当前位置:网站首页>Rockchip3399 start auto load driver
Rockchip3399 start auto load driver
2022-07-03 01:45:00 【mayday_ eighty】
It was previously verified on the development board of Jiuding
Find the relevant configuration file .mk ( If the file system does not support direct copy, use this method )
stay device In the catalog rockchip In the catalog rk3399 Of androidproducts.mk Seen inside ( Mongolia ) **
** This mk It includes the following mk
Open one of them mk Look dimly 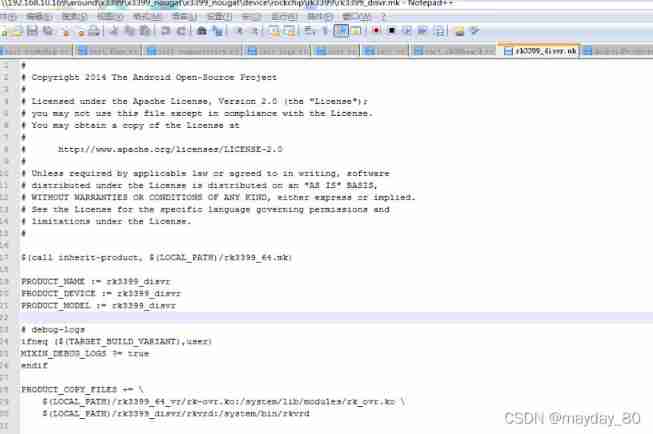
It's about ko How to package files filesystem in Write a reference to yourself mk Or in the existing mk Add modification above ( It's all up to Mongolia )
And then in init.xx.rc or init.rc Write in file insmod
边栏推荐
- Why is it not recommended to use BeanUtils in production?
- 网络安全-浅谈安全威胁
- [understanding of opportunity -36]: Guiguzi - flying clamp chapter - prevention against killing and bait
- JUC thread scheduling
- C#应用程序界面开发基础——窗体控制(3)——文件类控件
- Network security - scan
- Mathematical knowledge: step Nim game game game theory
- Why can't the start method be called repeatedly? But the run method can?
- 海量数据冷热分离方案与实践
- PS去除水印详解
猜你喜欢
Smart management of Green Cities: Digital twin underground integrated pipe gallery platform
网络安全-漏洞与木马
![[data mining] task 6: DBSCAN clustering](/img/af/ad7aa523b09884eee967c6773a613f.png)
[data mining] task 6: DBSCAN clustering
查询商品案例-页面渲染数据
C#应用程序界面开发基础——窗体控制(3)——文件类控件

leetcode刷题_两数之和 II - 输入有序数组

Sweet talk generator, regular greeting email machine... Open source programmers pay too much for this Valentine's day

View of MySQL

STM32 - vibration sensor control relay on
Installation and use of serial port packet capturing / cutting tool
随机推荐
[North Asia data recovery] data recovery case of raid crash caused by hard disk disconnection during data synchronization of hot spare disk of RAID5 disk array
C#应用程序界面开发基础——窗体控制(1)——Form窗体
[shutter] animation animation (animatedbuilder animation use process | create animation controller | create animation | create components for animation | associate animation with components | animatio
STM32 - introduction of external interrupts exti and NVIC
Some functions of applet development
电信客户流失预测挑战赛
C language course information management system
C#应用程序界面开发基础——窗体控制(2)——MDI窗体
Network security - phishing
Uniapp component -uni notice bar notice bar
Using tensorboard to visualize the model, data and training process
How is the mask effect achieved in the LPL ban/pick selection stage?
A simple tool for analyzing fgui dependencies
JUC thread scheduling
Smart management of Green Cities: Digital twin underground integrated pipe gallery platform
【数据挖掘】任务3:决策树分类
Network security - cracking system passwords
Using tensorboard to visualize the model, data and training process
[技术发展-23]:DSP在未来融合网络中的应用
网络安全-最简单的病毒