当前位置:网站首页>[technology development-26]: data security of new information and communication networks
[technology development-26]: data security of new information and communication networks
2022-07-05 01:58:00 【Silicon based workshop of slow fire rock sugar】
Preface :
Network security , Usually refers to computer network The safety of the , In fact, it can also refer to computer Communication network The safety of the . Computer communication network is the interconnection of several computers with independent functions through communication equipment and transmission media , With the support of communication software , A system that realizes information transmission and exchange between computers . Computer network refers to Shared resources For the purpose , utilize Means of communication Put several independent computer systems that are relatively scattered in the region 、 The terminal equipment is connected with the data equipment , And exchange data under the control of the protocol . The fundamental purpose of computer network is resource sharing , Communication network is the way to realize network resource sharing , therefore , Computer networks are secure , The corresponding computer communication network must also be secure , It should be able to realize... For network users Information switching And Resource sharing . Below , Network security refers to computer network security , Also refers to computer communication network security .
The basic meaning of safety : Objectively, there is no threat , Subjectively, there is no fear . That is, the object is not worried about its normal state being affected . Network security can be defined as : A network system is free from any threat and infringement , It can normally realize the function of resource sharing . To make the network realize the function of resource sharing normally , First of all, we must ensure the hardware of the network 、 The software can run normally , Then we should ensure the security of data information exchange . You can see from the previous two sections , Due to the abuse of resource sharing , It leads to network security problems . Therefore, the technical way of network security is to implement limited sharing .
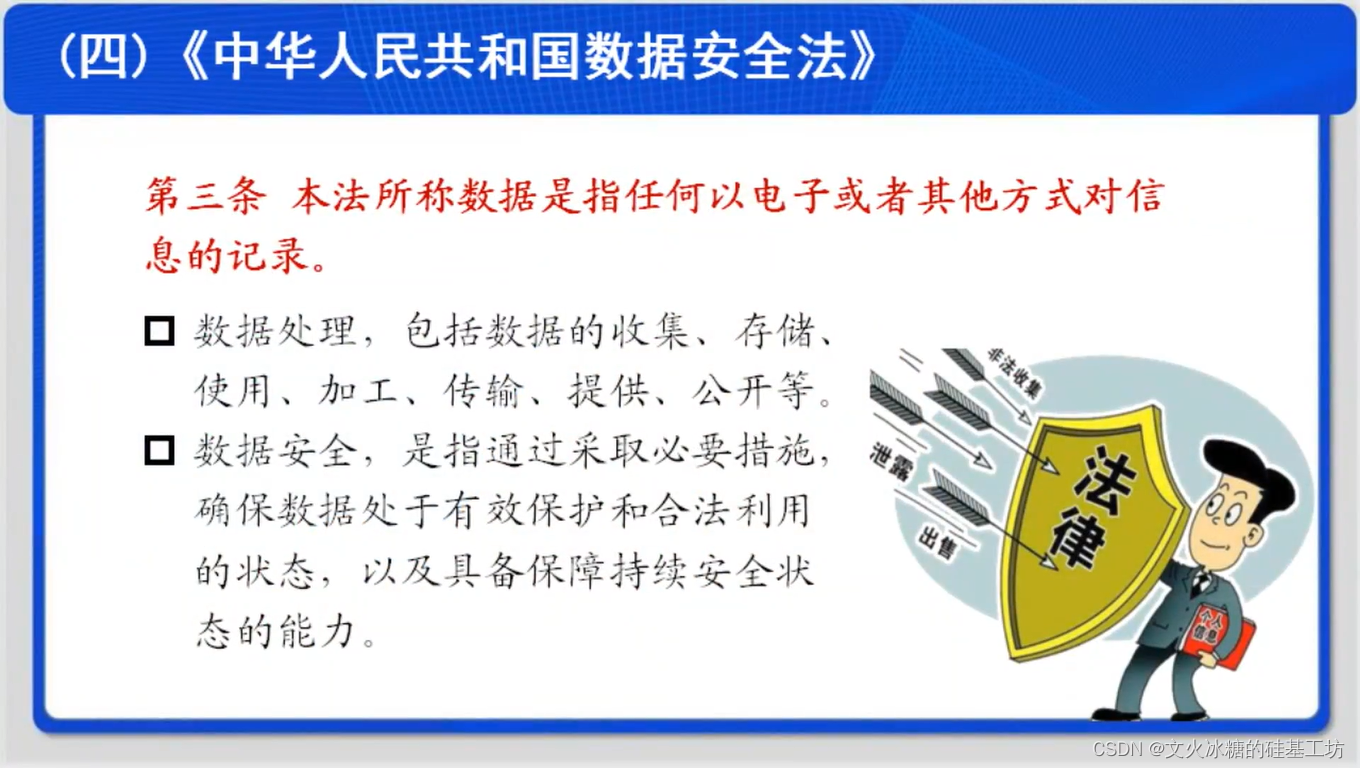
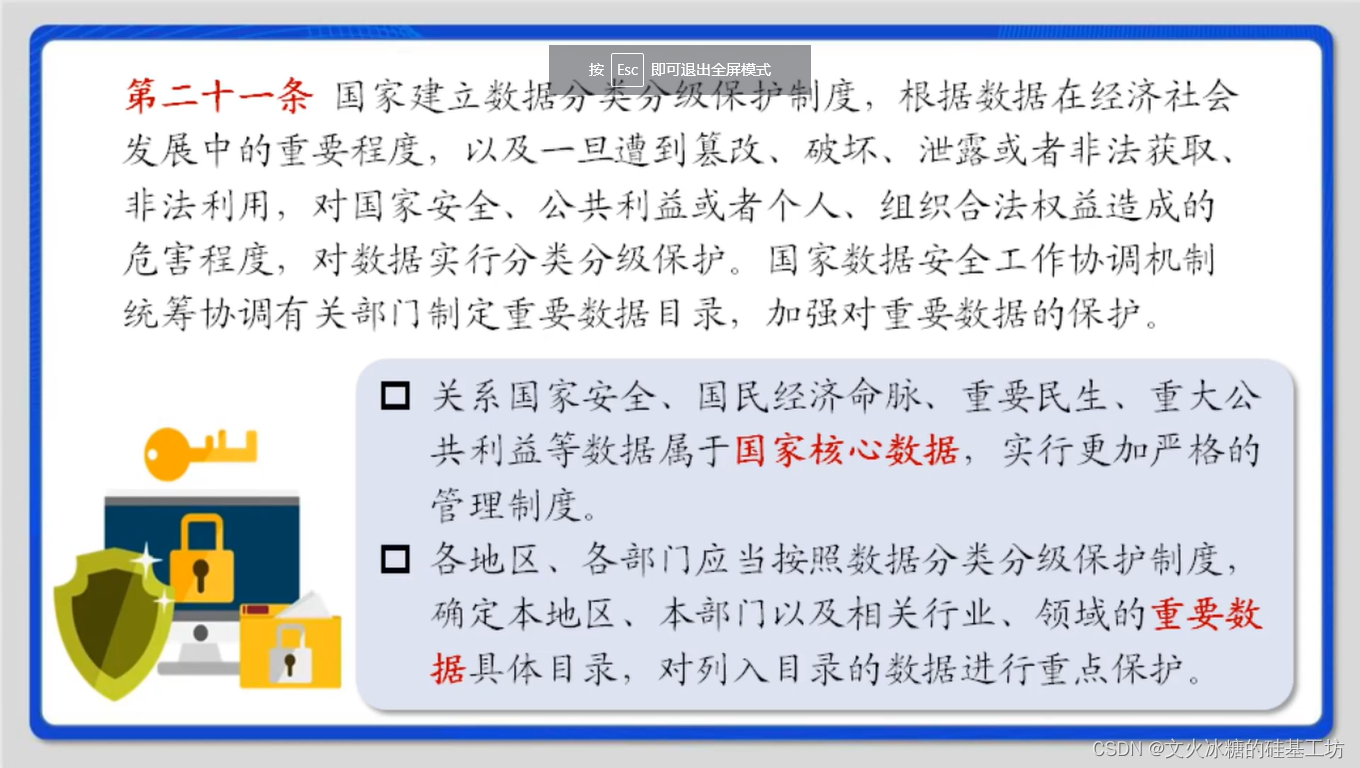
Definition of data security , By taking necessary measures , Make sure data In a state of effective protection and legal utilization , And the ability to maintain a state of continued security . Data security is the whole process security of data processing , Data processing , Including data collection 、 Storage 、 Use 、 machining 、 transmission 、 Provide 、 Open, etc .
Information security or data security have opposite meanings : One is the security of the data itself , Mainly refers to the adoption of modern cryptographic algorithm Actively protect data , Such as data confidentiality 、 Data integrity 、 Bidirectional strong Identity Authentication etc. , Data security is an active protection measure , The security of data itself must be based on reliable encryption algorithm and security system , There are mainly Symmetric algorithm And Public key cryptosystem Two kinds of . The second is the security of data protection , It mainly adopts modern information storage means to actively protect data , For example, through the disk array 、 The data backup 、 Disaster tolerance in other places And other means to ensure the security of data ,
Security of data processing It refers to how to effectively prevent data from entering 、 Handle 、 Due to hardware failure in statistics or printing 、 power failure 、 crash 、 Human misoperation 、 Procedural defects 、 Database damage or data loss caused by viruses or hackers , Some sensitive or confidential data may not be read by qualified personnel or operators , And cause data leakage and other consequences .
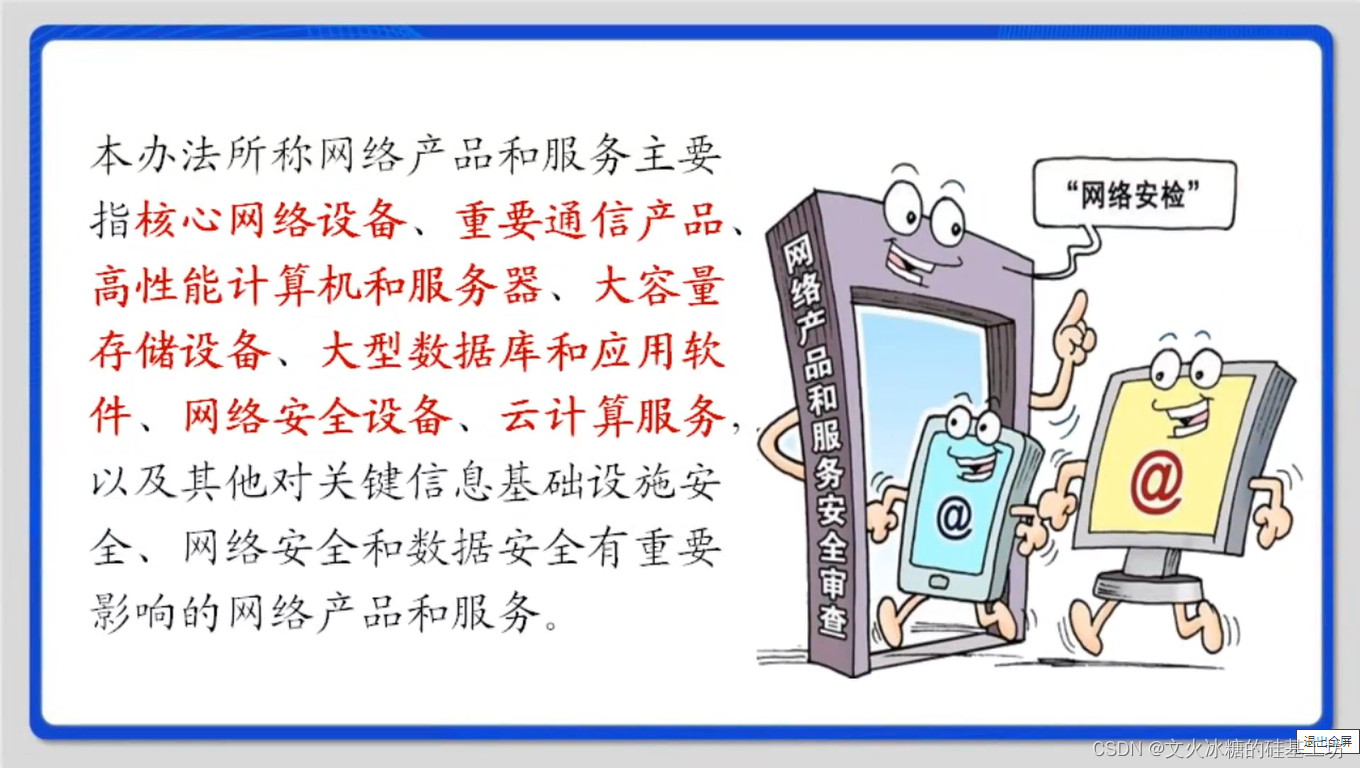
Data storage security It refers to the readability of the database beyond the operation of the system . Once the database is stolen , Even without the original system program , You can also write another program to view or modify the stolen database . From this point of view , An unencrypted database is not secure , Easy to cause commercial leakage , Therefore, the concept of data leakage prevention is derived , This involves Computer network communication Confidentiality of 、 Safety and software protection Other questions .

















边栏推荐
- Subject 3 how to turn on the high beam diagram? Is the high beam of section 3 up or down
- Three properties that a good homomorphic encryption should satisfy
- Common bit operation skills of C speech
- Stored procedure and stored function in Oracle
- Database postragesq PAM authentication
- PHP wechat official account development
- R language uses logistic regression and afrima, ARIMA time series models to predict world population
- Flutter 2.10 update details
- Limited query of common SQL operations
- [swagger]-swagger learning
猜你喜欢
力扣剑指offer——二叉树篇
MATLB|多微电网及分布式能源交易
Is there a sudden failure on the line? How to make emergency diagnosis, troubleshooting and recovery
Incremental backup? db full

如何搭建一支搞垮公司的技术团队?
R语言用logistic逻辑回归和AFRIMA、ARIMA时间序列模型预测世界人口
![[CTF] AWDP summary (WEB)](/img/4c/574742666bd8461c6f9263fd6c5dbb.png)
[CTF] AWDP summary (WEB)

The perfect car for successful people: BMW X7! Superior performance, excellent comfort and safety
PowerShell:在代理服务器后面使用 PowerShell
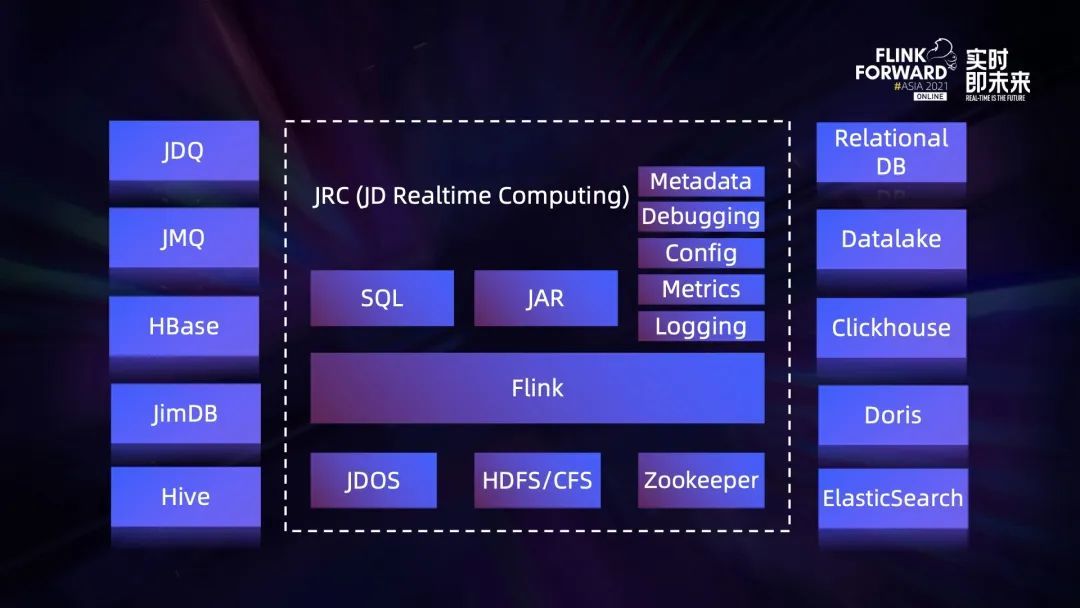
流批一體在京東的探索與實踐
随机推荐
Codeforces Global Round 19 ABC
Database postragesq role membership
JVM's responsibility - load and run bytecode
如何搭建一支搞垮公司的技術團隊?
Pytorch fine tuning (Fortune): hollowed out design or cheating
Prometheus monitors the correct posture of redis cluster
Common bit operation skills of C speech
Rabbit MQ message sending of vertx
Main window in QT application
Pytorch common code snippet collection
Remote control service
Timescaledb 2.5.2 release, time series database based on PostgreSQL
Win: use PowerShell to check the strength of wireless signal
MySQL regexp: Regular Expression Query
Nebula importer data import practice
Flutter 2.10 update details
Incremental backup? db full
Exploration and practice of integration of streaming and wholesale in jd.com
Some query constructors in laravel (2)
Wechat applet: the latest WordPress black gold wallpaper wechat applet two open repair version source code download support traffic main revenue