当前位置:网站首页>网络安全-ACL访问控制列表
网络安全-ACL访问控制列表
2022-07-03 01:11:00 【IT之一小佬】
ACL
- ACL(Access Control List)访问控制列表
- ACL是一种包过滤技术
ACL基于IP包头的IP地址、四层TCP/UDP头部的端口号,基于三、四层过滤 - ACL在路由器上配置,也可在防火墙上配置(一般称为策略)
参考博文:
网络安全学习--ACL_丢爸的博客-CSDN博客_acl安全
参考视频:
【千锋】网络安全300集全套视频教程(web安全/渗透测试/黑客攻防/信息安全/代码审计),网络安全基础入门到精通_哔哩哔哩_bilibili
【千锋】网络安全300集全套视频教程(web安全/渗透测试/黑客攻防/信息安全/代码审计),网络安全基础入门到精通_哔哩哔哩_bilibili
【千锋】网络安全300集全套视频教程(web安全/渗透测试/黑客攻防/信息安全/代码审计),网络安全基础入门到精通_哔哩哔哩_bilibili
【千锋】网络安全300集全套视频教程(web安全/渗透测试/黑客攻防/信息安全/代码审计),网络安全基础入门到精通_哔哩哔哩_bilibili
【千锋】网络安全300集全套视频教程(web安全/渗透测试/黑客攻防/信息安全/代码审计),网络安全基础入门到精通_哔哩哔哩_bilibili
边栏推荐
- CF1617B Madoka and the Elegant Gift、CF1654C Alice and the Cake、 CF1696C Fishingprince Plays With Arr
- 看完这篇 教你玩转渗透测试靶机Vulnhub——DriftingBlues-9
- 网络安全-漏洞与木马
- High-Resolution Network (篇一):原理刨析
- [keil5 debugging] debug is stuck in reset_ Handler solution
- [my advanced journey of OpenGL learning] collation of Euler angle, rotation order, rotation matrix, quaternion and other knowledge
- Do not log in or log in to solve the problem that the Oracle database account is locked.
- Telecom Customer Churn Prediction challenge
- Why is it not recommended to use BeanUtils in production?
- Vim 9.0正式发布!新版脚本执行速度最高提升100倍
猜你喜欢

Take you ten days to easily complete the go micro service series (I)

Using tensorboard to visualize the model, data and training process

【數據挖掘】任務6:DBSCAN聚類
Summary of interval knowledge

leetcode刷题_两数之和 II - 输入有序数组
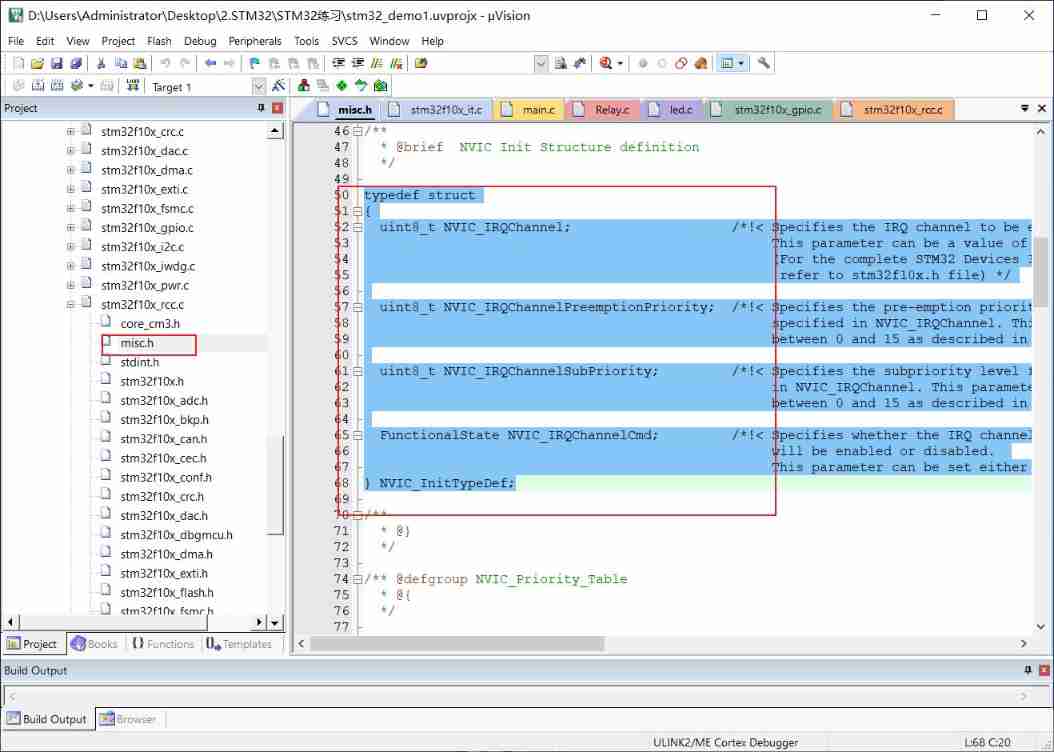
STM32 - introduction of external interrupts exti and NVIC

并发编程的三大核心问题 -《深入理解高并发编程》
![[shutter] animation animation (animatedbuilder animation use process | create animation controller | create animation | create components for animation | associate animation with components | animatio](/img/32/fa1263d9a2e5f77b0434fce1912cb2.gif)
[shutter] animation animation (animatedbuilder animation use process | create animation controller | create animation | create components for animation | associate animation with components | animatio
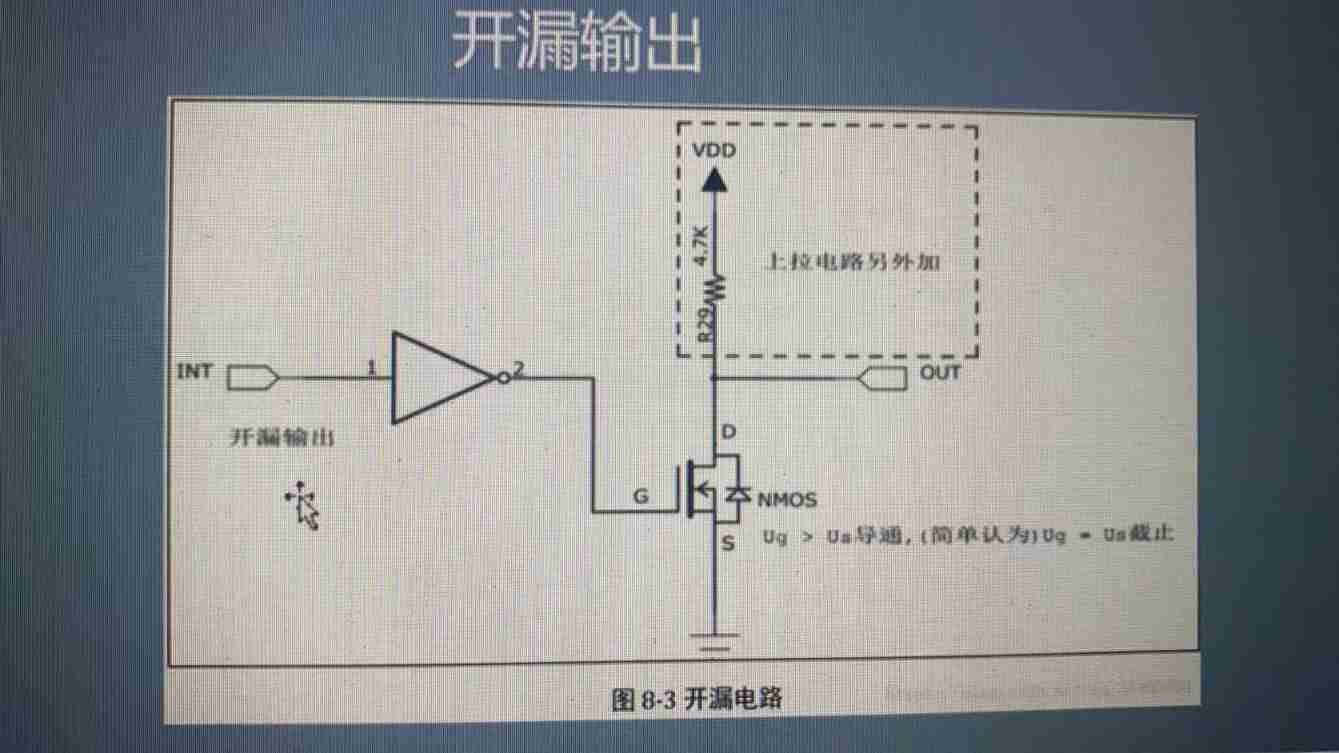
STM32 - GPIO input / output mode
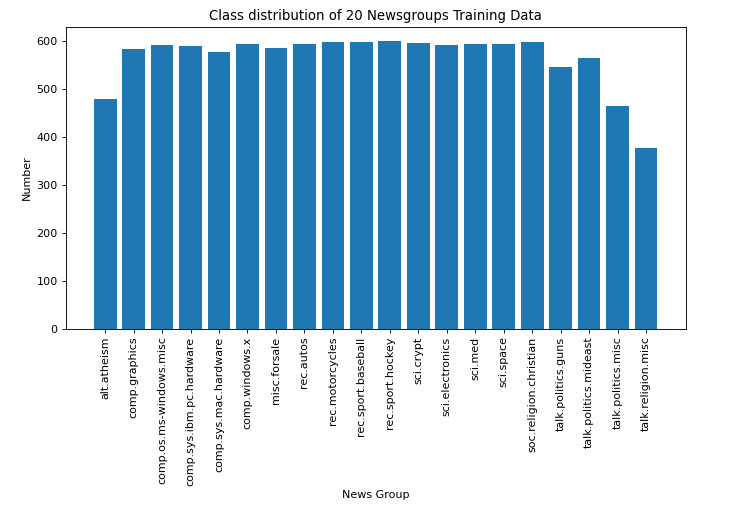
【数据挖掘】任务4:20Newsgroups聚类
随机推荐
Leetcode skimming questions_ Sum of two numbers II - enter an ordered array
[data mining] task 3: decision tree classification
[shutter] animation animation (the core class of shutter animation | animation | curvedanimation | animationcontroller | tween)
Concise analysis of redis source code 11 - Main IO threads and redis 6.0 multi IO threads
Tp6 fast installation uses mongodb to add, delete, modify and check
[data mining] task 2: mimic-iii data processing of medical database
Look at how clothing enterprises take advantage of the epidemic
Learn the five skills you need to master in cloud computing application development
Soft exam information system project manager_ Real topic over the years_ Wrong question set in the second half of 2019_ Morning comprehensive knowledge question - Senior Information System Project Man
[shutter] animation animation (basic process of shutter animation | create animation controller | create animation | set value listener | set state listener | use animation values in layout | animatio
[data mining] task 6: DBSCAN clustering
数学知识:Nim游戏—博弈论
【数据挖掘】任务5:K-means/DBSCAN聚类:双层正方形
How is the mask effect achieved in the LPL ban/pick selection stage?
SSL flood attack of DDoS attack
tail -f 、tail -F、tailf的区别
Summary of interval knowledge
什么是调。调的故事
Arduino dy-sv17f automatic voice broadcast
网络安全-木马