十三、系统优化
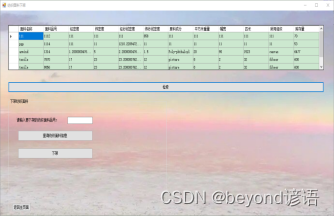
系统整体框架图 https://img blog.csdnimg.cn/bed0cda020d145dfa2716dddfa56e623.png 程序运行进入纺织面料库存管理系统主页面 https://img blog.csdnimg.cn/fe6c341cf7b44deba85ed49be60c...
2022-07-07 21:50【beyond谚语】
阅读更多leetcode-520. 检测大写字母-js
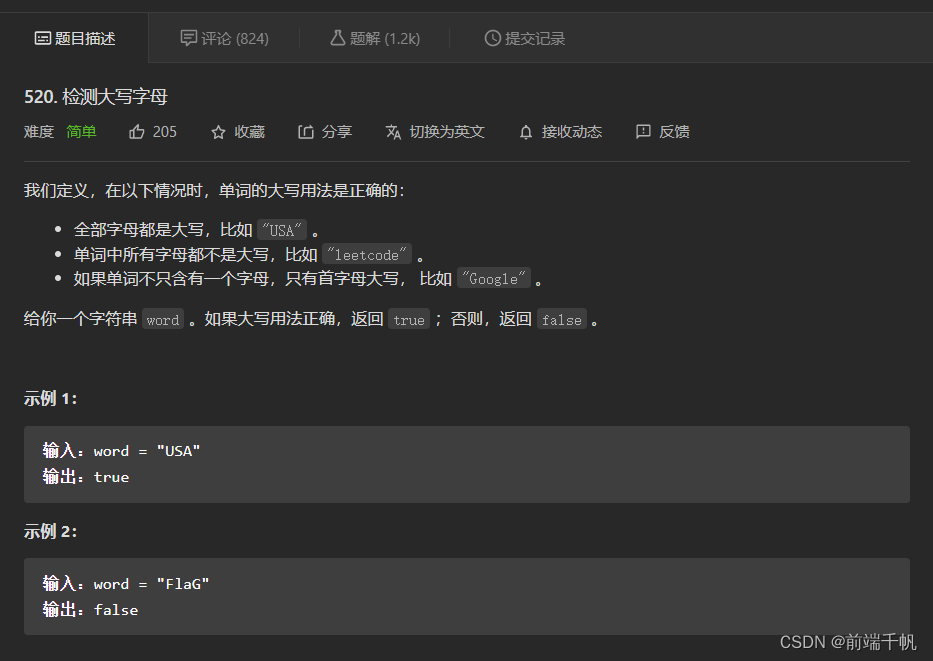
题目 https://img blog.csdnimg.cn/ff8d8fa531a3470bb74a90dd17f09302.png 代码 // / / @param {string} word / @return {boolean} / / var detectCapitalUse = fun...
2022-07-07 21:50【前端千帆】
阅读更多opencv scalar传入三个参数只能显示黑白灰问题解决
出错代码为: cv::Mat img2 h, w, CV 8UC1, cv::Scalar 0, 255, 0 ; scalar中传入的三个参数分别为BGR,上面这个函数我希望产生的是一个绿色的图片,然而实际上产生的却是白色的。 问题处在第三个参数,参数为CV 8UC1的时候表示产生的是黑白灰图案。...
2022-07-07 21:50【王柏~】
阅读更多解决:信息中插入avi格式的视频时,提示“unsupported video format”
大家好,又见面了,我是全栈君。 【測试步骤】:新建信息。加入AVI格式的 视频 【測试结果】:加入时弹出提示“unsupported video format” 该问题主要提如今手机彩信视频附件不支持该AVI格式的视频,因此我们通过操作流程对代码进行追踪,查找“unsupported video...
2022-07-07 21:50【全栈程序员站长】
阅读更多Adrnoid开发系列(二十五):使用AlertDialog创建各种类型的对话框
大家好,又见面了,我是全栈君。 AlertDialog能够生成各种内容的对话框。可是每种对话框都会有这样的的结构: 类似下边这样的的: 这仅仅是最简单的对话框。 我们来看下创建一个对话框须要的步骤: 1、使用创建AlertDialog.Builder对象 2、调用AlertDialog.Builde...
2022-07-07 21:50【全栈程序员站长】
阅读更多Redhat下安装fedora
大家好,又见面了,我是全栈君。 步骤具体解释: 1:到fedora官网下载fedora的DVD镜像文件。 2:在linux系统中预留一部分为未分区的空间大约50G 3: 在linux系统上的根分区创建一个fedora的目录,里面存放fedora的DVD镜像文件. 4: 在linux系统中挂载fedo...
2022-07-07 21:50【全栈程序员站长】
阅读更多Why does the market need low code?
Gartner forecast , end 2021 year , The market scale of application development demand increases , Will at least surpass the enterprise IT Delivery cap...
2022-07-07 23:10【Gemcoder】
阅读更多Kubernetes' simplified data storage storageclass (creation, deletion and initial use)
kubernetes Simplified data storage StorageClass( Create and delete as well as initial use ) List of articles Preface 7 One 、 pandas 16 StorageCl...
2022-07-07 23:10【zsk_ john】
阅读更多14、 Two methods of database export and import
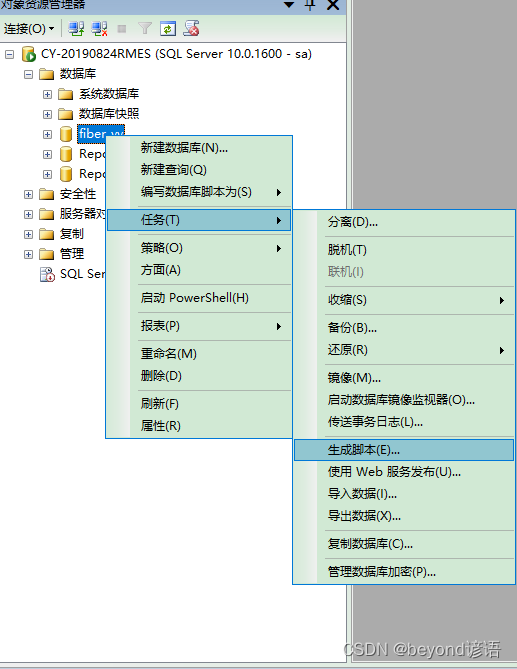
One 、 With SQL Script format export ( recommend ) export Right click the database to export , Mission — Generation script https://img blog.csdn...
2022-07-07 23:10【Beyond proverb】
阅读更多What are the similarities and differences between smart communities and smart cities
Community is the cell of city , It's an important part of smart city , It is also the inheritance of the concept of smart city 、 Development and impl...
2022-07-07 23:10【Gemcoder】
阅读更多Bit operation
An operation (Bit Operation) 136. A number that appears only once https://leetcode cn.com/problems/single number/ 136 httpsleetcodecncomproblemssi...
2022-07-07 23:10【Yake1965】
阅读更多JMeter interface automated test read case, execute and write back result
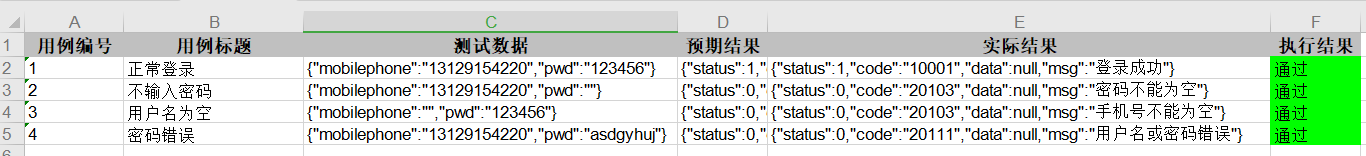
Preface : 【 At the end of the article, a lot of benefits are prepared for you 】 One : Environmental preparation 1. download jxl.jar This jar packa...
2022-07-07 23:10【Test Architect Bei fan】
阅读更多Binary tree
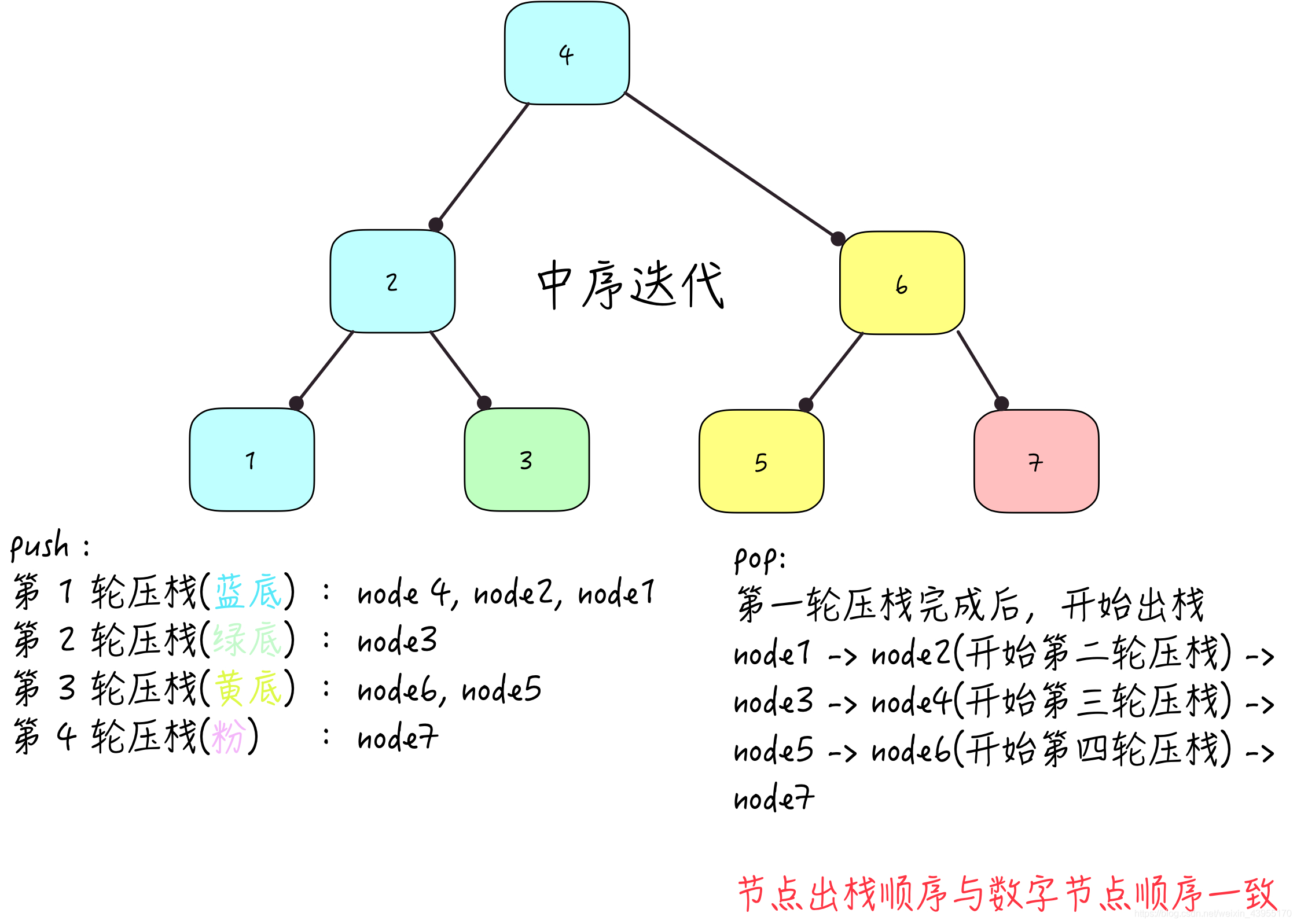
Binary tree (Binary Tree) Binary search tree 1 501. The mode in the binary search tree mode in binary search tree/ 501 httpsleetcodecnproblems...
2022-07-07 23:11【Yake1965】
阅读更多Grid
Grid 463. The perimeter of the island perimeter/ 463 httpsleetcodecnproblemsislandperimeter 1 200. Number of Islands of islands/ 200 httpslee...
2022-07-07 23:11【Yake1965】
阅读更多Network security -burpsuit
Reference video : 【 Qian Feng 】 Network security 300 A complete set of video tutorials web Security / Penetration test / Hacker attack and defense /...
2022-07-07 23:11【One of IT guys】
阅读更多Network security - joint query injection
Reference video : 【 Qian Feng 】 Network security 300 A complete set of video tutorials web Security / Penetration test / Hacker attack and defense /...
2022-07-07 23:11【One of IT guys】
阅读更多Network security - install CentOS
Reference video : 【 Qian Feng 】 Network security 300 A complete set of video tutorials web Security / Penetration test / Hacker attack and defense /...
2022-07-07 23:11【One of IT guys】
阅读更多Network security sqlmap and DVWA explosion
Reference video : 【 Qian Feng 】 Network security 300 A complete set of video tutorials web Security / Penetration test / Hacker attack and defense /...
2022-07-07 23:11【One of IT guys】
阅读更多Network security - phishing
Reference video : 【 Qian Feng 】 Network security 300 A complete set of video tutorials web Security / Penetration test / Hacker attack and defense /...
2022-07-07 23:11【One of IT guys】
阅读更多Network security - information query of operating system
Reference video : 【 Qian Feng 】 Network security 300 A complete set of video tutorials web Security / Penetration test / Hacker attack and defense /...
2022-07-07 23:11【One of IT guys】
阅读更多
边栏推荐
- More than 10000 units were offline within ten days of listing, and the strength of Auchan Z6 products was highly praised
- 【Seaborn】组合图表:FacetGrid、JointGrid、PairGrid
- Yarn开启ACL用户认证之后无法查看Yarn历史任务日志解决办法
- [open source] Net ORM accessing Firebird database
- Personal statement of testers from Shuangfei large factory: is education important for testers?
- UVALive – 4621 Cav 贪心 + 分析「建议收藏」
- Revit secondary development - get the project file path
- 实训九 网络服务的基本配置
- 微服务远程Debug,Nocalhost + Rainbond微服务开发第二弹
- Some arrangements about oneself
猜你喜欢
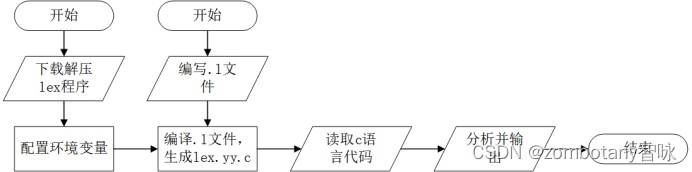
One 、 Experimental content 1. With the help of lexical analysis tools Flex or Lex complete ( Reference network resources ) 2. Input : High level la...

上一篇 初识 Flutter 的绘图组件 — CustomPaint 我们介绍了 CustomPaint 的基本概念和使用,可以看到 CustomPaint 其实和 前端的 Canvas 基本上是一样的,实际上前端 Canvas 支持的绘制方法 CustomPaint 都支持,毕竟 Custom...
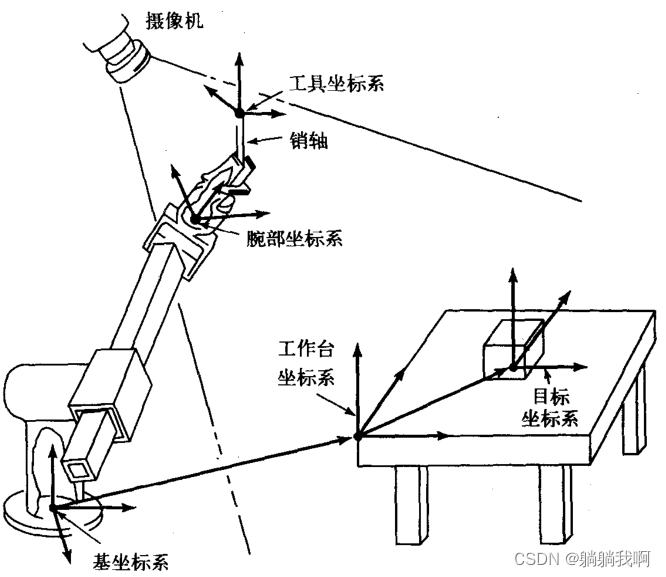
指南目录*: 机械臂速成小指南(零):指南主要内容及分析方法 53966219/article/details/125303151?spm=1001.2014.3001.5501 '机械臂速成小指南(零):指南主要内容及分析方法' 机械臂速成小指南(一):机械臂发展概况 53966219/...
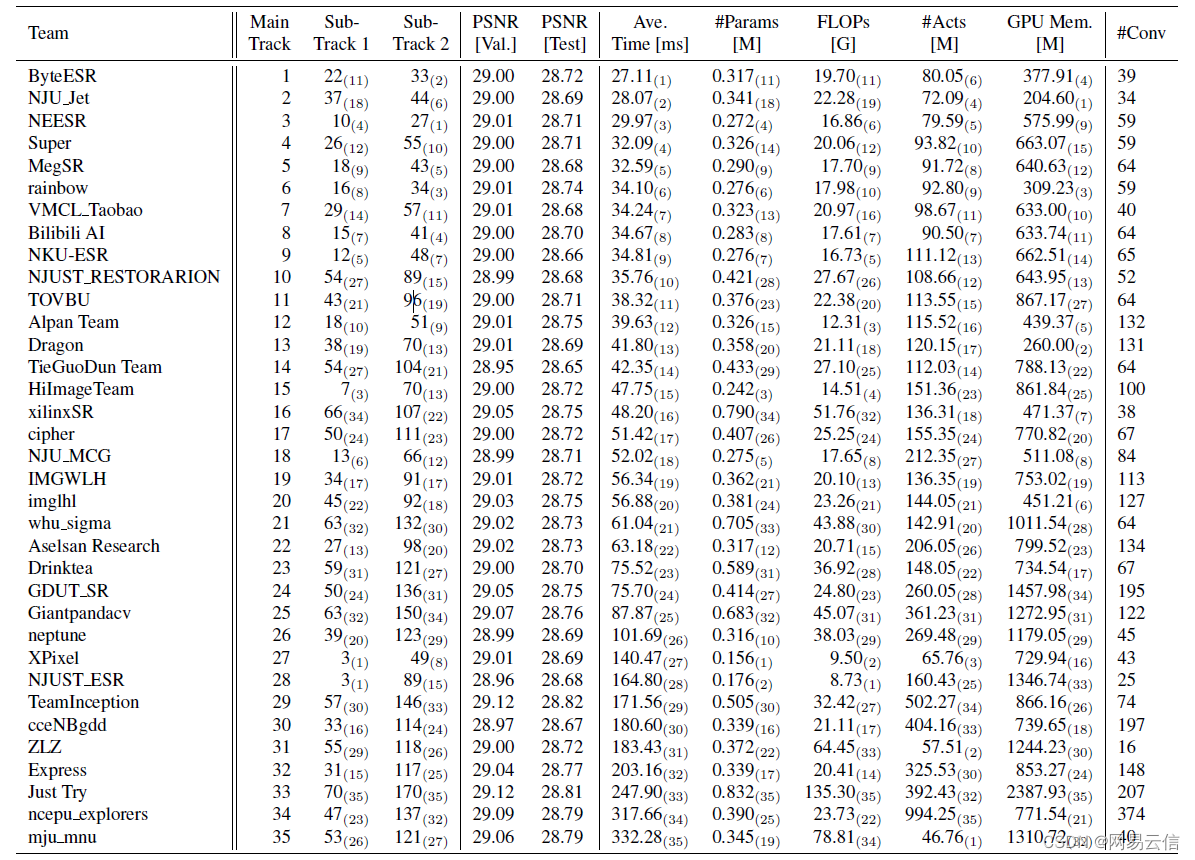
前言 近日,计算机视觉和模式识别领域顶级会议 CVPR 在美国新奥尔良市举办,同时计算机图像恢复领域最具影响力的全球性顶级赛事 NTIRE 在会上颁奖,网易云信音视频实验室取得 NTIRE 高效率超分辨率挑战赛总体性能赛道冠军,以及运行时间赛道季军。本文将着眼于 AI 超分技术从研究到部署的落地问...

Reading guide : Always look at big data DT My classmates all say that we are 「 Treasure number 」, That's because we have a traditional skill , Is t...
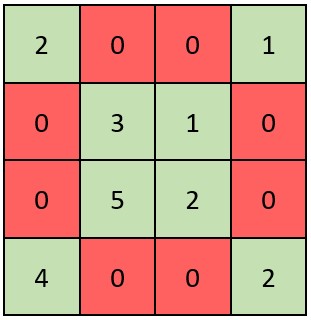
Catalog 599. The minimum index sum of two lists 599 2 Knowledge points involved : 10 Code section 12 674. The longest continuous increasing s...
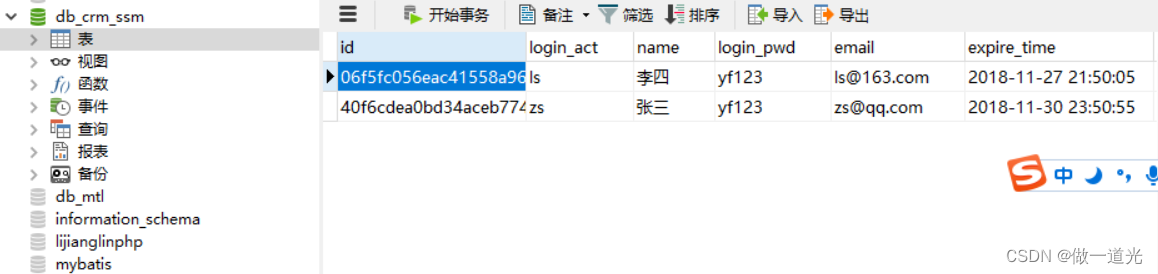
2.1CRM数据库设计 2.1.1数据库设计原则 我们可以结合项目原型来考虑数据库设计,市场活动,用户,这些都是需要是持久化的,所以都需要设计成表。表和表之间通常还会有一定的关系。看每一个创建表单上都有哪些属性。 1、所有的表来自于需求: 名词,特别是业务相关的名词。理清名词之间的关系。 ...
Through the last blog post , We can get the data of the file as follows : https://img blog.csdnimg.cn/a7facf8e07d5441b8bf049b92e611a6c.png So the pr...
When decomposing complex software systems , One of the technologies most used by software designers is layering . Layered right has many advantages :...

适合创建索引的一些情况 https://img blog.csdnimg.cn/c190e9197478440783324670dbf4b7b5.png https://img blog.csdnimg.cn/17a336de797748eea0aa7d8a93fae7d5.png https:/...