当前位置:网站首页>Room rate system - login optimization
Room rate system - login optimization
2022-07-07 03:11:00 【Full stack programmer webmaster】
Hello everyone , I meet you again , I'm the king of the whole stack
《 Personal edition of room charging system 》 Basically completed , mine U The code of layer is very, very messy . Basically D There are several functions in the layer ,B There are several functions in the layer ,U Layer use corresponding B Every function in the layer . For example, in login ,U Layer first uses a function check username And the user password Whether it is right , And then use “ Add user login record ” Function of . The following is the sequence diagram of login :
Login business is relatively simple , But for the complicated process of getting on the computer ?U The layer should check whether the card is registered . Whether the remaining amount is sufficient , Whether the status of the card is in use . Whether the card is not online now , After passing this series of tests , Also check the student table to display student information and so on .
This results in U Layer has many functions , and B The coupling degree of the layer is too large . Now let's think back and forth about the functions of each of the three layers :
The presentation layer (UI): Collect user input information and operations , Present specific business data to users . Generally speaking, it is user interface , That is, what a user sees and gets when using a system .
Business logic layer (BLL): Actions for detailed problems . It can also be said to be the operation of the data layer . Logical processing of data business . There are three main ways : from UI Get user instructions and data from , Run business logic ; from DAL Get data in , In order to offer UI Show ; from UI Get user instructions and data from , adopt DAL Write to data source .
Data access layer (DAL): The transactions of this layer directly operate the database , For the addition of data 、 Delete 、 changes 、 Search, etc. .
Under the guidance of the master , Changes have been made :
U layer :
' Sign in
Private Sub btnLogin_Click(sender As Object, e As EventArgs) Handles btnLogin.Click
' Check empty
If PublicFunction.IsEmptyText(Me) = True Then
Exit Sub
End If
' Instanced entity User, quote B layer
Dim euser As New Entity.User
Dim euserRecord As New Entity.UserRecord
Dim blogin As New BLL.LoginBLL
Try
' Pass the information entered by the user to the entity
euser.ProuserID = txtUserID.Text.Trim
euser.ProuserPwd = txtUserPwd.Text
' Feedback information after user verification
If blogin.Check(euser, euserRecord) Then ' Login successful
''UserID and UserLevel Is a global variable , Other functions need to be used
UserID = euser.ProuserID.Trim ' Go to space
UserLevel = euser.ProuserLevel.Trim ' Go to space
' The main window shows
Me.Hide()
frmMain.Show()
Else
MsgBox(" Login failed !username or password Mistake .", vbExclamation, " System prompt ") txtUserID.Focus() Exit Sub End If Catch ex As Exception MsgBox(" error !", vbExclamation, " System prompt ") End Try End SubB layer :
Public Function Check(ByVal euser As Entity.User, ByVal euserRecord As Entity.UserRecord) As Boolean
Dim dt As DataTable
dt = iuser.QueryUser(euser)
Try
If dt.Rows.Count = 0 Then
Return False
Else 'username and password Input correct
euser.ProuserID = dt.Rows(0).Item(0) ' user ID
euser.ProuserLevel = dt.Rows(0).Item(2) ' User level
' Enter the information recorded by the user on the computer
euserRecord.ProuserID = euser.ProuserID
euserRecord.ProuserLevel = euser.ProuserLevel
euserRecord.ProloginTime = Now
euserRecord.PrologoutTime = Now
euserRecord.ProisOnline = 1 '1 It means online .0 Means not online
euserRecord.Procomputer = My.Computer.Name ' Get the current computer username
' Add user login record
Dim result As Integer
result = iuser.AddUserRecord(euserRecord)
If result <> 0 Then ' Successfully joined the user record
Return True
End If
End If
Catch ex As Exception
Throw New Exception
End Try
End FunctionD layer :
' How to find users
Public Function QueryUser(euser As Entity.User) As DataTable Implements IUser.QueryUser
Try
Dim strSQL As String = "select * from T_User where [email protected] and [email protected] "
Dim params() As SqlParameter = {New SqlParameter("@userID", euser.ProuserID), New SqlParameter("@userPwd", euser.ProuserPwd)}
Dim helper As New SqlHelper.sqlHelper
Dim table = helper.GetDataTable(strSQL, CommandType.Text, params)
Return table
Catch ex As Exception
Throw New Exception
End Try
End Function
' The user successfully logged in to UserRecord
Public Function AddUserRecord(euserRecord As Entity.UserRecord) As Integer Implements IUser.AddUserRecord
' When each field is filled , The contents in the preceding brackets can be omitted
'Dim strSQL As String = "insert into T_UserRecord values(@userID,@level,@loginTime,@logoutTime,@computer,@isOnline)"
Try
Dim strSQL As String = "insert into T_UserRecord (userID,userLevel,loginTime,logoutTime,computer,isOnline)values(@userID,@level,@loginTime,@logoutTime,@computer,@isOnline)"
Dim params() As SqlParameter = {New SqlParameter("@userID", euserRecord.ProuserID),
New SqlParameter("@level", euserRecord.ProuserLevel),
New SqlParameter("@loginTime", euserRecord.ProloginTime),
New SqlParameter("@logoutTime", euserRecord.PrologoutTime),
New SqlParameter("@computer", euserRecord.Procomputer),
New SqlParameter("@isOnline", euserRecord.ProisOnline)}
Dim helper As New SqlHelper.sqlHelper
Dim intResult = helper.ExecuteNoQuery(strSQL, CommandType.Text, params)
Return intResult
Catch ex As Exception
Throw New Exception
End Try
End FunctionLogin sequence diagram after change :
The two login sequence diagrams form a sharp contrast , So the user clicks “ Sign in ”button after ,U The layer is responsible for collecting user input username and password, Then just call one Check() Function to verify .B Layer handles business logic . First infer user information , If the input is correct, proceed to the next step and add the user's computer record .D Layer and database . Add, delete, modify, etc .U The layer doesn't know the detailed authentication user details . This decouples , Attend to each one's own duties .
Summary : From the first computer room charging system last year . To today's personal version reconstruction . And the next cooperation reconstruction , Every step is a leap . At first we were purely process oriented , Now I have learned the three-tier architecture , Design patterns are used , But it is still very far away from object-oriented . We are moving forward step by step , This process is very important . It's like Tang Monk learning from the West , Suppose you can get the Sutra by turning the monkey king over . Then there will be no classic 《 Journey to the west 》 了 .
Copyright notice : This article is the original article of the blogger , Blog , Do not reprint without permission .
Publisher : Full stack programmer stack length , Reprint please indicate the source :https://javaforall.cn/116772.html Link to the original text :https://javaforall.cn
边栏推荐
- Andrews - multimedia programming
- Detailed explanation of 19 dimensional integrated navigation module sinsgps in psins (initial assignment part)
- Laravel php artisan 自动生成Model+Migrate+Controller 命令大全
- The version control of 2021 version is missing. Handling method
- [secretly kill little partner pytorch20 days] - [Day1] - [example of structured data modeling process]
- 杰理之在非蓝牙模式下,手机连接蓝牙不要跳回蓝牙模式处理方法【篇】
- Django database (SQLite) basic introductory tutorial
- [tools] basic concept of database and MySQL installation
- Don't you know the relationship between JSP and servlet?
- Cglib agent in agent mode
猜你喜欢
Appx代码签名指南
商城商品的知识图谱构建
Use of tensorboard
从 1.5 开始搭建一个微服务框架——日志追踪 traceId
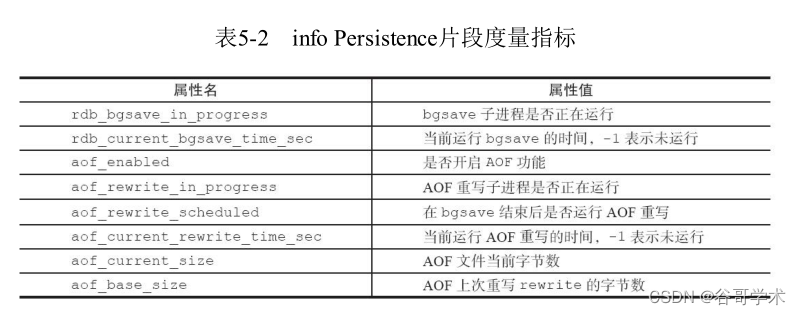
Redis入门完整教程:问题定位与优化

“零售为王”下的家电产业:什么是行业共识?

tensorboard的使用

Babbitt | metauniverse daily must read: is IP authorization the way to break the circle of NFT? What are the difficulties? How should holder choose the cooperation platform
How to write test cases for test coupons?

巴比特 | 元宇宙每日必读:IP授权是NFT的破圈之路吗?它的难点在哪里?Holder该如何选择合作平台?...
随机推荐
Left value, right value
Cryptography series: detailed explanation of online certificate status protocol OCSP
OC, OD, push-pull explanation of hardware
「小样本深度学习图像识别」最新2022综述
The version control of 2021 version is missing. Handling method
Use of promise in ES6
又一百万量子比特!以色列光量子初创公司完成1500万美元融资
The first symposium on "quantum computing + application of financial technology" was successfully held in Beijing
mos管实现主副电源自动切换电路,并且“零”压降,静态电流20uA
Le tube MOS réalise le circuit de commutation automatique de l'alimentation principale et de l'alimentation auxiliaire, et la chute de tension "zéro", courant statique 20ua
Kubernetes源码分析(二)----资源Resource
A complete tutorial for getting started with redis: problem location and optimization
Redis introduction complete tutorial: replication principle
PSINS中19维组合导航模块sinsgps详解(初始赋值部分)
知识图谱构建全流程
Oracle connection pool is not used for a long time, and the connection fails
SSL证书错误怎么办?浏览器常见SSL证书报错解决办法
[tools] basic concept of database and MySQL installation
Unity使用MaskableGraphic画一条带箭头的线
Andrews - multimedia programming