当前位置:网站首页>buuctf misc USB
buuctf misc USB
2022-07-07 07:43:00 【[mzq]】
USB
Title address : https://buuoj.cn/challenges#USB
There are two documents in the title, one 233.rar One key.ftm file , First decompress rar The file gets a flag.txt Ridicule from the author
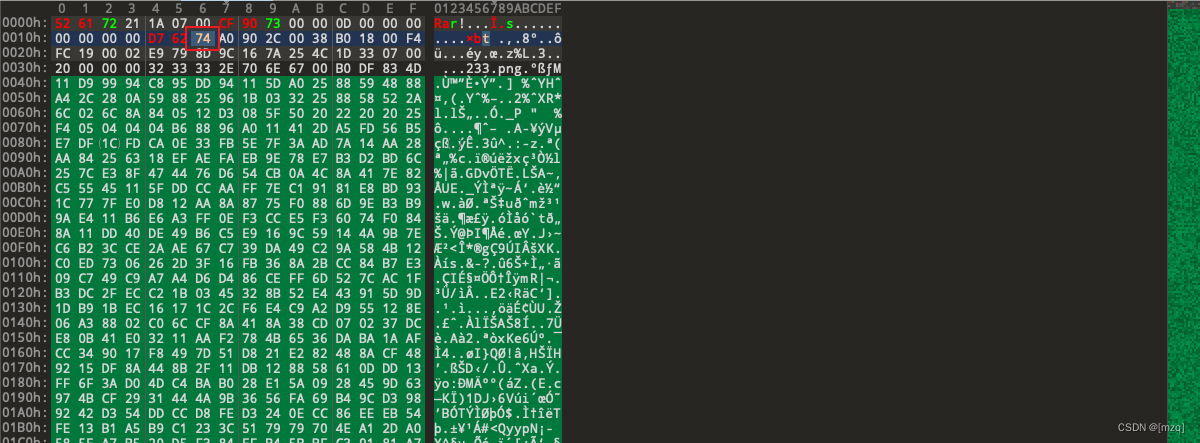
use 010editor Open discovery rar The file block of should be 74 instead of 7A , hold 7A It is amended as follows 74
After repairing and decompressing, you get a 233.png , use stegsolve open , Find the QR code
Scan the code to get
ci{v3erf_0tygidv2_fc0}

stay key.ftm Found in the file zip file , extract zip Decompress the compressed package to get key.pcapng
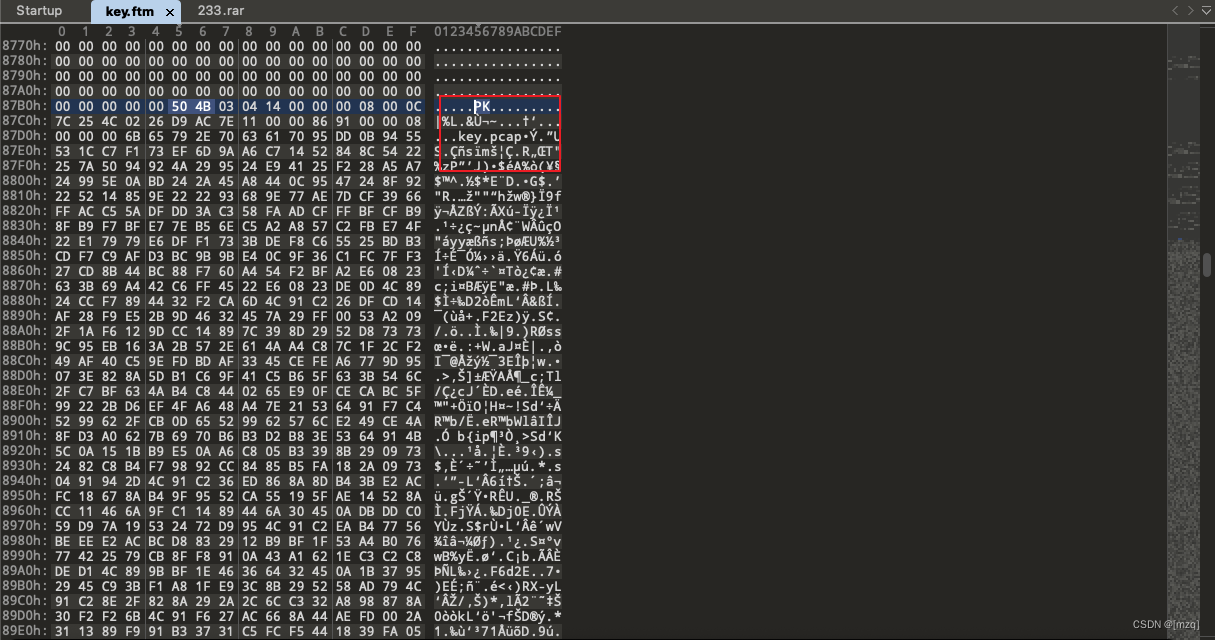
use UsbKeyboardDataHacker Decrypt usb Traffic
#!/usr/bin/env python
import sys
import os
DataFileName = "usb.dat"
presses = []
normalKeys = {
"04":"a", "05":"b", "06":"c", "07":"d", "08":"e", "09":"f", "0a":"g", "0b":"h", "0c":"i", "0d":"j", "0e":"k", "0f":"l", "10":"m", "11":"n", "12":"o", "13":"p", "14":"q", "15":"r", "16":"s", "17":"t", "18":"u", "19":"v", "1a":"w", "1b":"x", "1c":"y", "1d":"z","1e":"1", "1f":"2", "20":"3", "21":"4", "22":"5", "23":"6","24":"7","25":"8","26":"9","27":"0","28":"<RET>","29":"<ESC>","2a":"<DEL>", "2b":"\t","2c":"<SPACE>","2d":"-","2e":"=","2f":"[","30":"]","31":"\\","32":"<NON>","33":";","34":"'","35":"<GA>","36":",","37":".","38":"/","39":"<CAP>","3a":"<F1>","3b":"<F2>", "3c":"<F3>","3d":"<F4>","3e":"<F5>","3f":"<F6>","40":"<F7>","41":"<F8>","42":"<F9>","43":"<F10>","44":"<F11>","45":"<F12>"}
shiftKeys = {
"04":"A", "05":"B", "06":"C", "07":"D", "08":"E", "09":"F", "0a":"G", "0b":"H", "0c":"I", "0d":"J", "0e":"K", "0f":"L", "10":"M", "11":"N", "12":"O", "13":"P", "14":"Q", "15":"R", "16":"S", "17":"T", "18":"U", "19":"V", "1a":"W", "1b":"X", "1c":"Y", "1d":"Z","1e":"!", "1f":"@", "20":"#", "21":"$", "22":"%", "23":"^","24":"&","25":"*","26":"(","27":")","28":"<RET>","29":"<ESC>","2a":"<DEL>", "2b":"\t","2c":"<SPACE>","2d":"_","2e":"+","2f":"{","30":"}","31":"|","32":"<NON>","33":"\"","34":":","35":"<GA>","36":"<","37":">","38":"?","39":"<CAP>","3a":"<F1>","3b":"<F2>", "3c":"<F3>","3d":"<F4>","3e":"<F5>","3f":"<F6>","40":"<F7>","41":"<F8>","42":"<F9>","43":"<F10>","44":"<F11>","45":"<F12>"}
def main():
# check argv
if len(sys.argv) != 2:
print("Usage : ")
print(" python UsbKeyboardHacker.py data.pcap")
print("Tips : ")
print(" To use this python script , you must install the tshark first.")
print(" You can use `sudo apt-get install tshark` to install it")
print("Author : ")
print(" WangYihang <[email protected]>")
print(" If you have any questions , please contact me by email.")
print(" Thank you for using.")
exit(1)
# get argv
pcapFilePath = sys.argv[1]
# get data of pcap
os.system("tshark -r %s -T fields -e usb.capdata 'usb.data_len == 8' > %s" % (pcapFilePath, DataFileName))
# read data
with open(DataFileName, "r") as f:
for line in f:
presses.append(line[0:-1])
# handle
result = ""
for press in presses:
if press == '':
continue
if ':' in press:
Bytes = press.split(":")
else:
Bytes = [press[i:i+2] for i in range(0, len(press), 2)]
if Bytes[0] == "00":
if Bytes[2] != "00" and normalKeys.get(Bytes[2]):
result += normalKeys[Bytes[2]]
elif int(Bytes[0],16) & 0b10 or int(Bytes[0],16) & 0b100000: # shift key is pressed.
if Bytes[2] != "00" and normalKeys.get(Bytes[2]):
result += shiftKeys[Bytes[2]]
else:
print("[-] Unknow Key : %s" % (Bytes[0]))
print("[+] Found : %s" % (result))
# clean the temp data
os.system("rm ./%s" % (DataFileName))
if __name__ == "__main__":
main()
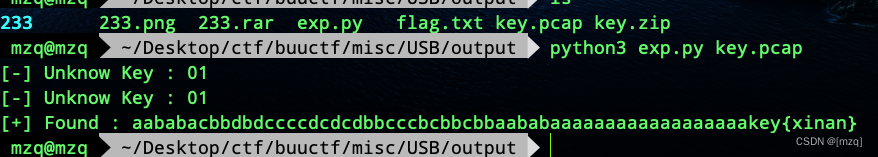
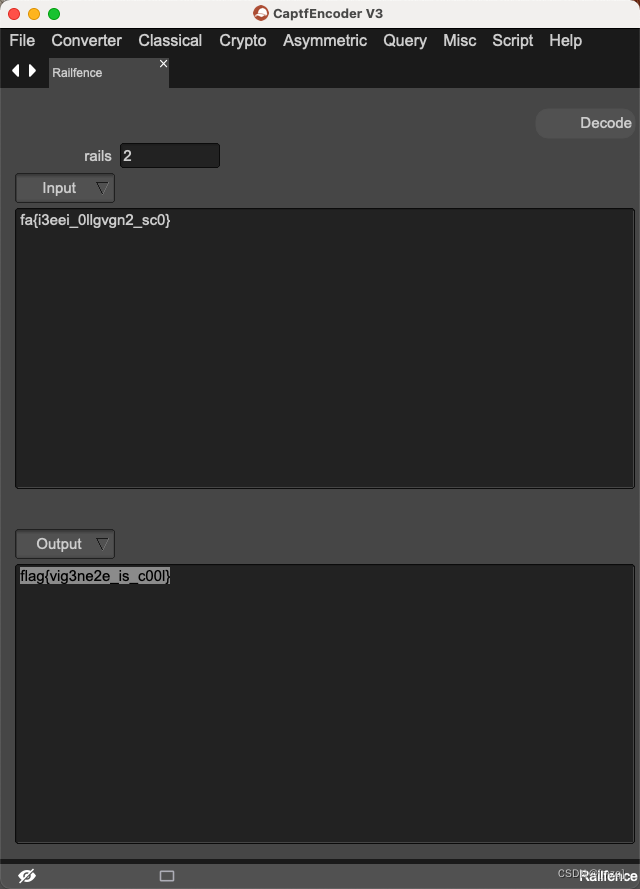
String obtained with QR code , Conduct
Vigeneredecode ,key yesxinan
Vigenere : https://atomcated.github.io/Vigenere/
Then proceed Railfence Decrypt The number of columns is 2
边栏推荐
- Mysql高低版本切换需要修改的配置5-8(此处以aicode为例)
- Technology cloud report: from robot to Cobot, human-computer integration is creating an era
- 通信设备商,到底有哪些岗位?
- 面试结束后,被面试官在朋友圈吐槽了......
- Leetcode-206. Reverse Linked List
- [Linux] process control and parent-child processes
- After the interview, the interviewer roast in the circle of friends
- Gslx680 touch screen driver source code analysis (gslx680. C)
- 二、并发、测试笔记 青训营笔记
- 按键精灵脚本学习-关于天猫抢红包
猜你喜欢
二、并发、测试笔记 青训营笔记
After the interview, the interviewer roast in the circle of friends
English translation is too difficult? I wrote two translation scripts with crawler in a rage
外包干了四年,废了...

2、 Concurrent and test notes youth training camp notes
3、 High quality programming and performance tuning practical youth training camp notes
![[semantic segmentation] - multi-scale attention](/img/2d/652681c08e484fe232b8fb91b7194e.jpg)
[semantic segmentation] - multi-scale attention
图解GPT3的工作原理
resource 创建包方式
【数学笔记】弧度
随机推荐
nacos
numpy中dot函数使用与解析
面试结束后,被面试官在朋友圈吐槽了......
[GUET-CTF2019]虚假的压缩包
vus. Precautions for SSR requesting data in asyndata function
Write CPU yourself -- Chapter 9 -- learning notes
Example of Pushlet using handle of Pushlet
Outsourcing for four years, abandoned
3、 High quality programming and performance tuning practical youth training camp notes
07_ Handout on the essence and practical skills of text measurement and geometric transformation
L'externalisation a duré trois ans.
Wechat applet full stack development practice Chapter 3 Introduction and use of APIs commonly used in wechat applet development -- 3.9 introduction to network interface (IX) extending the request3 met
我理想的软件测试人员发展状态
Advanced practice of C language (high level) pointer
抽丝剥茧C语言(高阶)数据的储存+练习
JSON introduction and JS parsing JSON
【p2p】本地抓包
四、高性能 Go 语言发行版优化与落地实践 青训营笔记
IPv4 exercises
Live online system source code, using valueanimator to achieve view zoom in and out animation effect