当前位置:网站首页>Learn to punch in Web
Learn to punch in Web
2022-07-06 20:11:00 【Five five six six_ Pendulum machine 0524】
Hetian network security laboratory
2022.7.5
Use burp Punch in with brute force
burpsuite
burp It is equivalent to adding a layer of proxy at the middle end of the browser sending requests to the server , The request sent will be intercepted
burpsuite Set listening port :
burp:Proxy-Options, Local 8080 The port is selected by default , You can add another Add
Local : Control panel - The Internet and Internet-Internet Options - Connect - LAN settings - proxy server
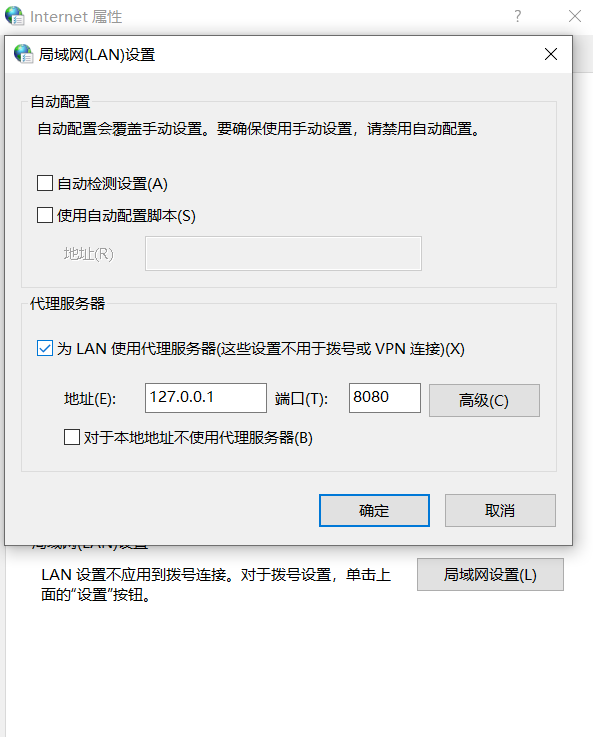
Proxy-Intercept-Intercept is on, Then start visiting the website , Click after interception forward, This package is sent from the proxy to the server , The results returned by the server will still be recorded , Click on drop This bag will be thrown away
compare The module compares the two packets
Right click on the packet send to comparer,Comparer-Words/Bytes
repeater Module replay analysis response
Right click on the packet send to repeater,Repeater-Go, The right side returns the server's response
intruder Module burst
Right click on the packet send to intruder,Target Set to explode host Address and port number ,positions Of Add$ Field blasting point ,Payloads Set the type of blasting fill ,Load Add Dictionary
CTFweb Subtotal two punch
see HTTP Original request package and response package
F12-network- Click on php
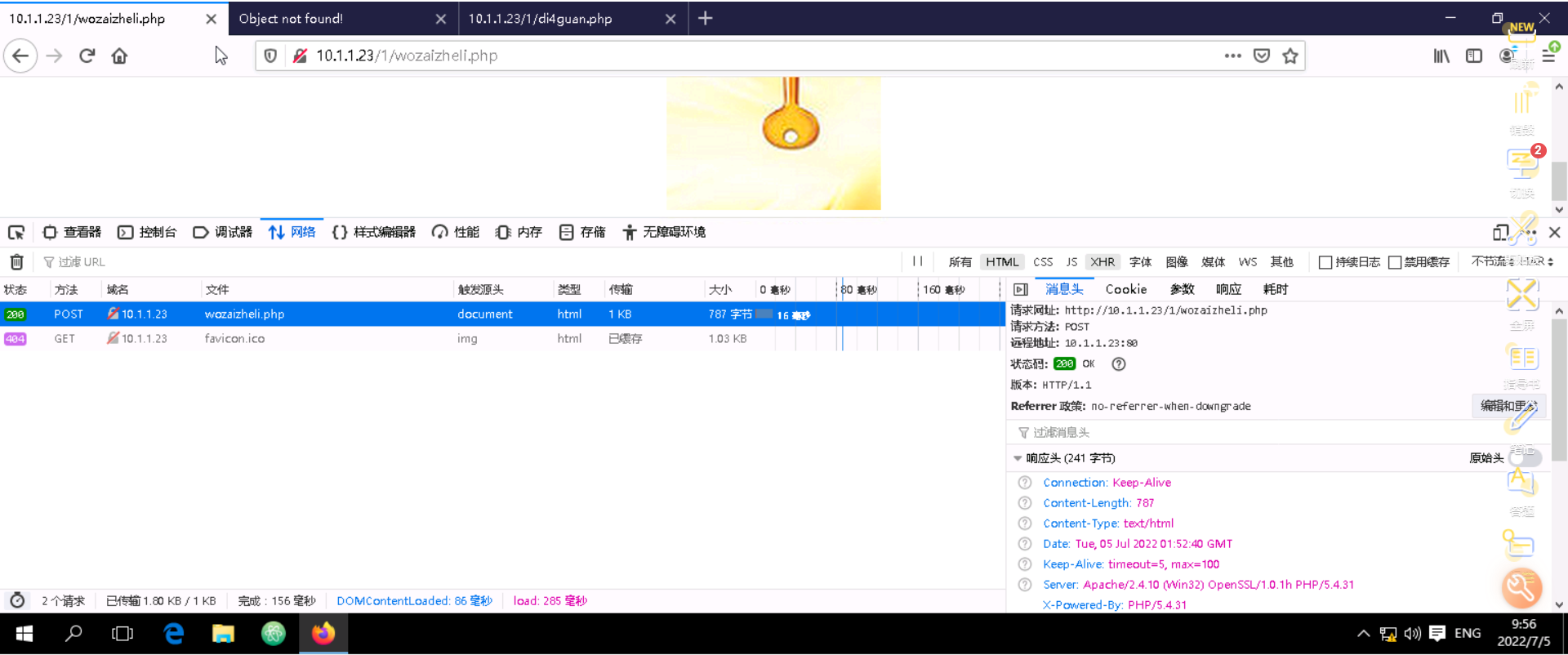
style=“display:none” Hidden elements
Used to hide an element ,none Change it to block You can unhide
●display:none --- Do not reserve physical space for hidden objects , That is, the object disappears completely on the page , Generally speaking, you can't see or touch .
●visible:hidden--- Make objects invisible on Web pages , However, the space occupied by the object on the web page has not changed , Generally speaking, you can't see but feel .
come from display:none_harry5508 The blog of -CSDN Blog _display:none
边栏推荐
- POJ 3207 Ikki's Story IV – Panda's Trick (2-SAT)
- Cesium Click to draw a circle (dynamically draw a circle)
- String长度限制?
- Special topic of rotor position estimation of permanent magnet synchronous motor -- Summary of position estimation of fundamental wave model
- HMS Core 机器学习服务打造同传翻译新“声”态,AI让国际交流更顺畅
- 22-07-05 upload of qiniu cloud storage pictures and user avatars
- Qinglong panel white screen one key repair
- Jupyter launch didn't respond after Anaconda was installed & the web page was opened and ran without execution
- Vscode debug run fluent message: there is no extension for debugging yaml. Should we find yaml extensions in the market?
- 句号压缩过滤器
猜你喜欢
Transformer model (pytorch code explanation)
It's enough to read this article to analyze the principle in depth
(3) Web security | penetration testing | basic knowledge of network security construction, IIS website construction, EXE backdoor generation tool quasar, basic use of
![[network planning] Chapter 3 data link layer (3) channel division medium access control](/img/df/dd84508dfa2449c31d72c808c50dc0.png)
[network planning] Chapter 3 data link layer (3) channel division medium access control
【计网】第三章 数据链路层(4)局域网、以太网、无线局域网、VLAN
新一代垃圾回收器—ZGC
B-杰哥的树(状压树形dp)
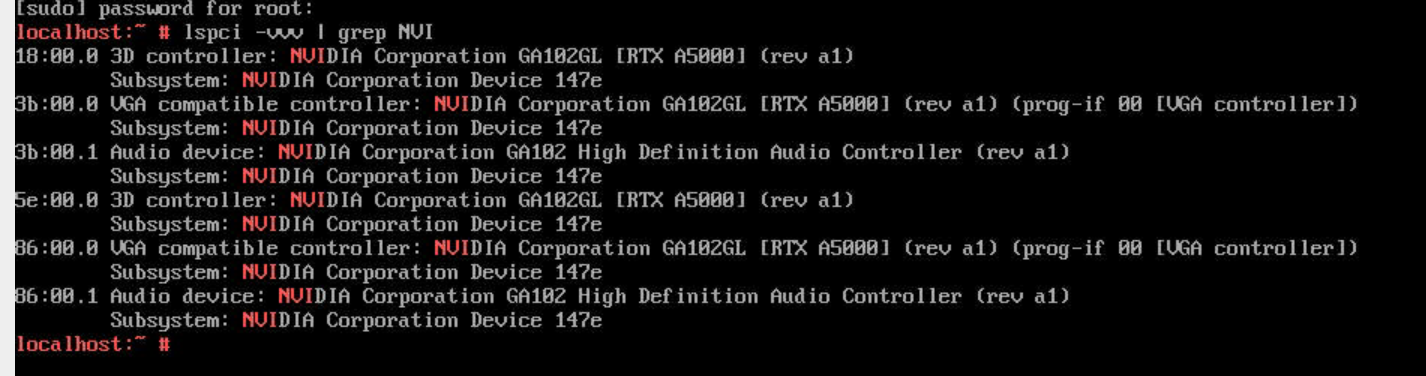
A5000 vgpu display mode switching
Example of shutter text component
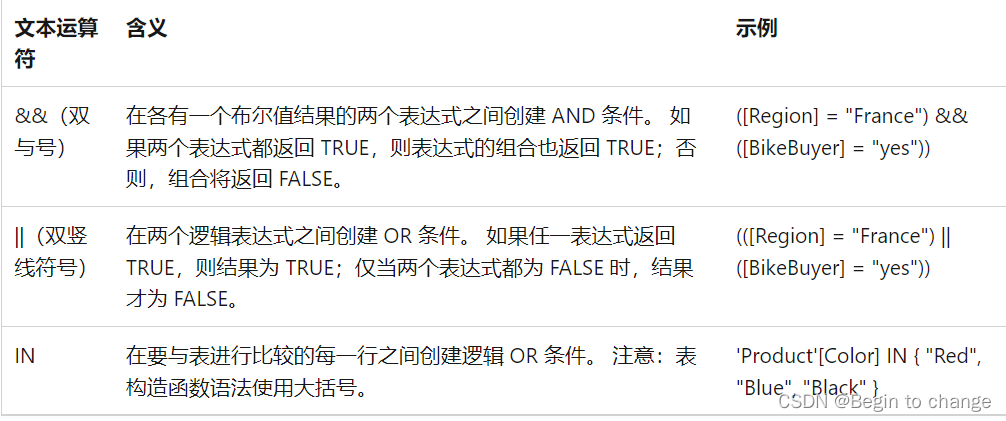
PowerPivot - DAX (first time)
随机推荐
Selenium advanced operations
Cesium 两点之间的直线距离
技术分享 | 抓包分析 TCP 协议
腾讯T4架构师,android面试基础
广州首个数据安全峰会将在白云区开幕
A5000 vGPU显示模式切换
01 基础入门-概念名词
Redisson bug analysis
Initial experience of addresssanitizer Technology
It's enough to read this article to analyze the principle in depth
爬虫(14) - Scrapy-Redis分布式爬虫(1) | 详解
logstash高速入口
BeagleBoneBlack 上手记
22-07-05 upload of qiniu cloud storage pictures and user avatars
青龙面板白屏一键修复
《数字经济全景白皮书》保险数字化篇 重磅发布
Pay attention to the partners on the recruitment website of fishing! The monitoring system may have set you as "high risk of leaving"
Vscode debug run fluent message: there is no extension for debugging yaml. Should we find yaml extensions in the market?
爬虫(14) - Scrapy-Redis分布式爬虫(1) | 详解
永磁同步电机转子位置估算专题 —— 基波模型类位置估算概要