当前位置:网站首页>10 schemes to ensure interface data security
10 schemes to ensure interface data security
2022-07-07 15:50:00 【Java confidant_】
Preface
In our daily development , How to ensure the security of interface data ? Personally feel , Interface data security assurance process , Mainly reflected in these aspects : One is The data transfer Safety in the process , And the data arrives at the server , how Identifying data , The last point is Security of data storage . Today, I want to talk to you about how to ensure the security of interface data 10 A plan .
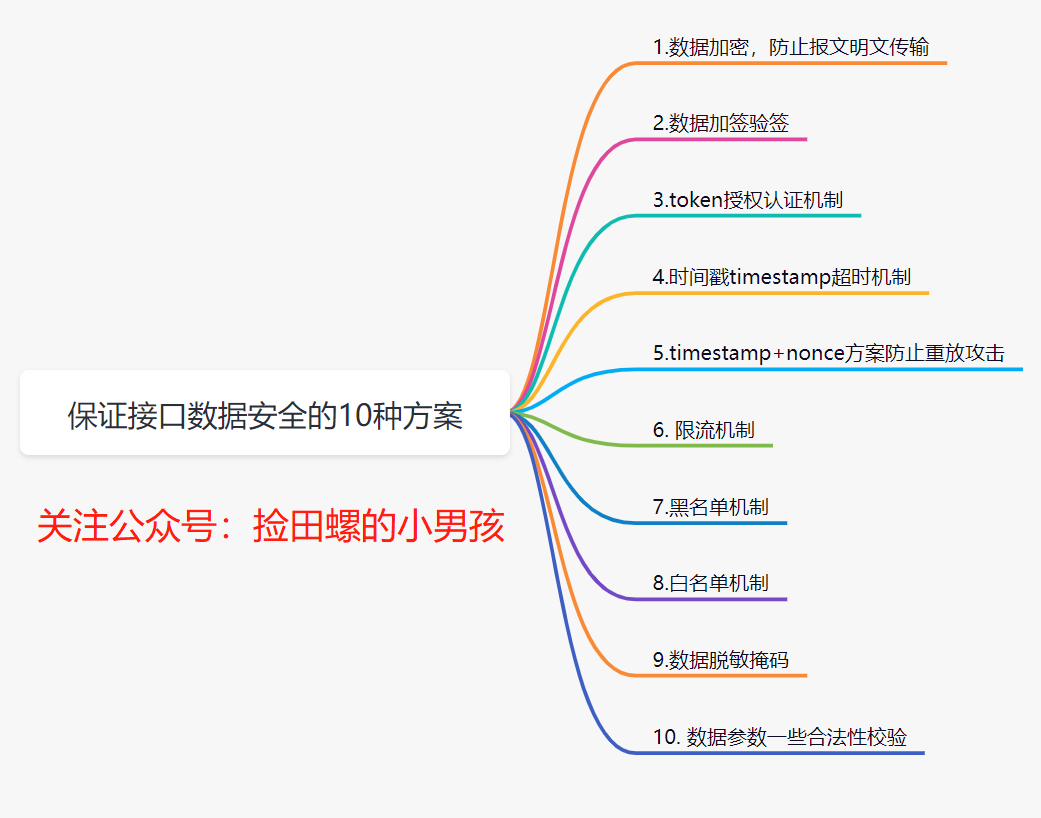
1. Data encryption , Prevent the transmission of newspaper messages .
We all know , Data in the process of network transmission , It's easy to be caught . If you are using http agreement , Because it is transmitted in clear text , Users' data can be easily obtained by others . So we need to encrypt the data .
1.1 How to encrypt data ?
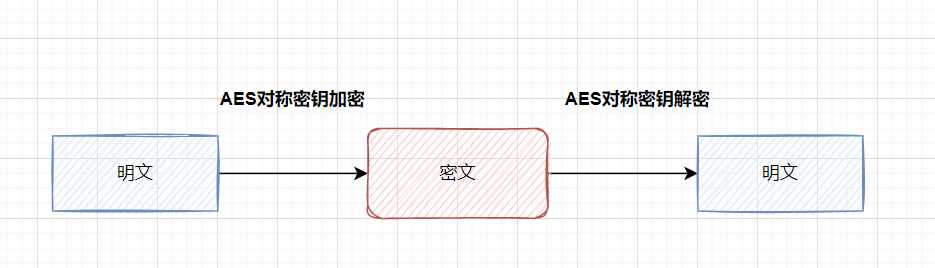
Common implementation methods , That's right Key fields encryption . such as , You have a login interface , You can be right password encryption . What encryption algorithm is generally used ? Easy to use Symmetric encryption algorithm ( Such as AES) To encrypt and decrypt , Or hash algorithm processing ( Such as MD5).
What is? Symmetric encryption : An encryption algorithm that uses the same key for encryption and decryption .
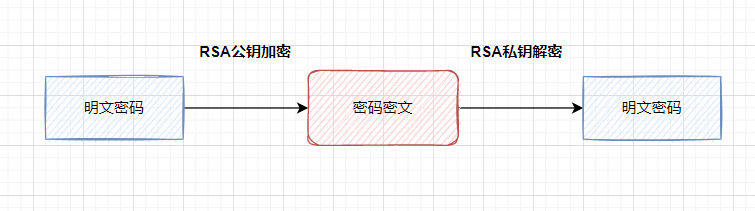
Asymmetric encryption : Asymmetric encryption algorithm requires two keys ( Public key and private key ). Public key and private key exist in pairs , If you encrypt data with a public key , Only the corresponding private key can be decrypted .
A safer way , Just use Asymmetric encryption algorithm ( Such as RSA perhaps SM2), Public key encryption , Private key decryption .
If you want to encrypt all fields , It is generally recommended to use https agreement .https In fact, in the http and tcp Add a layer of encryption between SSL.
1.2 friends , Do you remember https How about the principle of ?
Interview is also often asked , as follows :
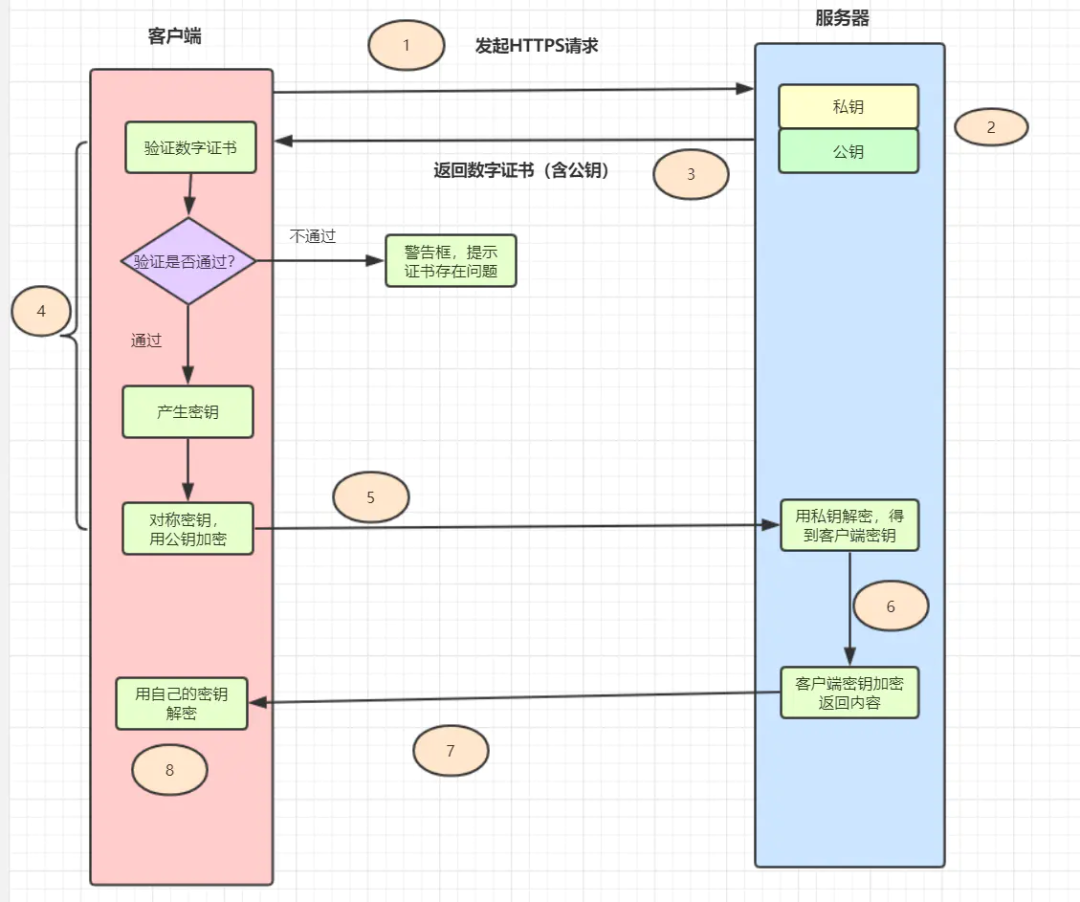
Client initiated Https request , Connected to the server 443 port .
The server must have a set of digital certificates ( The certificate contains a public key 、 Certification authority 、 Expiration date, etc ).
The server sends its own digital certificate to the client ( The public key is in the certificate , The private key is held by the server ).
After the client receives the digital certificate , Will verify the validity of the certificate . If the certificate is verified , A random symmetric key will be generated , Encrypt with the public key of the certificate .
The client sends the encrypted key of the public key to the server .
After the server receives the ciphertext key sent by the client , Use your previously reserved private key to decrypt it asymmetrically , After decryption, you get the client's key , Then use the client key to encrypt the returned data symmetrically , The data transmitted by maozi are ciphertext .
The server returns the encrypted ciphertext to the client .
When the client receives , Decrypt it symmetrically with your own key , Get the data returned by the server .
Daily business , Data transmission encryption , use https That's all right. , If the safety requirements are high , Such as login and registration , Need to transmit password , The password can be used RSA And so on , Encrypt password . If your business , The security requirements are very high , You can simulate https This process , To message , Do encryption and decryption again .
2. Data signature verification
Data message signature verification , yes Common means to ensure the safety of data transmission , It can ensure that the data is in No tampering during transmission . I used to do it Enterprise transfer system , Just use the additional signature to verify the signature .
2.1 What is countersigning and signature verification ?
Data signature : use Hash Algorithm ( Such as
MD5, perhaps SHA-256) Generate message summary from original request parameters , Then encrypt the digest with the private key , Get the digital signature corresponding to this messagesign( This process is The signature of the ). Generally speaking , The requesting party will send Digital signature and original message Send it to the receiver .
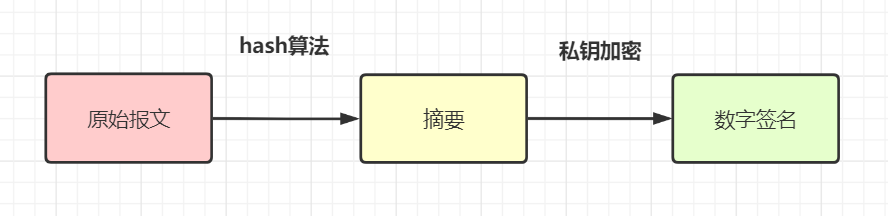
attestation : The receiver gets the original message and digital signature (
sign) after , use The same Hash Algorithm ( For example, they all use MD5) Generate a summary from the message A. in addition , Decrypt the digital signature with the public key provided by the other party , Get a summary B, contrast A and B Are they the same? , You can know whether the message has been tampered with .
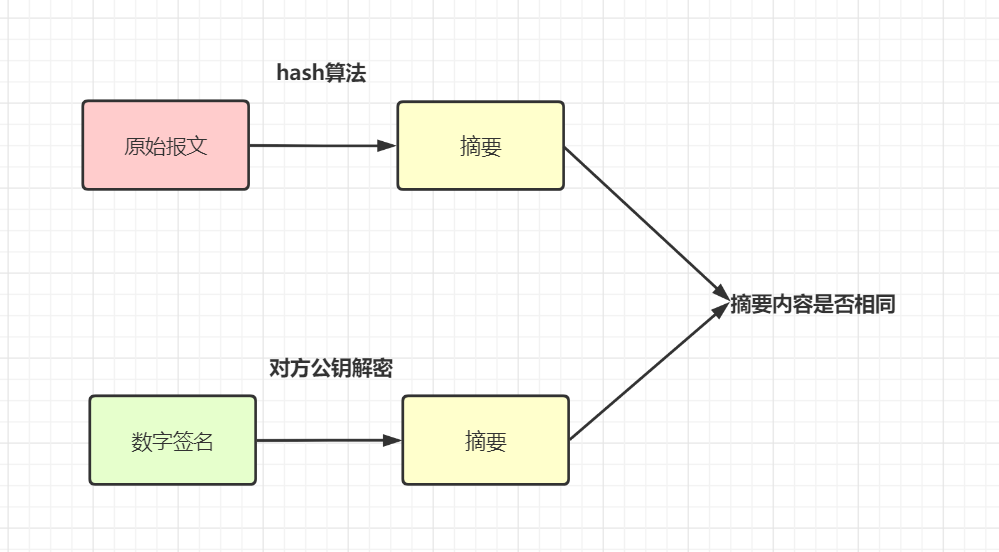
Actually The signature of the , I understand , The request parameters , According to certain rules , utilize hash Algorithm + The encryption algorithm generates a The only label sign. If the signature is checked , That is to treat the request parameters according to the same rules , Then use the same hash Algorithm , And the corresponding key decryption processing , To compare whether this signature is consistent .
Another example , Some partners achieve this , Set all non empty parameters ( Contains a package
AccessKey, Unique developer ID ) In ascending order , Then splice another oneSecretKey( This is only used for local encryption , Not participating in network transmission , It is only used as a signature inside ), Get onestringSignTempValue , Last use MD5 operation , obtainsign.After the server receives the message , Can check , Only by having a legal identity
AccessKeyAnd signatureSigncorrect , Only then . This solves the problem of authentication and parameter tampering , If the request parameters are hijacked , Because the hijacker can't getSecretKey( For local encryption only , Not participating in network transmission ), He can't forge a legal request
2.2 With https Wait for encrypted data , Why is it necessary to add a signature for verification
Some friends may have questions , Signature verification is mainly to prevent data from being tampered with during transmission , If it's all used https The next protocol encrypts the data , Why can it be tampered with ? Why is it necessary to add a signature for verification ?
The data was encrypted during transmission , Theoretically , Even if caught , And the data won't be tampered with . however https It's not absolutely safe Of course . There's another point :
httpsThe encrypted part is only on the Internet , Then there are many services that jump to each other on the intranet , Countersignature can also be in This is guaranteed not to be tampered with by intermediaries , Therefore, the interface development with high security requirements for general transfer , Need to be Additional signature
3.token Authorization and authentication mechanism
Daily development , Our website or APP, Are all need The user login Of . So if it is Non login interface , How to ensure safety , How to confirm the user's identity ? have access to token Authorization mechanism .
3.1 token Authorized authentication scheme
token Authorized authentication scheme : The user enters the user name and password on the client , Click to log in , The server will verify the password successfully , A unique value will be returned to the client token, And will token In the form of key value pairs stored in the cache ( It's usually Redis) in . The subsequent client should take this with it for all operations requiring authorization module token, After the server receives the request , to token verification , If token There is , It shows that it is a legal request .
token The login authorization flow chart is as follows :
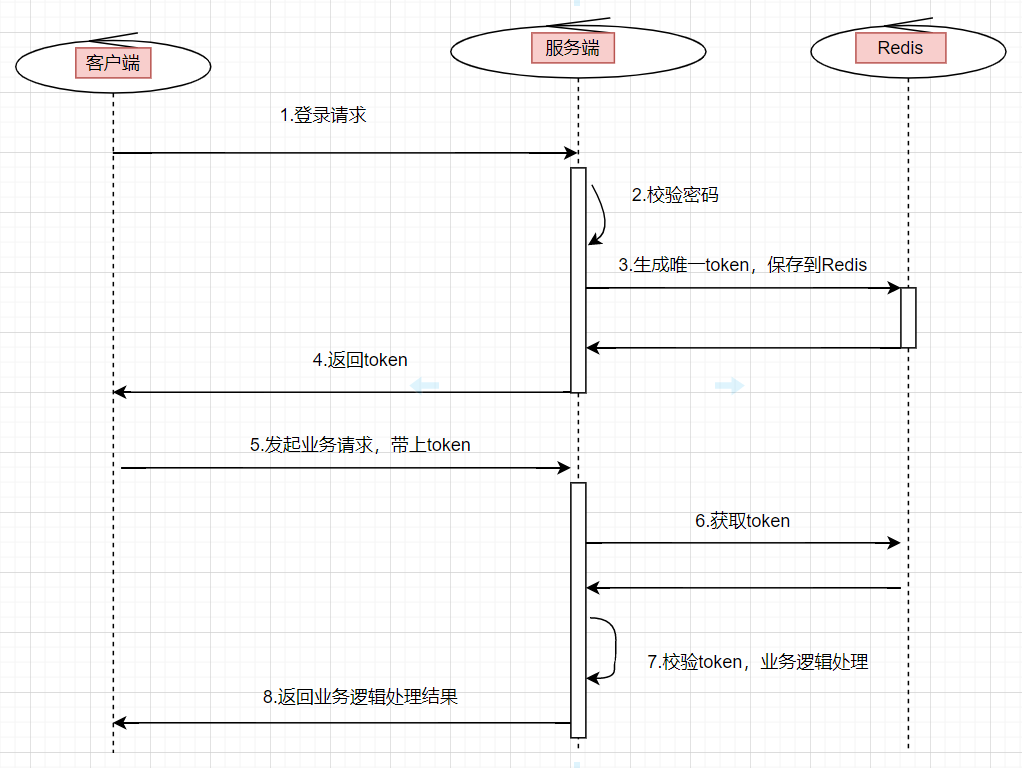
The user enters the user name and password , Initiate a login request
The server verifies the password , If the verification passes , Generate a globally unique
token.take
tokenStored inredisin , amongkeyyestoken,valueyesuserIdOr user information , Set an expiration time .Put this
tokenReturn to the clientWhen the user initiates other business requests , You need to bring this
tokenBackground services will uniformly intercept interface requests , Conduct
tokenValidation , And get user information from it , For subsequent business logic . Iftokennon-existent , Indicates that the request is invalid .
3.2 How to ensure token The safety of the ?token Hijacked ?
How can we guarantee token What about the safety of the company ?
for instance , If I get token, Is it possible to call any interface on the server side ? We can consider from these aspects :
token Set a reasonable period of validity
Use https agreement
token You can encrypt again
If you are accessing sensitive information , Simply add token It's not enough. , Usually, the white list will be configured
Speaking of token, Some friends may think of jwt, namely (JSON Web Token), In fact, it is token A kind of . Interested friends can go to know about it .
4. Time stamp timestamp Timeout mechanism
Data is easy to capture , Suppose we use https And countersignature , Even if the middleman catches the data message , It can't see the real data . But some lawbreakers , He doesn't care about the real data , Instead, you get the captured packets directly , Make a malicious request ( such as DOS attack ), To bring down your system .
We can introduce Timestamp timeout mechanism , To ensure interface security . Namely : Every time a user requests it, he will bring a timestamp of the current time timestamp, The server receives timestamp after , Decrypt , After passing the examination , Compare with the current time of the server , If the time difference is greater than a certain time ( such as 3 minute ), The request is considered invalid .
5.timestamp+nonce The scheme prevents replay attacks
The timestamp timeout mechanism is also vulnerable , If it's in Within the time difference , Replay attacks by hackers , That won't work . have access to timestamp+nonce programme .
nonce Refers to a unique random string , Used to identify each signed request . We can send every request nonce Parameters are stored in a “set aggregate ” in , Or maybe json Format is stored in a database or cache . Each processing HTTP When asked , First of all, judge the nonce Whether the parameter is in the “ aggregate ” in , If there is an illegal request .
However, for servers , Keep forever nonce The price is very high . Can combine timestamp To optimize . because timstamp Parameter for more than 3min Request , It's considered illegal to ask , So we just need to store 3min Of nonce Parametric “ aggregate ” that will do .
6. Current limiting mechanism
If users are real users , He maliciously calls the interface frequently , Want to bring down your system ? In this case, it is necessary to access current limiting .
have access to Guava Of RateLimiter Stand alone current limiting , You can also use Redis Distributed current limitation , You can also use Alibaba open source components sentinel Current limiting . for instance , How many requests can you accept in a minute .
7. Blacklist mechanism
If malicious requests from real users are found , You can set up a blacklist mechanism , Black the user . General situation , There will be some competitors , Or users who are not bad intentions , Want to do your system . therefore , In order to ensure safety , Generally, our business system , There needs to be a blacklist mechanism . For blacklist initiated requests , Just return the error code directly .
8. White list mechanism
With the blacklist mechanism , You can also set up a white name single machine system . The enterprise transfer system I used to be responsible for , If an outside merchant wants to access our system , You need to apply for the online white list in advance . At that time, O & M will apply for IP Internet white list , Only the requests in the white list , To access our transfer system .
9. Data desensitization mask
For passwords , Or cell phone number 、 Sensitive information such as ID card , Generally, desensitization mask is required to display , If it's a password , It also needs to be encrypted and saved to the database .
For mobile phone numbers 、 ID card information , Daily development , When checking logs , What you see should be masked . The purpose is to try not to disclose these user information , Although only development and operation and maintenance can read the log , But it still needs to be prevented , Do masking .
Save the password to the database , We definitely can't directly save in plaintext . The simplest also needs MD5 Deal with it and save it ,Spring Security Medium BCryptPasswordEncoder It's fine too , Its bottom layer is SHA-256 + Random salt + secret key Encrypt password , and SHA and MD The series is the same , All are hash Algorithm of abstract class .
10. Check the validity of data parameters .
Security assurance of interface data , We also need our system , There is a data validity check , In a nutshell Parameter checking , For example, the length of ID card , Length of mobile phone number , Is it a number, etc .
summary
This paper introduces 10 A scheme to ensure the security of interface data . friends , If there are other plans , You can comment in the message area , Exchange and study together .
recommend
Technical involution group , Learn together !!

PS: Because the official account platform changed the push rules. , If you don't want to miss the content , Remember to click after reading “ Looking at ”, Add one “ Star standard ”, In this way, each new article push will appear in your subscription list for the first time . spot “ Looking at ” Support us !
边栏推荐
- Do not use memset to clear floating-point numbers
- How to build your own super signature system (yunxiaoduo)?
- 15. Using the text editing tool VIM
- Webcodecs parameter settings -avc1.42e01e meaning
- Jacobo code coverage
- Annexb and avcc are two methods of data segmentation in decoding
- [quick start of Digital IC Verification] 24. AHB sramc of SystemVerilog project practice (4) (AHB continues to deepen)
- 避坑:Sql中 in 和not in中有null值的情况说明
- 有一头母牛,它每年年初生一头小母牛。每头小母牛从第四个年头开始,每年年初也生一头小母牛。请编程实现在第n年的时候,共有多少头母牛?
- C Alibaba cloud OSS file upload, download and other operations (unity is available)
猜你喜欢
Super simple and fully automated generation super signature system (cloud Xiaoduo minclouds.com cloud service instance), free application in-house test app distribution and hosting platform, maintenan
webgl_ Enter the three-dimensional world (2)
Ida Pro reverse tool finds the IP and port of the socket server

有钱人买房就是不一样

全日制研究生和非全日制研究生的区别!
【数字IC验证快速入门】29、SystemVerilog项目实践之AHB-SRAMC(9)(AHB-SRAMC SVTB Overview)
【数字IC验证快速入门】20、SystemVerilog学习之基本语法7(覆盖率驱动...内含实践练习)
Gd32 F3 pin mapping problem SW interface cannot be burned
Mesh merging under ue4/ue5 runtime
UE4 exports the picture + text combination diagram through ucanvasrendertarget2d
随机推荐
Three. JS introductory learning notes 0: illustration of how webgl and threejs work
【兰州大学】考研初试复试资料分享
numpy---基础学习笔记
Implementation of crawling web pages and saving them to MySQL using the scrapy framework
How to understand that binary complement represents negative numbers
#HPDC智能基座人才发展峰会随笔
Three. JS introductory learning notes 00: coordinate system, camera (temporarily understood)
OpenGL common functions
A wave of open source notebooks is coming
Detailed explanation of unity hot update knowledge points and introduction to common solution principles
Do you know the relationship between the most important indicators of two strong wind control and the quality of the customer base
Webcodecs parameter settings -avc1.42e01e meaning
【数字IC验证快速入门】22、SystemVerilog项目实践之AHB-SRAMC(2)(AMBA总线介绍)
【Markdown语法高级】让你的博客更精彩(四:设置字体样式以及颜色对照表)
[quick start of Digital IC Verification] 18. Basic grammar of SystemVerilog learning 5 (concurrent threads... Including practical exercises)
[Lanzhou University] information sharing of postgraduate entrance examination and re examination
Vite path alias @ configuration
webgl_ Graphic transformation (rotation, translation, zoom)
Create lib Library in keil and use lib Library
[quick start of Digital IC Verification] 25. AHB sramc of SystemVerilog project practice (5) (AHB key review, key points refining)