当前位置:网站首页>Hash table and full comments
Hash table and full comments
2022-07-07 02:36:00 【@Landscape post yuan】
#include "stdio.h"
#include "stdlib.h"
typedef struct{
int* elem; // Data element storage base address , Assign arrays dynamically
int count; // Number of current data elements
}HashTable;
int m=0; // Hash table length , Global variables
//HASHSIZE Define the hash table length as the length of the array
typedef enum { // Or not typedef, take Status On the front , The function called is preceded by enum
OK=1,SUCCESS=1,UNSUCCESS=0,HASHSIZE=12,NULLKEY=-32768
}Status;
Status InitHashTable(HashTable *H){ // Initialize hash table
int i;
m=HASHSIZE;
H->count=m;
H->elem=(int *)malloc(m*sizeof(int));
for(i=0;i<m;i++)
H->elem[i]=NULLKEY;
return OK;
}
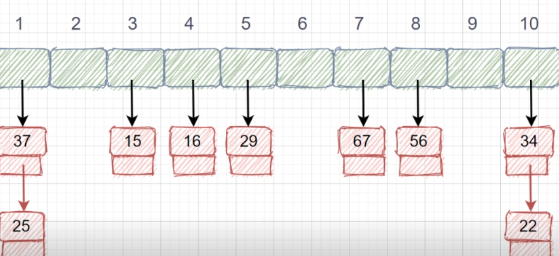
int Hash(int key){ // Hash function key amount to qq account number
return key%m; // Division and remainder Return key
}
void InsertHash(HashTable* H,int key){ // Insert keywords into hash table
int addr=Hash(key); // Find the hash address
printf("The subscript of the inserted array position:%d\n",addr);
while(H->elem[addr]!=NULLKEY) // If it's not empty , Then conflict
addr=(addr+1)%m; // Develop linear detection of addressing
H->elem[addr]=key; // Until there is a space to insert keywords
}
Status SearchHash(HashTable H,int key,int* addr){ // Insert keywords into hash table
*addr=Hash(key); // Find the hash address
while(H.elem[*addr]!=key){ // If it's not empty , Then conflict
*addr=(*addr+1)%m; // Develop linear detection of addressing
if(H.elem[*addr]==NULLKEY||*addr==Hash(key)){
// If the loop goes back to the origin
// Key does not exist
return UNSUCCESS;
}
}
return SUCCESS;
}
int main(){
int i=0;
HashTable H;
InitHashTable(&H);
while(i<HASHSIZE){
InsertHash(&H,i); // Insert 12 Number
i++;
}
int key=0;
int addr; // Return the function of subscript
while(key<HASHSIZE){
if(SearchHash(H,key,&addr)==SUCCESS){ // Search the position of this number
printf("Print the position of this number:%d\n",addr);
} else{
printf("UNSUCCESS\n");
}
key++;
}
}
边栏推荐
- 4 -- Xintang nuc980 mount initramfs NFS file system
- postgresql 之 数据目录内部结构 简介
- [server data recovery] data recovery case of a Dell server crash caused by raid damage
- leetcode:5. Longest palindrome substring [DP + holding the tail of timeout]
- Apifox,你的API接口文档卷成这样了吗?
- [Mori city] random talk on GIS data (II)
- C#/VB.NET 删除Word文檔中的水印
- MySQL
- Alibaba cloud middleware open source past
- C语言练习题_1
猜你喜欢
![[unity notes] screen coordinates to ugui coordinates](/img/e4/fc18dd9b4b0e36ec3e278e5fb3fd23.jpg)
[unity notes] screen coordinates to ugui coordinates

【森城市】GIS数据漫谈(二)
![leetcode:5. Longest palindrome substring [DP + holding the tail of timeout]](/img/62/d4d5428f69fc221063a4f607750995.png)
leetcode:5. Longest palindrome substring [DP + holding the tail of timeout]
B站6月榜单丨飞瓜数据UP主成长排行榜(哔哩哔哩平台)发布!
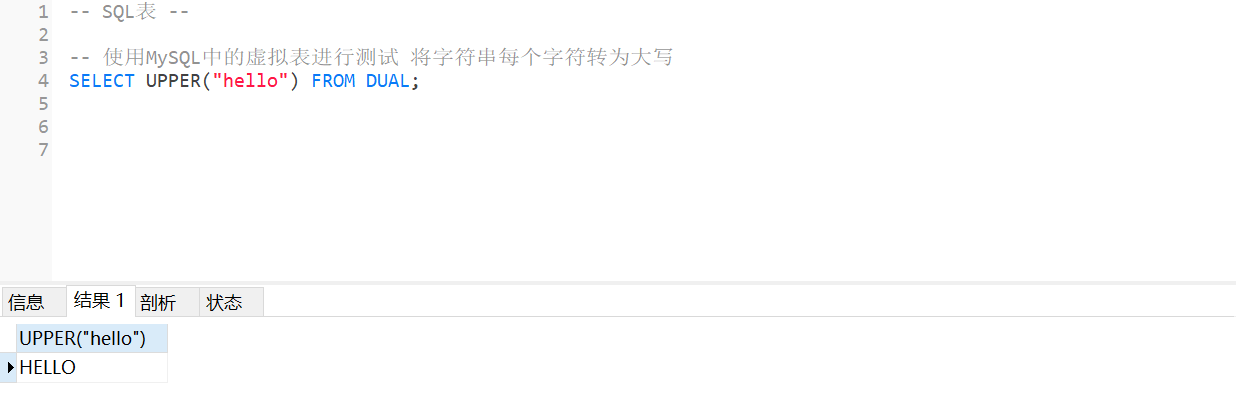
MySQL --- 常用函数 - 字符串函数
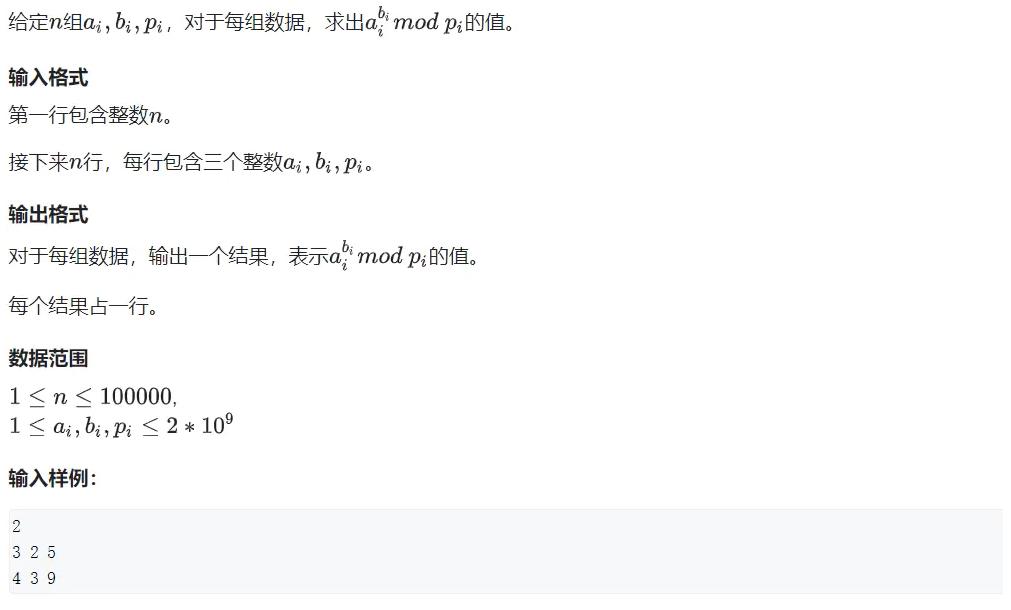
数论 --- 快速幂、快速幂求逆元
NuScenes数据集关于Radar数据的统计
电气工程及其自动化
测试优惠券要怎么写测试用例?

1 -- Xintang nuc980 nuc980 porting uboot, starting from external mx25l
随机推荐
Untiy文本框的代码换行问题
所谓的消费互联网仅仅只是做行业信息的撮合和对接,并不改变产业本身
Infrared camera: juge infrared mag32 product introduction
CSDN 夏令营课程 项目分析
STM32项目 -- 选题分享(部分)
The boss is quarantined
记一次JAP查询导致OOM的问题分析
【Node学习笔记】chokidar模块实现文件监听
基于ensp防火墙双击热备二层网络规划与设计
Douban average 9 x. Five God books in the distributed field!
MySQL
Halcon实例转OpenCvSharp(C# OpenCV)实现--瓶口缺陷检测(附源码)
ODBC database connection of MFC windows programming [147] (with source code)
This week's hot open source project!
6-6 vulnerability exploitation SSH security defense
Yyds dry goods inventory # solve the real problem of famous enterprises: maximum difference
leetcode:5. Longest palindrome substring [DP + holding the tail of timeout]
Web3's need for law
go swagger使用
Web3对法律的需求