当前位置:网站首页>(3) Web security | penetration testing | basic knowledge of network security construction, IIS website construction, EXE backdoor generation tool quasar, basic use of
(3) Web security | penetration testing | basic knowledge of network security construction, IIS website construction, EXE backdoor generation tool quasar, basic use of
2022-07-06 19:42:00 【Black zone (rise)】
First, learn to use IIS Build a website
Common build platform scripts are enabled
ASP,PHP,ASPX,JSP,PY,JAVAWEB Such as the environment
domain name IP Directory resolution security issues
① adopt IP Address access can find more information , Sometimes you can find program source code backup files and sensitive information
② Domain name access can only find all files in one folder ,ip Access is the upper level of domain name access .
③ Support when building the website IP Access and domain name access , Domain name access points to a directory ,IP Access points to the root directory .
Common file suffix resolution corresponds to security
Specifies that the suffix corresponds to a file , If you encounter a file that cannot be parsed when accessing the website, the middleware may default or add some settings, resulting in problems in parsing .
Set print processing specific program requests
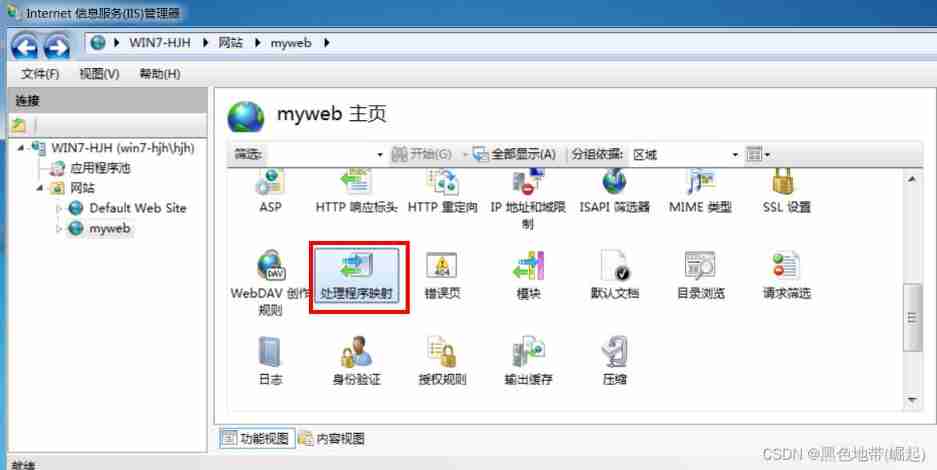
Safety protection in common safety tests
Internal websites of schools and enterprises , Will restrict external access to internal websites , Limit IP Address , Regulate the permissions of visitors . Authentication and access control , User based restrictions , Limit IP Address access , Authorized access - Only specified IP The address can be accessed . Access denied - Appoint IP Address denied access .
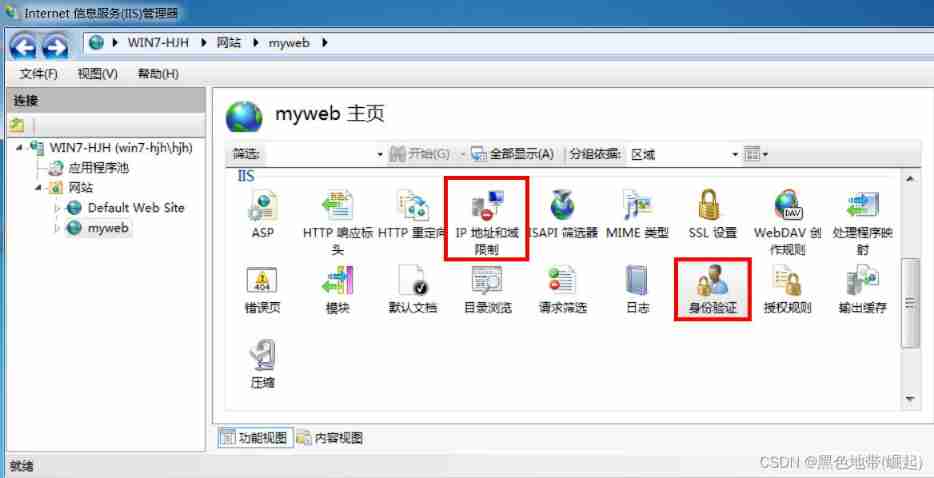
WEB Back door and user and file permissions
exe Back door generation tool Quasar
link :https://pan.baidu.com/s/15XpECQY8SKJwIBxsTy_F3Q
Extraction code :hj12
Usage method :
Folder settings related permissions , Disable guest user permissions , Cause the connected back door to see nothing , It's a protective skill , It is also a common problem in security testing
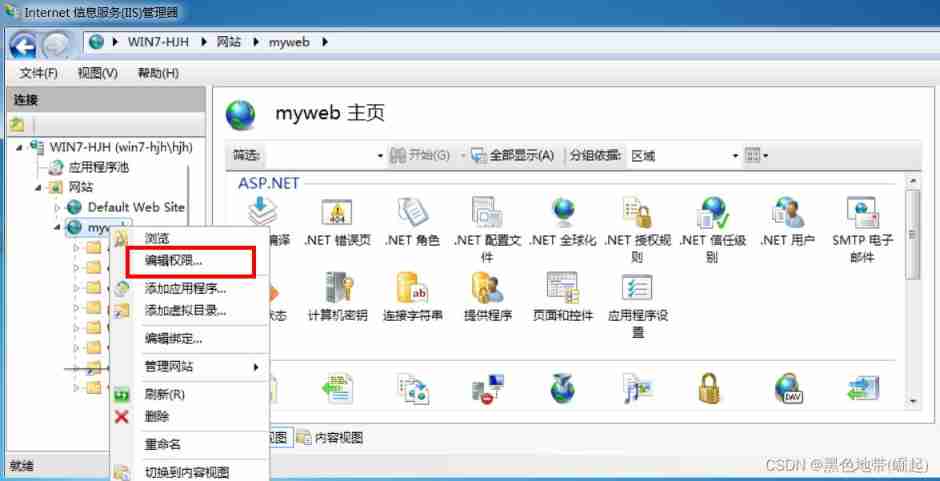
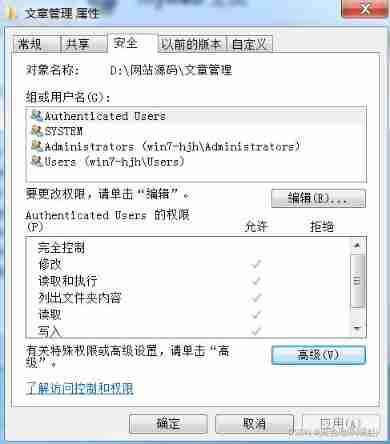
Brief identification based on middleware
The data packet returned by fetching , Query the platform information
service:nginx/1.8.0
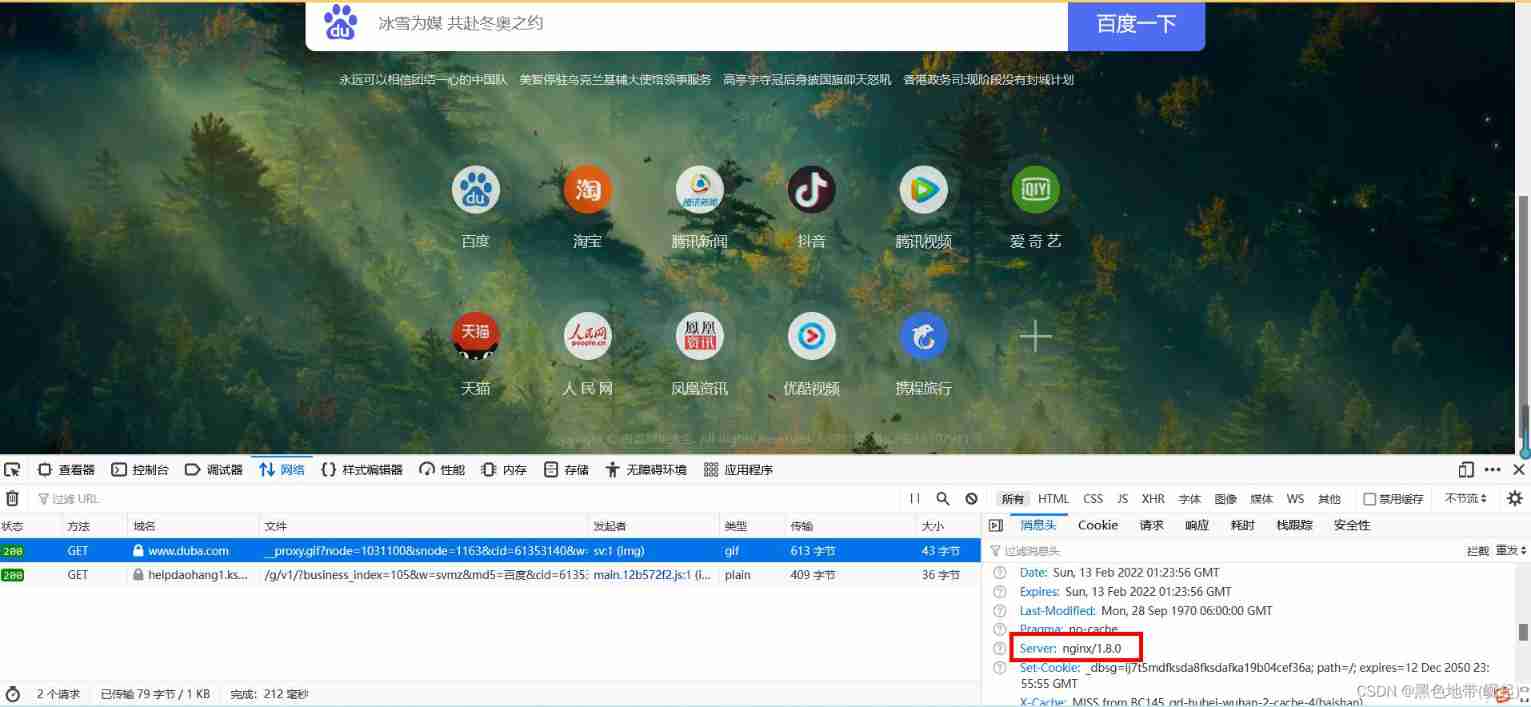
web Summary of common middleware vulnerabilities
link :https://pan.baidu.com/s/1NKejdCI_UY8syRIDfVZwEg
Extraction code :hj12
边栏推荐
- Introduction to enterprise lean management system
- 【计算情与思】扫地僧、打字员、信息恐慌与奥本海默
- Understand yolov1 Part II non maximum suppression (NMS) in prediction stage
- MATLAB中deg2rad和rad2deg函数的使用
- GCC [7] - compilation checks the declaration of functions, and link checks the definition bugs of functions
- Information System Project Manager - Chapter VIII project quality management
- 腾讯T3手把手教你,真的太香了
- VMware virtual machine cannot open the kernel device "\.\global\vmx86"
- Microservice architecture debate between radical technologists vs Project conservatives
- MySQL information Schema Learning (i) - - General table
猜你喜欢
信息系统项目管理师---第八章 项目质量管理
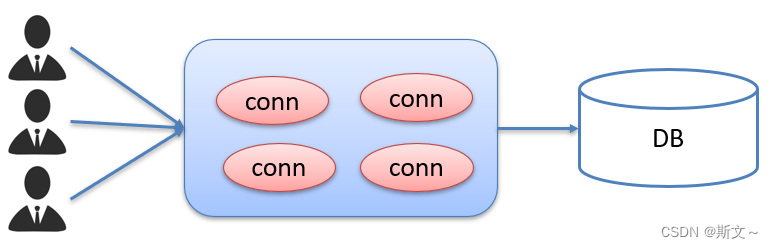
Druid database connection pool details

Carte de réflexion + code source + notes + projet, saut d'octets + jd + 360 + tri des questions d'entrevue Netease
![[translation] linkerd's adoption rate in Europe and North America exceeded istio, with an increase of 118% in 2021.](/img/09/106adc222c06cbd2f4f66cf475cce2.jpg)
[translation] linkerd's adoption rate in Europe and North America exceeded istio, with an increase of 118% in 2021.
MySQL information Schema Learning (i) - - General table

社招面试心得,2022最新Android高频精选面试题分享
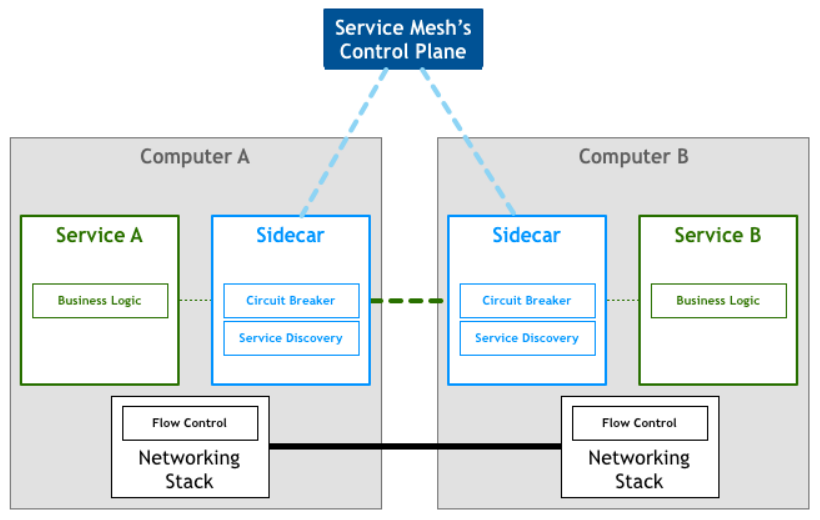
Microservice architecture debate between radical technologists vs Project conservatives
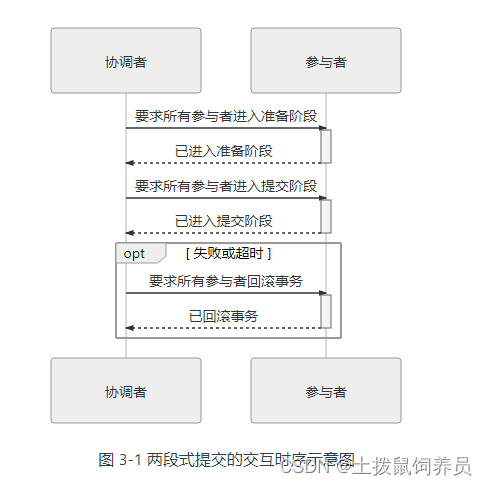
Phoenix Architecture 3 - transaction processing
Problems encountered in using RT thread component fish
Spark foundation -scala
随机推荐
Reflection and illegalaccessexception exception during application
在解决了 2961 个用户反馈后,我做出了这样的改变...
部门树递归实现
今日直播 | “人玑协同 未来已来”2022弘玑生态伙伴大会蓄势待发
Translation D28 (with AC code POJ 26:the nearest number)
终于可以一行代码也不用改了!ShardingSphere 原生驱动问世
【计算情与思】扫地僧、打字员、信息恐慌与奥本海默
思維導圖+源代碼+筆記+項目,字節跳動+京東+360+網易面試題整理
Druid database connection pool details
121. The best time to buy and sell stocks
腾讯Android面试必问,10年Android开发经验
信息系统项目管理师---第八章 项目质量管理
Carte de réflexion + code source + notes + projet, saut d'octets + jd + 360 + tri des questions d'entrevue Netease
The "white paper on the panorama of the digital economy" has been released with great emphasis on the digitalization of insurance
How can my Haskell program or library find its version number- How can my Haskell program or library find its version number?
[translation] Digital insider. Selection process of kubecon + cloudnativecon in Europe in 2022
学习探索-使用伪元素清除浮动元素造成的高度坍塌
从sparse.csc.csr_matrix生成邻接矩阵
Lick the dog until the last one has nothing (simple DP)
学习打卡web
 https://blog.csdn.net/qq_53079406/article/details/122901947?spm=1001.2014.3001.5501
https://blog.csdn.net/qq_53079406/article/details/122901947?spm=1001.2014.3001.5501