当前位置:网站首页>Technology sharing | packet capturing analysis TCP protocol
Technology sharing | packet capturing analysis TCP protocol
2022-07-06 21:18:00 【Hogwarts_ test】
This article is excerpted from the internal textbook of Hogwarts testing and development society
TCP The protocol is in the transport layer , A connection oriented 、 reliable 、 Transport layer communication protocol based on byte stream .
Environmental preparation
Classify interface testing tools , It can be classified as follows :
- Network sniffer tool :tcpdump,wireshark
- Agent tools :fiddler,charles,anyproxyburpsuite,mitmproxy
- Analysis tools :curl,postman,chrome Devtool
Caught analysis TCP agreement
tcpdump
tcpdump Is a The of packets transmitted over a network “ head ” Completely intercepted to provide analysis Tools for . It supports for network layer 、 agreement 、 host 、 Network or port filtering , And provide and、or、not And other logical statements to remove useless information .
Give Way tcpdump Always monitor 443 port , If there is any difference, enter it into log In file
sudo tcpdump port 443 -v -w /tmp/tcp.log Use this command , Will put the report in the directory /tmp/tcp.log in .
Common parameters | meaning |
|---|---|
port 443 | monitor 443 port |
-v | Output more detailed information |
-w | Write data to log in |
wireshark
wireshark It is also a network sniffing tool , In addition to having tcpdump function , There are more extensions , For example, analysis tools , But in interface testing , The process of capturing packets is often carried out on the server , Servers generally do not provide UI Interface , therefore wireshark Unable to work on server , Can only use tcpdump Grab bag generation log, And then log Import wireshark Use , There is UI Analysis on the client of the interface .
Caught analysis TCP agreement
Grab one http Of get request :
- Search on Baidu mp3
http://www.baidu.com/s?wd=mp3 - use tcpdump Intercept this get request , And generate log
- use wireshark open tcpdump Generated log
Use wireshark see log:
log The first few messages are three handshakes . Because the channel is unreliable , Before sending the data , It is necessary to ensure channel stability , And three handshakes are like the following operations :
- The first handshake : When establishing a connection , The client sends syn package (syn=j) To the server , And enter SYN_SENT state , Wait for server to confirm .
- The second handshake : Server received syn package , Must confirm customer's SYN(ack=j+1), At the same time, I also send a SYN package (seq=k), namely SYN+ACK package , At this time, the server enters SYN_RECV state ;
- The third handshake : Client receives server's SYN+ACK package , Send confirmation package to server ACK(ack=k+1), This package has been sent , Client and server access ESTABLISHED(TCP Successful connection ) state , Complete three handshakes .
After three handshakes , Can further communicate , It looks like this :
At the end of the communication , Four waves are also required :
- First wave : The client sends a... To the server FIN, Request to turn off data transfer .
- Second wave : The server received... From the client FIN, Send a ACK, among ack The value is equal to the FIN+SEQ.
- Third wave : The server sends a... To the client FIN, Tell client application to close .
- Fourth wave : The client receives... From the server FIN, Reply to one ACK To the server . among ack The value is equal to the FIN+SEQ.
Be careful : A request may be divided into multiple packets , So is a data , So in wireshark You'll see a lot of bags .
边栏推荐
- Acdreamoj1110 (multiple backpacks)
- b站视频链接快速获取
- SAP Fiori应用索引大全工具和 SAP Fiori Tools 的使用介绍
- JS get array subscript through array content
- Vim 基本配置和经常使用的命令
- Why does MySQL index fail? When do I use indexes?
- Regular expression collection
- for循环中break与continue的区别——break-完全结束循环 & continue-终止本次循环
- The most comprehensive new database in the whole network, multidimensional table platform inventory note, flowus, airtable, seatable, Vig table Vika, flying Book Multidimensional table, heipayun, Zhix
- Reflection operation exercise
猜你喜欢
缓存更新策略概览(Caching Strategies Overview)

968 edit distance
Is this the feeling of being spoiled by bytes?
![[MySQL] basic use of cursor](/img/cc/39b1e17b48d0de641d3cbffbf2335a.png)
[MySQL] basic use of cursor
The most comprehensive new database in the whole network, multidimensional table platform inventory note, flowus, airtable, seatable, Vig table Vika, flying Book Multidimensional table, heipayun, Zhix

审稿人dis整个研究方向已经不仅仅是在审我的稿子了怎么办?
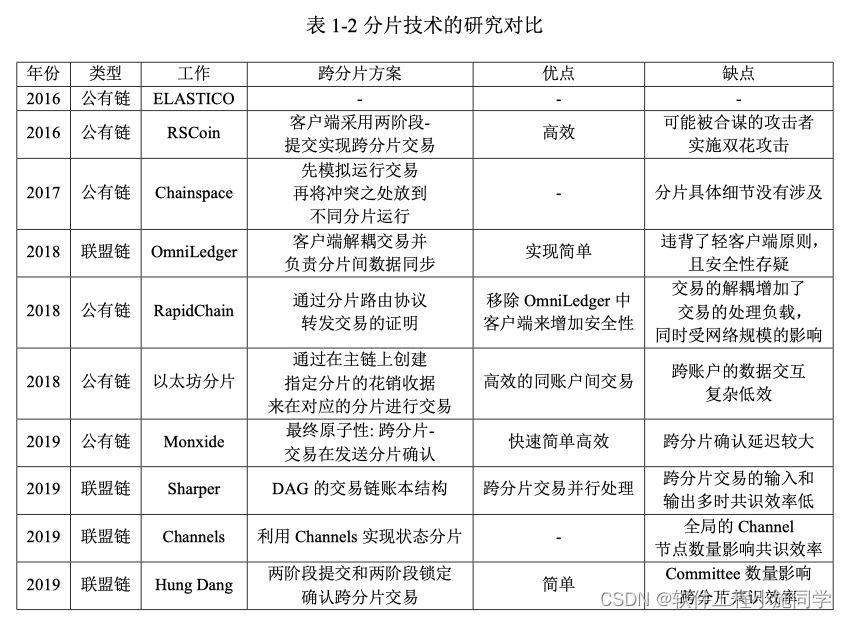
跨分片方案 总结
Set up a time server
HMS Core 机器学习服务打造同传翻译新“声”态,AI让国际交流更顺畅

3D face reconstruction: from basic knowledge to recognition / reconstruction methods!
随机推荐
2022 fields Award Announced! The first Korean Xu Long'er was on the list, and four post-80s women won the prize. Ukrainian female mathematicians became the only two women to win the prize in history
3D face reconstruction: from basic knowledge to recognition / reconstruction methods!
Is it profitable to host an Olympic Games?
Pat 1078 hashing (25 points) ⼆ times ⽅ exploration method
数据湖(八):Iceberg数据存储格式
@PathVariable
Proxy and reverse proxy
Infrared thermometer based on STM32 single chip microcomputer (with face detection)
OAI 5g nr+usrp b210 installation and construction
Word bag model and TF-IDF
【论文解读】用于白内障分级/分类的机器学习技术
通过数字电视通过宽带网络取代互联网电视机顶盒应用
OneNote 深度评测:使用资源、插件、模版
Torch Cookbook
[MySQL] basic use of cursor
R language visualizes the relationship between more than two classification (category) variables, uses mosaic function in VCD package to create mosaic plots, and visualizes the relationship between tw
What is the problem with the SQL group by statement
3D人脸重建:从基础知识到识别/重建方法!
Why does MySQL index fail? When do I use indexes?
【滑动窗口】第九届蓝桥杯省赛B组:日志统计