当前位置:网站首页>Brief introduction to tcp/ip protocol stack
Brief introduction to tcp/ip protocol stack
2022-07-05 05:34:00 【Raise items】
List of articles
Network layering
To the network layered , It is convenient to study computer network technology . The industry standard computer network layered design includes the following three . When we discuss network protocols , The reference is four layers Model .
| OSI Seven layer model | TCP/IP Five layer model | TCP/IP Four layer model |
| application layer | application layer | application layer |
| The presentation layer | ||
| The session layer | ||
| Transport layer | Transport layer | Transport layer |
| The network layer | The network layer | The network layer |
| Data link layer | Data link layer | Network interface layer |
| The physical layer | The physical layer |
The link layer 、 Data link layer and network interface layer are a concept .
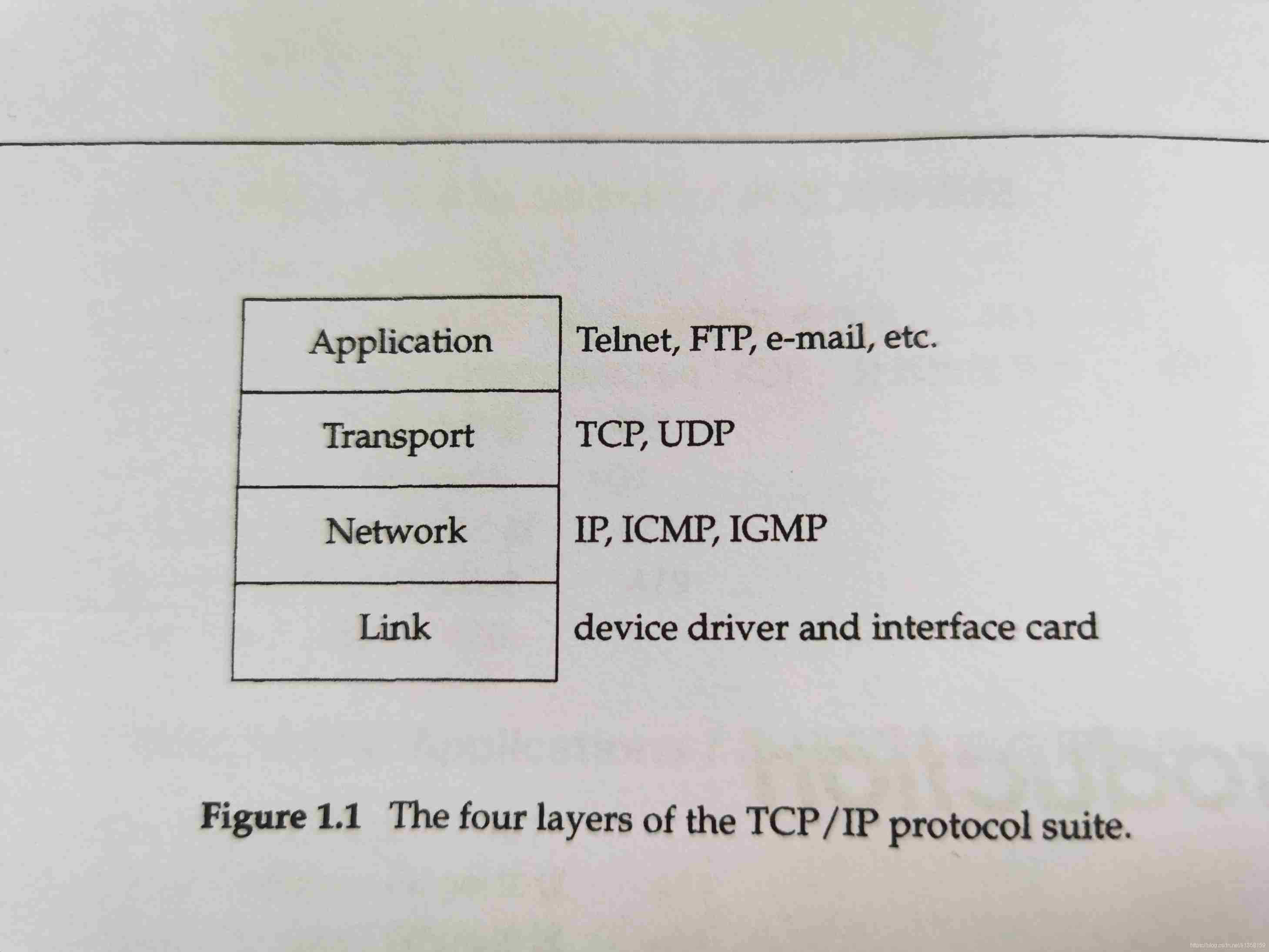
The link layer
The link layer includes Device drivers and Network interface card , They jointly deal with the physical interface Hardware details .
Device drivers are software , Part of the operating system .
Network interface card is hardware , Also known as network card 、 network adapter , And network transmission media ( Twisted pair 、 Coaxial cable 、 Optical fiber, etc ) Connected to a .
The link layer = network card + Network card driver
Link layer protocols include :ARP、RARP、 Ethernet protocol
The network layer
Network layer processing is different host Route and forward messages in the network .
Network layer protocols include :IP、ICMP、IGMP
Transport layer
The transport layer is for different hosts Applications Provide data flow interaction .
The transport layer protocol has :TCP、UDP
application layer
The application layer handles the details of a particular application .
Application layer protocols include :Telnet、FTP、SMTP、SNMP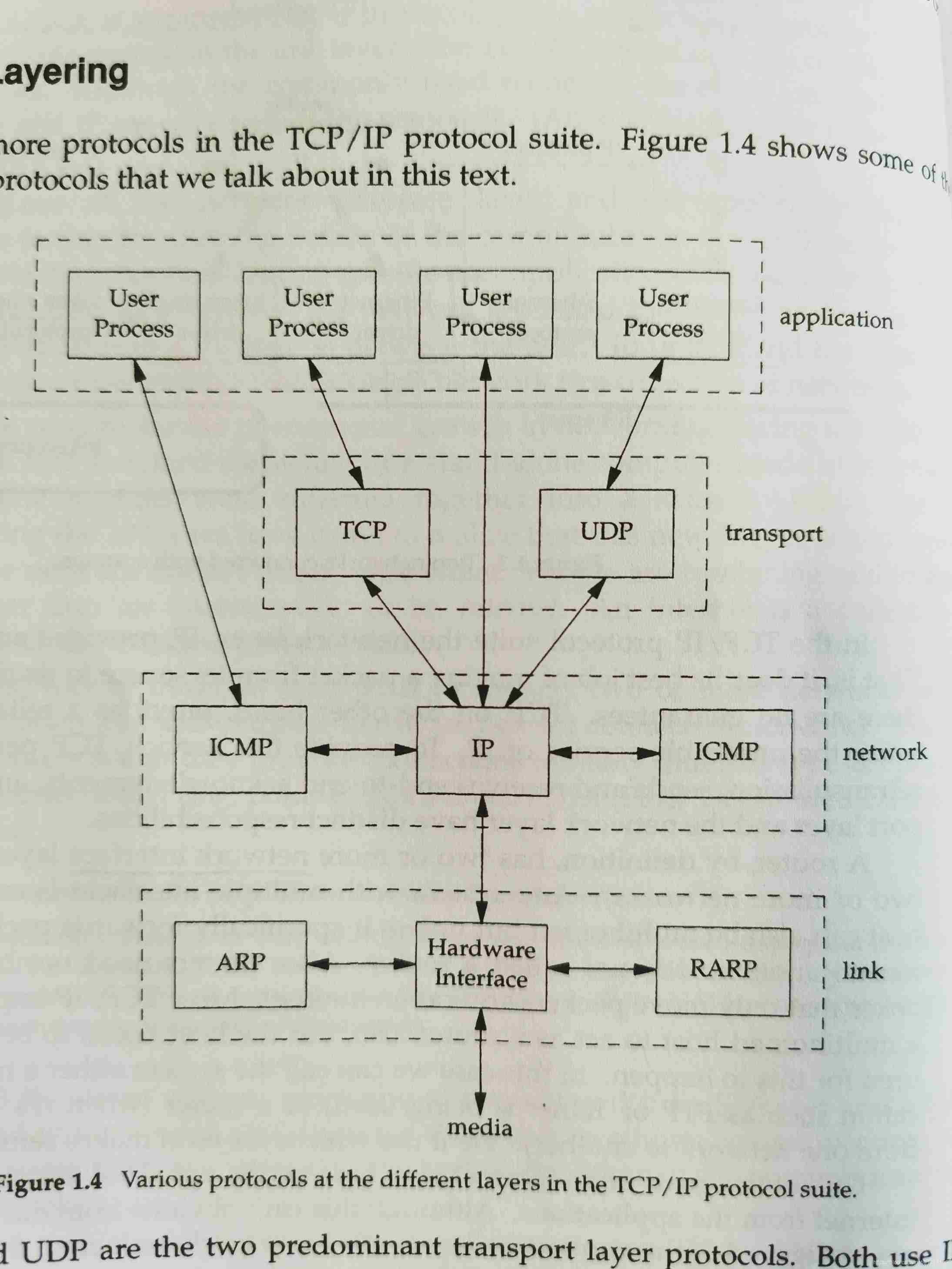
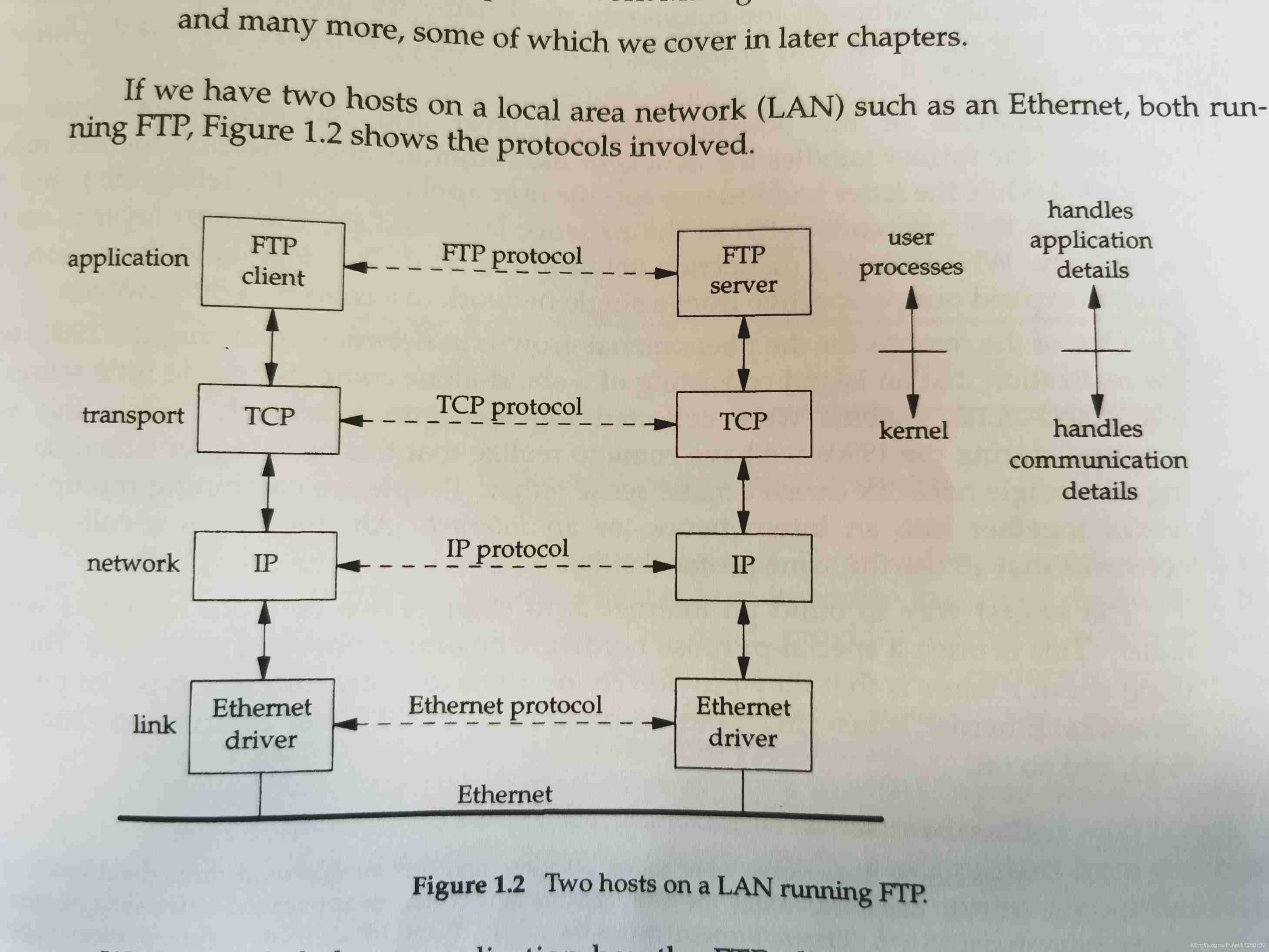
When processes communicate over the network , The application layer protocol handles the details of the application , Running on the operating system user Space ; Transport layer 、 The network layer and data link layer protocols handle the details of communication , Running on the operating system kernel Space .
Message encapsulation
When an application wants to pass TCP/IP When the protocol stack sends data , Data will be encapsulated layer by layer from top to bottom . Every floor will Add the relevant information of this layer to the head or tail of the sent data .
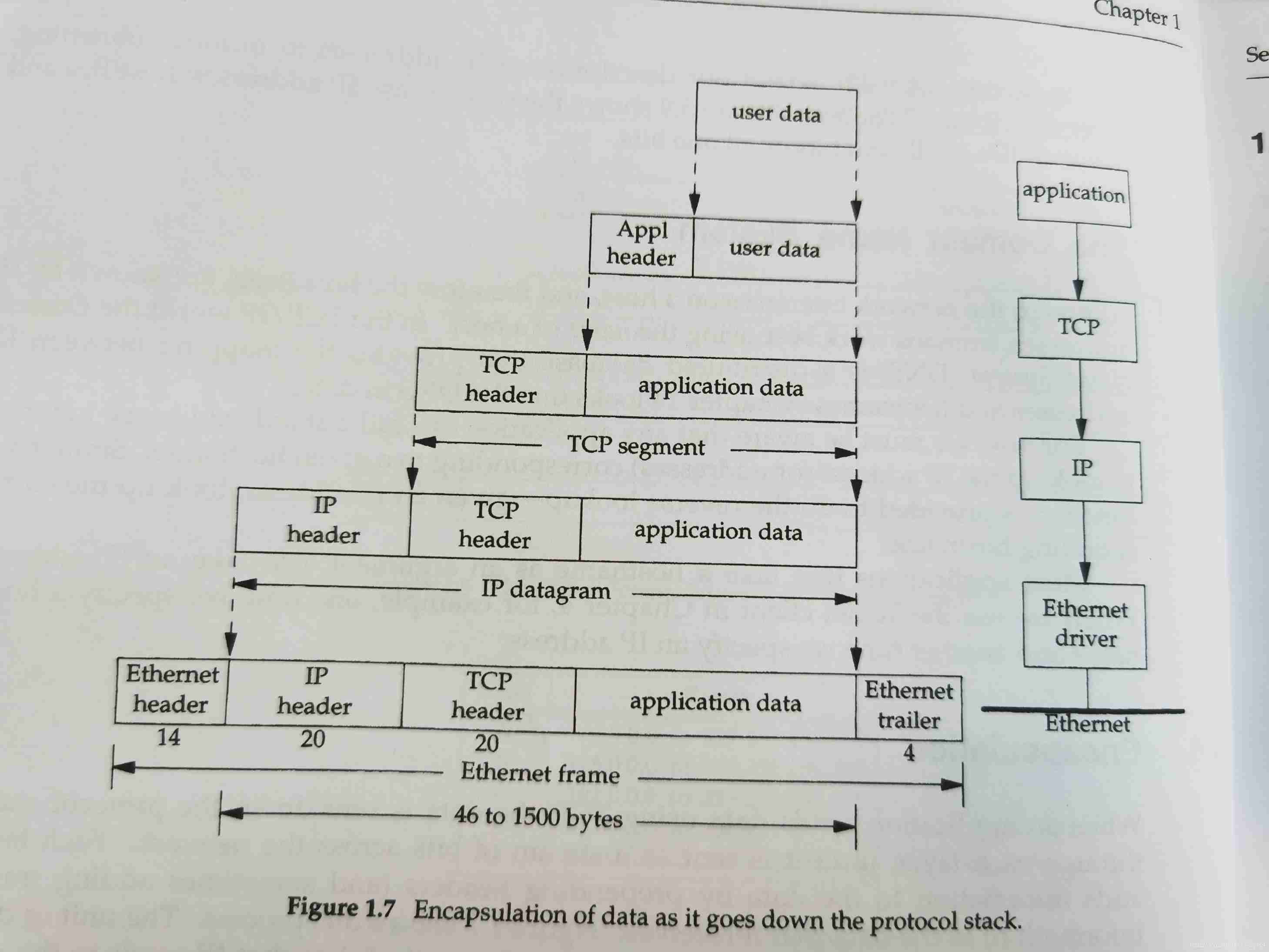
The receiver will strip each layer of information layer by layer , Until the data actually sent by the opposite end is obtained at the application layer .
边栏推荐
- 使用Electron开发桌面应用
- Haut OJ 1350: choice sends candy
- A new micro ORM open source framework
- Haut OJ 1401: praise energy
- 过拟合与正则化
- 2020ccpc Qinhuangdao J - Kingdom's power
- After setting up the database and website When you open the app for testing, it shows that the server is being maintained
- Web APIs DOM node
- Pointnet++的改进
- Double pointer Foundation
猜你喜欢
全排列的代码 (递归写法)
![[to be continued] [UE4 notes] L2 interface introduction](/img/0f/268c852b691bd7459785537f201a41.jpg)
[to be continued] [UE4 notes] L2 interface introduction
Sword finger offer 09 Implementing queues with two stacks
Sword finger offer 35 Replication of complex linked list
剑指 Offer 06.从头到尾打印链表
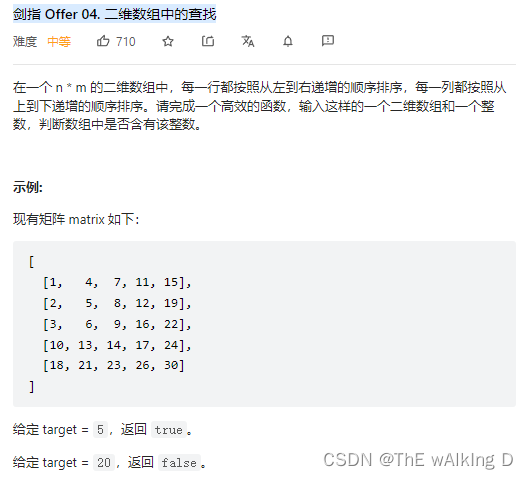
剑指 Offer 04. 二维数组中的查找

The present is a gift from heaven -- a film review of the journey of the soul
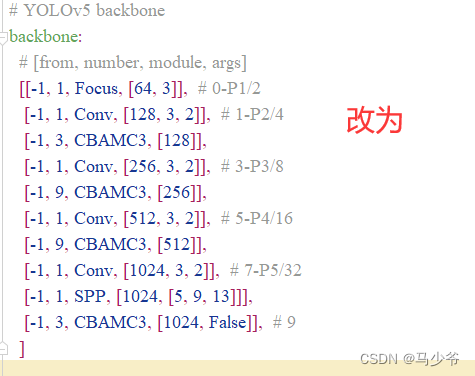
Yolov5 ajouter un mécanisme d'attention
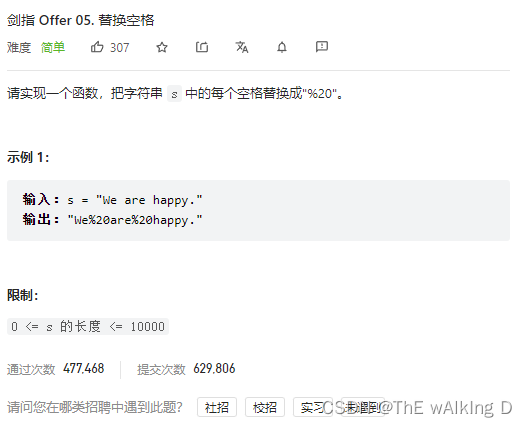
剑指 Offer 05. 替换空格

剑指 Offer 35.复杂链表的复制
随机推荐
Romance of programmers on Valentine's Day
Codeforces Round #716 (Div. 2) D. Cut and Stick
[es practice] use the native realm security mode on es
Animation scoring data analysis and visualization and it industry recruitment data analysis and visualization
Little known skills of Task Manager
Detailed explanation of expression (csp-j 2021 expr) topic
[to be continued] [UE4 notes] L3 import resources and project migration
[jailhouse article] performance measurements for hypervisors on embedded ARM processors
A new micro ORM open source framework
每日一题-搜索二维矩阵ps二维数组的查找
Mysql database (I)
[to be continued] [UE4 notes] L1 create and configure items
Haut OJ 1347: addition of choice -- high progress addition
Pointnet++的改进
【Jailhouse 文章】Look Mum, no VM Exits
[speed pointer] 142 circular linked list II
剑指 Offer 53 - II. 0~n-1中缺失的数字
Sword finger offer 04 Search in two-dimensional array
To the distance we have been looking for -- film review of "flying house journey"
第六章 数据流建模—课后习题