当前位置:网站首页>Redis distributed lock, lock code logic
Redis distributed lock, lock code logic
2022-07-05 02:11:00 【I use mosquito repellent incense】
public boolean lock(String key, String value) {
if(redisTemplate.opsForValue().setIfAbsent(key, value)) {
return true;
}
String currentValue = redisTemplate.opsForValue().get(key);
if (!StringUtils.isEmpty(currentValue)
&& Long.parseLong(currentValue) < System.currentTimeMillis()) {
String oldValue = redisTemplate.opsForValue().getAndSet(key, value);
if (!StringUtils.isEmpty(oldValue) && oldValue.equals(currentValue)) {
return true;
}
}
return false;
}
- 1.
- 2.
- 3.
- 4.
- 5.
- 6.
- 7.
- 8.
- 9.
- 10.
- 11.
- 12.
- 13.
- 14.
- 15.
Suppose there are two threads now A and B At the same time lock() Method , That is, the of these two threads value It's exactly the same , All for value=2020-12-19, And they all carry out String oldValue = redisTemplate.opsForValue().getAndSet(key, value);, There will be one to execute first and then :
If a thread A Execute first , Back to oldValue=2020-12-18, Simultaneous setting value = 2020-12-19, because oldvalue=currentValue return true, namely A The thread is locked ;
here B The thread continues to execute , Back to oldValue=2020-12-19,oldvalue!=currentValue, return false, Locking failed
So the logic of this code is to lock only one thread
边栏推荐
- 187. Repeated DNA sequence - with unordered_ Map basic content
- 如何搭建一支搞垮公司的技術團隊?
- Visual explanation of Newton iteration method
- Use the difference between "Chmod a + X" and "Chmod 755" [closed] - difference between using "Chmod a + X" and "Chmod 755" [closed]
- [source code attached] Intelligent Recommendation System Based on knowledge map -sylvie rabbit
- JVM's responsibility - load and run bytecode
- RichView TRVStyle MainRVStyle
- What is the length of SHA512 hash string- What is the length of a hashed string with SHA512?
- I use these six code comparison tools
- Yolov5 model training and detection
猜你喜欢
![[technology development-26]: data security of new information and communication networks](/img/13/10c8bd340017c6516edef41cd3bf6f.png)
[technology development-26]: data security of new information and communication networks
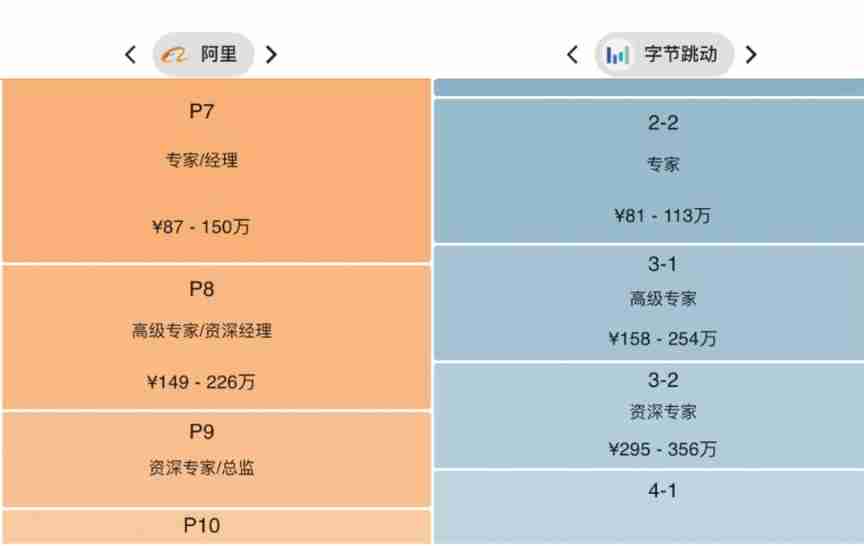
He was laid off.. 39 year old Ali P9, saved 150million

如何搭建一支搞垮公司的技術團隊?
![[OpenGL learning notes 8] texture](/img/77/a4a784a535ea6f4c2382857b266cec.jpg)
[OpenGL learning notes 8] texture
Summary and practice of knowledge map construction technology
Interesting practice of robot programming 15- autoavoidobstacles
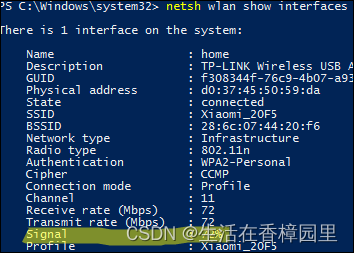
Win:使用 PowerShell 检查无线信号的强弱
Grub 2.12 will be released this year to continue to improve boot security
Icu4c 70 source code download and compilation (win10, vs2022)
Yolov5 model training and detection
随机推荐
Yyds dry inventory swagger positioning problem ⽅ formula
Practical case of SQL optimization: speed up your database
Learn tla+ (XII) -- functions through examples
Win:使用 Shadow Mode 查看远程用户的桌面会话
Chinese natural language processing, medical, legal and other public data sets, sorting and sharing
Icu4c 70 source code download and compilation (win10, vs2022)
Can financial products be redeemed in advance?
[技术发展-26]:新型信息与通信网络的数据安全
Win: enable and disable USB drives using group policy
MATLB | multi micro grid and distributed energy trading
batchnorm.py这个文件单GPU运行报错解决
STM32 series - serial port UART software pin internal pull-up or external resistance pull-up - cause problem search
Yolov5 model training and detection
如何搭建一支搞垮公司的技术团队?
Restful Fast Request 2022.2.1发布,支持cURL导入
Vulnstack3
Exploration and practice of integration of streaming and wholesale in jd.com
[swagger]-swagger learning
He was laid off.. 39 year old Ali P9, saved 150million
Outlook:总是提示输入用户密码