brief introduction
When we visit the website, we will deal with all kinds of certificates , Like visiting https On the web , Need to detect https Certificate validity of the website .
OCSP Is a verification protocol , Used to get X.509 Revocation status of digital certificate . It is to replace CRL And the emergence of .
This article will introduce in detail OCSP Implementation and advantages of .
PKI Medium CRL
We know that PKI Architecture ,CA Certificates are a very important component , Client pass CA Certificate to verify the reliability of the service . about CA For the certificate itself, the expiration time can be specified when it is created . In this way, the certificate can not be used after expiration , Need to apply for a new certificate .
However, it is not enough to specify the expiration time for the certificate , For example, because of our business needs , What if the certificate needs to be revoked ?
PKI There is one provided in called CRL(certificate revocation list) The mechanism of , Used to maintain the list of revoked certificates .
This CRL By CA To issue , It is usually generated before the certificate expires . Because if the certificate has expired , So this CRL It's meaningless .
about CRL itself , It is a list of certificates , The format of the certificate is usually X.509.
CRL Generally, the certificate is issued by CA To maintain and publish , Release CRL The component is called CRL issuer, Generally speaking CRL issuer and CA It's the same service , But you can also send... As needed CRL issuer and CA To break up .
CRL By CA Regularly released , Of course, you can also revoke a as needed CA Reissue the certificate when CRL. be-all CRL All have expiration dates , Within this expiration time , The client can be based on CRL Signature in , Go to CA verification CRL The effectiveness of the , To prevent CRL Forgery of .
CRL The shortcomings of
that CRL What are the disadvantages ?
First CRL Maintain a list of revoked certificates , In order to ensure the effectiveness of the system , The client checks every time CA When the certificate is valid , From the CA Get this from the server CRL. And then through CRL To verify the corresponding CA Certificate Status .
If you get this every time CRL, There may be the following problems .
The first question is , If CRL Unavailable , Then the client can't get this CRL, You can't verify CA The status of the certificate , This makes the service unavailable .
Another problem is , If there are many certificates to revoke , This CRL It may be relatively large , Thus causing a waste of network resources .
The last question is PKI The purpose of certificate system itself is to establish a self verifiable , A security system that does not rely on online services , If you have to get it online every time CRL Words , Just go PKI This advantage of .
CRL The state of
although CRL Maintain a list of revocation certificates , However, the status of certificates in this list is different .
CRL There are two statuses of certificates in , The first is that the certificate has been revoked , For example, the certification authority CA It is found that the previously issued certificate is wrong , Or because of other reasons, such as the disclosure of the private key, the original certificate is not secure enough , The certificate needs to be withdrawn . Or the certificate authority's certificate is revoked because it fails to comply with some policies , You need to set the previous certificate to revocation status .
There is also a state of temporary revocation , It's called Hold state , The certificate is temporarily invalid , For example, determine whether the user's private key is lost . When the user finally finds the private key , Then the certificate can still be restored .
OCSP workflow
since CRL There are so many shortcomings , So one is used to replace CRL Of OCSP There's an agreement .
So let's see OCSP workflow .
If A and B To use PKI To communicate . In order to ensure the security of communication ,A Send your public key to B, And tell B, This is my public key , You can use this public key to verify the message I sent you .
B Upon receipt of A After the public key of , I'm not sure A Your public key is correct , Not tampered with . So from the A Extracted from the public key of serial number, And encapsulate it into a 'OCSP request' Medium distribution CA The server .
CA In the server OCSP responder It reads 'OCSP request' request , And extract A Of the public key serial number.OCSP responder from CA Query this in the database of the server serial number Whether it is in the list of revoked databases .
If it's not found , That means A Your public key is still valid ,OCSP responder A signed... Will be sent OCSP response to B.
B By using CA Public key verification of the server OCSP response The effectiveness of the , So as to confirm A Your public key is still valid .
Last B Use A The public key and A To communicate .
OCSP The advantages of
From the above OCSP We can roughly summarize the following work flow OCSP be relative to CRL The advantages of .
First OCSP The amount of data in response is greater than CRL smaller , So there is less demand and pressure on the network .
In addition, because OCSP The response has less data to parse , therefore OCSP The implementation of the client is better than CRL It's simpler .
Although because of CRL All kinds of shortcomings , stay web No longer used in the environment , But by being more efficient OCSP Replace , however CRL Still running in CA In other environments .
OCSP Details of the agreement
OCSP The agreement is in RFC 6960 As defined in .
OCSP The protocol can be divided into request protocol and response protocol , Next, let's introduce .
OCSP request
One OCSP The request needs to contain the protocol version number , Request service , Certificate to be verified identifier And optional extensions .
OCSP responder On receiving OCSP After the request , It's going to check OCSP The validity of the message , If there is a problem with the message, an exception will be returned , Otherwise, it will be processed according to the requested service .
OCSP Request if ASN.1(Abstract Syntax Notation One) Abstract syntax notation this can be expressed as :
OCSPRequest ::= SEQUENCE {
tbsRequest TBSRequest,
optionalSignature [0] EXPLICIT Signature OPTIONAL }
TBSRequest ::= SEQUENCE {
version [0] EXPLICIT Version DEFAULT v1,
requestorName [1] EXPLICIT GeneralName OPTIONAL,
requestList SEQUENCE OF Request,
requestExtensions [2] EXPLICIT Extensions OPTIONAL }
Signature ::= SEQUENCE {
signatureAlgorithm AlgorithmIdentifier,
signature BIT STRING,
certs [0] EXPLICIT SEQUENCE OF Certificate OPTIONAL}
Version ::= INTEGER { v1(0) }
Request ::= SEQUENCE {
reqCert CertID,
singleRequestExtensions [0] EXPLICIT Extensions OPTIONAL }
CertID ::= SEQUENCE {
hashAlgorithm AlgorithmIdentifier,
issuerNameHash OCTET STRING, -- Hash of issuer's DN
issuerKeyHash OCTET STRING, -- Hash of issuer's public key
serialNumber CertificateSerialNumber }
ASN.1 Is an interface description language , adopt ASN.1, We can clearly describe the format information of data .
One OCSPRequest Is optionally signed by OCSP request tbsRequest And the corresponding signature optionalSignature Composed of .
among TBSRequest It contains the version number ,OCSP requestor Name , Status list of certificates requestList, The optional extended data consists of these items .
OCSP Respond to
about OCSP In terms of response , According to different transmission protocols, its structure is also different . But all responses should contain responseStatus Field indicates the processing status of the request .
OCSP Sound application ASN.1 The format is represented as follows :
OCSPResponse ::= SEQUENCE {
responseStatus OCSPResponseStatus,
responseBytes [0] EXPLICIT ResponseBytes OPTIONAL }
OCSPResponseStatus ::= ENUMERATED {
successful (0), -- Response has valid confirmations
malformedRequest (1), -- Illegal confirmation request
internalError (2), -- Internal error in issuer
tryLater (3), -- Try again later
-- (4) is not used
sigRequired (5), -- Must sign the request
unauthorized (6) -- Request unauthorized
}
ResponseBytes ::= SEQUENCE {
responseType OBJECT IDENTIFIER,
response OCTET STRING }
responseStatus Is the status of the response ,responseBytes Is an optional response result .
there response It's a BasicOCSPResponse Object's DER code :
BasicOCSPResponse ::= SEQUENCE {
tbsResponseData ResponseData,
signatureAlgorithm AlgorithmIdentifier,
signature BIT STRING,
certs [0] EXPLICIT SEQUENCE OF Certificate OPTIONAL }
OCSP stapling
You can see OCSP When the customer needs to check whether the certificate is revoked , You need to OCSP responser request , To confirm the validity of the certificate .
But this method actually divulges the user's private information , because OCSP responser Know the certificate that the client needs to verify , Just know the website the client is visiting .
So I introduced OCSP stapling To solve this problem .
So what is OCSP stapling Well ?
OCSP stapling Is directly to the OCSP Put the certificate in the place that the client wants to access web Server , because OCSP Certificates are time stamped and digitally signed , Therefore, its correctness can be guaranteed .
these OCSP The certificate will be displayed on the client and web End build SSL The handshake is included in OCSP Response .
In this way, the client does not need to be separated from CA Establish additional connections , This improves performance .
OCSP stapling It needs to be started on the server side .
If you're using a apache The server , First, you need a version greater than 2.3.3.
Then it needs to be in .conf In the document <VirtualHost></VirtualHost> block External addition :
SSLStaplingCahe shmcb: /tmp/stapling_cache(128000)
And then in <VirtualHost></VirtualHost> block Add... Inside of :
SSLUseStapling On
If you're using a nginx, First, you need a version greater than 1.3.7.
And then in nginx Configuration file for server {} block Add :
ssl_stapling on;
ssl_stapling_verify on;
If you want to verify whether a website is open OCSP stapling, You can go to https://entrust.ssllabs.com/ Query in the website :
In this website , You can enter the address of any website you want to query , Then you can get the following information :
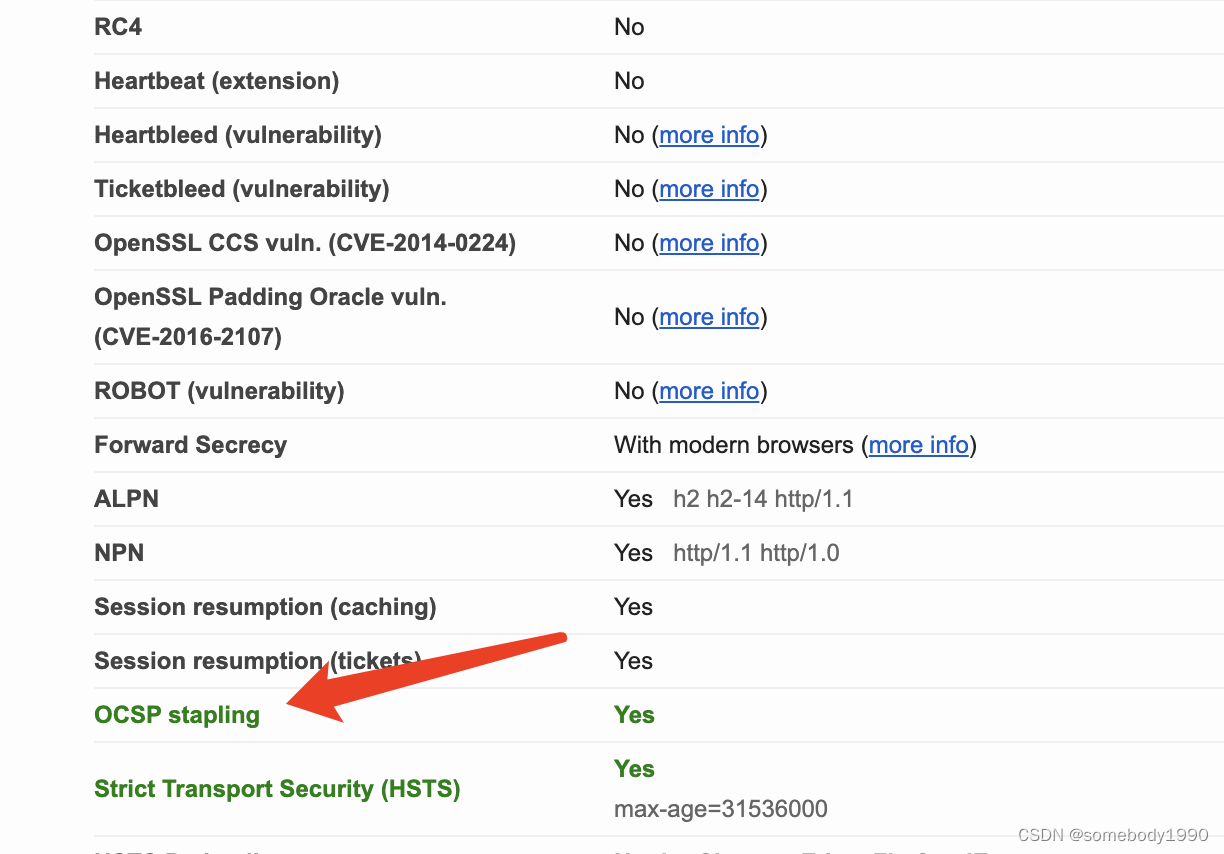
You can see that this website is open OCSP stapling Of .
summary
OCSP and OCSP stapling Is a very useful certificate revocation verification protocol , Has been widely used . You can check whether your website is used .
Please refer to http://www.flydean.com/43-pki-ocsp/
The most popular interpretation , The deepest dry goods , The most concise tutorial , There are so many tricks you don't know about waiting for you to discover !
Welcome to my official account. :「 Program those things 」, Know technology , Know you better !