当前位置:网站首页>Security level
Security level
2022-07-05 01:47:00 【Salted fish Feifei】
In cryptography , The security level is an encryption primitive ( Such as a ciphertext or a hash function ) Measurement of the safety intensity that can be achieved , Its unit is usually bit. An encryption scheme is n-bit Safe , It means that an attacker wants to break the scheme , Must perform at least  operations . for example AES-128( The key length is 128bit) The security level of is 128-bit, It's about equal to 3072-bit Of RSA.
operations . for example AES-128( The key length is 128bit) The security level of is 128-bit, It's about equal to 3072-bit Of RSA.
The target security level is , The security level that must be achieved in the design of this scheme . If the attacker can break this scheme at a lower cost , It means that the target security level is not reached .
Different encryption schemes are right “ Break through ” The definition of is not necessarily the same , It depends on the security requirements of the problem solved by the solution . For example, an encryption scheme , Such as RAS, According to some ciphertext pairs , find RSA The key of . A hash function , It may be to find an original image whose hash value is a fixed value , That is, the original image of hash function is stable , It is also possible to find that the hash values of two plaintext are the same , That is, the collision problem .
Generally speaking , For symmetric encryption scheme , The security level is the length of the key , such as AES-128 The security level of is 128bit. Of course, for hash functions , The original image problem is the length of the key , The collision problem is half the length of the key . however Phelix( One basis MAC Stream cipher of XOR operation ) have 256bit The key of , But it only provides 128bit Security level of .SHA-3 Of SHAKE variant , about 256bit Output , The security level of the original image and collision is 128bit.
For asymmetric encryption , It's a little different . Usually come a Book , Asymmetric encryption is based on a difficult mathematical problem , The problem goes in one direction ( Encryption direction ) It's simple. , And its reverse direction ( Decryption direction ) It's difficult , Need some help information ( secret key ) Can be solved simply . Breaking this encryption scheme can often be prescribed to solve a difficult problem , such as RSA It can be reduced to the problem of large integer factorization . therefore , The security level of asymmetric encryption is defined according to the time required by the best algorithm to solve this difficult problem . and , These algorithms are often faster than brute force cracking .
about “ Break through ” An encryption scheme , It refers to finding an algorithm that can break the scheme , The operation required is lower than the security level he claims . however , In practice, it may not be possible .
Now, , Less than  It can be solved . and
It can be solved . and  To
To  It may be solved in the future .
It may be solved in the future .
Reference resources :
Wikipedia :security level
边栏推荐
- C basic knowledge review (Part 3 of 4)
- 如何搭建一支搞垮公司的技術團隊?
- [OpenGL learning notes 8] texture
- What is the length of SHA512 hash string- What is the length of a hashed string with SHA512?
- Abacus mental arithmetic test
- Word processing software
- batchnorm.py这个文件单GPU运行报错解决
- 微信小程序:最新wordpress黑金壁纸微信小程序 二开修复版源码下载支持流量主收益
- He was laid off.. 39 year old Ali P9, saved 150million
- 85.4% mIOU! NVIDIA: using multi-scale attention for semantic segmentation, the code is open source!
猜你喜欢
微信小程序:星宿UI V1.5 wordpress系统资讯资源博客下载小程序微信QQ双端源码支持wordpress二级分类 加载动画优化
Wechat applet: independent background with distribution function, Yuelao office blind box for making friends
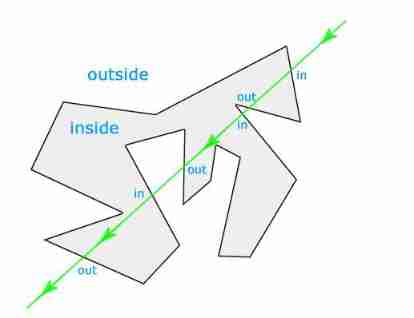
JS implementation determines whether the point is within the polygon range
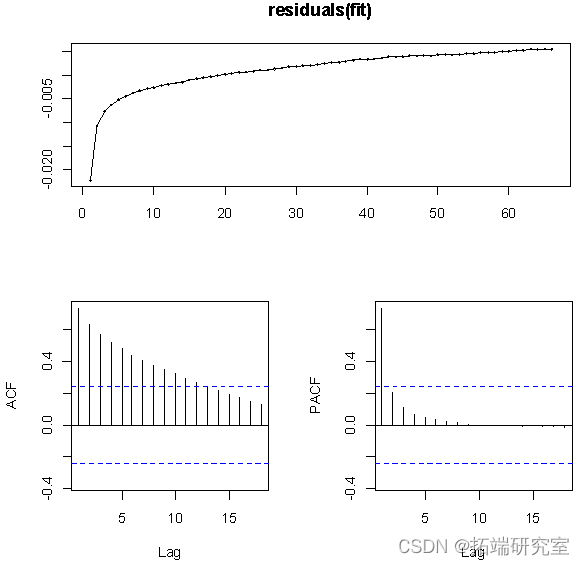
R language uses logistic regression and afrima, ARIMA time series models to predict world population

Mysql database | build master-slave instances of mysql-8.0 or above based on docker
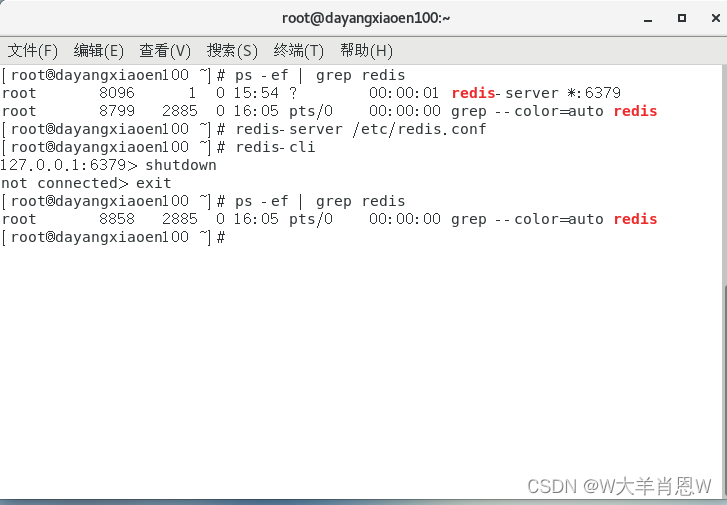
Introduction to redis (1)
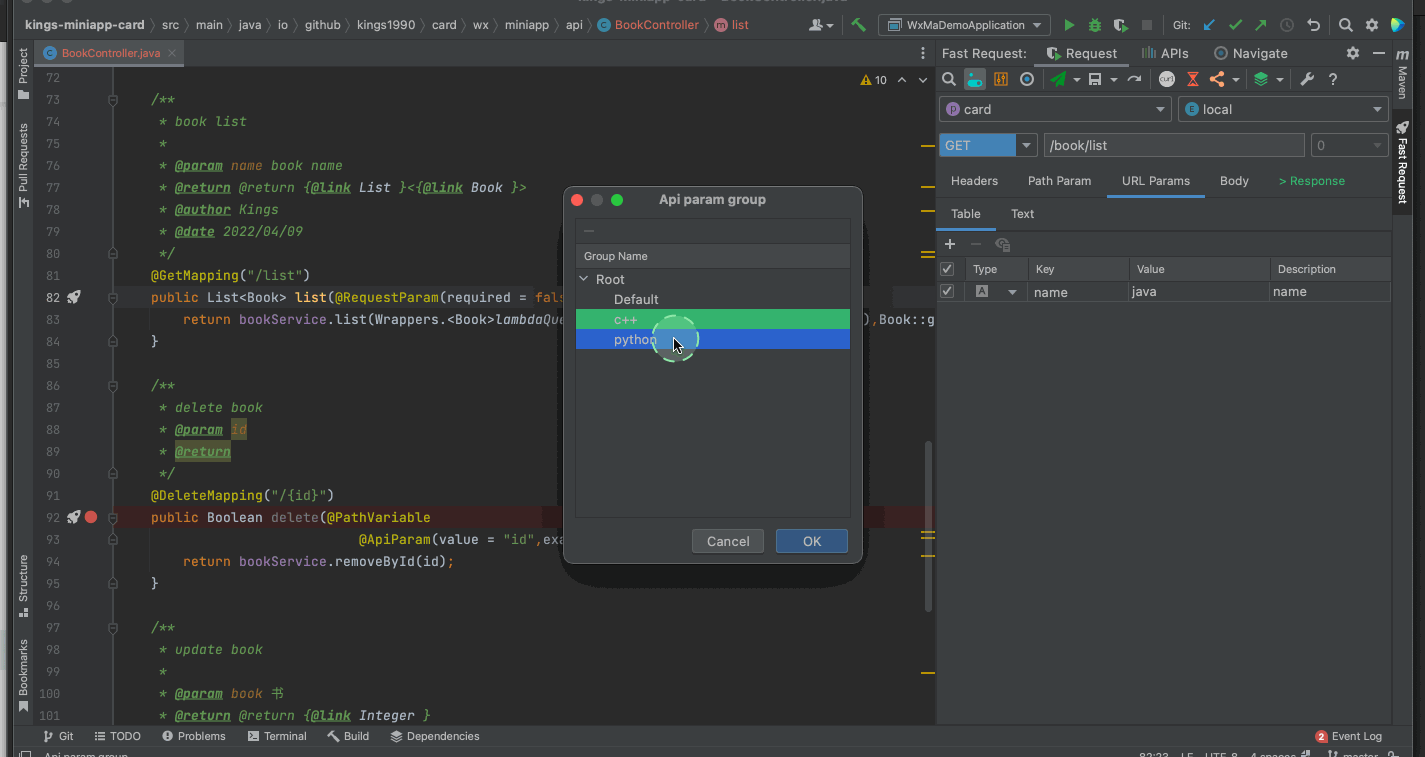
Restful fast request 2022.2.1 release, support curl import
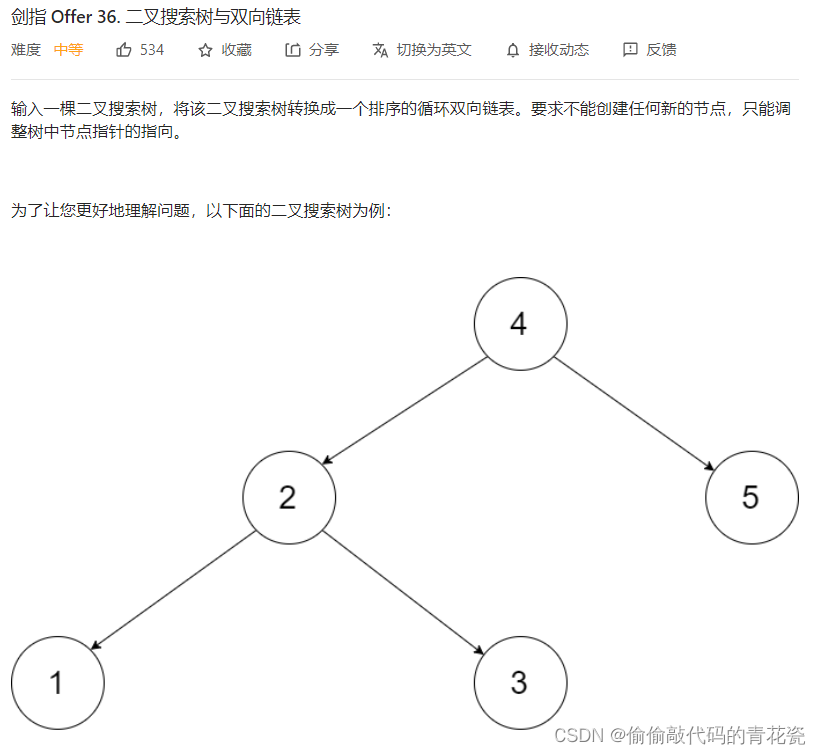
力扣剑指offer——二叉树篇
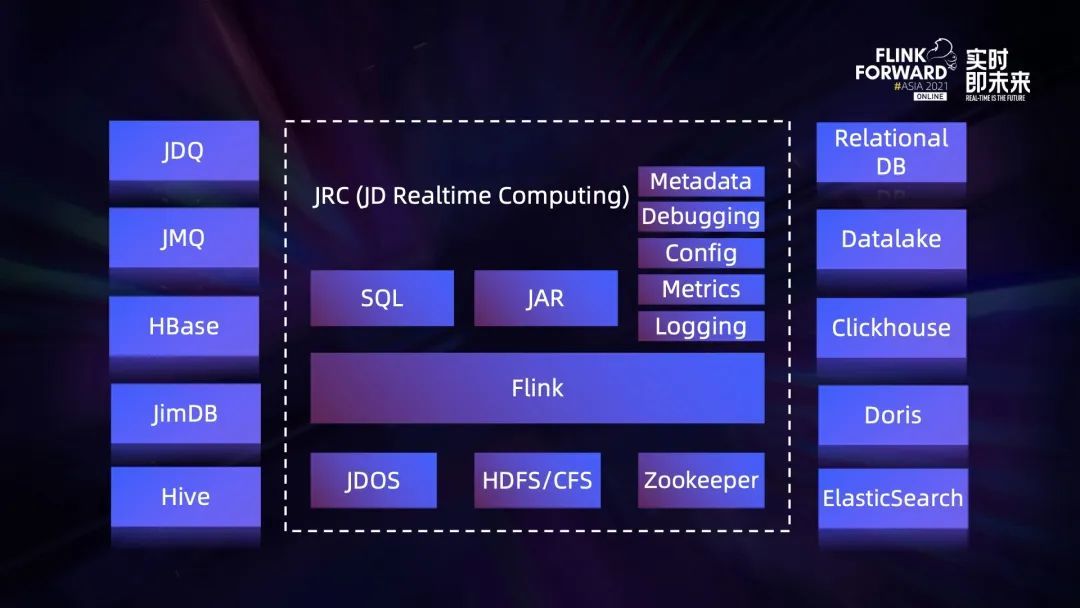
流批一體在京東的探索與實踐
MySQL regexp: Regular Expression Query
随机推荐
R语言用logistic逻辑回归和AFRIMA、ARIMA时间序列模型预测世界人口
Win: add general users to the local admins group
Win: enable and disable USB drives using group policy
Is there a sudden failure on the line? How to make emergency diagnosis, troubleshooting and recovery
Win: use shadow mode to view the Desktop Session of a remote user
Package What is the function of JSON file? What do the inside ^ angle brackets and ~ tilde mean?
Include rake tasks in Gems - including rake tasks in gems
JS implementation determines whether the point is within the polygon range
PowerShell: use PowerShell behind the proxy server
Great God developed the new H5 version of arXiv, saying goodbye to formula typography errors in one step, and mobile phones can also easily read literature
Do you know the eight signs of a team becoming agile?
微信小程序:独立后台带分销功能月老办事处交友盲盒
流批一体在京东的探索与实践
RichView TRVStyle MainRVStyle
無心劍英譯席慕容《無怨的青春》
Numpy library introductory tutorial: basic knowledge summary
Restful Fast Request 2022.2.1发布,支持cURL导入
C语音常用的位运算技巧
What is the current situation and Prospect of the software testing industry in 2022?
Database postragesq BSD authentication