当前位置:网站首页>The harm of game unpacking and the importance of resource encryption
The harm of game unpacking and the importance of resource encryption
2022-07-06 08:34:00 【Fairguard mobile game reinforcement】
In the sub circuit “ The bestselling ”—— B female game
According to the market analysis report of frost Sullivan, a consulting company ,2013-2017 year , The market size of Chinese women's mobile games is calculated by revenue , The compound annual growth rate is 101.6%; expect 2022 year , China's female mobile game market will reach 935 One hundred million yuan .

The market size of Chinese women's mobile games in terms of revenue
Some reports point out , Women are more loyal in mobile games , The willingness to spend time and money on games is stronger . Driven by the continuous rise of women's social status and the increase of female mobile game players , The female game market has obviously become “ The bestselling ”.
Among the female games, the most representative one is the second female game ( A love simulation game with women as the target audience ). According to the huge calculation report ,2021 year 5 month , The number of live broadcasts of b-female game anchors 、 The growth rate of live broadcast duration is higher than that of other games , The number of viewers attracted has increased by 6405%, It is enough to prove the user volume and popularity of b-women Games .

The live broadcast of b-women games increased significantly , The data source is huge
tencent 、 NetEase 、 MIHA tour and other game manufacturers have successively landed at the b-women Game track , I want to share in this .
The network war caused by the unpacking of games with tens of millions of downloads
2021 year 6 month 24 Before going online the next day , Tencent's second female game 《 The love between light and night 》 The number of appointments on the official website has exceeded ten million , Quickly rush to apple after going online App store Top of the free list . As of the date of publication , Seven wheat data display 《 The love between light and night 》 The cumulative download volume of Android is estimated to exceed 3979 Ten thousand times ,iPhone And iPad The total download volume is estimated to exceed 291 Ten thousand times .
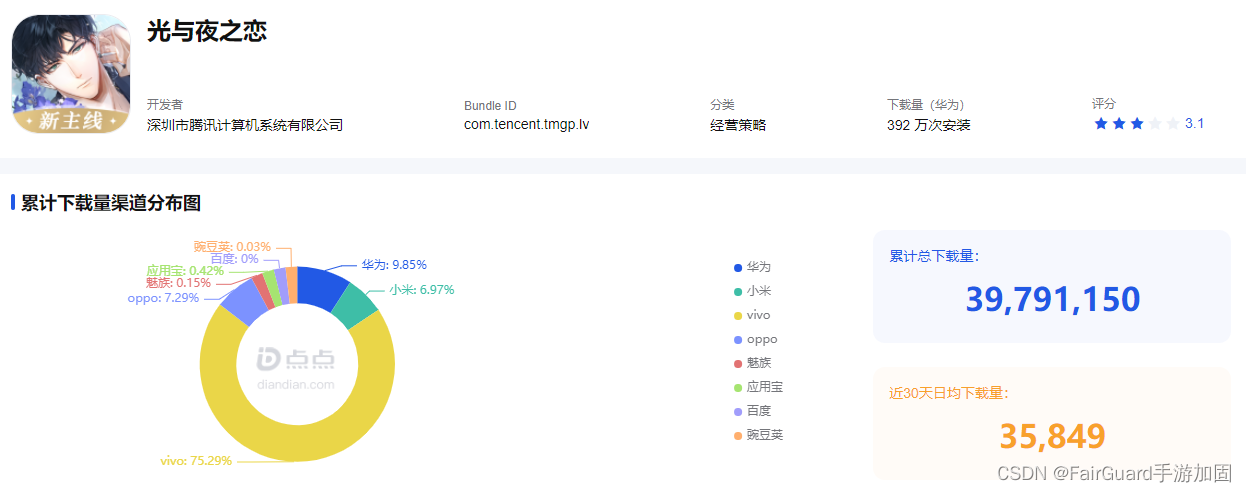
《 The love between light and night 》 Android downloads , Data source: Qimai data
And this game with tens of millions of downloads , But because of being unpacked , Caused an unprecedented network storm .
In the game 《 The love between light and night 》 in , The heroine played by the player can attack many male protagonists . It was one of the men who was unpacked this time “ Xia Mingxing ” Birthday card for , It was supposed to be 5 month 22 The information released on the th was released on the social platform by the unpacker nearly a month in advance .
It's like you plan the proposal process without telling your girlfriend , And the other party already knows the details , This sense of surprise and failure triggered the wrath of fans , One after another, they asked the government to deal with the unpackers by legal means .
After the official handed the lawyer's letter to the unpacker , But it caused the dissatisfaction of other players , Before, when other hero game resources were unpacked, the official only sent a Weibo warning , In this way “ Differential treatment ” Let them not accept . thus , The curse war between different camps in a game circle has begun , The official is caught in it , disoriented .
Another Tencent product “ National level ” Mobile Games 《 Glory of Kings 》 I was also troubled by unpacking , In the game “ Five tigers will ”“ Four beauties ” Series of skin Skill effects and some modeling were revealed on major platforms , It triggered players' criticism of the official production level , Finally, overturn and redo , The previous plan was in vain , It's a huge loss .
Unpacking occurs frequently , How to protect game resources ?
Unpacking will have a huge impact on game operation , There are even hidden dangers of game security , Pictures in game resources 、 Video or script , Are the intellectual property of the game , If it is unlocked by the cracker or competitor , Get the content , The impact on the game will be incalculable .
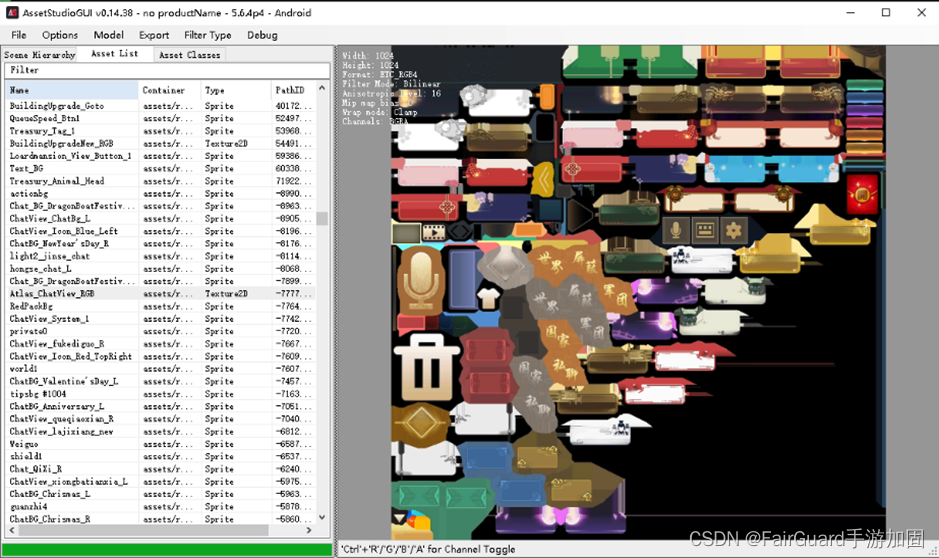
《 halo 4》 Art materials have been plagiarized
Besides , If game resources are modified, they will also produce plug-in effects .
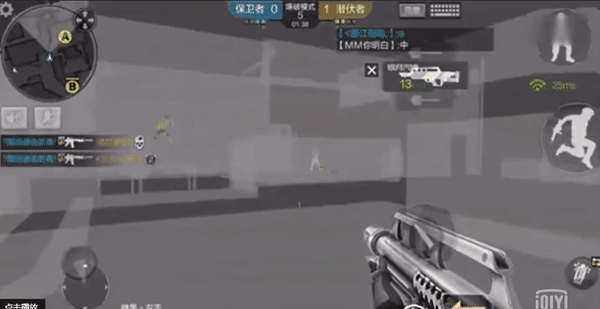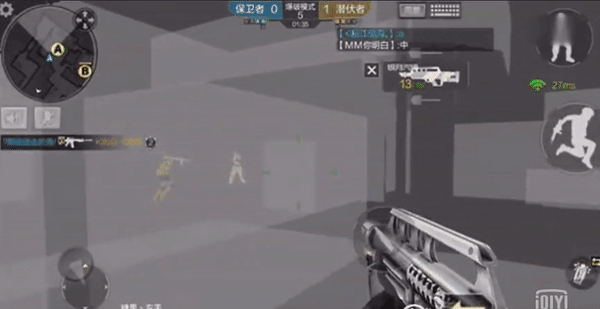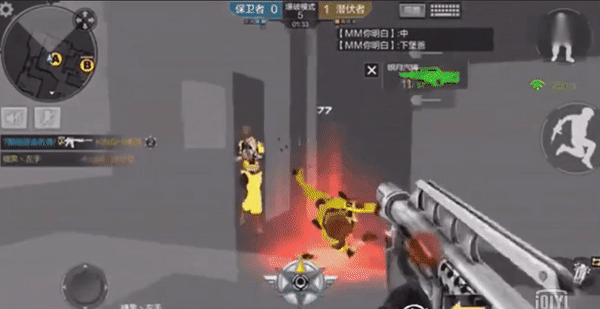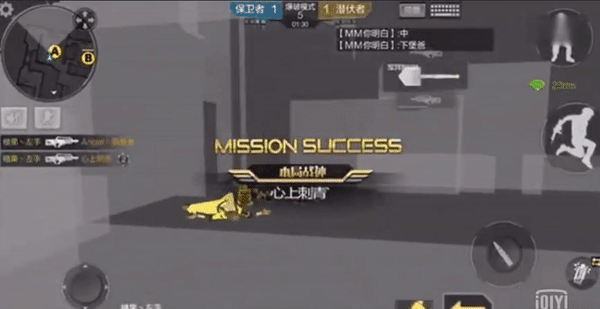
some FPS The game resource material has been modified to be transparent , Realize the perspective effect
Many games now recognize that Assetbundle The importance of resource encryption , But how to encrypt game resources at the same time , Decryption costs very little , This problem has become the pain point of many games .
FairGuard The R & D team spends a lot of time on unity The engine does black box analysis , Make sure. Assetbundle Loading mechanism and its file structure . The following encryption scheme is formulated :
First of all, through the right Assetbundle File structure analysis , Find the core file block of the resource file , Encrypt the core file block , Then when the game is running , Yes unity engine Assetbundle Loading time for burying point , Decrypt the core file block at the buried point .
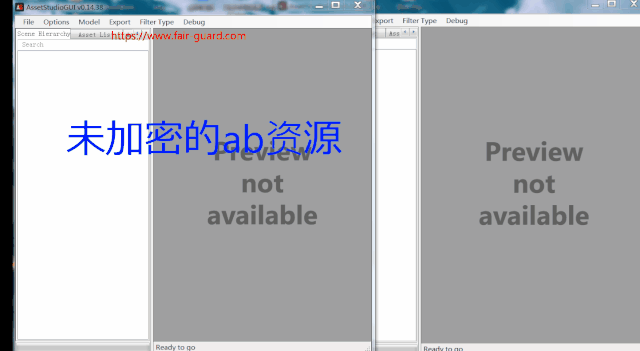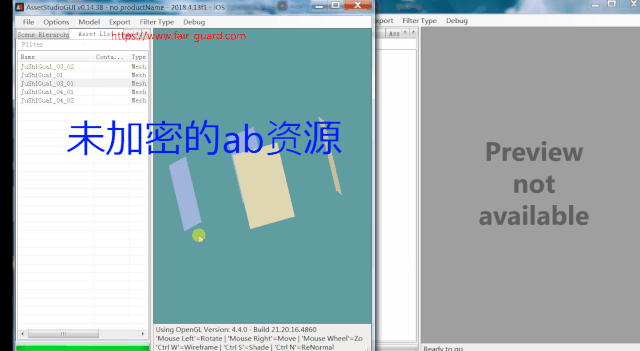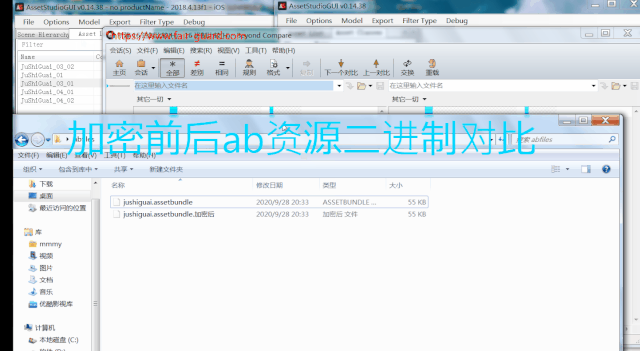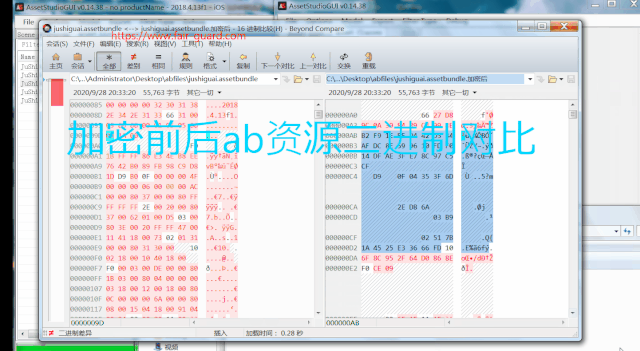
Before and after encryption Assetbundle Resource effect comparison
边栏推荐
- sys.argv
- ROS编译 调用第三方动态库(xxx.so)
- Online yaml to CSV tool
- What is CSRF (Cross Site Request Forgery)?
- 【ROS】usb_cam相机标定
- 根据csv文件某一列字符串中某个数字排序
- Browser thread
- The ECU of 21 Audi q5l 45tfsi brushes is upgraded to master special adjustment, and the horsepower is safely and stably increased to 305 horsepower
- C language custom type: struct
- IOT -- interpreting the four tier architecture of the Internet of things
猜你喜欢
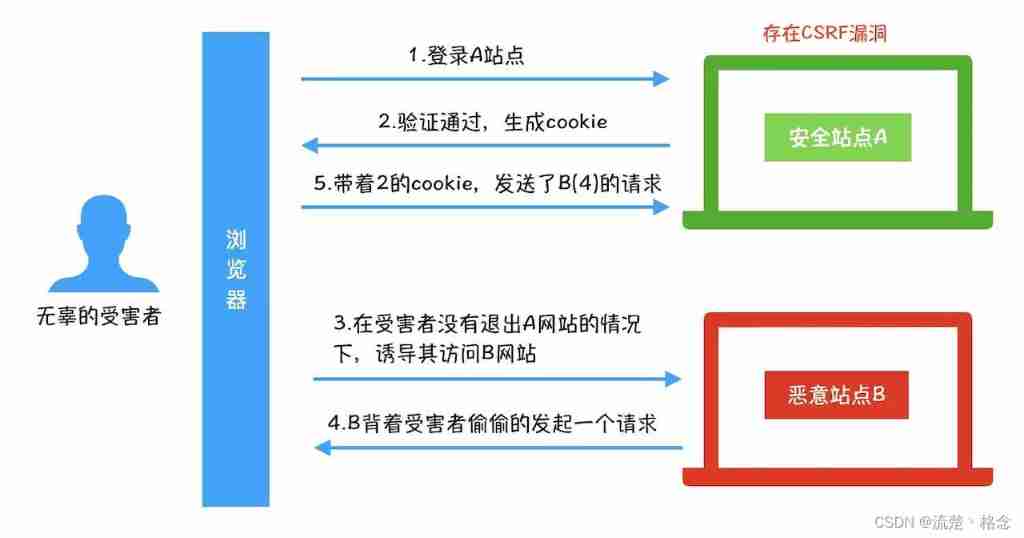
What is CSRF (Cross Site Request Forgery)?
MySQL learning records 12jdbc operation transactions
Circular reference of ES6 module

Beijing invitation media
Image,cv2读取图片的numpy数组的转换和尺寸resize变化
【MySQL】鎖
Process of obtaining the electronic version of academic qualifications of xuexin.com
marathon-envs项目环境配置(强化学习模仿参考动作)
Online yaml to CSV tool
Yyds dry goods inventory three JS source code interpretation eventdispatcher
随机推荐
[MySQL] database stored procedure and storage function clearance tutorial (full version)
704 二分查找
egg. JS directory structure
Permutation and combination function
pcd转ply后在meshlab无法打开,提示 Error details: Unespected eof
Deep analysis of C language data storage in memory
FairGuard游戏加固:游戏出海热潮下,游戏安全面临新挑战
The ECU of 21 Audi q5l 45tfsi brushes is upgraded to master special adjustment, and the horsepower is safely and stably increased to 305 horsepower
visdom可视化实现与检查介绍
egg. JS getting started navigation: installation, use and learning
String to leading 0
CISP-PTE实操练习讲解
leetcode刷题 (5.29) 哈希表
Golang force buckle leetcode 1020 Number of enclaves
China vanadium battery Market Research and future prospects report (2022 Edition)
移位运算符
2022.02.13 - NC002. sort
Synchronized solves problems caused by sharing
优秀的软件测试人员,都具备这些能力
[brush questions] top101 must be brushed in the interview of niuke.com
