当前位置:网站首页>Simple test of the use of iptables
Simple test of the use of iptables
2022-08-01 20:34:00 【daydayup9527】
iptables
四表五链
配直iptables时,不指定表,默认使用filter表.配置时不指定规则链,则配置所有链;
数据包进入该链时,从上向下匹配,匹配即停止,开始应用规则.如果全都不匹配,则应用默认规则;
命令规则:
Options are capitalized:-L、-P、-A、-I、 -D、 -F
chain name capitalization:INPUT、OUTPUT、FORWARD
The target operation is capitalized:DROP、 ACCEPT、 REJECT..
其他小写: -s -p --sport --deport...
一般配置nat表跟filter表
INPUT:数据包的目标地址是自己,则进入INPUT链
OUTPUT:数据包的源地址是自己,则进入OUTPUT链
FORWARD:数据包穿过自己,则进入FORWARD链
[[email protected] ~]# iptables -t filter -L # -t指定表名
[[email protected] ~]# iptables -nL #默认filter表,所有规则链都是空的
Chain INPUT (policy ACCEPT) #INPUT链默认规则是接受
target prot opt source destination
Chain FORWARD (policy ACCEPT) #FORWARD链默认规则是接受
target prot opt source destination
Chain OUTPUT (policy ACCEPT) #OUTPUT链默认规则是接受,一般不限制
target prot opt source destination
iptables [-t表名] 选项 [链名] [条件] [-j满足条件的操作]
web服务只允许ssh http 访问,Others are not allowed
iptables匹配规则:自上到下,匹配即停止.Default rules last.
[[email protected] ~]# iptables -A INPUT -s 192.168.1.1 -j ACCEPT
#-Ais an append rule(最后面),-s是匹配源地址,-j为jump,采取的行为,ACCEPT是接受
master 192.168.1.11 node1 192.168.1.12 本机 192.168.1.1
-P 设置默认规则
[[email protected] ~]# iptables -P INPUT DROP #注意先执行,会断开ssh
#将INPUT链的默认规则改为DROP丢弃.-P 设置默认规则,The default rule is checked last
[[email protected] ~]# iptables -nL
Chain INPUT (policy DROP) #默认drop,最后检查
target prot opt source destination
ACCEPT all -- 192.168.1.1 0.0.0.0/0 #代表anywhere
[[email protected] ~]# ifconfig ens33
ens33: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.1.12 netmask 255.255.255.0 broadcast 192.168.1.255
[[email protected] ~]# ping 192.168.1.11 #不通
#node1 ip 192.168.1.12,只有192.168.1.1accept一个规则,Does not match to go by defaultdrop
允许192.168.1.0网络的主机ssh连接master
-I 插入规则
[[email protected] ~]# iptables -I INPUT 1 -s 192.168.1.0/24 -p tcp --dport 22 -j ACCEPT
#-I是插入到INPUT链的 1 第1个位置.-p指定协议 --dport指定目标端口号 -j是执行的操作
#查看规则
[[email protected] ~]# iptables -nL #n是指用数字来表示端口号、主机等
Chain INPUT (policy DROP)
target prot opt source destination
ACCEPT tcp -- 192.168.1.0/24 0.0.0.0/0 tcp dpt:22
ACCEPT all -- 192.168.1.1 0.0.0.0/0
-A 追加规则
[[email protected] ~]# iptables -A INPUT -s 192.168.1.12 -j DROP
[[email protected] ~]# iptables -nL INPUT
Chain INPUT (policy DROP)
target prot opt source destination
ACCEPT tcp -- 192.168.1.0/24 0.0.0.0/0 tcp dpt:22
ACCEPT all -- 192.168.1.1 0.0.0.0/0
DROP all -- 192.168.1.12 0.0.0.0/0
-D 删除规则
[[email protected] ~]# iptables -D INPUT 3
[[email protected] ~]# iptables -nL INPUT
Chain INPUT (policy DROP)
target prot opt source destination
ACCEPT tcp -- 192.168.1.0/24 0.0.0.0/0 tcp dpt:22
ACCEPT all -- 192.168.1.1 0.0.0.0/0
举例
[[email protected] ~]# yum -y install httpd
[[email protected] ~]# systemctl start httpd
默认规则是drop,So the visit will be stuck,注意状态 SYN-SENT
[[email protected] ~]# curl 192.168.1.11 #卡住,
[[email protected] ~]# ss | grep SENT #Open a terminal again,看到http一直处于SYN-SENT状态,防火墙不通
tcp SYN-SENT 0 1 192.168.1.12:50846 192.168.1.11:http
[[email protected] ~]# curl 192.168.1.11
curl: (7) Failed connect to 192.168.1.11:80; Connection timed out
[[email protected] ~]# ss | grep SENT #curl超时后,再次查看SYN-SENT的连接.发现没了
[[email protected] ~]# iptables -I INPUT 1 -s 192.168.1.0/24 -p tcp --dport 80 -j ACCEPT
[[email protected] ~]# iptables -nL INPUT
Chain INPUT (policy DROP)
target prot opt source destination
ACCEPT tcp -- 192.168.1.0/24 0.0.0.0/0 tcp dpt:80
ACCEPT tcp -- 192.168.1.0/24 0.0.0.0/0 tcp dpt:22
ACCEPT all -- 192.168.1.1 0.0.0.0/0
Access is the same at this time
[[email protected] ~]# curl 192.168.1.11
ping ICMP协议
应用层 ssh http ftp (Then add a presentation layer、会话层)
传输层 tcp / udp端口号
网络层 icmp (ping) #icmp不放开,There is no need to consider the transmission of the above two layers
数据链路层
物理层
1、No rules are set(配置了默认drop),卡主
[[email protected] ~]# ping 192.168.1.11 #The rules are as above,Displays the card owner
PING 192.168.1.11 (192.168.1.11) 56(84) bytes of data.
^C
--- 192.168.1.11 ping statistics ---
2 packets transmitted, 0 received, 100% packet loss, time 1000ms
2、设置REJECT,显示 不可达Destination Port Unreachable
[[email protected] ~]# iptables -A INPUT -s 192.168.1.12 -p icmp -j REJECT
[[email protected] ~]# iptables -nL INPUT
Chain INPUT (policy DROP)
REJECT icmp -- 192.168.1.12 0.0.0.0/0 reject-with icmp-port-unreachable
[[email protected] ~]# ping 192.168.1.11
PING 192.168.1.11 (192.168.1.11) 56(84) bytes of data.
From 192.168.1.11 icmp_seq=1 Destination Port Unreachable
From 192.168.1.11 icmp_seq=2 Destination Port Unreachable
3、设置ACCEPT,显示ping通
[[email protected] ~]# iptables -I INPUT 1 -s 192.168.1.12 -p icmp -j ACCEPT
[[email protected] ~]# ping 192.168.1.11
PING 192.168.1.11 (192.168.1.11) 56(84) bytes of data.
64 bytes from 192.168.1.11: icmp_seq=1 ttl=64 time=0.272 ms
64 bytes from 192.168.1.11: icmp_seq=2 ttl=64 time=0.677 ms
显示规则的行号 --line-numbers
[[email protected] ~]# iptables -nL INPUT --line-numbers
Chain INPUT (policy DROP)
num target prot opt source destination
1 ACCEPT icmp -- 192.168.1.12 0.0.0.0/0
2 ACCEPT tcp -- 192.168.1.0/24 0.0.0.0/0 tcp dpt:80
3 ACCEPT tcp -- 192.168.1.0/24 0.0.0.0/0 tcp dpt:22
4 ACCEPT all -- 192.168.1.1 0.0.0.0/0
不保存规则,重启iptables服务,自定义规则将消失
[[email protected] ~]# iptables-save >rule.txt
[[email protected] ~]# iptables–restore <rule.txt
FORWARD链测试
1)client主机配置IP、添加网关
[[email protected] ~]# nmcli connection modify ens33 ipv4.method manual \
ipv4.addresses 192.168.4.10/24 autoconnect yes
[[email protected] ~]# nmcli connection modify ens33 ipv4.gateway 192.168.4.5
[[email protected] ~]# nmcli connection up
[[email protected] ~]# ifconfig ens33
ens33: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.4.10
[[email protected] ~]# route -n
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
0.0.0.0 192.168.4.5 0.0.0.0 UG 100 0 0 ens33
192.168.4.0 0.0.0.0 255.255.255.0 U 100 0 0 ens33
2)web1主机配置IP、添加网关
[[email protected] ~]# nmcli connection modify ens33 ipv4.method manual \
ipv4.addresses 192.168.1.12/24 autoconnect yes
[[email protected] ~]# nmcli connection modify ens33 ipv4.gateway 192.168.1.11
[[email protected] ~]# nmcli connection up eth0
[[email protected] ~]# ifconfig ens33
ens33: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.1.12
[[email protected] ~]# route -n
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
0.0.0.0 192.168.1.11 0.0.0.0 UG 100 0 0 ens33
192.168.1.0 0.0.0.0 255.255.255.0 U 100 0 0 ens33
3)proxy主机配置IP、开启路由转发
[[email protected] ~]# nmcli connection modify ens33 ipv4.method manual \
ipv4.addresses 192.168.4.5/24 autoconnect yes
[[email protected] ~]# nmcli connection up ens33
[[email protected] ~]# nmcli connection modify ens37 ipv4.method manual \
ipv4.addresses 192.168.1.11/24 autoconnect yes
[[email protected] ~]# nmcli connection up ens37
[[email protected] ~]# ip a
...
2: ens33: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group
inet 192.168.1.11/24
3: ens37: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group
inet 192.168.4.5/24
[[email protected] ~]# ping 192.168.1.12
PING 192.168.1.12 (192.168.1.12) 56(84) bytes of data.
^C
--- 192.168.1.12 ping statistics ---
2 packets transmitted, 0 received, 100% packet loss, time 1001ms
[[email protected] ~]# echo 'net.ipv4.ip_forward=1' >> /etc/sysctl.conf #开启转发
[[email protected] ~]# sysctl -p
net.ipv4.ip_forward = 1
[[email protected] ~]# ping 192.168.1.12
PING 192.168.1.12 (192.168.1.12) 56(84) bytes of data.
64 bytes from 192.168.1.12: icmp_seq=7 ttl=63 time=2.48 ms
64 bytes from 192.168.1.12: icmp_seq=8 ttl=63 time=5.92 ms
4)在web主机上启动http服务
[[email protected] ~]# yum -y install httpd
[[email protected] ~]# echo "test page" > /var/www/html/index.html
[[email protected] ~]# systemctl restart httpd
[[email protected] ~]# curl http://192.168.1.12 #成功
5)设置proxy规则,Protected behind a firewallWeb服务器
[[email protected] ~]# iptables -I FORWARD -s 192.168.4.10 -p tcp --dport 80 -j DROP
设置完防火墙规则后,再次使用clientClient access test effect
[[email protected] ~]# curl http://192.168.2.100 #失败
配置SNAT实现共享上网
[[email protected] ~]# tail -n1 /var/log/httpd/access_log #这里显示的是client机的ip
192.168.4.10 - - [01/Aug/2022:10:43:58 +0800] "GET / HTTP/1.1" 200 10 "-" "curl/7.29.0"
client访问服务时,Equivalent to public network accessweb(Server intranet service)时,Not directly connected to the intranet.must be disguised as192.168.1.0network segment can be accessed192.168.1.12,That is, it needs to be disguised as a network cardIP为192.168.1.11时,to complete public network access
[[email protected] ~]# iptables -F
[[email protected] ~]# iptables -t nat -A POSTROUTING -s 192.168.4.0/24 -p tcp --dport 80 -j SNAT --to-source 192.168.1.11
[[email protected] ~]# iptables -t nat -nL POSTROUTING
Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
SNAT tcp -- 192.168.4.0/24 0.0.0.0/0 tcp dpt:80 to:192.168.1.11
#192.168.4.0/24The network segment to anywhere on the intranet of this place,All disguised as192.168.1.11进行访问.(192.168.1.11It seems to be understood as a public network that provides server service bindingip)
[[email protected] ~]# tail -n1 /var/log/httpd/access_log
192.168.1.11 - - [01/Aug/2022:10:50:22 +0800] "GET / HTTP/1.1" 200 10 "-" "curl/7.29.0"
#此时的web日志,正好说明了这一点
对于proxy外网IPThe following address masquerading can be performed for non-fixed cases
[[email protected] ~]# iptables -t nat -A POSTROUTING -s 192.168.4.0/24 -p tcp --dport 80 -j MASQUERADE
所有iptablesRules are temporary rules,Permanent retention if requirediptables规则
[[email protected] ~]# service iptables save #保存防火墙规则
iptables: Saving firewall rules to /etc/sysconfig/iptables:[ OK ]
Firewall extension rules are used-mparameters to enable these extended functions
根据MAC地址过滤
[[email protected] ~]# iptables -I INPUT -s 192.168.4.10 -p tcp --dport 22 -j DROP
#Set rules to prohibit192.168.4.10使用ssh远程本机.当client主机修改IP地址后,The rule will be invalid
根据MAC地址过滤,可以防止这种情况的发生.
[[email protected] ~]# nmap -sF -n 192.168.2.100 #扫描mac地址
[[email protected] ~]# ip link show eth0 #查看client的MAC地址
eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP mode DEFAULT qlen 1000
link/ether 52:54:00:00:00:0b brd ff:ff:ff:ff:ff:ff
[[email protected] ~]# iptables -A INPUT -p tcp --dport 22 -m mac --mac-source 52:54:00:00:00:0b -j DROP
#拒绝52:54:00:00:00:0bThis host is remote to this machine
Set filtering rules based on multiple ports
[[email protected] ~]# iptables -A INPUT -p tcp -m multiport --dports 20,25,80,110,143,16501:16800 -j ACCEPT
#一次性开启20,25,80,110,143,16501到16800所有的端口
基于IPAddress range setting rules
1)允许从 192.168.4.10-192.168.4.20 主机ssh远程登录本机
[[email protected] ~]# iptables -A INPUT -p tcp --dport 22 -m iprange --src-range 192.168.4.10-192.168.4.20 -j ACCEPT
#Multiple targets can also be restricted hereIP的范围,参数是--dst-range,用法与--src-range一致.
2)禁止从 192.168.4.0/24 other hosts on the network segmentssh远程登录本机
[[email protected] ~]# iptables -A INPUT -p tcp --dport 22 -s 192.168.4.0/24 -j DROP
Help manual for extended rules
[[email protected] -l# man iptables-extensions
边栏推荐
- Failed to re-init queues : Illegal queue capacity setting (abs-capacity=0.6) > (abs-maximum-capacity
- 面试突击70:什么是粘包和半包?怎么解决?
- Does LabVIEW really close the COM port using VISA Close?
- 虚拟机的IP地址自动变为127.0.0.1
- Protocol Buffer usage
- 宝塔搭建PESCMS-Ticket开源客服工单系统源码实测
- LinkedList source code sharing
- WhatsApp group sending actual combat sharing - WhatsApp Business API account
- The configuration manual for the secondary development of the XE training system of the missing moment document system
- 【节能学院】智能操控装置在高压开关柜的应用
猜你喜欢
LTE time domain and frequency domain resources
面试突击70:什么是粘包和半包?怎么解决?
Postman 批量测试接口详细教程
![[Energy Conservation Institute] Application of Intelligent Control Device in High Voltage Switchgear](/img/6d/05233ce5c91a612b6247ea07d7982e.jpg)
[Energy Conservation Institute] Application of Intelligent Control Device in High Voltage Switchgear
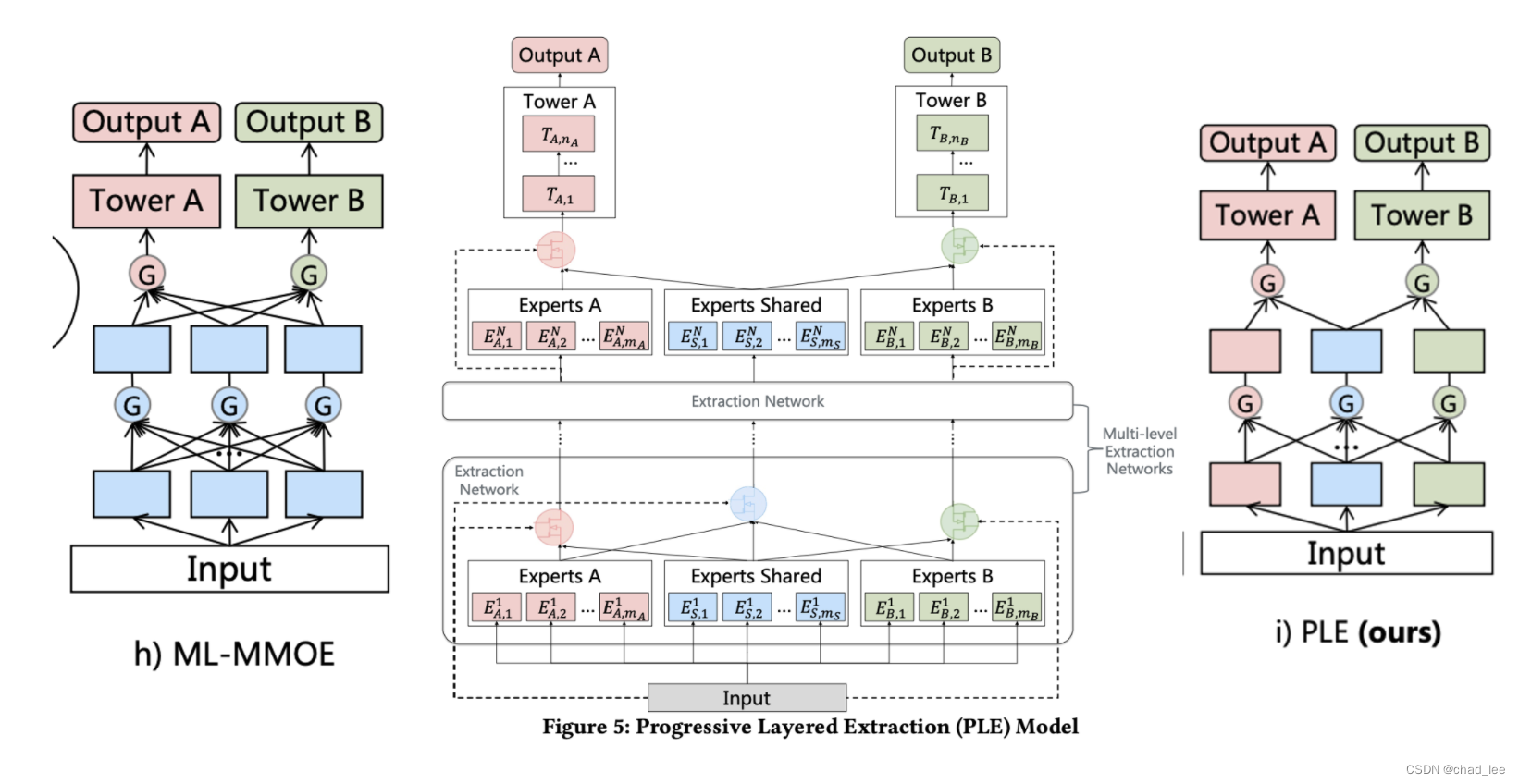
【多任务模型】Progressive Layered Extraction: A Novel Multi-Task Learning Model for Personalized(RecSys‘20)

C语言实现-直接插入排序(带图详解)
宝塔搭建PESCMS-Ticket开源客服工单系统源码实测

Arthas 常用命令
![[Multi-task optimization] DWA, DTP, Gradnorm (CVPR 2019, ECCV 2018, ICML 2018)](/img/a1/ec038eeb6c98c871eb31d92569533d.png)
[Multi-task optimization] DWA, DTP, Gradnorm (CVPR 2019, ECCV 2018, ICML 2018)

98. Embedded controller EC actual combat EC development board development completed
随机推荐
Digital twin Beijing the imperial palace, yuan universe is the process of tourism
数字孪生北京故宫,元宇宙推进旅游业进程
Addition, Subtraction, Multiplication of Large Integers, Multiplication and Division of Large Integers and Ordinary Integers
【kali-信息收集】(1.3)探测网络范围:DMitry(域名查询工具)、Scapy(跟踪路由工具)
任务调度线程池-应用定时任务
实用新型专利和发明专利的区别?秒懂!
[Multi-task model] Progressive Layered Extraction: A Novel Multi-Task Learning Model for Personalized (RecSys'20)
线程池处理异常的方法
Fork/Join线程池
基于FPGA的任意字节数(单字节、多字节)的串口(UART)发送(含源码工程)
SIPp 安装及使用
Excel advanced drawing techniques, 100 (22) - how to respectively the irregular data
Acrel-5010重点用能单位能耗在线监测系统在湖南三立集团的应用
vant实现Select效果--单选和多选
面试官:大量请求 Redis 不存在的数据,从而打倒数据库,有什么方案?
Wildcard SSL/TLS certificate
C语言实现-直接插入排序(带图详解)
Go 语言中常见的坑
StringTable详解 串池 性能调优 字符串拼接
1374. 生成每种字符都是奇数个的字符串 : 简单构造模拟题