当前位置:网站首页>H3C firewall rbm+vrrp networking configuration
H3C firewall rbm+vrrp networking configuration
2022-07-06 05:51:00 【Creator of high-quality network system】
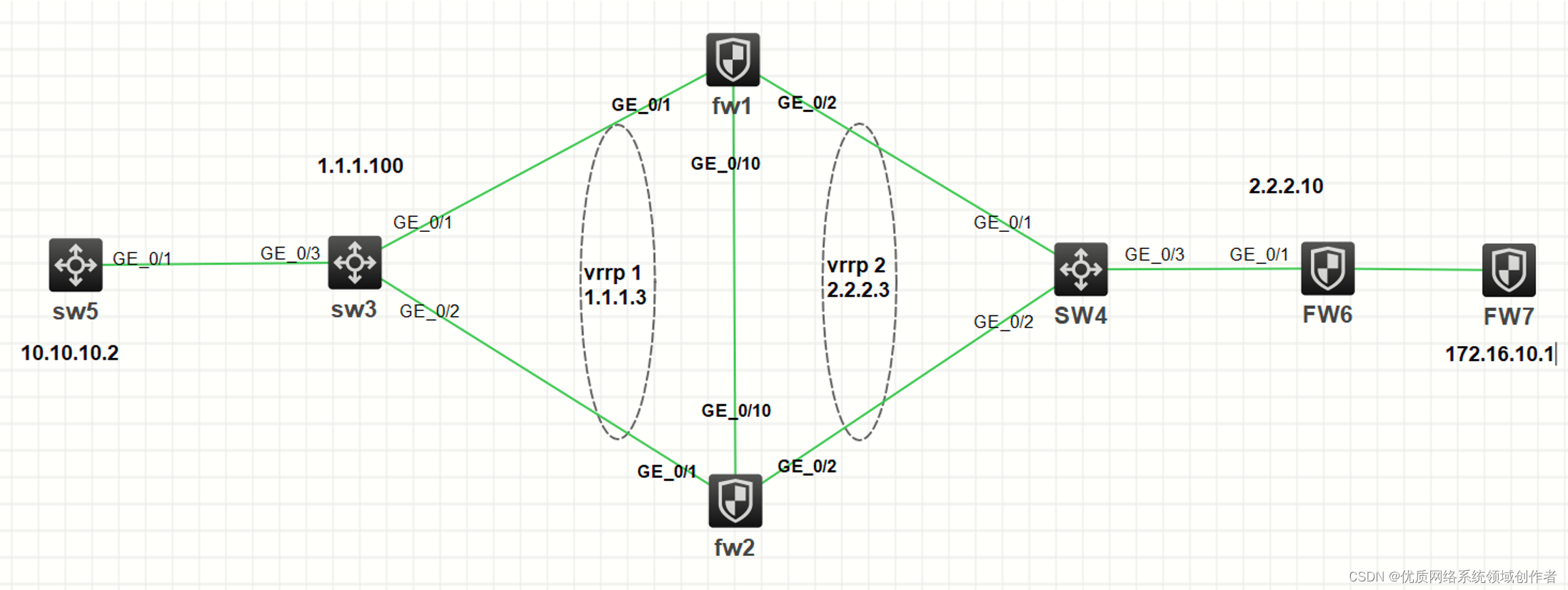
The basic networking is as above , This experiment adopts HCL Simulator complete .fw1 And fw2 establish RBM, The uplink and downlink use vrrp docking .sw3、sw4 by 2 Layer switch , Be a firewall RBM When the connection is accidentally disconnected , It can be transmitted through the switch vrrp message , by vrrp Its own negotiation mechanism realizes active and standby . stay fw1、fw2 Both use vrrp 2 Virtual address of ipsec To configure , Under normal circumstances, the flow goes fw1, Only fw1 and fw6 establish ipsec sa, because RBM Not yet ipsec Synchronization of , So normally fw2 Don't fw6 build ipsec, When the active and standby switches, the traffic goes up fw2, The flow of interest is automatically triggered fw2 and fw6 establish ipsec Tunnel , At the same time as fw6 And the only vrrp Virtual address establishment connection , Can't feel fw1 and fw2 Switch between main and backup , So you need to configure dpd Keep alive detection , When the active and standby switch, the new one can be negotiated in time ike sa and ipsec sa.
Configuration steps
One 、fw1 Basic configuration :
Configure interface ip Address and vrrp Virtual address ,g1/0/10 To act as RBM Interface
interface GigabitEthernet1/0/1
port link-mode route
ip address 1.1.1.1 255.255.255.0
vrrp vrid 1 virtual-ip 1.1.1.3 active
interface GigabitEthernet1/0/2
port link-mode route
ip address 2.2.2.1 255.255.255.0
vrrp vrid 2 virtual-ip 2.2.2.3 active
interface GigabitEthernet1/0/10
port link-mode route
ip address 10.0.0.1 255.255.255.0
Interface plus security domain ,RBM The interface does not need to add a security domain , The device is released by default
security-zone name Trust
import interface GigabitEthernet1/0/1
security-zone name Untrust
import interface GigabitEthernet1/0/2
Configure static routing
ip route-static 10.10.10.0 24 1.1.1.100
ip route-static 172.16.10.0 24 2.2.2.10
To configure RBM, The device acts as the master management device , Main standby mode
remote-backup group
data-channel interface GigabitEthernet1/0/10
configuration sync-check interval 12
local-ip 10.0.0.1
remote-ip 10.0.0.2
device-role primary
Configure detailed security policies , Let go local and trust、untrust Between domains vrrp message
security-policy ip
rule 1 name 1
action pass
source-zone local
destination-zone trust
service vrrp
rule 2 name 2
action pass
source-zone trust
destination-zone local
service vrrp
rule 3 name 3
action pass
source-zone local
destination-zone untrust
service vrrp
rule 4 name 4
action pass
source-zone untrust
destination-zone local
service vrrp
边栏推荐
- Redis6 cluster setup
- Query the standard text code corresponding to a work center (s) in the production order
- Report on the competition status and investment decision recommendations of Guangxi hospital industry in China from 2022 to 2028
- (column 22) typical column questions of C language: delete the specified letters in the string.
- Cannot build artifact 'test Web: War expanded' because it is included into a circular depend solution
- Rustdesk builds its own remote desktop relay server
- 实践分享:如何安全快速地从 Centos迁移到openEuler
- Garbage collector with serial, throughput priority and response time priority
- 27io stream, byte output stream, OutputStream writes data to file
- 【经验】win11上安装visio
猜你喜欢
Station B, Master Liu Er - back propagation
High quality coding tool clion
The usage and difference between strlen and sizeof
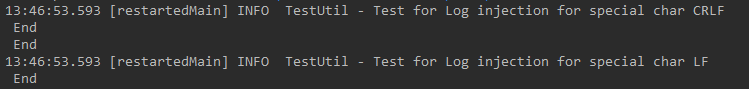
应用安全系列之三十七:日志注入

Sequoiadb Lake warehouse integrated distributed database, June 2022 issue
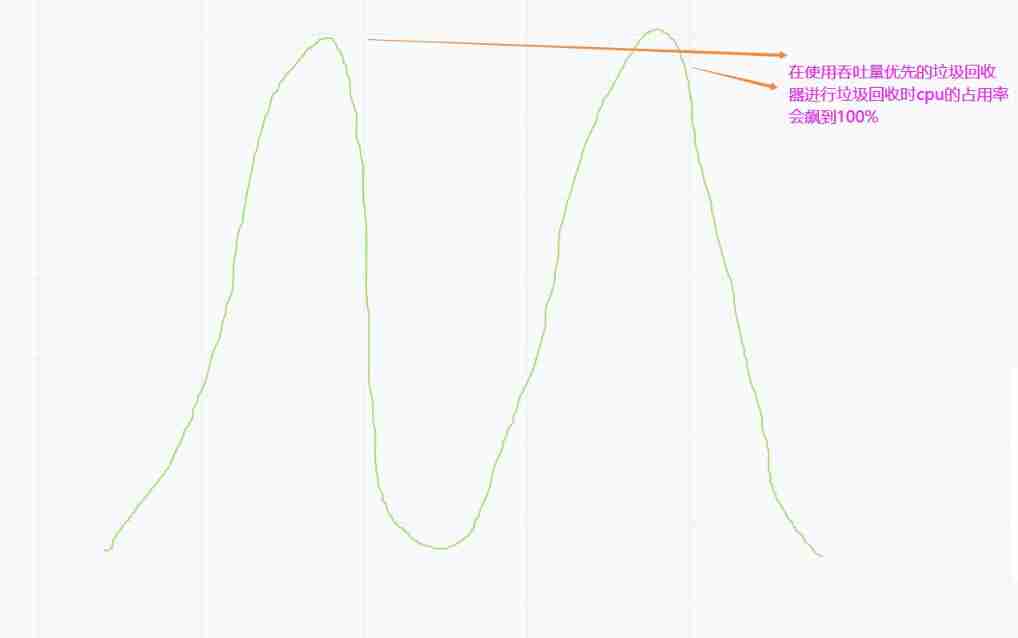
Garbage collector with serial, throughput priority and response time priority

29io stream, byte output stream continue write line feed

What impact will frequent job hopping have on your career?
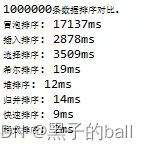
Embedded interview questions (IV. common algorithms)

The ECU of 21 Audi q5l 45tfsi brushes is upgraded to master special adjustment, and the horsepower is safely and stably increased to 305 horsepower
随机推荐
Node 之 nvm 下载、安装、使用,以及node 、nrm 的相关使用
A master in the field of software architecture -- Reading Notes of the beauty of Architecture
Game push: image / table /cv/nlp, multi-threaded start!
应用安全系列之三十七:日志注入
Deep learning -yolov5 introduction to actual combat click data set training
Analysis report on development trends and investment planning of China's methanol industry from 2022 to 2028
查詢生產訂單中某個(些)工作中心對應的標准文本碼
养了只小猫咪
29io stream, byte output stream continue write line feed
Migrate Infones to stm32
【经验】win11上安装visio
华为BFD的配置规范
As3013 fire endurance test of cable distribution system
[SQL Server fast track] - authentication and establishment and management of user accounts
01. Project introduction of blog development project
My 2021
P2802 go home
[Jiudu OJ 08] simple search x
Redis消息队列
28io stream, byte output stream writes multiple bytes