当前位置:网站首页>Alibaba cloud ack introduction
Alibaba cloud ack introduction
2022-07-02 09:54:00 【Don't talk about Xiao Li】
1.k8s The network division
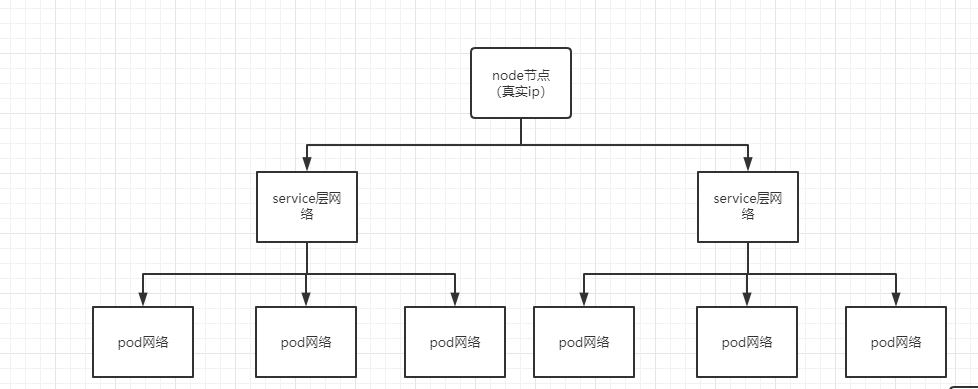
k8s The Internet in ( More detailed summary ) - jojoword - Blog Garden (cnblogs.com)
2.ack The meaning of each layer
1. Cluster information Cluster information shows the basic information and connection information of the cluster
2. Node management
2.1. Node pool Simply understood as machine , Pool of all machines
2.2. node Every machine
3. Namespaces and quotas A literal namespace , Resource isolation
4. The workload
4.1. No state Data that does not need persistence can be used in this way Such as Nginx Tomcat etc.
4.2. A stateful Data needs to be persistent Such as MySQL Redis Message queuing, etc
4.3. Set of daemons The network plugin 、 Log collection 、 Node monitoring, etc
38 k8s-16.DaemonSet: Set of daemons - Panda shrimp - Blog Garden (cnblogs.com)
4.4. Tasks and scheduled tasks
4.4.1. A task is a one-time task
4.4.2. Timed tasks need no explanation
4.5. Container group One pod It is a container group
Container group _ summary | Kuboard
4.6. Custom resources Create custom resources , That is, customize restful api
5. The Internet
5.1. service k8sservice The middle layer in the three-layer network
kubernetes(k8s)service Use - Simple books (jianshu.com)
5.2. route seeing the name of a thing one thinks of its function forward
ingress Introduce - Simple books (jianshu.com)
6. Configuration Management
6.1. Configuration item Save key value pairs of configuration data
k8s -- ConfigMap - Simple books (jianshu.com)
6.2. Confidential dictionary Store sensitive information such as token etc.
[(17 Bar message ) k8s And Secret Understand and use in detail _Jerry00713 The blog of -CSDN Blog ](k8s And Secret Understand and use in detail _Jerry00713 The blog of -CSDN Blog _k8s secret file secrets Used to store and manage some sensitive data , Like passwords ,token, Key and other sensitive information . It is the Pod The encrypted data you want to access is stored in Etcd in ., The user can then use the Pod In the container of Volume Or environment variables Secret There's information in it .)
7. Storage
7.1. Storage statement PVC
7.2. Storage volume PV
7.3. Storage class StorageClass
Xiaobaixue k8s(12)-k8s in PV and PVC understand - ZhanLi - Blog Garden (cnblogs.com)
8. application
8.1.helm k8s Package manager image docker Sum of images docker
8.2. Service Grid (Service Mesh) Not this time , There are too many things involved
8.3.knative Ali component , No introduction
边栏推荐
猜你喜欢
随机推荐
int与string、int与QString互转
How to use pyqt5 to make a sensitive word detection tool
FragmentTabHost实现房贷计算器界面
C语言之二进制与十进制
JDBC回顾
Timed thread pool implements request merging
阿里云SLS日志服务
The latest progress and development trend of 2022 intelligent voice technology
CKEditor 4.10.1 上传图片提示“不正确的服务器响应” 问题解决
阿里云ack介绍
2837xd code generation module learning (4) -- idle_ task、Simulink Coder
Save video opencv:: videowriter
2837xd 代码生成——补充(1)
2837xd代码生成模块学习(3)——IIC、eCAN、SCI、Watchdog、eCAP模块
Data insertion in C language
Operation and application of stack and queue
Int to string, int to qstring
Mobile mall app solution: how much is it to make an app? Detailed explanation of APP mall development content
ZK configuration center -- configuration and use of config Toolkit
2837xd code generation - stateflow (4)