当前位置:网站首页>Design and implementation of campus epidemic prevention and control system based on SSM
Design and implementation of campus epidemic prevention and control system based on SSM
2022-07-05 02:31:00 【Salted fish brother】
word The full version can be downloaded as follows >>>>>>>>
Objective record
Abstract ------------------------------------------------------------- I
ABSTRACT-------------------------------------------------------- II
1 The introduction ---------------------------------------------------------- 1
1.1 Research background ------------------------------------------------ 1
1.2 Research status ------------------------------------------------ 1
1.3 Research significance ------------------------------------------------ 2
1.4 Paper organization structure -------------------------------------------- 2
2 Related technology and development environment -------------------------------------------- 4
2.1 Related technology introduction -------------------------------------------- 4
2.1.1 B/S Architecture brief introduction -------------------------------------- 4
2.1.2 Java Technical introduction ------------------------------------- 4
2.1.3 MySQL Database introduction ---------------------------------- 5
2.2 Introduction to development environment -------------------------------------------- 5
3 Systems analysis ------------------------------------------------------ 6
3.1 Feasibility analysis ---------------------------------------------- 6
3.1.1 Technical feasibility ---------------------------------------- 6
3.1.2 Economic feasibility ---------------------------------------- 6
3.1.3 Operational feasibility ---------------------------------------- 7
3.2 System performance analysis -------------------------------------------- 7
3.3 System functional requirements analysis ---------------------------------------- 7
3.3.1 Administrator use case diagram -------------------------------------- 7
3.3.2 Student use case diagram ---------------------------------------- 8
4 Overall design of the system ------------------------------------------------- 10
4.1 Functional structure diagram of the system --------------------------------------- 10
4.2 System database design ----------------------------------------- 10
4.2.1 Conceptual structural design ------------------------------------- 10
4.2.2 Data logical structure design --------------------------------- 13
5 Detailed design of the system ------------------------------------------------- 16
5.1 System development process design --------------------------------------- 16
5.2 System foreground function process --------------------------------------- 16
5.2.1 The login process ----------------------------------------- 16
5.2.2 Registration process ----------------------------------------- 17
5.2.3 Password modification process ------------------------------------- 18
5.3 User module flow chart ----------------------------------------- 19
5.4 Administrator module flow chart --------------------------------------- 21
6 system implementation ----------------------------------------------------- 24
6.1 System interface design and implementation ------------------------------------- 24
6.2 System login interface ------------------------------------------- 24
6.3 Design and implementation of client ------------------------------------- 25
6.3.1 User center interface ------------------------------------- 25
6.3.2 Users modify their personal information --------------------------------- 26
6.3.3 Users submit submission information --------------------------------- 26
6.3.4 Users view detection information --------------------------------- 27
6.3.5 Users view isolation information --------------------------------- 27
6.4 Design and implementation of administrator ------------------------------------- 28
6.4.1 Administrator center interface ----------------------------------- 28
6.4.2 Managing personal information ------------------------------------- 28
6.4.3 Management information ------------------------------------- 29
6.4.4 Manage epidemic dynamics ------------------------------------- 30
6.4.5 Manage student information ------------------------------------- 30
6.4.6 View student reports ------------------------------------- 31
6.4.7 Check the detection information ------------------------------------- 31
6.4.8 View isolation information ------------------------------------- 32
6.4.9 View statistics ------------------------------------- 32
7 The system test ----------------------------------------------------- 34
7.1 Program debugging ----------------------------------------------- 34
7.2 testing procedure ----------------------------------------------- 34
7.3 Test and analysis ----------------------------------------------- 35
7.4 Test conclusion ----------------------------------------------- 37
8 Summary and prospect --------------------------------------------------- 38
8.1 summary --------------------------------------------------- 38
8.2 expectation --------------------------------------------------- 38
reference -------------------------------------------------------- 39
thank ------------------------------------------------------------ 41
pick want
2020 The novel coronavirus epidemic swept the country , Under the leadership of the wise decision of the Party Central Committee, all Chinese people have overcome the epidemic , Students begin to resume classes , But novel coronavirus may spread , Campus epidemic prevention and control should not be careless . Therefore, it is urgent to develop an epidemic prevention and control system , It has far-reaching significance for campus epidemic prevention and control , Digitalize epidemic prevention and control information , Informatization can increase the ability of epidemic prevention and control , Contain the danger in the bud .
This article uses browser - The server mode is B/S Pattern , use Java Technology as a programming language to develop campus epidemic prevention and control system . This system aims to realize personal information 、 Information information 、 What's going on 、 Student information 、 Students report 、 Detection information 、 Isolate information 、 Statistical information and other functions . At the same time, the system has multi-level permissions , It is divided into administrator permission and ordinary student permission . Student authority : Personal information 、 Information information 、 What's going on 、 Report information 、 Detection information 、 Isolate information browsing function . Administrator users mainly maintain the data information generated by the system , Including the addition, deletion, modification and query of the above information . At the same time, the system uses a free database server MySQL As a local database server ,MySQL Free and efficient , It is completely competent for the application scenario of the system .
This paper develops the campus epidemic prevention and control system based on the standard software development process , Determine the functional requirements of the system through demand analysis , Design the function of the system , Determine the entity relationship of the database , Design database tables according to entity relationship diagram , adopt Java Implement the system , And test the system .
key word : Campus epidemic prevention and control system Java technology MySQL B/S Pattern
ABSTRACT
With the rapid development of the network, the management system using the network has gradually begun to develop. The online management mode has soon been integrated into the eyeballs of many enterprises, and then the "epidemic prevention and control system on campus" has emerged, which makes the information management of epidemic prevention and control on campus more convenient and simple.
For this campus of epidemic prevention and control system design, system development mainly USES the Java language technology, B/S framework, in the design of the whole system using MySQL database to complete the data storage, depending on the real demand to realize campus epidemic prevention and control of network management, all kinds of information in order to storage, page after entering the campus epidemic prevention and control system, can master the initial operation of the interface, the administrator login after the main features include: personal information, information, epidemic dynamics, student information, student information to, isolation, detection, information, statistics, etc.Student: Personal information, information information, epidemic situation, reporting information, detection information, isolation information and other functions.This paper mainly describes the background of the development of the campus epidemic prevention and control system.
The system mainly introduces the demand analysis and functional requirements, and makes a detailed test and summary of the system.Specific from the business process, database design and system structure and other aspects of the problem
Keywords:Campus Epidemic Prevention and control system Java technology MySQL B/S pattern
1 The introduction
1.1 Research background
Internet technology is developing rapidly , With 5G And gigabit optical fiber as the representative of the new generation of network technology has also been rapid development , At present, Internet speed is no longer a major obstacle restricting the development of the Internet [1]. So recite here .........
1.2 Research status
Since the discovery of covid-19 , Has taken many lives , It's very regrettable , At present, although the epidemic has been controlled in China , But other countries in the world are facing the situation of COVID-19 out of control , As a member of globalization , China is still facing huge epidemic prevention and control pressure , Campus prevention and control is still the top priority , How to be effective ...............
1.3 Research significance
In this paper, a campus epidemic prevention and control system is established to manage the prevention and control of COVID-19 by digitalization and informatization . At present, students come from all over the country and are densely populated , The pressure of campus prevention and control is particularly huge , Through this system, students can view personal information online 、 Information information 、 What's going on , And on time .........
1.4 Paper organization structure
At the beginning of developing the system , Some basic knowledge in the system , Mainly from the overall description , And carried out a systematic analysis [2]. The main purpose of analysis and investigation is to make the system better 、 More perfect design . The main research content of this paper is about in the mainstream Web Development framework and standard software development process ..........
The first 1 Chapter The introduction . This chapter introduces the campus epidemic prevention and control system ........
The first 2 Chapter Related development technology and development environment . On the campus epidemic ..........
The first 3 Chapter Systems analysis . The basic functions of the system are introduced ......
The first 4 Chapter Overall design of the system . First of all, from the .........
The first 5 Chapter Detailed design of the system . In this chapter, the use process of each module of the system is designed in detail .
The first 6 Chapter system implementation . in front 4 Zhang Yu .........
The first 7 Chapter The system test . On the campus epidemic ......
The first 8 Chapter Summary and prospect . Carry out .........
2 Related technology and development environment
The system is in the mainstream SSM Web Under the development framework , Use standard software development process , Development B/S The mode of College causes the prevention and control system .........
2.1 Related technology introduction
2.1.1 B/S Architecture brief introduction
At present, with the acceleration of broadband , Internet speed is no longer a major obstacle to the development of the Internet .B/S The application of architecture is widely popular , This mode can ..........
At the same time, this article uses SSM The framework divides the system into control layers 、 View layer and model layer are developed hierarchically , Simplify the system development process , On the basis of improving the maintainability of the system, the principle of independence of each module in the system development is guaranteed .B/S Architecture integration SSM Framework of the MVC Development principles ,............
2.1.2 Java Technical introduction
Java Language was developed by the end of the twentiethcentury Sun Issued by the company , And open source .Java Language has object-oriented characteristics , and C Language is a process oriented programming language , Sequential execution in process oriented programming languages , And about object orientation , In fact, it can be understood that every thing is an object , The object is Java Instantiation of classes in , And a class is an entity that contains some attributes . When using object-oriented ,............
2.1.3 MySQL Database introduction
MySQL It is the most commonly used database in system development , Its small size and fast response , It can meet most usage scenarios , At the same time, it is also a free relational database server , Query the values of attributes in database tables through structured query language , Usually in MySQL Database table , A table needs to have one or more attributes , One of these attributes is required as the primary key of the whole table , Primary keys are non repeatable and are used to uniquely identify an entity [4]............
In this system, by using SSM In the framework Mybatis Management database establishment Dao layer , Realize the data interaction between the system and the database ,..........
2.2 Introduction to development environment
MyEclipse yes Java Applications for , The application development program and debugging environment are well integrated , meanwhile MyEclipse Support extended JavaEE Plug-ins such as Tomca............
3 Systems analysis
After the system requirements analysis , The requirements of the system have been determined , Next, we need to analyze the possible problems in the process of system development through system analysis ,..........
3.1 Feasibility analysis
Whether a system has development significance , A feasibility analysis must be carried out , Whether the deficiencies in some places have been changed through the development of the system , According to the campus epidemic prevention and control system , Developing this system can better solve the problems of administrators' information management of campus epidemic prevention and control , can ..........
3.1.1 Technical feasibility
The technical feasibility analysis is mainly about the technical analysis used , To judge whether the design of the system is possible , Technical analysis is the most important step in the whole analysis process , Is the key to the success of system development . First , The technical data required for the development of the system is easy to obtain and use JSP Dynamic interaction technology , secondly , Database adoption ........
3.1.2 Economic feasibility
All development software or services in the system are open source and free , There is no need to pay patent licensing fees, which greatly saves costs , At the same time, the business process of this system is not complex , Undergraduate knowledge is enough ........
3.1.3 Operational feasibility
The system interface uses HTML build , It has good user friendliness , At the same time, this interface is convenient for later maintenance and upgrading , The system operates ........
3.2 System performance analysis
Simple : If the system works properly , And powerful , stay .......
Scope of application : The campus epidemic prevention and control system developed according to the actual epidemic prevention and control needs of the campus is targeted , It can meet the needs of epidemic prevention and control on campus , At the same time, due to the strong epidemic prevention and control in many places .......
3.3 System functional requirements analysis
For the development process of campus epidemic prevention and control system, the first step is to establish clear user needs , Only under the premise of clarifying the needs of users can we develop products that meet the needs of users .......
3.3.1 Administrator use case diagram
Pictured 3-1 The use case diagram of the system administrator is shown , As shown in the use case diagram, the authority of the system administrator has a total of eight modules , Mainly for students .........
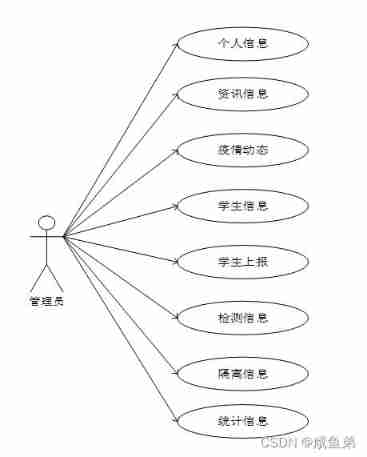
chart 3-1 Administrator use case diagram
3.3.2 Student use case diagram
The student use case is shown in the figure 3-2 Shown , The student module is mainly divided into six functional modules , Through this six function module, students can realize personal information entry and maintenance , see ........
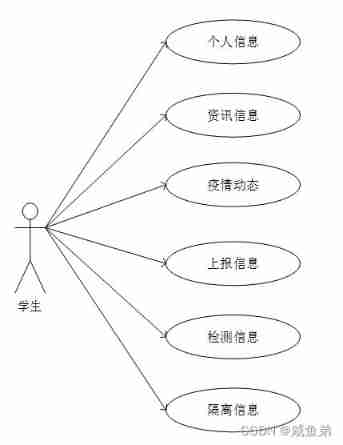
chart 3-2 Student use case diagram
4 Overall design of the system
4.1 Functional structure diagram of the system
Through system requirements analysis , The main functional structure of the campus epidemic prevention and control system is shown in the figure below 4-1 Shown :
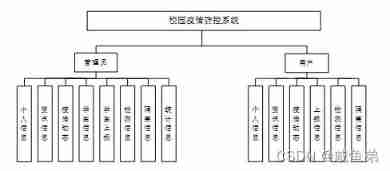
chart 4-1 System function structure diagram
4.2 System database design
4.2.1 Conceptual structural design
Entity relation diagram is an essential part of database design , Abstract the entities and relationships that need to be faced in the process of system data processing through data requirements analysis , Database ........
(1) The information table mainly includes numbers , zhang ......
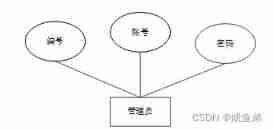
chart 4-2 Administrator entity diagram
(2) The announcement information table mainly includes viewing , title , Content , Photo , Photo name ,......

chart 4-3 Attribute diagram of announcement entity
(3) The epidemic situation dynamic information table mainly includes regions , Diagnosis , Suspected , explain ,..........
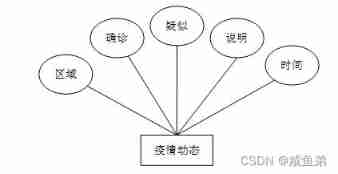
chart 4-4 Epidemic dynamic entity attribute diagram
(4) The student information form mainly includes login name , full name , Gender , Age , Telephone , remarks , class , state , Time ......
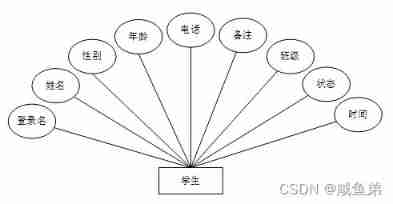
chart 4-5 Student entity attribute map
(5) The inspection information sheet mainly includes numbers , full name , result , explain , junction ......
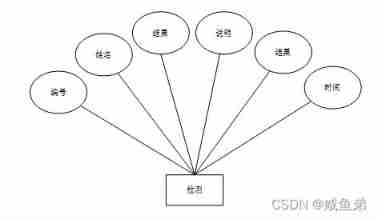
chart 4-6 Detect entity attribute graph
(6) The isolation information table mainly includes classes , full name , Area , Days , say ..........
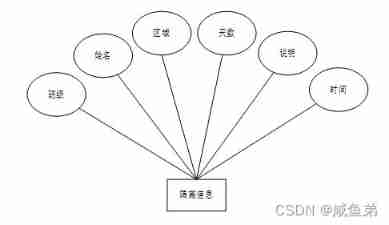
chart 4-7 Attribute graph of isolated information entity
(7) The whole campus epidemic prevention and control system E-R Pictured 4-8 Shown .
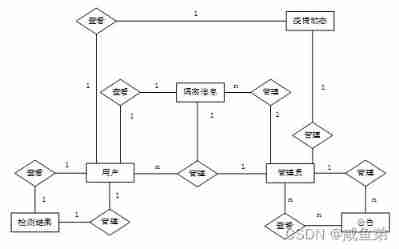
4.2.2 Data logical structure design
The use of each database is separated , Have one or more tables in the database , These tables represent entities and relationships in the database conceptual design model , stay .....
The designed logic data table is as follows :
surface 4-1 t_admin Administrator information table
Name | data type | length | Could you empty | notes |
adminId | int | 20 | no | Number |
adminName | varchar | 20 | yes | account number |
adminPassword | varchar | 20 | yes | password |
surface 4-2 t_gonggao Announcement information sheet
surface 4-3 t_yqdt Epidemic situation dynamic information table
Name | data type | length | Could you empty | notes |
quyu | varchar | 50 | yes | Area |
quezhen | varchar | 50 | yes | Diagnosis |
yisi | varchar | 20 | yes | Suspected |
shuoming | varchar | 50 | yes | explain |
date | varchar | 20 | yes | Time |
surface 4-4 t_user Student information sheet
Name | data type | length | Could you empty | notes |
userId | int | 11 | no | Login name |
userName | varchar | 20 | yes | full name |
userSex | varchar | 20 | yes | Gender |
userAge | varchar | 50 | yes | Age |
userPhone | int | 11 | yes | Telephone |
userBeizhu | int | 11 | yes | remarks |
userBanji | varchar | 20 | yes | class |
UserZhuangtai | varchar | 20 | yes | state |
userTime | int | 11 | yes | Time |
surface 4-5 t_sjxingtai Test information table
surface 4-6 t_geli Test information table
5 Detailed design of the system
5.1 System development process design
The first step of the system is to analyze the needs and clarify the real needs of the target users , Determine the design direction of each module function of the system , Establish the basic system model and analyze Campus epidemic prevention and control system Database tables for conceptual design and detailed design . According to the basic design of the system function , For the system ......
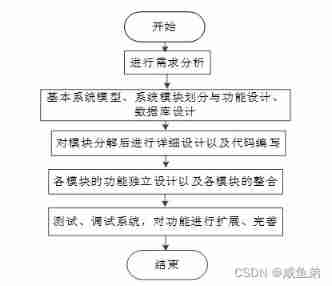
chart 5-1 System development flow chart
5.2 System foreground function process
5.2.1 The login process
In order to ensure the safety of the system , Users or administrators must log in if they want to enter the campus epidemic prevention and control system , You need to select the corresponding user role , Enter login information , Input .......

chart 5-2 Login flowchart
5.2.2 Registration process
Users or administrators without accounts can register , The registration flow chart is shown in Figure 5-3 Shown .
chart 5-3 Registration information flow chart
5.2.3 Password modification process
When changing the password, the user or administrator must enter the original password and the new password . If the operation fails, return to the password modification interface . The flow chart of password modification is shown in Figure 5-4 Shown .
chart 5-4 Change password flowchart
5.3 User module flow chart
(1) Personal information : user Entry system You can view personal information , The content of personal information can be modified . The flow chart of personal information is shown in the figure 5-5 Shown .
(2) Report information : user Entry system You can view the reported information , You can modify the submitted information . The flow chart of reporting information is shown in the figure 5-6 Shown .
chart 5-5 Personal information flow chart chart 5-6 Report information flow chart
(3) The user sequence diagram is shown in Figure 5-7 Shown .
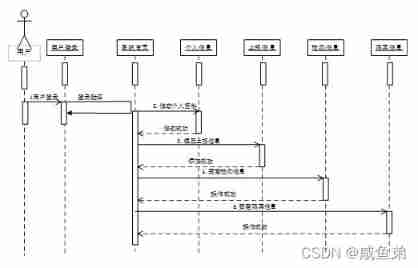
chart 5-7 User sequence diagram
5.4 Administrator module flow chart
(1) Information information : Administrators Entry system You can view information , You can add, delete, modify and query the content of the information . The information flow chart is shown in the figure 5-8 Shown .
(2) What's going on : Administrators Entry system You can view the epidemic situation , You can add, delete, modify and check the dynamic content of the epidemic . The epidemic dynamic flow chart is shown in the figure 5-9 Shown .
chart 5-8 Information flow chart chart 5-9 Epidemic dynamic flow chart
(3) Student information : Administrators Entry system You can view student information , You can add, delete, modify and check the content of student information . The student information flow chart is shown in the figure 5-10 Shown .
chart 5-10 Student information flow chart
(4) The administrator sequence diagram is shown in the figure 5-11 Shown .
chart 5-11 Administrator sequence diagram
6 system implementation
6.1 System interface design and implementation
Open the browser , First, show the homepage of the website of the campus epidemic prevention and control system , This system has a navigation bar interface on the homepage of the website : Users can click to browse , Thus to different ........
chart 6-1 System homepage
6.2 System login interface
The first step of this system needs to log in to the system , The campus epidemic prevention and control system is mainly used for campus internal users . Therefore, the account is created by the administrator . The user needs to enter the user name and password given by the administrator and select the user role , Note that the account numbers between the two roles are not interconnected, so you should select the matching account .........
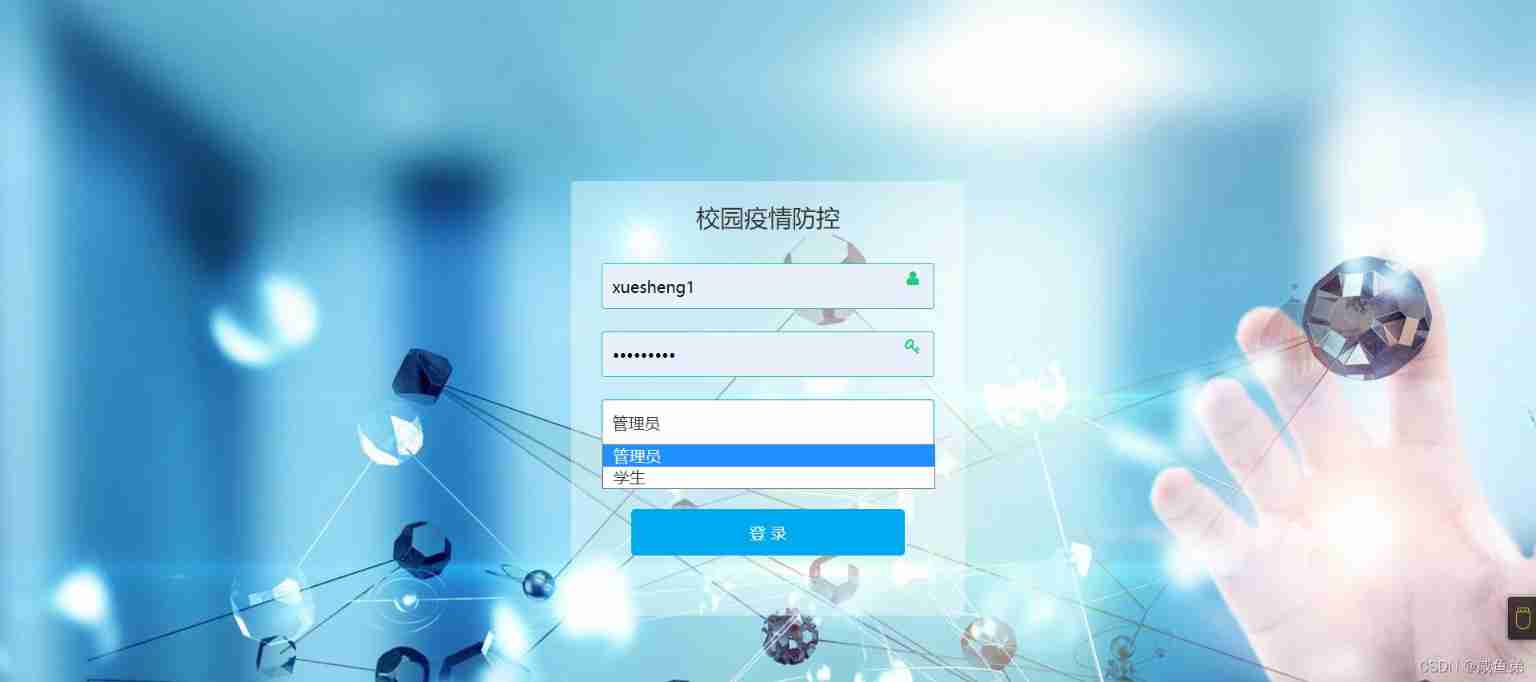
chart 6-2 System login interface
public void mimaAdmin(HttpServletRequest request, HttpServletResponse response)
throws Exception {
try {
JSONObject result = new JSONObject();
String adminPassword = (String) request.getParameter("adminPassword");
String adminPassword1 = (String) request.getParameter("adminPassword1");
Admin admin = new Admin();
admin.setAdminName("admin");
admin.setAdminPassword(adminPassword);
6.3 Design and implementation of client
6.3.1 User center interface
After entering the campus epidemic prevention and control system , Users can see several function modules mentioned in the main page , Login to the client to view personal information 、 Information information 、 What's going on 、 Report ..........
chart 6-3 User center interface
6.3.2 Users modify their personal information
Users can view personal information after entering the system , Click the Modify button to modify your personal information , The modified format will be submitted to the database for update , If ........

chart 6-4 Modify the personal information interface
6.3.3 Users submit submission information
Users can view the reported information after entering the system , Click the Modify button to modify the type , Location , state , Body temperature is modified , Click OK to submit , After submission, it will be submitted to the database for update . If the modification is illegal, the corresponding error will be prompted . Users can also edit their own information ......
chart 6-5 The user submits the report information interface
6.3.4 Users view detection information
Users can view the detection information after entering the system , You can enter the description and type to search and view . The interface is shown in the figure 6-6 Shown .
chart 6-6 Detection information interface diagram
6.3.5 Users view isolation information
The user can view the isolation information after entering the system , You can search and view the area . The interface is shown in the figure 6-7 Shown .
chart 6-7 Isolation information interface
6.4 Design and implementation of administrator
6.4.1 Administrator center interface
The administrator can view personal information after logging in 、 Website information 、 Information information 、 What's going on 、 Report information 、 Students report 、 Detection information 、 Isolation letter .....
chart 6-8 Administrator center interface
6.4.2 Managing personal information
Administrators Entry system You can delete log information , By clicking options , Click the delete button to delete , Successful deletion will delete the corresponding records in the database . The interface is shown in the figure 6-9 Shown .
chart 6-9 Personal information interface diagram
6.4.3 Management information
Administrators Entry system You can view information , You can add, delete, modify and query the contents of the announcement information , You can modify the photos of the announcement , Type and time of announcement . After modification, the front end transmits the information to the server , The server updates the database according to the new data received . The interface is shown in the figure 6-10 Shown .
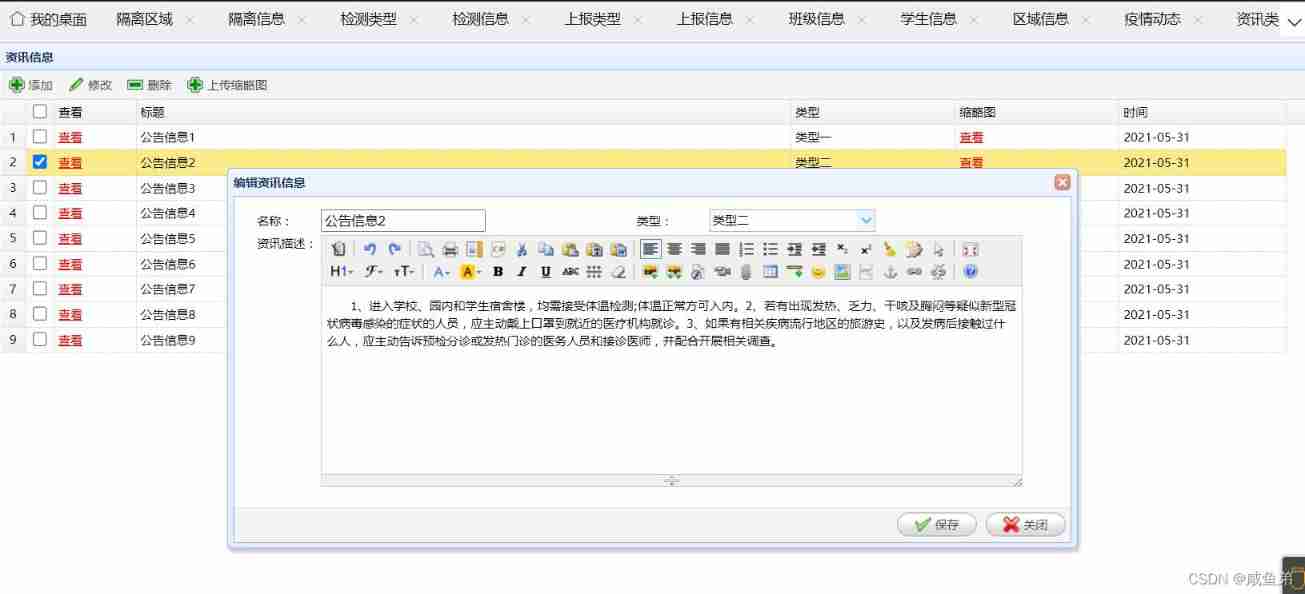
chart 6-10 Information interface
public void getGonggaos(HttpServletRequest request,
HttpServletResponse response) throws Exception {
request.setCharacterEncoding("UTF-8");
response.setCharacterEncoding("UTF-8");
String page = (String) request.getParameter("page");
String rows = (String) request.getParameter("rows");
String gonggaoName = (String) request.getParameter("gonggaoName");
String gonggaoId = (String) request.getParameter("gonggaoId");
String ggtypeId = (String) request.getParameter("ggtypeId");
String sdate = (String) request.getParameter("sdate");
String edate = (String) request.getParameter("edate");
PageBean pageBean = null;
if ((StringUtil.isNotEmpty(page))&&(!page.equals("null"))) {
pageBean = new PageBean(Integer.parseInt(page),Integer.parseInt(rows));
}else{
pageBean = new PageBean(0,0);
}
6.4.4 Manage epidemic dynamics
Administrators Entry system You can view the dynamic information of the epidemic , It can be applied to areas with epidemic dynamics , Number of confirmed cases , Number of suspects , Modify the description and time , Submit to the database for update after successful modification . The interface is shown in the figure 6-11 Shown .
chart 6-11 Epidemic dynamic interface
6.4.5 Manage student information
Administrators Entry system You can view student information , You can login to students , full name , Gender , Age , Telephone , remarks , class , state , Time to modify . Submit to the database for update after successful modification . The interface is shown in the figure 6-12 Shown .
chart 6-12 Student information interface
6.4.6 View student reports
Administrators Entry system You can view the information reported by students , Students can be placed , Type to search . The interface is shown in the figure 6-13 Shown .
chart 6-13 Student report interface
6.4.7 Check the detection information
Administrators Entry system You can view the detection information , You can enter the description and type to search and view . Convenient and rapid screening of student information has not been uploaded . The interface is shown in the figure 6-14 Shown .
chart 6-14 Detection information interface diagram
6.4.8 View isolation information
Administrators Entry system You can view isolation information , You can select an area to search and view . The interface is shown in the figure 6-15 Shown .
chart 6-15 Isolation information interface
6.4.9 View statistics
Administrators Entry system You can view statistics , Statistical information can be transformed into ' The pie chart , More intuitive viewing . The interface is shown in the figure 6-16 Shown .
chart 6-16 Statistical information interface
The key codes of statistical information are as follows :
public void deleteSjleixing(HttpServletRequest request, HttpServletResponse response)
throws Exception {
try {
String delIds = (String) request.getParameter("delIds");
System.out.println("delIds = " + delIds);
JSONObject result = new JSONObject();
String str[] = delIds.split(",");
for (int i = 0; i < str.length; i++) {
sjleixingService.deleteSjleixing(Integer.parseInt(str[i]));
}
result.put("success", "true");
result.put("delNums", str.length);
ResponseUtil.write(response, result);
} catch (Exception e) {
7 The system test
7.1 Program debugging
After the system integration is completed, the system needs to be debugged , Early system debugging ensures that each module of the system can run , Make sure there are no grammatical errors , Reduce runtime errors ......
In the design of the whole program of the system , Some wrong messages often appear . For these instructions, the syntax is wrong , At the same time, the program will prompt ,........ Of .
7.2 testing procedure
(1) The importance of testing
Every developed system will have some big and small problems . If you can't find the problem in the testing phase of the system , It will affect the use of the whole software system to a certain extent , So find problems and solve them , Is the purpose of system testing . The fundamental purpose of system testing is : Whether various functions can be realized , How administrators operate in the system . How to call the data information table in the system , Whether the expected function can be achieved .........
(2) Test steps
For the development process of this system, it must go through several stages ......
The system test is mainly divided into the following steps , Through the following steps, the whole system can be tested from part to whole . In the system test, the first step is module test , In the module test, each module of the system needs to be tested separately , To test whether the function realization of the module conforms to the pre .........
7.3 Test and analysis
After the above testing and analysis, it is mainly carried out from the following aspects :
Use case name : Student login test
Basic description : Have the reservation permission of the system through login
.........
(1) User login test :
surface 7-1 Log in to the test case table
testing procedure | data | Expected results | test result | |
Click the login button | nothing | Go to the login page | success | |
Fill in the user name and verification code , Click the login button | user name | The input box empties the content and prompts “ Please enter your user name and password ” | success | |
Fill in the password and verification code , Click the login button | password | The input box empties the content and prompts “ Please enter your user name and password ” | success | |
Fill in the user name and password , Click the login button | user name 、 password | The input box empties the content and prompts “ Error in captcha input ” | success | |
Fill in the wrong or nonexistent user name and password | user name 、 password | The input box empties the content and prompts “ Wrong user name or password ” | success | |
Fill in the correct user name and password | user name 、 password | Jump to home page , The student's name is displayed in the upper right corner | success | |
(2) Campus epidemic prevention and control management test :
surface 7-2 Campus epidemic prevention and control management test case table
testing procedure | data | Expected results | test result | |
Click the View Details button of campus epidemic prevention and control | nothing | Jump to the details of epidemic prevention and control on campus | success | |
Click the add button | nothing | Jump to add page | success | |
Check the Add button | nothing | Jump to the campus epidemic prevention and control page | success | |
(3) Manage and delete the campus epidemic prevention and control test :
surface 7-3 Adjust the test case table of campus epidemic prevention and control
testing procedure | data | Expected results | test result | |
Click on campus epidemic prevention and control | nothing | The page switches to the campus epidemic prevention and control management module | success | |
Check the campus epidemic prevention and control to delete | nothing | Campus epidemic prevention and control is checked | success | |
Click the delete button | nothing | A pop-up box prompts the service | ||
Click to query | nothing | The page switches to the campus epidemic prevention and control management module | success | |
Check all information about epidemic prevention and control on the campus | nothing | Campus epidemic prevention and control is checked | success | |
Click the delete button | nothing | The pop-up box indicates that campus epidemic prevention and control cannot be deleted | success | |
Click the delete button | nothing | The pop-up box indicates that the operation is successful | success | |
7.4 Test conclusion
Through the above tests, we found that the campus epidemic prevention and control system conforms to the functional design , In the test, we complete the function test of the system through different test cases , For example, enter the wrong user name and password in the login interface , The system prompts that the user name and password are incorrect , or .........
8 Summary and prospect
8.1 summary
The development of campus epidemic prevention and control system mainly uses Java Language development , The system server is local Tomcat The server , System development options MyEclipse As JavaEE The compiler of the project , For system development architecture B/S structure , Students can directly open the browser to visit ........
8.2 expectation
After using programming technology to realize the project , Test each module of the system , Correct the errors found in time . Finally, the modules of the system that can work normally Play different functions , Staff can more clearly understand and learn the operation process of this system , And be able to control the system .........
If you need more information, please download it from the link below
边栏推荐
- Unpool(nn.MaxUnpool2d)
- Cut! 39 year old Ali P9, saved 150million
- Day_ 17 IO stream file class
- Use the difference between "Chmod a + X" and "Chmod 755" [closed] - difference between using "Chmod a + X" and "Chmod 755" [closed]
- 使用druid連接MySQL數據庫報類型錯誤
- tuple and point
- Pgadmin 4 V6.5 release, PostgreSQL open source graphical management tool
- Advanced conditional statements of common SQL operations
- Security level
- openresty ngx_lua執行階段
猜你喜欢
Go RPC call

CAM Pytorch
openresty ngx_lua执行阶段
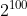
Security level
Single line function*
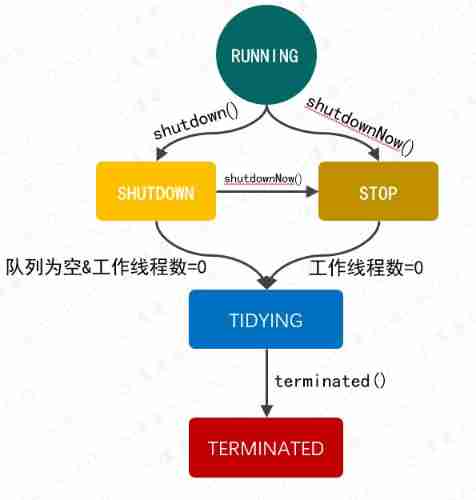
Write a thread pool by hand, and take you to learn the implementation principle of ThreadPoolExecutor thread pool
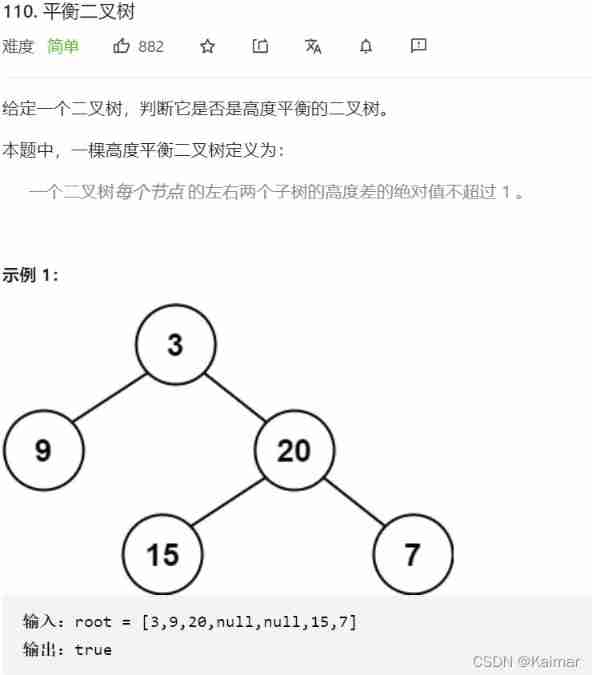
【LeetCode】110. Balanced binary tree (2 brushes of wrong questions)
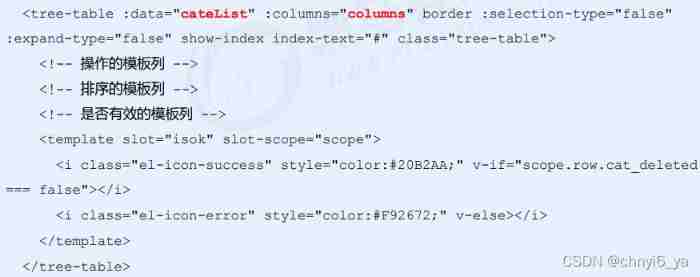
8. Commodity management - commodity classification
Elfk deployment
Pytest (5) - assertion
随机推荐
Visual explanation of Newton iteration method
Grub 2.12 will be released this year to continue to improve boot security
The perfect car for successful people: BMW X7! Superior performance, excellent comfort and safety
JVM's responsibility - load and run bytecode
Exploration of short text analysis in the field of medical and health (I)
Word processing software
Leetcode takes out the least number of magic beans
Restful fast request 2022.2.1 release, support curl import
Avoid material "minefields"! Play with super high conversion rate
Stored procedure and stored function in Oracle
Which common ports should the server open
Kotlin - coroutine
TCP security of network security foundation
LeetCode 314. Binary tree vertical order traversal - Binary Tree Series Question 6
数据库和充值都没有了
Naacl 2021 | contrastive learning sweeping text clustering task
Cut! 39 year old Ali P9, saved 150million
Restful Fast Request 2022.2.1发布,支持cURL导入
100 basic multiple choice questions of C language (with answers) 04
[機緣參悟-38]:鬼穀子-第五飛箝篇 - 警示之一:有一種殺稱為“捧殺”