当前位置:网站首页>Things about data storage 2
Things about data storage 2
2022-07-07 05:47:00 【It's Yi'an】
Part1: Original code , Inverse code , Complement code Signed number ? Sign bit Value bits integer
According to what rules is the data stored in the computer ? So let's see , Original code , Inverse code , Complement code .
According to the definition, the negative integer original code with sign, the inverse code and complement are different , Unsigned and positive numbers are the same .
The first bit is the sign bit , It's all used 0 Express positive ,1 Negative . The numerical digits are all different
Part2:-10 Integers Complement code Why? adder Unification of addition and subtraction
Let's give you an example int:-10, We know that an integer occupies 4 Bytes
00000000 00000000 00000000 00000000; empty : The general situation is not 0
10000000 00000000 00000000 00001010; Original code
11111111 11111111 11111111 11110101; Inverse code
11111111 11111111 11111111 11110110; Complement code
ff ff ff f6; Hexadecimal representation
In the computer , Integer data is represented by hexadecimal complement
Why do this ?
This is related to the structure of the computer , As I thought before , Use signals to represent the form of numbers , These figures will be used after all , The basic algorithm between numbers , How to realize addition and subtraction , It's easy to think about it with us 1+1, be equal to 2, How to add and subtract in the computer ?
Add , Before learning the principles of computer composition , First we know that addition is the addition of signals at two positions , Use a component , When both are 1 If yes, it becomes 0, At the same time, the latter one becomes 1(0) Or 0(1). What about subtraction 1 become 0,0 become 1 Do you ? This is the same as addition ? How to distinguish ? In those days , When the complement of the original code has not appeared , To solve this problem , Someone put forward the concept of original code, inverse code and complement , a pile 101010 Explore , Now it seems very reasonable , Know this rule , It's a bit like the Berlin Wall . The existence of complement allows subtraction to do addition .
Part3:
Large and small end Memory block Low address Pattern The way Byte order
When we are opening up space , The opened space is called memory block , By number , It has high address side and low address side , The same data 0x11223344,0x High position … status .
We put it in memory block in bytes , Obviously, there are many sorting methods , The two most used methods are to put the high address in the low place , Low address to high and high address to high , Put the low address low , Two ways , The former is called big end mode , The latter is called small end mode . Because it is put in bytes , There is the word byte order .
Part4:
char %d Improve the overall shape %u
It was said before char Type can be put into integer , but char It takes only one byte , When an integer data is put into char In the middle of the day , Press 32 Bits are first converted to complements , Only the last byte put in is the low byte . When char To use %d When the output , We need to improve the integer first , If the first one is 1, Make up 1 To 32 position , if 0 Then fill 0( Only negative integers complement 1, Because its original code, inverse code and complement are different )
%u It's an unsigned integer , Judge before complement conversion ( After integer lifting )
Part5:
char Range Complement code With or without symbols repair 1000 0000 circle +1 Change sign 128
char Types are divided into signed and unsigned , It is also stored in memory in the form of complement 、
The signed range is ·-128—>127:01111111(127)+1=10000000(-128)
The unsigned range is 0à255:00000000(0)à11111111(255)
We know that the complement in memory needs to be reduced by one , But symbolic ·10000000 It will automatically convert here -128. And because of the complement , ad locum 127+1=-128.
边栏推荐
- Differences and introduction of cluster, distributed and microservice
- 软件测试面试技巧
- Taobao commodity details page API interface, Taobao commodity list API interface, Taobao commodity sales API interface, Taobao app details API interface, Taobao details API interface
- Educational Codeforces Round 22 B. The Golden Age
- Codeforces Round #416 (Div. 2) D. Vladik and Favorite Game
- Différenciation et introduction des services groupés, distribués et microservices
- Lombok插件
- 架构设计的五个核心要素
- 集群、分布式、微服务的区别和介绍
- Dj-zbs2 leakage relay
猜你喜欢
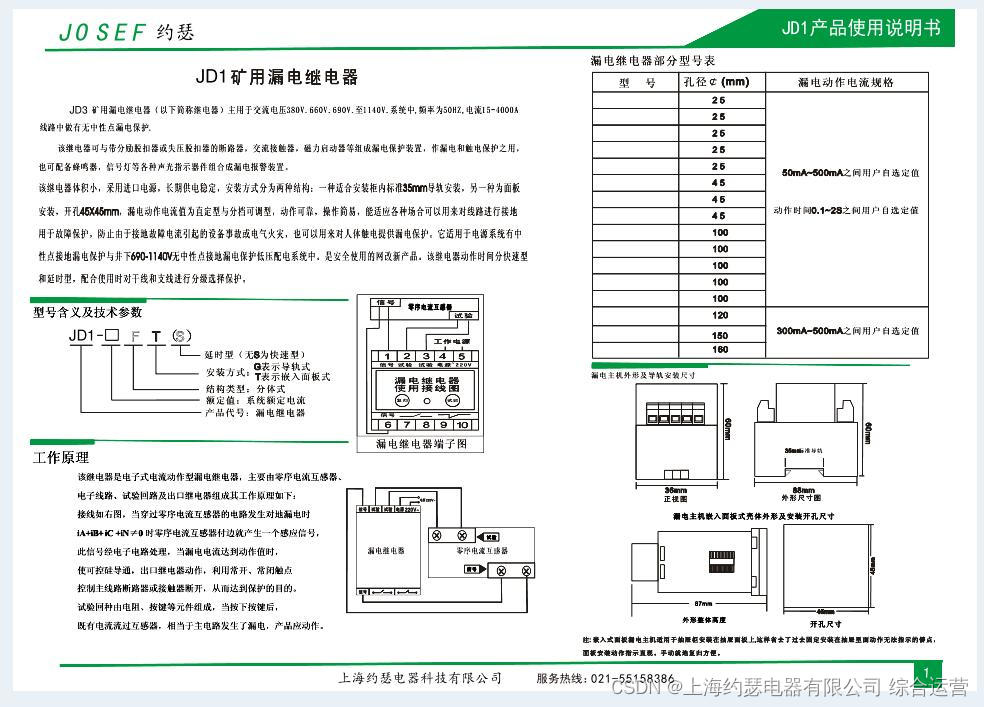
Leakage relay jd1-100
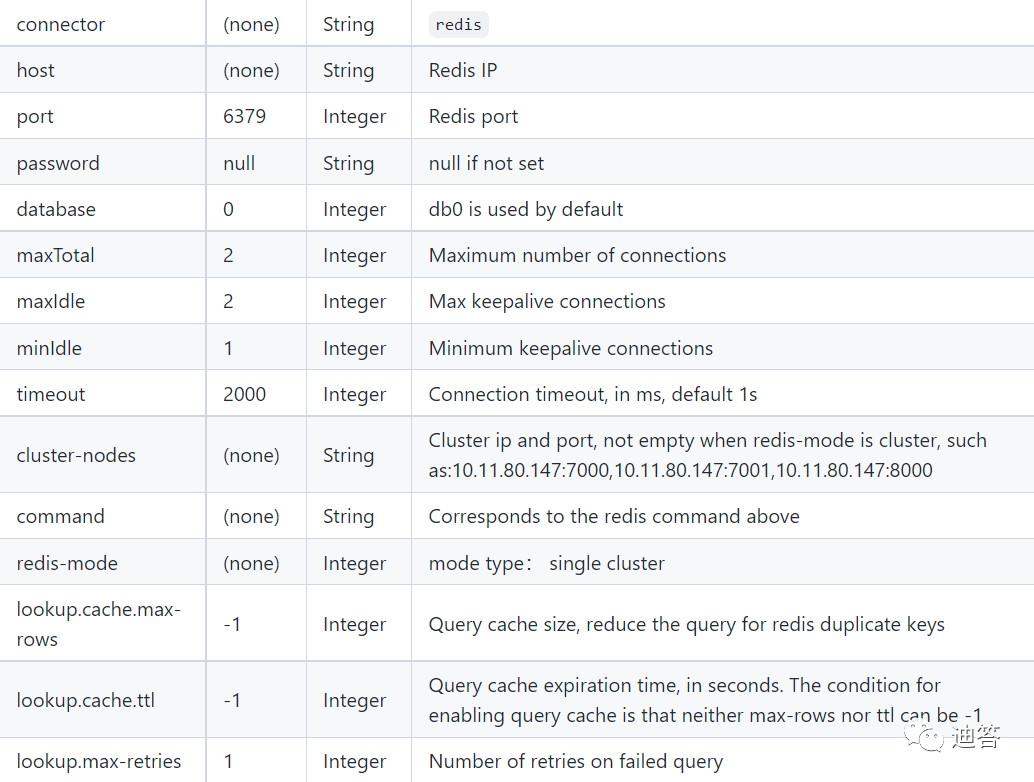
Flink SQL 实现读写redis,并动态生成Hset key
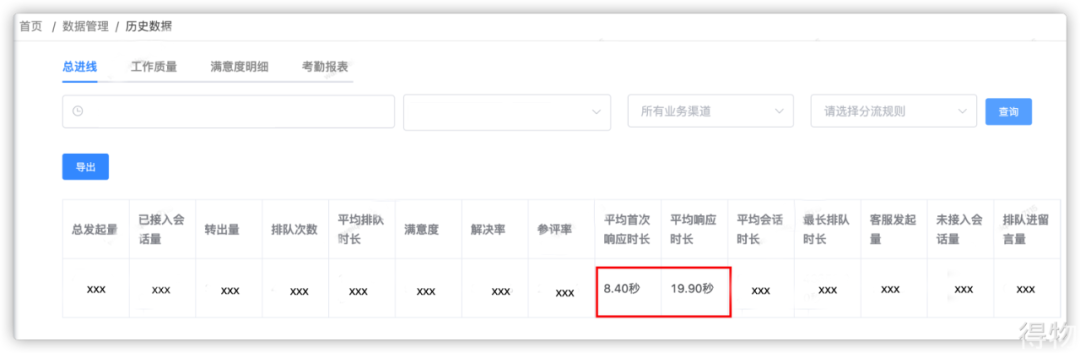
Get the way to optimize the one-stop worktable of customer service
bat 批示处理详解
分布式事务介绍
![Paper reading [semantic tag enlarged xlnv model for video captioning]](/img/e3/633f6aac7a51ad7b3dc0e45dbe1f60.png)
Paper reading [semantic tag enlarged xlnv model for video captioning]
Unity keeps the camera behind and above the player
Pytorch builds neural network to predict temperature
![R language [logic control] [mathematical operation]](/img/93/06a306561e3e7cb150d243541cc839.png)
R language [logic control] [mathematical operation]

I didn't know it until I graduated -- the principle of HowNet duplication check and examples of weight reduction
随机推荐
The 2022 China low / no code Market Research and model selection evaluation report was released
Paper reading [open book video captioning with retrieve copy generate network]
Polynomial locus of order 5
Web architecture design process
Nodejs get client IP
微信小程序蓝牙连接硬件设备并进行通讯,小程序蓝牙因距离异常断开自动重连,js实现crc校验位
Go 語言的 Context 詳解
1. AVL tree: left-right rotation -bite
关于服装ERP,你知道多少?
Harmonyos practice - Introduction to development, analysis of atomized services
AI人脸编辑让Lena微笑
async / await
[binary tree] binary tree path finding
拼多多商品详情接口、拼多多商品基本信息、拼多多商品属性接口
R语言【逻辑控制】【数学运算】
Mybaits multi table query (joint query, nested query)
《HarmonyOS实战—入门到开发,浅析原子化服务》
Codeforces Round #416 (Div. 2) D. Vladik and Favorite Game
OpenSergo 即将发布 v1alpha1,丰富全链路异构架构的服务治理能力
论文阅读【Sensor-Augmented Egocentric-Video Captioning with Dynamic Modal Attention】