当前位置:网站首页>JVM quick start
JVM quick start
2022-07-06 08:35:00 【So, dream】
List of articles
JVM brief introduction
What is? JVM?
JVM yes Java virtual machine (Java Virtual Machine) For short . It's called a virtual machine , Because it is an abstract computer , There is a complete hardware architecture inside ( register , Stack , Instruction system, etc ).
Simply speaking ,Java A virtual machine is a perform Java Bytecode virtual computer .
What is a virtual machine ?
Definition : A virtual machine is a virtual computer . It's a software , Can simulate a series of virtual computer instructions .
Virtual machines can be divided into System virtual machine and Program virtual machine Two kinds of .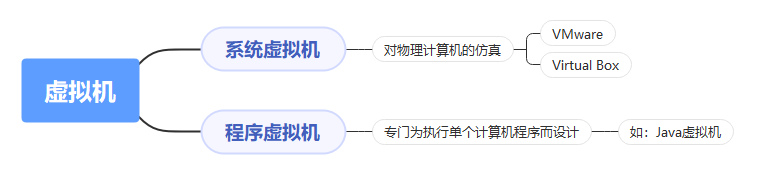
JVM The role of
Java Virtual machine is The running environment of binary bytecode , Responsible for loading bytecode into its interior , explain / Compile to the corresponding platform (Linux,Mac,Windows etc. ) Execution of machine instructions on .
JVM Characteristics
- Platform independence
- A compilation , Run anywhere
- Automatic memory management
- Automatic garbage collection
JVM The location of
It was said that , Virtual machine is a software that simulates the instructions of virtual computer . So it It's essentially a piece of software , Running on the operating system .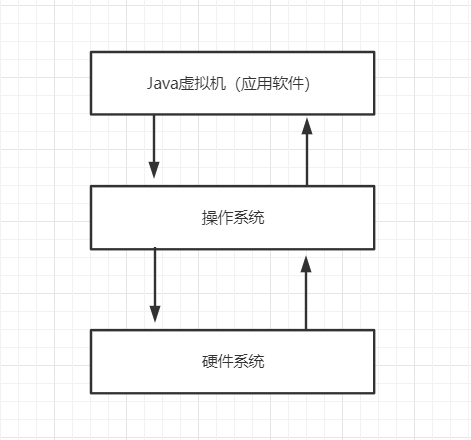
JVM Structure
JVM The structure of can be simply represented by the figure below :
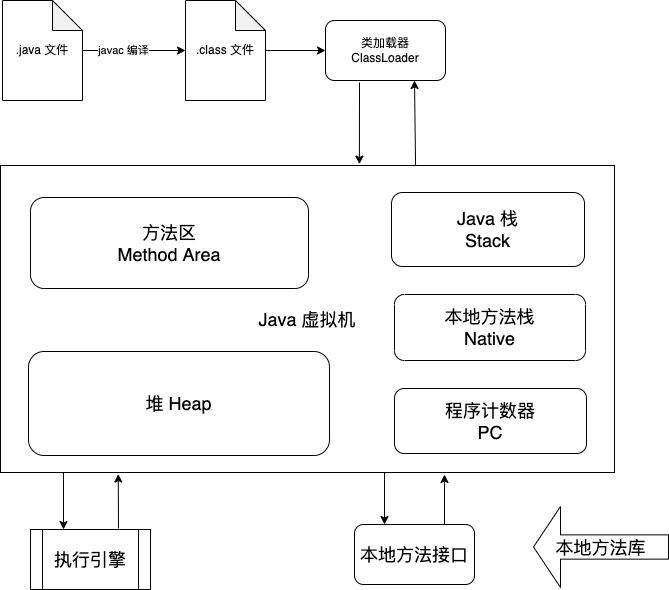
Java Memory optimization mainly focuses on heap , The method area is a special heap area .
Class loader
Class loader (ClassLoader) be used for Load the bytecode file into JVM Middle to run .
JVM Three layers are provided in ClassLoader:
- Bootstrap classLoader: Boot class loader , Mainly used for loading Java Core class library of .
- ExtClassLoader: Extend the classloader , Used for loading jre/lib/ext Some of the extended jar package .
- AppclassLoader: system class loader , Used to load classes in the application .
Parent delegate mechanism
The parental appointment mechanism is JVM load .class The mechanism of . When loading a class , The system class loader delegates upward to the extension class loader , The extension class loader delegates upward to the boot class loader . If the boot class loader contains this class , Load successfully . Otherwise, it is handed down to the extension class loader to load , The extension class loader cannot load , It will be loaded by the system class loader .
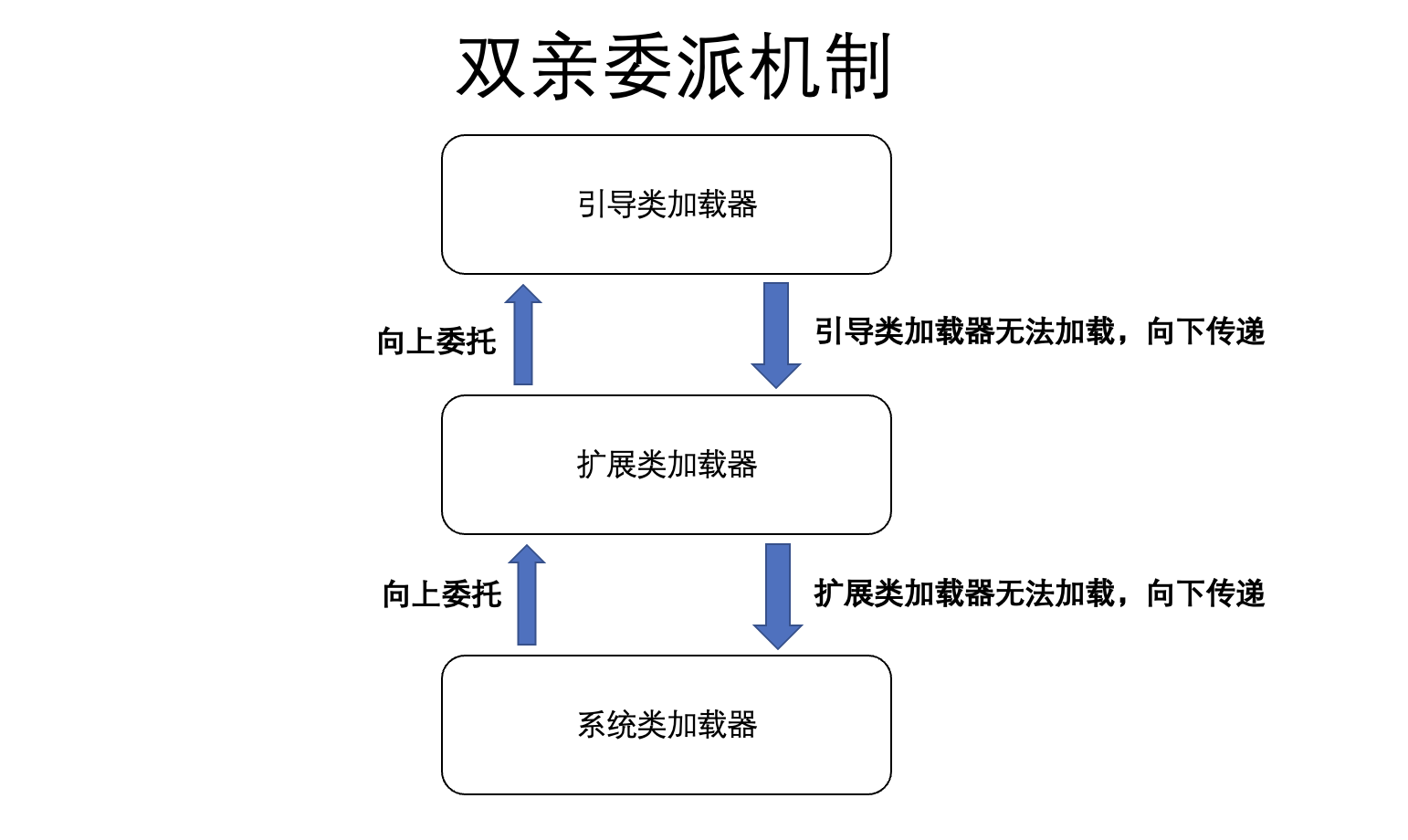
Advantages of parental delegation :(1) Avoid class reloading , Once a class is loaded by the parent loader , It will not be loaded by the subclass loader (2) Protect program security , Prevent the core file from being tampered
Sandbox security mechanism
Sandbox is a security mechanism in the field of computer security , Provide an isolated environment for running programs . If JVM It's a big box , If I run an unknown program directly inside , Is likely to JVM Other internal procedures have adverse effects . therefore , We can do it in JVM Zhongjian has a small box ( The sandbox ), Let it run in this small box .
If the code in the sandbox needs to access the operating system and local resources , How to ensure safety ? Sandbox security mechanism provides different for different sandboxes jurisdiction , Call the operating system and local resources according to permissions . for example , Core classes have the highest permissions , Remote code has lower permissions .
native keyword
native It means local , When the method is native Keyword modification , Express Java The scope of action of has not reached , Will call libraries in other languages . Execute to be native The modified method will enter the local method stack , call JNI (Java Native Interface) To operate other programming languages .
Native Method Stack : For registration native Method , Load the local method library when the execution engine executes
JNI: Local method interface , Call the class libraries of other languages through this interface
Java Use native Keywords are for extension Java Use , Can be in Java Using other programming languages , So that it can stand .
Program counter
Each thread has a program counter , Threads are private . It's a pointer , Point to the bytecode in the method area , Tell the execution engine which instruction to execute now .
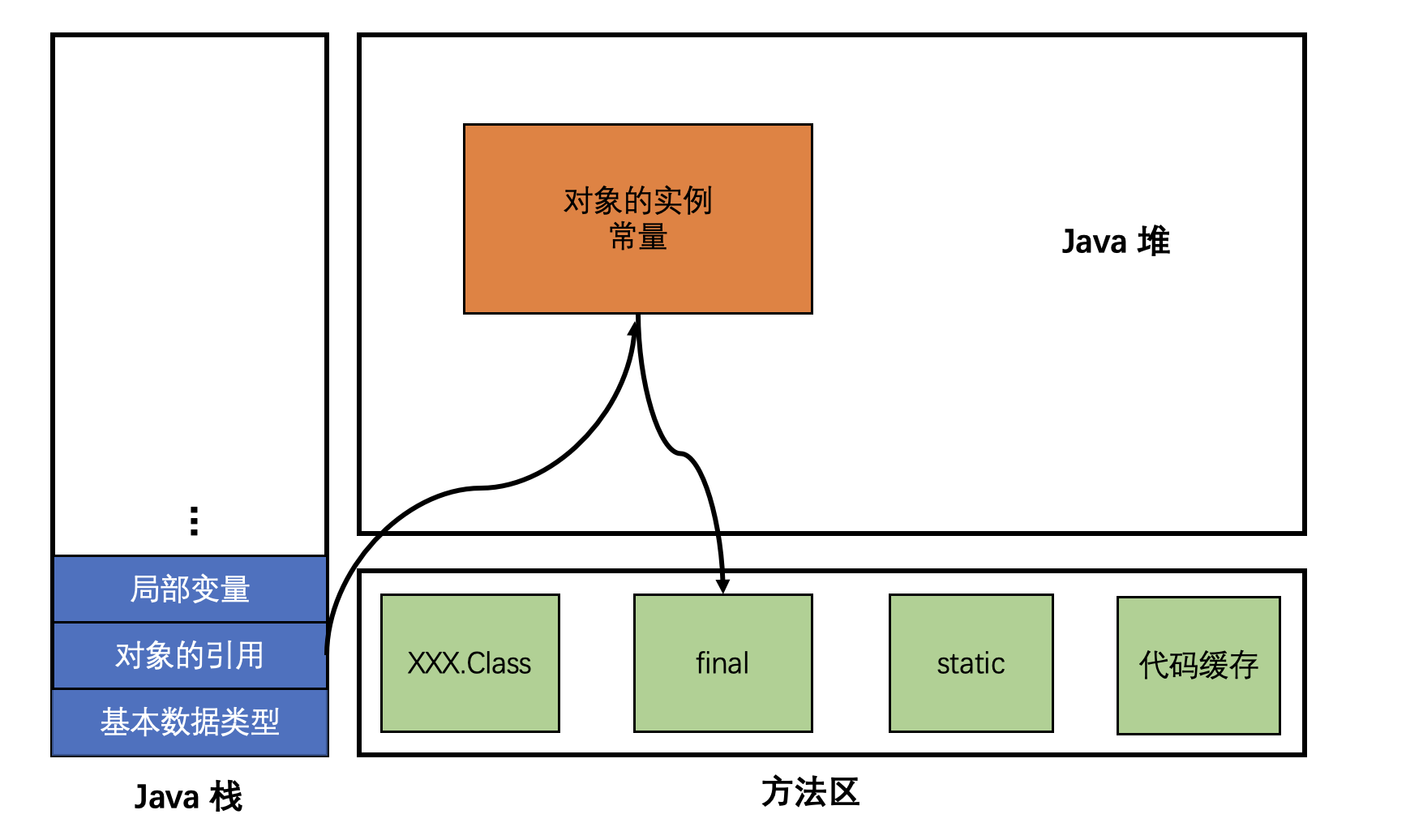
Method area
Method area Shared by all threads , All field and method bytecodes , And some special methods , Such as constructor , The interface code is also defined here . Simply speaking , Information about all defined methods is stored in this area , This area is a shared area .
Static variables 、 Constant 、 Class object ( Construction method 、 Interface definition ) The runtime constant pool exists in the method area , But variable instances exist in heap memory
Stack
A stack is a last in, first out data structure . The operation of stack supervisor , Life cycle is synchronized with thread .
Thread end , Stack memory is also released , So for the stack , There is no recycling .
The contents stored in the stack are :
- Eight basic data types
- References to objects in the heap
Pile up
Instances in the heap used to store objects . The stack is thread level , There is only one heap in the virtual machine .
The memory of the heap can be further subdivided into : New Area 、 Elderly area and meta space . The new area can be subdivided into Eden Park 、 survive 0 Area and survival 1 District .
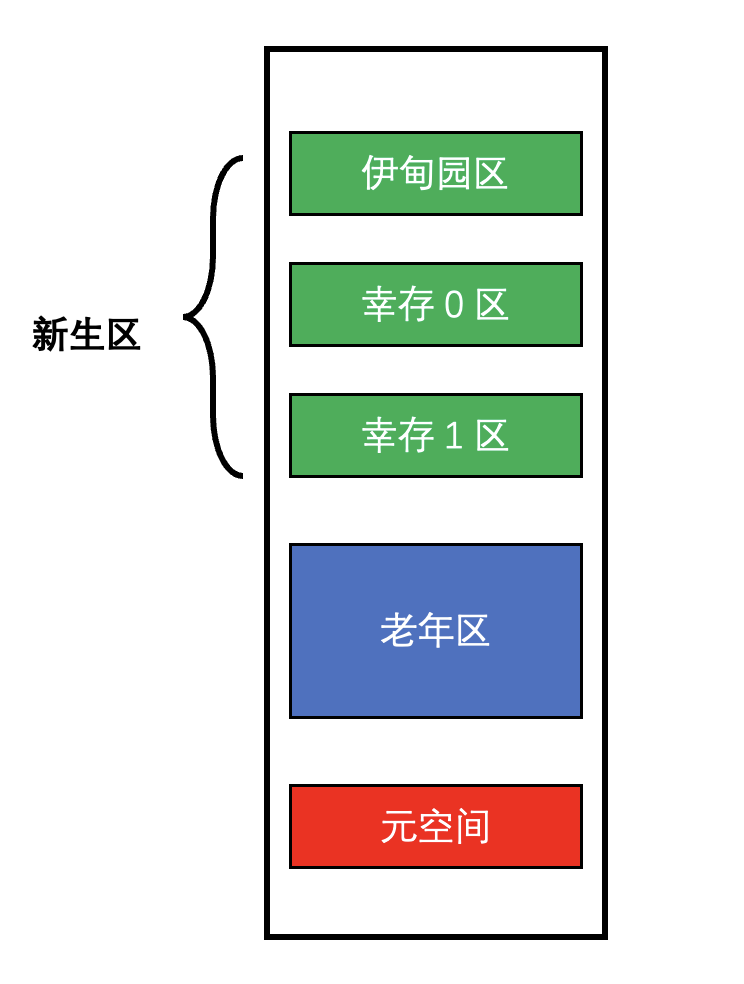
New Area
Eden Park is the place where objects are generated , When Eden Park is full , Will trigger a lightweight GC, Objects that have not been cleared will be sent to the survival area . When the new area is full , Will trigger a reset GC, heavy GC The surviving objects will be sent to the elderly area . Besides , Without setting , The new area has experienced 15 Second light GC The target will be sent to the elderly .
Old age area
The old area is used to store the heavy experience in the new area GC Or reach light GC Objects that still survive after the threshold number .
Meta space
Meta space is resident in memory , What's stored is Java Some environment or class information at runtime .
IDEA Set in JVM Size
At the project construction site , double-click Edit Configurations
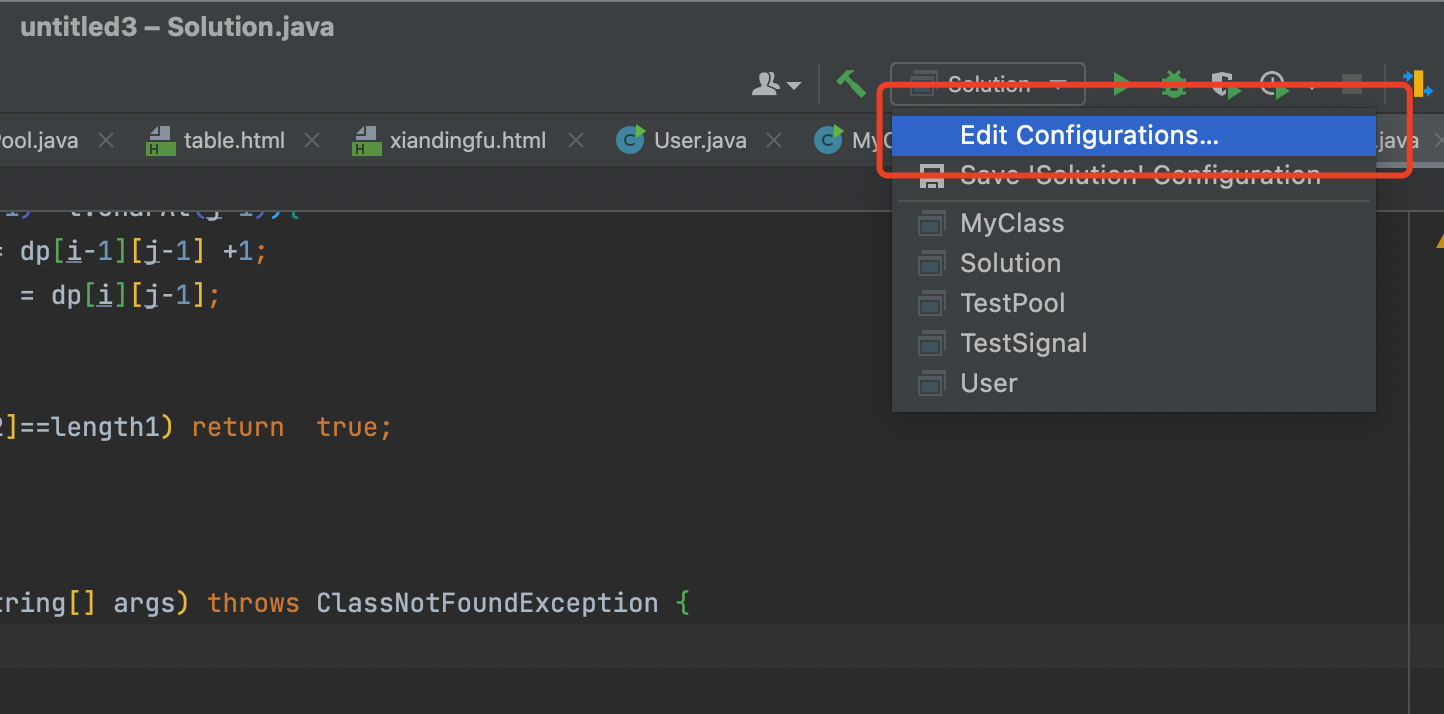
In the pop-up page , Set the size of the virtual machine 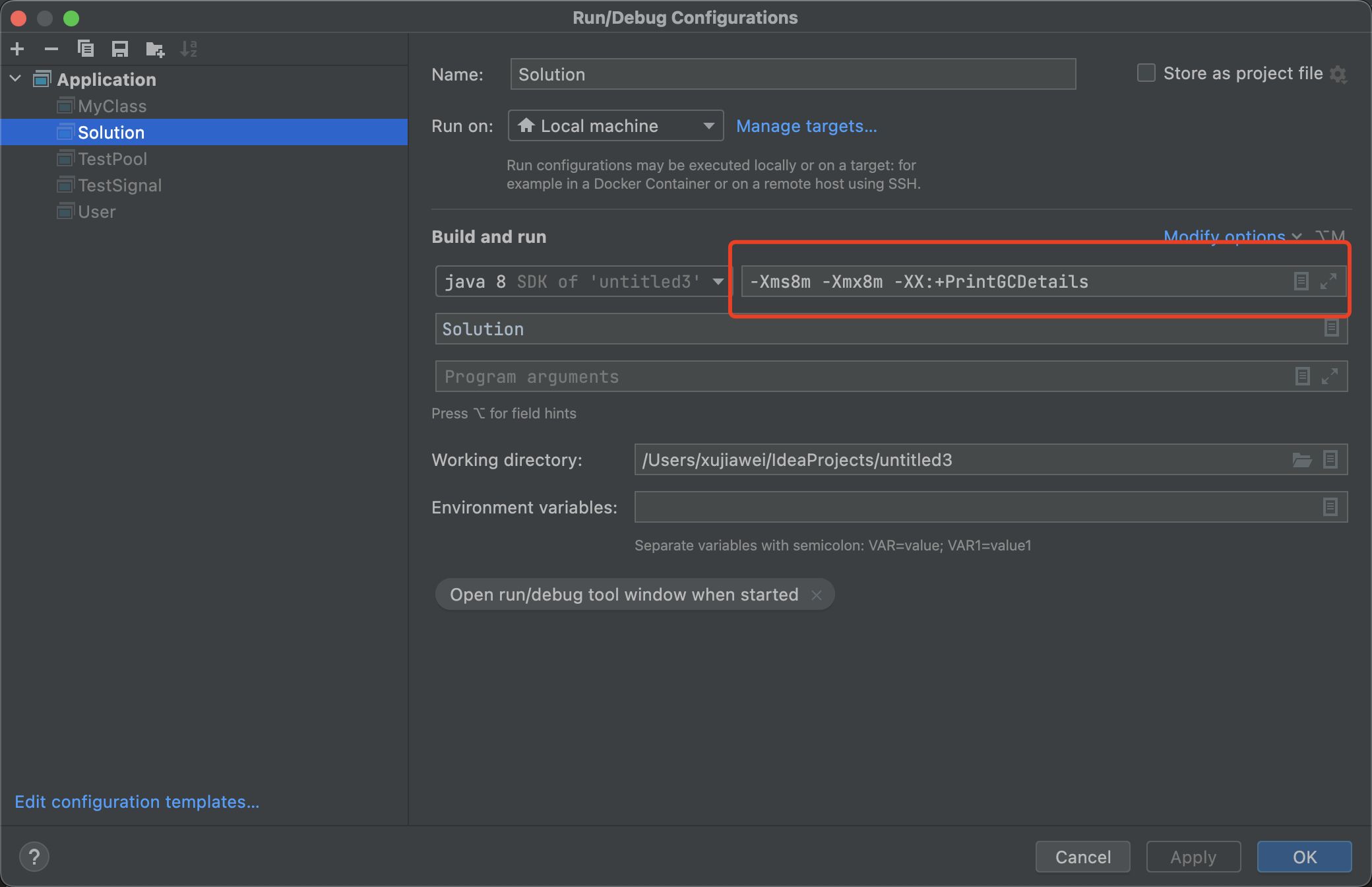
-Xms8m -Xmx8m -XX:+PrintGCDetails in -Xms、-Xmx Used to set the initial memory allocation size and the maximum allocated memory ,-XX:+PrintGCDetails For printing GC Details of .
Garbage collection mechanism
Garbage recycling is mainly concentrated in Eden Park and the elderly area .
Types of garbage collection include light GC and heavy GC, light GC Only clean the new areas , and heavy GC It's the whole picture GC.
GC Common algorithms of include Replication Algorithm 、 Mark removal method and mark sorting method .
Copy algorithm
Here we will be survivors 0 District And survivors 1 The district is called from Area and to District . When Eden Park is full , Will trigger a light GC, The surviving object enters to District , And then from Copy the existing objects in the area to to In the area ; The final will be from Empty the area and Exchange from Area and to The location of the area .

The advantage of this method is There will be no memory fragmentation , And the time complexity is low , The disadvantage is to maintain an empty to District , It's a waste of resources .
Mark removal method
Mark removal method includes two steps , First scan , Mark the elements to be cleared , Then scan again to clear the object .
The advantages of this method will not cause a waste of resources , But it has high time complexity , And will produce memory fragments .
Mark up
Mark sorting method is based on mark clearing method , By moving objects, memory fragmentation is avoided .
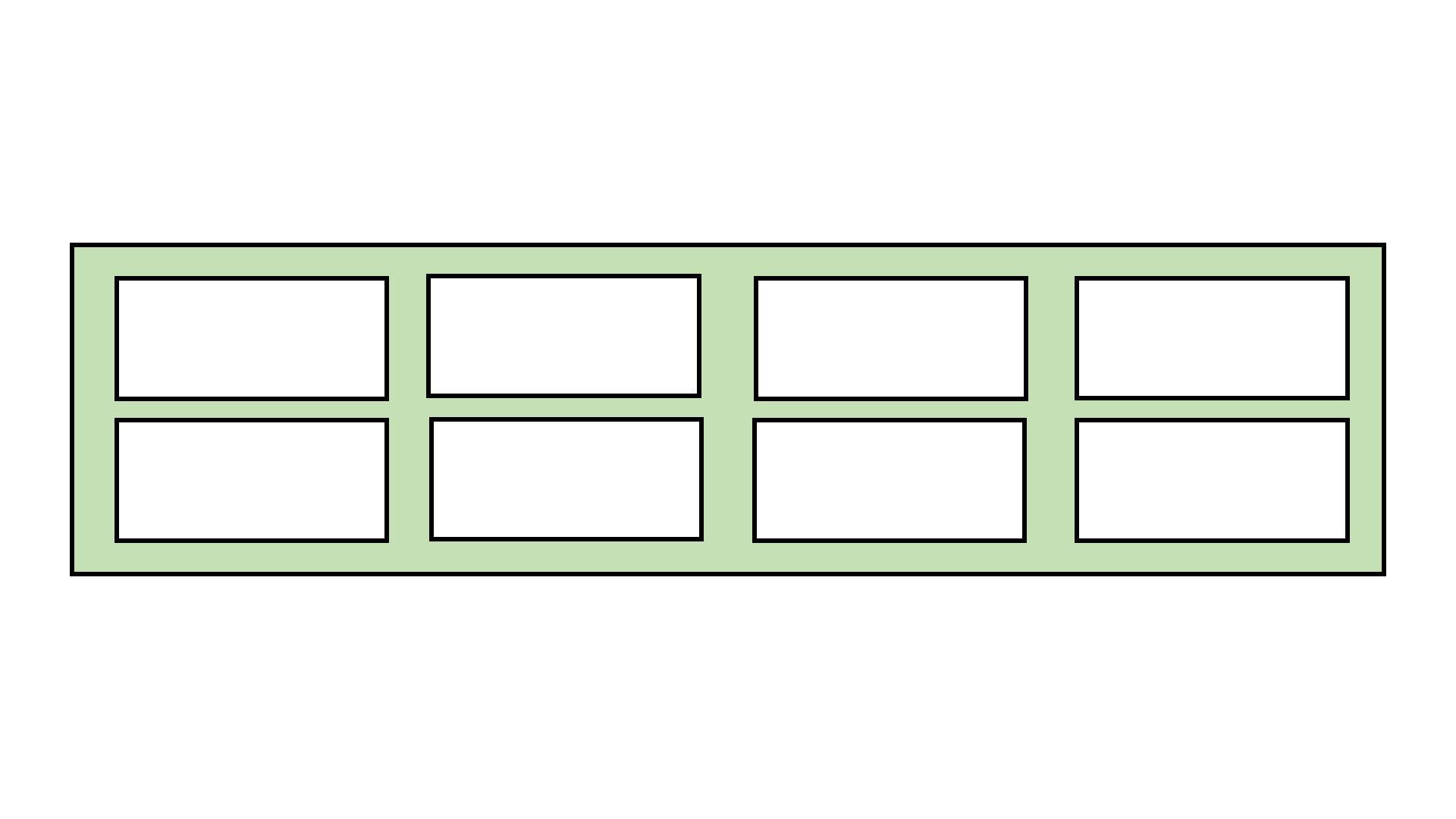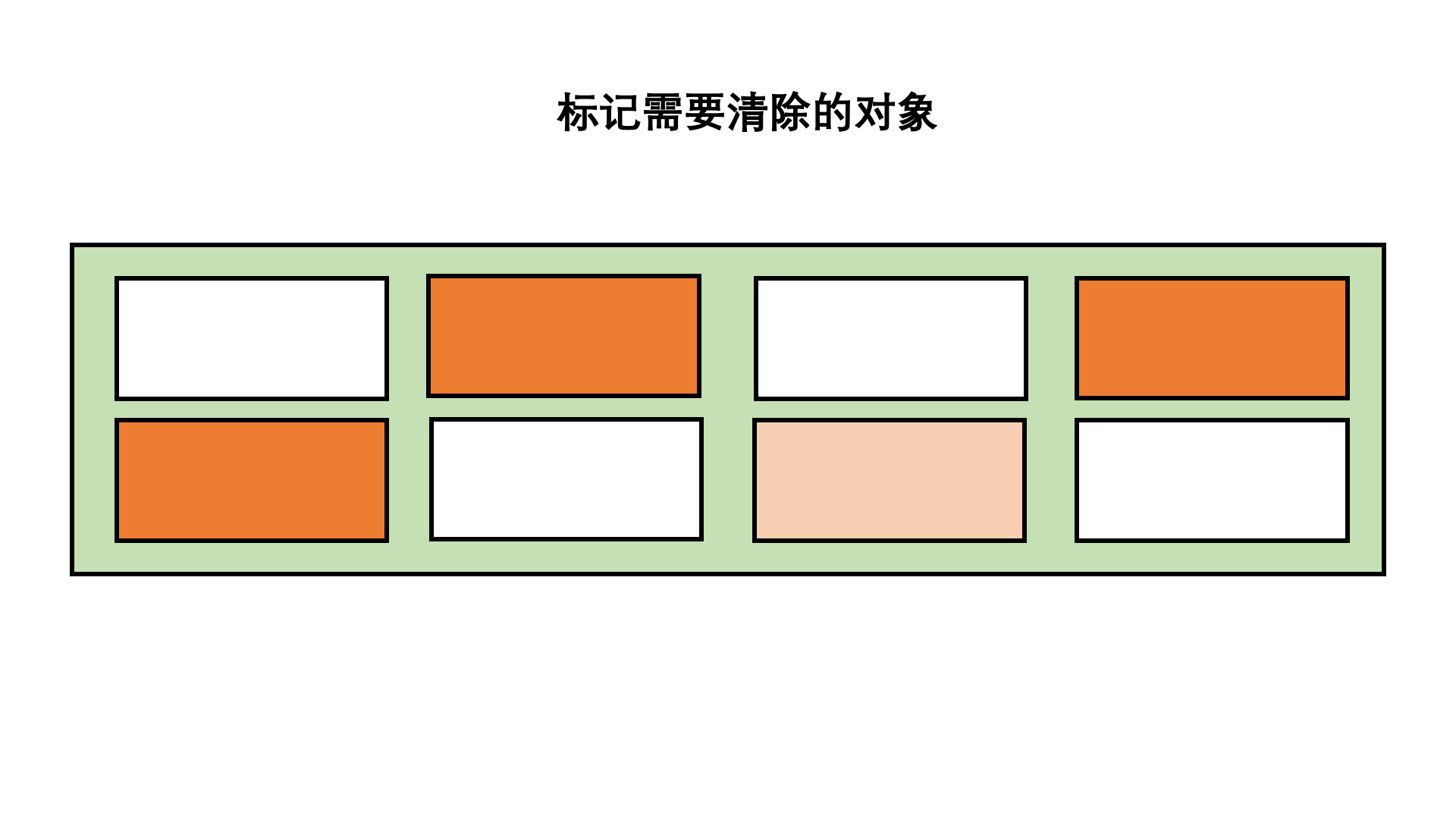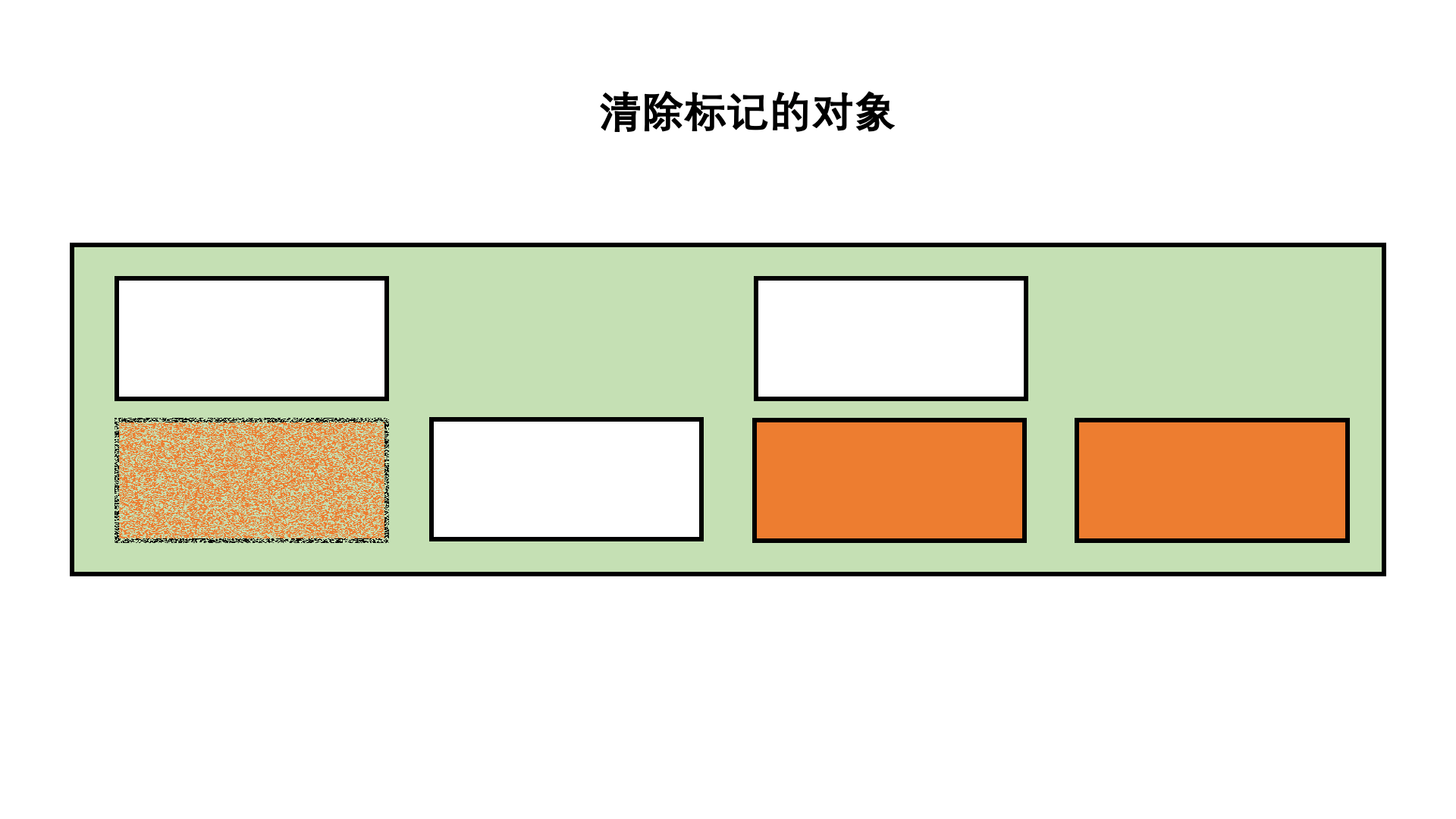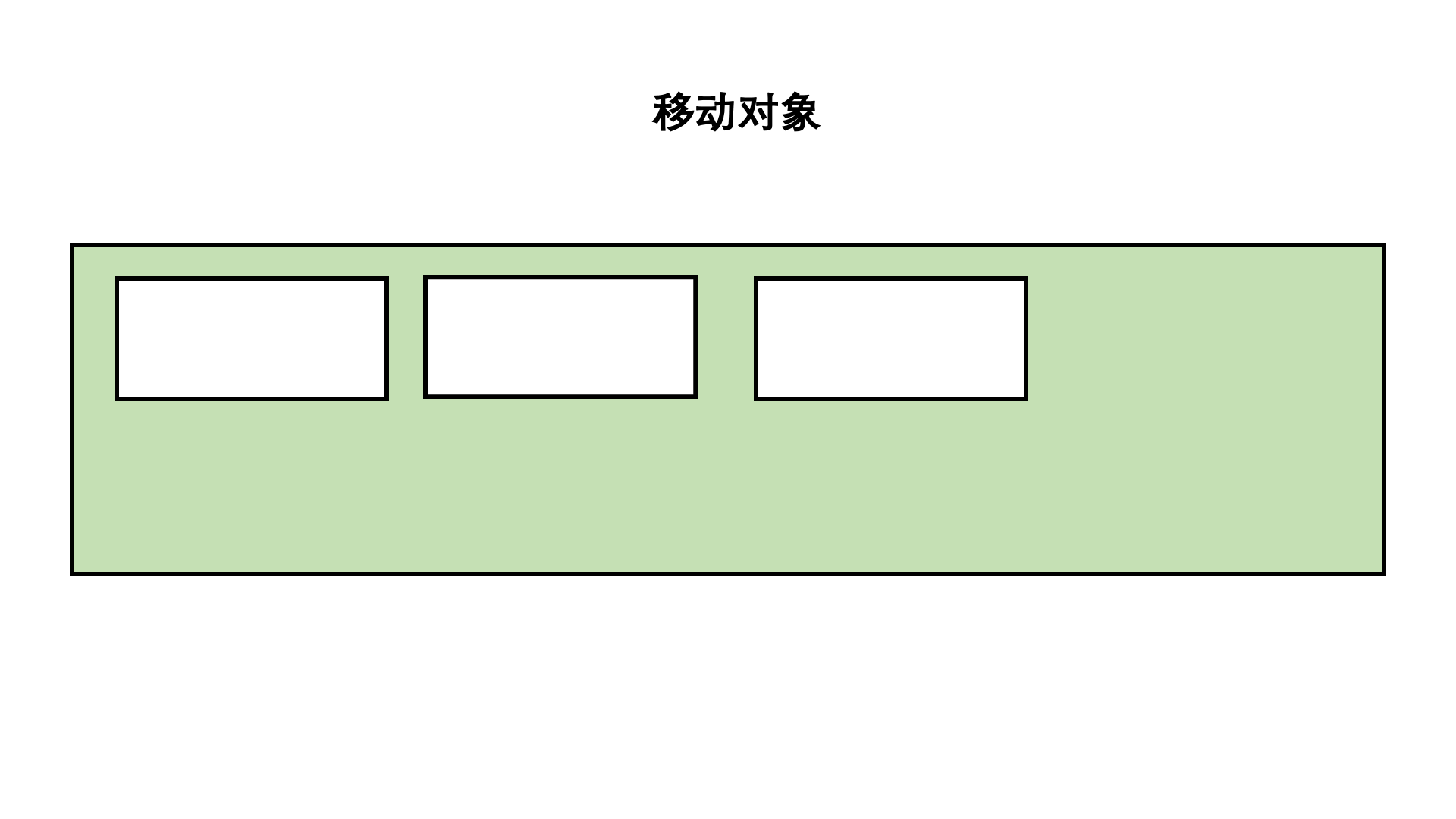
Compared with mark removal , The time complexity of this algorithm is higher , But there will be no memory fragmentation .
边栏推荐
- Fibonacci sequence
- Crash problem of Chrome browser
- 2022 Inner Mongolia latest water conservancy and hydropower construction safety officer simulation examination questions and answers
- Visual implementation and inspection of visdom
- Unified ordering background interface product description Chinese garbled
- Roguelike游戏成破解重灾区,如何破局?
- JVM 快速入门
- Let the bullets fly for a while
- 企微服务商平台收费接口对接教程
- The resources of underground pipe holes are tight, and the air blowing micro cable is not fragrant?
猜你喜欢
随机推荐
[cloud native topic -45]:kubesphere cloud Governance - Introduction and overall architecture of enterprise container platform based on kubernetes
logback1.3. X configuration details and Practice
Colorlog结合logging打印有颜色的日志
Vocabulary notes for postgraduate entrance examination (3)
TCP/IP协议
Precise query of tree tree
JVM 快速入门
704 二分查找
Research Report on Market Research and investment strategy of microcrystalline graphite materials in China (2022 Edition)
PLT in Matplotlib tight_ layout()
VMware 虚拟化集群
如何进行接口测试测?有哪些注意事项?保姆级解读
The resources of underground pipe holes are tight, and the air blowing micro cable is not fragrant?
延迟初始化和密封类
Crash problem of Chrome browser
Problems in loading and saving pytorch trained models
Unified ordering background interface product description Chinese garbled
Colorlog combined with logging to print colored logs
Golang force buckle leetcode 1020 Number of enclaves
swagger设置字段required必填

![[MySQL] log](/img/e9/1617122888c096cf6aba2bdb88f0ef.png)