当前位置:网站首页>IP day 16 VLAN MPLS configuration
IP day 16 VLAN MPLS configuration
2022-07-06 05:59:00 【m0_ sixty-four million two hundred and sixty-five thousand thre】
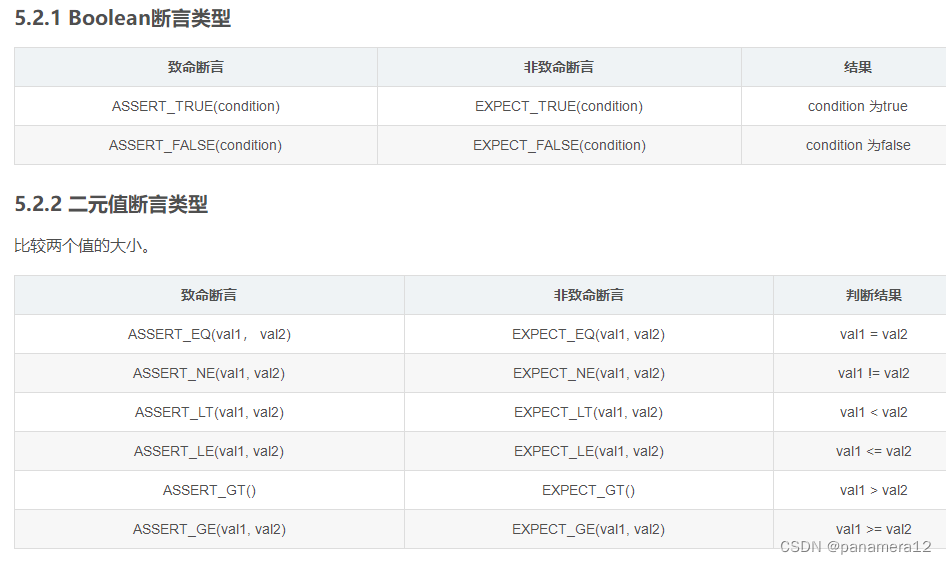
MPLS VPN To configure
establish VRF Space [r2]ip vpn-instance a
[r2-vpn-instance-a]
To configure VRF Space
[r2-vpn-instance-a]route-distinguisher 100:100 --- To configure RD value
[r2-vpn-instance-a-af-ipv4]vpn-target 100:1 export-extcommunity --- Configure outbound RT
[r2-vpn-instance-a-af-ipv4]vpn-target 100:2 import-extcommunity --- Configure inbound RT
[r2-GigabitEthernet0/0/0]ip binding vpn-instance a ---- Speak interface binding Set to the corresponding VRF In the space
( Bind first and then configure ip)
[r2]display ip routing-table vpn-instance a ---- see VRF Spatial routing table
[r2]ping -vpn-instance a 192.168.2.1
[r2]ip route-static vpn-instance a 192.168.1.0 24 192.168.2.1 ---- Configure static routing in the spatial routing table
MP-BGP Jianlin [r2]bgp 1
[r2-bgp]router-id 2.2.2.2
[r2-bgp]peer 4.4.4.4 as 1
[r2-bgp]peer 4.4.4.4 connect-interface LoopBack 0
[r2-bgp]ipv4-family vpnv4
[r2-bgp-af-vpnv4]peer 4.4.4.4 enable
MP-BGP Route Publishing
[r2-bgp]ipv4-family vpn-instance a
[r2-bgp-a]import-route direct
[r2-bgp-a]import-route static
[r2]display bgp vpnv4 vpn-instance a routing-table ---- Look inside the space BGP surface
[r2]display fib vpn-instance a --- Look inside the space FIB surface
[r2]rip 1 vpn-instance a ---- stay VRF Start in space RIP process
[r2-rip-1]v 2
[r2-rip-1]network 192.168.2.0
[r4]ospf 2 vpn-instance b router-id 4.4.4.4 ---- stay VRF Start in space ospf process
Then republish ,bgp To republish, you need to enter your own vpf Space
The three-tier architecture of the enterprise --- Suggestions for building an enterprise network
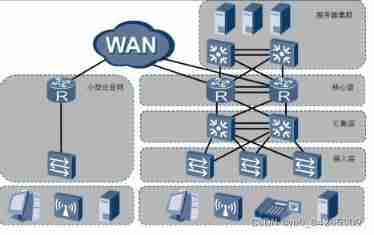
Park ---- factory , The government authority , Office buildings , campus , Park, etc , These public places are The network built to realize data exchange can be called campus network . The side of different campus networks The emphasis may be different .
Wireless is always the last kilometer of wired : Wireless connections need to rely on wireless devices that can transmit and receive wireless signals , And these devices Finally, it also needs to be connected to the network through cable .
AP --- Wireless access point
WLAN --- WLAN ---- In a broad sense, it refers to radio waves , laser , Infrared And so on to replace part or all of the transmission media of the wired LAN .
Wireless networks are inherently flawed :
1, Poor penetration of wireless signals Wireless uses Ethernet Technology --- Frequency division ---- And the civil wireless network uses Data transmission in low frequency band , The congenital defect of low frequency band is poor penetration .
2, The transmission rate of wireless network is related to the signal strength , and , His transmission rate refers to the bidirectional rate
1000 / 8 * 0.85 = 106.25
200 / 8 / 2 * 0.85 = 10.625
3, Wireless network transmission efficiency is low , Slower
Conflict domain : The scope of the conflict --- A hub is in a conflict domain
CSMA/CD --- Carrier sense multiple access / Conflict detection technology WLAN is equivalent to in the same conflict domain , And wireless technology is the way to solve the conflict The method is to use CSMA/CA
CSMA/CA --- Carrier sense multiple access / Conflict avoidance techniques --- Its transmission efficiency is higher than CD Lower technology
The wireless device cannot detect the conflict. The reason --- Dynamic range of wireless signal strength It's very big , Often the received signal strength may be much less than the sent signal strength , This makes it difficult to detect conflicts ( It can increase hardware performance and improve strength )
CA Technology to avoid conflict :
1, When no message is sent in the listening range , Don't send signals directly , It is , Set yourself a random timer first . 2,CSMA/CA The technology adopts stop flow control .
Access layer ---- The main purpose is to connect the terminal equipment to the network , Provide access port ---- Generally, layer-2 switches are used ( rely on MAC Address table realizes two layer forwarding )
Convergence layer ---- The main purpose is to gather the traffic collected by the access layer , Generally, three-layer switching is adopted machine ---- It has a layer-2 interface similar to that used by ordinary layer-2 switches , It also has something similar to routing A three-layer interface used by a device or computer . The biggest difference between the second floor opening and the third floor opening is whether there is IP Address .
The layer-3 switch can pass through MAC Address table realizes two layer forwarding , Three layer forwarding can also be realized through routing table .
The core of the three-tier architecture of enterprise network --- redundancy ---- Backup
1, Line redundancy
2, Equipment redundancy
3, Gateway redundancy
4,UPS redundancy ---- UPS --- Uninterruptible power supply ---- Ensure that the power supply of enterprise equipment reaches To 6 individual 9 The usability of .99.9999%
A real three-tier architecture , There must be redundancy .
Core layer --- The main function is to complete the rapid forwarding of data between public and private networks . ---- One Generally, select the router as the core layer device .
VLAN
V --- fictitious
LAN --- LAN ---- Networks with small geographical coverage
MAN --- Metropolitan area network
WAN --- Wide area network
LAN --- Broadcast area
VLAN --- Virtual LAN --- After the switch and router work together , Put the original one The broadcast domain is logically divided into multiple ;
First step : establish VLAN
[Huawei]display vlan --- see VLAN Information VID --- VLAN ID ---- Distinguish and calibrate different VLAN ---- IEEE Organize and issue 802.1Q The standard requires --- VID Must be by 12 Bit binary structure . Value range 0 - 4095,0 and 4095 Is the reserved number , therefore , The available value range is 1 - 4094
[Huawei]vlan 2 --- establish VLAN
[Huawei]vlan batch 4 to 100 --- Batch creation VLAN
[Huawei]undo vlan batch 4 to 10 --- Batch deletion VLAN
The second step : Put the interface into VLAN
VID Configure the interface mapped to the switch , Realization VLAN Division --- First floor VLAN/ Physics VLAN
VID Configure the mapping to data MAC Address , Realization VLAN Division --- On the second floor VLAN
VID Configure the type fields mapped to the data , Realization VLAN Division --- Three layers VLAN
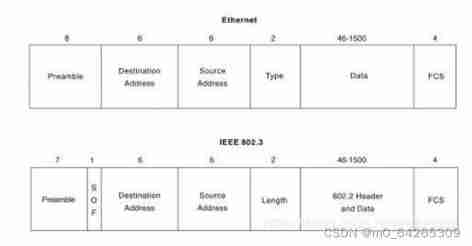
VLAN Can also be based on IP Address division , It can even be done according to the strategy VLAN Divide .
802.1Q Standard design VLAN The label of , By 4 Bytes make up , It includes 12 Bit VID, Used to distinguish between different VLAN Of traffic . And add this label to Ethernet Ⅱ Type frame Source MAC Between address and type fields .
802.1Q The standard stipulates , Frames with labels are called tagged The frame or 802.1Q frame , No label The signed frame is called untagged frame
According to this feature , We call the link between the switch and the computer ACCESS link , and And ,ACCESS The interface on the switch side of the link is called ACCESS Interface .ACCESS Only Can pass untagged frame , also , These frames can only belong to the same VLAN.
We call the link between switches trunk link ,trunk The interfaces at both ends of the link are called trunk Interface .trunk The link is allowed to pass through tagged frame , And these frames can belong to multiple individual VLAN.
The third step : To configure trunk main rd
The second step is configuration
[sw1-GigabitEthernet0/0/1]port link-type access
[sw1-GigabitEthernet0/0/1]port default vlan 2
[sw1]port-group group-member GigabitEthernet 0/0/3 GigabitEthernet 0/0/4
[sw1-port-group] --- Create an interface group
Step 3 configuration
[sw1-GigabitEthernet0/0/5]port link-type trunk
[sw1-GigabitEthernet0/0/5]port trunk allow-pass vlan all
hybrid --- Hybrid interface
[sw1]display port vlan active
Link Type ---- Huawei equipment , The default interface type of all interfaces is hybrid
PVID --- Huawei gives every interface , You need to configure a PVID, That is, the interface belongs to VID. All interfaces have not been changed PVID Default PVID The value is 1.
Huawei system regulations : All data entering the switch through the interface , Must be marked with the right interface Ought to be PVID The label of , in other words , All data inside the switch is labeled .
ACCESS Interface
1, When ACCESS The interface received a message from the link untagged After the frame , Exchange opportunities in this frame add to VID Interface for PVID yes tag, Then look at this VID Whether it is in the Allow list , If in , Then for what you get tagged Forward frames .
2, When tagged The frame goes from other ports of the switch to one ACCESS After a mouth , Then the switch will check Check the... In this frame tag Of VID Whether you are in your allow list , If in , Will tag be stripped Then forward it from the link , If not , Then discard .
3, If ACCESS The interface received a message from the link tagged After the frame , Then directly look at the target of the data Sign the VID Whether you are in your allow list , Forward in , No longer discard .
trunk Interface
1, When trunk The interface received a message from the link untagged frame , The switch adds... To the data frame first One VID by PVID Of tag, Then according to VID View the Allow List , If there is , Then forward , Such as If not , Then discard ;
2, When one tagged The frame goes from other ports of the switch to one trunk After the port , If tag Of VID stay trunk In the allowed list of , Then forward ( If VID and trunk Interface PVID phase meanwhile , The label needs to be peeled off when transferring out , If not PVID The same label , Then directly transfer out ), If not , Throw away ;
3, If trunk The port receives a message from the link tagged After the frame , View tag Medium VID, Such as If in the Allow List , Then forward , be not in , Then discard ;
Different interfaces have different modification permissions when customizing the forwarding table .
ACCESS Modify permission of interface
You can modify PVID, You can also modify the Allow List ( however , The Allow list can only have one VID, And it has to be with PVID identical ), The export packaging method is only non packaging .
trunk Modify permission of interface
You can modify PVID, You can also modify the Allow List , The Allow list can be set to more than one VID, Export packaging is only packaging ( and PVID same VID If it is in the Allow list, it is fixed as No With label )
[sw1-GigabitEthernet0/0/5]port trunk pvid vlan 2 ---- Sure modify trunk Of PVID
hybrid --- Modify permission of hybrid interface
You can modify PVID, You can also modify the Allow List , There can also be more than one allowed list VID, The packaging method can also be modified .
[sw1-GigabitEthernet0/0/1]port link-type hybrid
[sw1-GigabitEthernet0/0/1]port hybrid pvid vlan 2 --- modify hybrid Interface PVID
[sw1-GigabitEthernet0/0/1]port hybrid untagged vlan 2 3 4 --- set Semantic allow list
边栏推荐
- 类和对象(一)this指针详解
- c语言——冒泡排序
- P2802 回家
- The ECU of 21 Audi q5l 45tfsi brushes is upgraded to master special adjustment, and the horsepower is safely and stably increased to 305 horsepower
- Embedded interview questions (I: process and thread)
- Mysql database master-slave cluster construction
- Rustdesk builds its own remote desktop relay server
- MPLS test report
- What is independent IP and how about independent IP host?
- Network protocol model
猜你喜欢
随机推荐
SQLMAP使用教程(三)实战技巧二
What is independent IP and how about independent IP host?
养了只小猫咪
H3C S5820V2_5830V2交换机IRF2堆叠后升级方法
J'ai un chaton.
Grant Yu, build a web page you want from 0
H3C S5820V2_ Upgrade method after stacking IRF2 of 5830v2 switch
公司視頻加速播放
Raised a kitten
[course notes] Compilation Principle
Wib3.0 leapfrogging, in leapfrogging (ง • ̀_•́) ง
Clock in during winter vacation
Garbage collector with serial, throughput priority and response time priority
About PHP startup, mongodb cannot find the specified module
多线程应用的测试与调试
P2802 go home
Practice sharing: how to safely and quickly migrate from CentOS to openeuler
[Jiudu OJ 07] folding basket
wib3.0 跨越,在跨越(ง •̀_•́)ง
The usage and difference between strlen and sizeof
![[Jiudu OJ 08] simple search x](/img/a7/12a00c5d1db2deb064ff5f2e83dc58.jpg)