Security analysis and protection of domestic operating system
20. Database system security
20.1 Database Security Overview
20.2 Database security mechanism and implementation technology
20.3 Oracle Database security analysis and protection
20.4 MS SQL Database security analysis and protection
20.5 MySQL Database security analysis and protection
20.6 Security analysis and protection of domestic database
21. Network device security
21.1 Overview of network equipment security
21.2 Security mechanism and implementation technology of network equipment
21.3 Network equipment security enhancement technology and method
21.4 Common vulnerabilities and solutions of network devices
- Professional English for network information security
Examination subjects 2∶ Network information security engineering and comprehensive application practice
1. Network security risk assessment and demand analysis
1.1 Network security risk assessment practice
1.2 Network security data collection and analysis
2. Common scheme design of network security
2.1 Operating system security scheme design
2.2 Design of network equipment and communication security scheme
2.3 Security scheme design of computing environment
2.4 Application and data security scheme design
2.5 Network security management scheme design
3. Deployment and use of network security equipment
3.1 Firewall deployment and use
3.2 IDS/IPS Deployment and use
3.3 Deployment and use of gateways
3.4 VPN Deployment and use
3.5 Vulnerability scanning deployment and use
4. Network information system security configuration and management
4.1 Operating system security configuration and management
4.2 Database system security configuration and management
4.3 Website system security configuration and management
4.4 Network device security configuration and management
5. Website security needs analysis and security protection engineering
5.1 Website security threats and needs analysis
5.2 Apache Security analysis and enhancement
5.3 IIS Security analysis and enhancement
5.4 Web Application vulnerability analysis and protection
5.5 Website security protection mechanism and technical scheme
5.5.1 Website component security reinforcement
5.5.2 Website attack protection and security monitoring
6. Cloud computing security requirements analysis and security protection engineering
6.1 Cloud computing security threats and needs analysis
6.1.1 Cloud computing security threats
6.1.2 Cloud computing security requirements
6.2 Cloud computing security protection mechanism and technical scheme
6.2.1 Cloud computing security level protection framework
6.2.2 Cloud computing security protection
6.2.3 Cloud computing security management
6.2.4 Cloud computing security operation and maintenance
6.3 Cloud computing security protection case analysis
7. Industrial control safety demand analysis and safety protection engineering
7.1 Security threat and demand analysis of industrial control system
7.2 Safety protection mechanism and technology of industrial control system
7.2.1 Physical and environmental safety protection
7.2.2 Security zoning and boundary protection
7.2.3 Identity authentication and access control
7.24 Remote access security
7.2.5 Safety reinforcement of industrial control system
7.2.6 Industrial control safety audit
7.2.7 Malicious code prevention
7.2.8 Industrial control data security
7.2.9 Industrial control safety monitoring and emergency response
7.2.10 Industrial control safety management
7.2.11 Typical product technology of industrial control safety
8. Mobile application security requirement analysis and security protection engineering
8.1 Mobile application security threat and demand analysis
8.2 Android System security and protection mechanism
8.3 iOS System security and protection mechanism
8.4 Mobile application security protection mechanism and technical scheme
8.4.1 Mobile application App Safety risk
8.4.2 Mobile application App Safety reinforcement
84.3 Mobile application App Safety inspection
8.5 Mobile application security comprehensive application case analysis
9. Big data security demand analysis and security protection engineering
9.1 Big data security threat and demand analysis
9.1.1 Big data security threat analysis
9.1.2 Big data security requirements analysis
9.2 Big data security protection mechanism and technical scheme
9.2.1 Big data self security protection technology
9.2.2 Big data platform security protection technology
9.2.3 Big data service security protection technology
9.2.4 Big data privacy security protection technology
9.2.5 Big data operation security protection technology
9.2.6 Big data security management and Standards
9.3 Big data security protection case analysis
边栏推荐
- 又一百万量子比特!以色列光量子初创公司完成1500万美元融资
- Redis Getting started tutoriel complet: positionnement et optimisation des problèmes
- centerX: 用中国特色社会主义的方式打开centernet
- MySQL提升大量数据查询效率的优化神器
- Redis getting started complete tutorial: replication configuration
- Lingyun going to sea | yidiantianxia & Huawei cloud: promoting the globalization of Chinese e-commerce enterprise brands
- Static proxy of proxy mode
- 换个姿势做运维!GOPS 2022 · 深圳站精彩内容抢先看!
- Oracle中日期的使用方法实例
- Redis入门完整教程:客户端案例分析
猜你喜欢
Error: could not find a version that satisfies the requirement xxxxx (from versions: none) solutions
Use of promise in ES6
Qt蓝牙:QBluetoothDeviceInfo
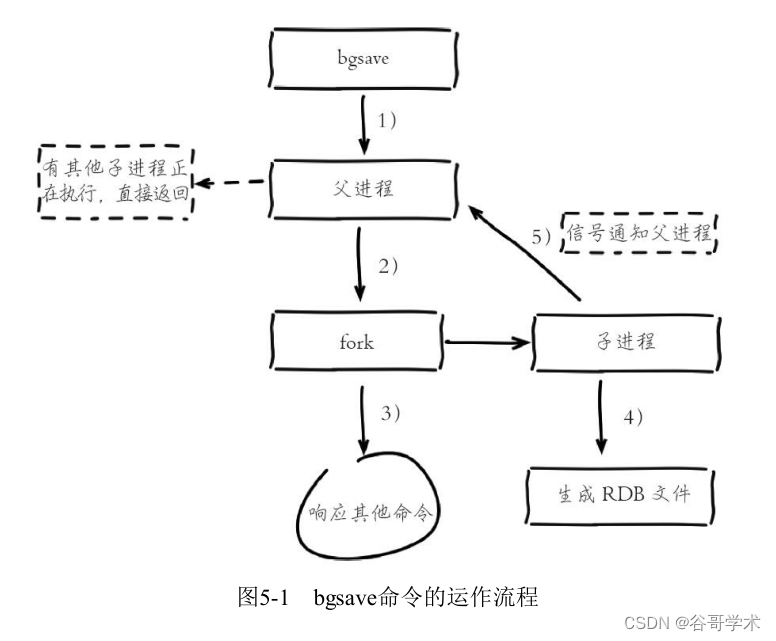
Redis入门完整教程:RDB持久化
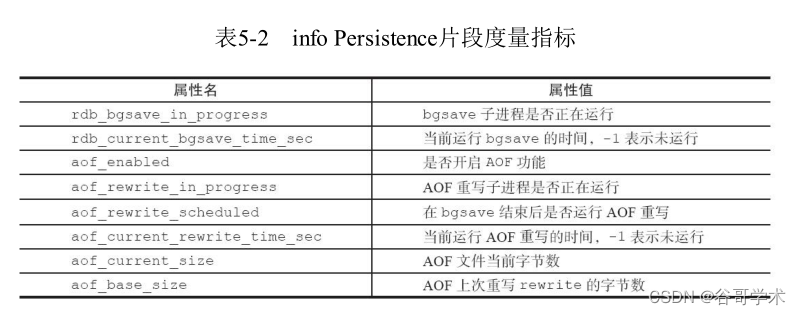
Redis入门完整教程:问题定位与优化
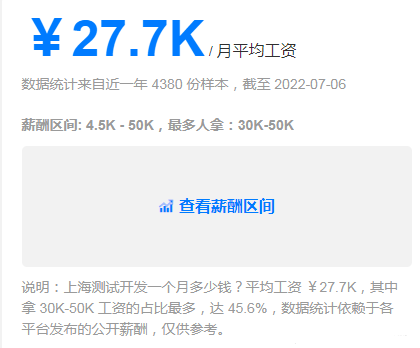
The annual salary of general test is 15W, and the annual salary of test and development is 30w+. What is the difference between the two?

Es6中Promise的使用
Dotconnect for DB2 Data Provider
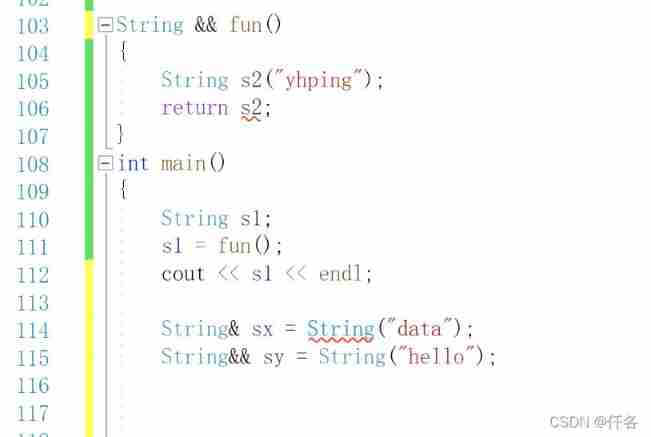
Left value, right value

Detailed explanation of 19 dimensional integrated navigation module sinsgps in psins (time synchronization part)
随机推荐
惯导标定国内外研究现状小结(删减版)
Code line breaking problem of untiy text box
Redis入门完整教程:问题定位与优化
What management points should be paid attention to when implementing MES management system
知识图谱构建全流程
Unity使用MaskableGraphic画一条带箭头的线
Cloud Mail . NET Edition
Metaforce force meta universe fossage 2.0 smart contract system development (source code deployment)
PSINS中19维组合导航模块sinsgps详解(初始赋值部分)
Electrical engineering and automation
mos管實現主副電源自動切換電路,並且“零”壓降,靜態電流20uA
巴比特 | 元宇宙每日必读:IP授权是NFT的破圈之路吗?它的难点在哪里?Holder该如何选择合作平台?...
How to write test cases for test coupons?
What are the characteristics of the operation and maintenance management system
wzoi 1~200
[node learning notes] the chokidar module realizes file monitoring
又一百万量子比特!以色列光量子初创公司完成1500万美元融资
尚硅谷JVM-第一章 类加载子系统
The whole process of knowledge map construction
Planning and design of double click hot standby layer 2 network based on ENSP firewall