当前位置:网站首页>Information collection of penetration test
Information collection of penetration test
2022-07-05 15:37:00 【GALi_ two hundred and thirty-three】
information gathering
Domain information collection
whois Inquire about
whois Is a standard Internet Protocol , It can be used to collect network registration information , Registered domain name ,IP Address, etc .
kali Under the whois Inquire about
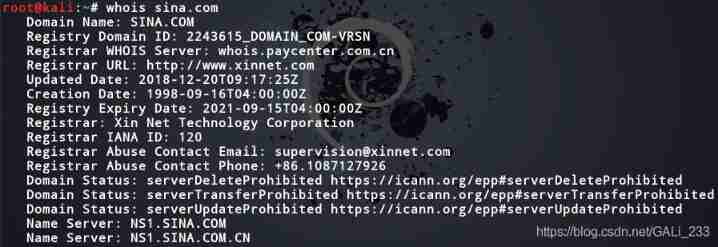
online whois Inquire about
- Love station network https://whois.aizhan.com/
- Home of stationmaster https://whois.chinaz.com/
Record information inquiry
Website filing is the filing that the owner of the website needs to apply to the relevant national departments according to national laws and regulations ,
Check the inner eye https://www.tianyancha.com/
ICP Record query http://www.beianbeian.com/
Home of stationmaster http://icp.chinaz.com/sina.com
Subdomain information collection
subdomain , That is, the secondary domain name , It is the domain name under the top-level domain name . The website is large , You can start with the sub station .
layer Subdomain excavator violence enumeration
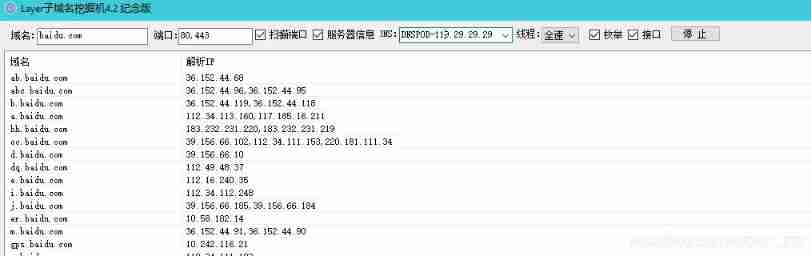
Online tools
Home of stationmaster http://tool.chinaz.com/subdomain/
Certificate transparency public log enumeration
Certificate transparency (Certificate Transparnecy , CT) It's a certificate authority (CA) A project for , The certificate authority will SSL/TLS Publish the certificate to the public log . One SSL/TLS Certificates usually contain domain names 、 Subdomain name and email address .
crt.sh https://crt.sh/
censys https://censys.io/
Search engine enumeration
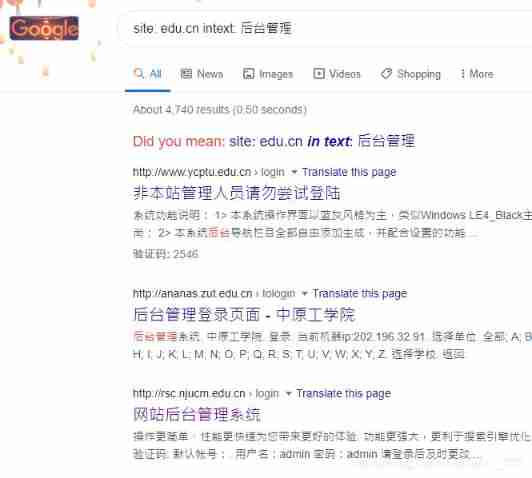
utilize google Search search sites under specific domain names
“site: baidu.com”
Sensitive information collection
Google Haking
Common grammar
| keyword | explain |
|---|---|
| Site | Specify domain name |
| Inurl | URL Keywords existing in |
| Intext | Keywords in the body of a web page |
| Filetype | Specify file type |
| Intitle | Keywords in the page title |
| Link | link:baidu.com That is, return and baidu.com Made a link URL |
| Info | Find some basic information about the designated site |
| cache | Search for Google About caching some content in |
Such as searching the background management page
Port information collection
Port information collection is a very important process , The corresponding service can be identified by scanning the open port of the server , Then look for attack methods for services .
Commonly used tools Nmap, Massan, Royal sword high speed TCP Port scanning tools, etc .
Common ports and descriptions
File sharing service port
| Port number | Port specification | Direction of attack |
|---|---|---|
| 21/22/69 | FTP/TFTP File transfer protocol | Allow anonymous Uploads 、 download 、 Blasting and sniffing operations |
| 2049 | Nfs service | Improper configuration |
| 139 | Samba service | Blast 、 Unauthorized access 、 Remote code execution |
| 389 | Ldap Directory Access Protocol | Inject 、 Allow anonymous access 、 Weak password |
Remote connection service port
| Port number | Port specification | Direction of attack |
|---|---|---|
| 22 | SSH Remote connection | Blast 、SSH Tunnel and Intranet agent forwarding 、 File transfer |
| 23 | Telnet Remote connection | Blast 、 Sniffing 、 Weak password |
| 3389 | Rdp Remote Desktop Connection | Shift back door ( need Window Server 2003 The following systems )、 Blast |
| 5900 | VNC | Weak password burst |
| 5632 | PyAnywhere service | Grab the code 、 Code execution |
Web Application service port
| Port number | Port specification | Direction of attack |
|---|---|---|
| 80/443/8080 | common Web Service port | Web attack 、 Blast 、 Corresponding server version vulnerability |
| 7001/7002 | WebLogic Console | Java Deserialization 、 Weak password |
| 8080/8089 | Jboss/Resin/Jetty/Jenkins | Deserialization 、 Console weak password |
| 9090 | WebSphere Console | Java Deserialization 、 Weak password |
| 4848 | GlassFish Console | Weak password |
| 1352 | Lotus domino The mail service | Weak password 、 Information leakage 、 Blast |
| 10000 | Webmin-Web Control panel | Weak password |
Database service port
| Port number | Port specification | Direction of attack |
|---|---|---|
| 3306 | MySQL | Inject 、 Raise the right 、 Blast |
| 1433 | MSSQL database | Inject 、 Raise the right 、SA Weak password 、 Blast |
| 1521 | Oracle database | TNS Blast 、 Inject 、 rebound shell |
| 5432 | PostgreSQL database | Blast 、 Inject 、 Weak password |
| 27017/27018 | MongoDB | Blast 、 Unauthorized access |
| 6379 | Redis database | Unauthorized access can be attempted 、 Weak password burst |
| 5000 | SysBase/DB2 database | Blast 、 Inject |
Mail service port
| Port number | Port specification | Direction of attack |
|---|---|---|
| 25 | SMTP The mail service | Mail forgery |
| 110 | POP3 agreement | Blast 、 Sniffing |
| 143 | IMAP agreement | Blast |
Network common protocol port
| Port number | Port specification | Direction of attack |
|---|---|---|
| 53 | DNS The domain name system | Allow zone transfer 、DNS hijacked 、 Cache poisoning 、 cheating |
| 67/68 | DHCP service | hijacked 、 cheating |
| 161 | SNMP agreement | Blast 、 Collect target intranet information |
Special service port
| Port number | Port specification | Direction of attack |
|---|---|---|
| 2181 | Zookeeper service | Unauthorized access |
| 8069 | Zabbix service | Remote execution 、SQL Inject |
| 9200/9300 | Elasticsearch service | Remote execution |
| 11211 | Memcache service | Remote execution |
| 512/513/514 | Linux Rexec service | Blast 、Rlogin Sign in |
| 873 | Rsync service | Anonymous access 、 Upload files |
| 3690 | Svn service | Svn leak 、 Unauthorized access |
| 50000 | SAP Management Console | Remote execution |
fingerprint identification
Don't use fingerprints here to refer to websites CMS The fingerprint , Computer operating system or web The fingerprint of the container , These fingerprints are actually some feature codes or keywords , Such as WordPress in robots.txt Will contain wp-admin, index.php Will contain generator-wordpress 3.xx etc. . Identify the system used by the target , In order to find the vulnerability of the corresponding version to attack .
CMS(Content Managerment System), Content management system , It's a kind of being in WEB front end (Web The server ) And back office systems or processes ( Content creation 、 edit ) Between the software systems . The creator of the content 、 Editors 、 Publishers use the content management system to submit 、 modify 、 The examination and approval 、 Publish content . I mean “ Content ” May include documents 、 form 、 picture 、 Data in the database or even videos and everything you want to publish to Internet、Intranet as well as Extranet Website information .
common CMS:
- Enterprise station building system :MetInfo( Mito )、 Cicada knowledge 、SiteServer CMS(.net platform ) etc. ;
2.B2C Mall system : Business school shopex、ecshop、hishop、xpshop etc. ;
3. Portal station building system :DedeCMS( DedeCms ,PHP+MYSQL)、 The empire CMS(PHP+mysql)、PHPCMS、 Move easily 、cmstop,dianCMS( Change point CMS,.net platform ) etc. ;
4. The blog system :wordpress、Z-Blog etc. ;
5. Forum Community :discuz、phpwind、wecenter etc. ;
6. Question answering system :Tipask、whatsns etc. ;
7. Encyclopedia system :HDwiki;
8.B2B Portal system :destoon、B2Bbuilder、 A friendly neighbor B2B etc. ;
9. Talent recruitment website system : The knight CMS、PHP Cloud talent management system ;
10. Real estate website system :FangCms etc. ;
11. Online Education station building system :kesion( Kexun ,ASP)、EduSoho Online school ;
12. Movie website system : Apple cms、ctcms、movcms etc. ;
13. The system of building novel literature station :JIEQI CMS;
Tool recommendation : Mitsurugi Web fingerprint identification , Whatweb
Online fingerprint identification website :
- BugScaner:http://whatweb.bugscaner.com/look/
- The cloud knows the fingerprint :http://www.yunsee.cn/finger.html
- WhatWeb:https://whatweb.net/
real IP
Through domain name resolution , You can get the website IP, But sometimes it can be parsed IP Not the real server address IP. If the goal is done CDN, that The parsing result may be CDN Node IP Address .
CDN The full name is Content Delivery Network, The content distribution network .CDN It is an intelligent virtual network based on the existing network , Rely on edge servers deployed everywhere , Load balancing through the central platform 、 content distribution 、 Scheduling and other functional modules , Let users get the content they need nearby , Reduce network congestion , Improve user access response speed and hit rate .CDN The key technologies are content storage and distribution technology .
For websites , adopt CDN Acceleration can improve the speed of website access , Because this is a technology that distributes website content to different nodes through caching . When the website has CDN After acceleration , It can often be based on the user's request region , Choose a cache server on the network closest to the user , This can provide users with content services faster , It is no different from directly accessing the source site , This way to shorten the distance from the content network , Technology to achieve accelerated effect . Only when the user has actual data interaction, it will be from the remote Web Server response .
Check whether the target uses CDN

Obtained from different regions IP The address is different , Then it is possible to do CDN, It can be detected through online websites
https://www.17ce.com/
Bypass CDN
- Internal mailbox source . Register through website users or RSS Subscription function , Generally, it is not done here cdn
- Scan website test files . Such as phpinfo、test etc.
- Sub station domain name .
- Foreign agent visits .(http://asm.ca.com/en/ping.php)
- Query domain name resolution record .(https://www.netcraft.com)
- APP Grab the bag
- Bypass CloudFlare CDN Find the real IP.(http://www.crimeflare.us/cfs.html#box)
Sensitive directory information collection
Detecting the directory structure and hidden sensitive files of the target site is an essential content . It is possible to get the background page of the website , File upload page , Even the source code of the website .
Most tools are combined with dictionaries to detect
Commonly used tools :DirBuster、 Background scan of Royal sword
Online tools :https://www.webscan.cc/
Reference resources :《Web Safe attack and defense Penetration test practice guide 》
边栏推荐
- The difference between abstract classes and interfaces in PHP (PHP interview theory question)
- P6183 [USACO10MAR] The Rock Game S
- 1330: [example 8.3] minimum steps
- Misc Basic test method and knowledge points of CTF
- Live broadcast preview | how to implement Devops with automatic tools (welfare at the end of the article)
- 美团优选管理层变动:老将刘薇调岗,前阿里高管加盟
- JMeter performance test: serveragent resource monitoring
- Bugku cyberpunk
- 一文搞定vscode编写go程序
- R 熵权法计算权重及综合得分
猜你喜欢

Bugku's Ah Da
I spring and autumn blasting-1
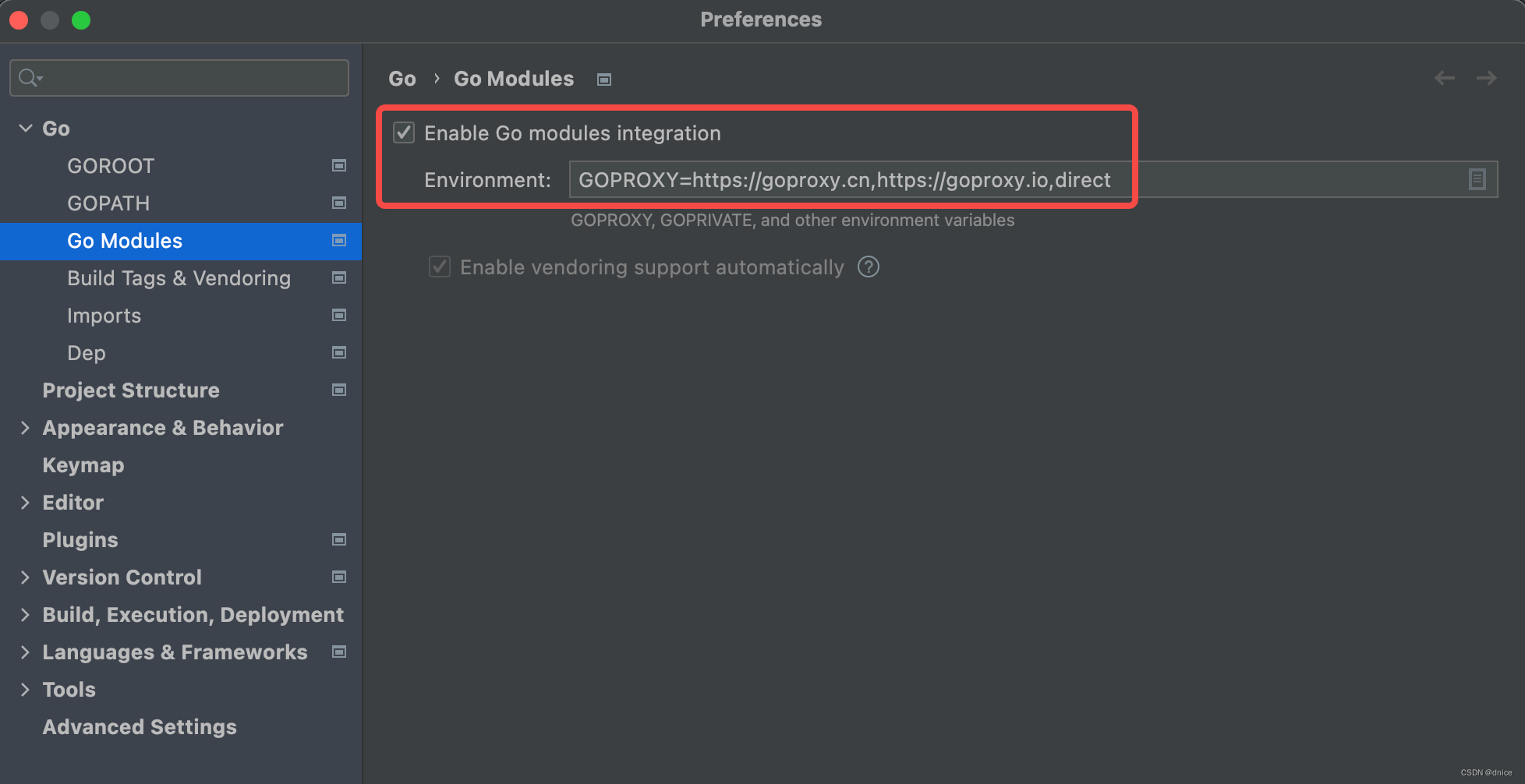
【简记】解决IDE golang 代码飘红报错
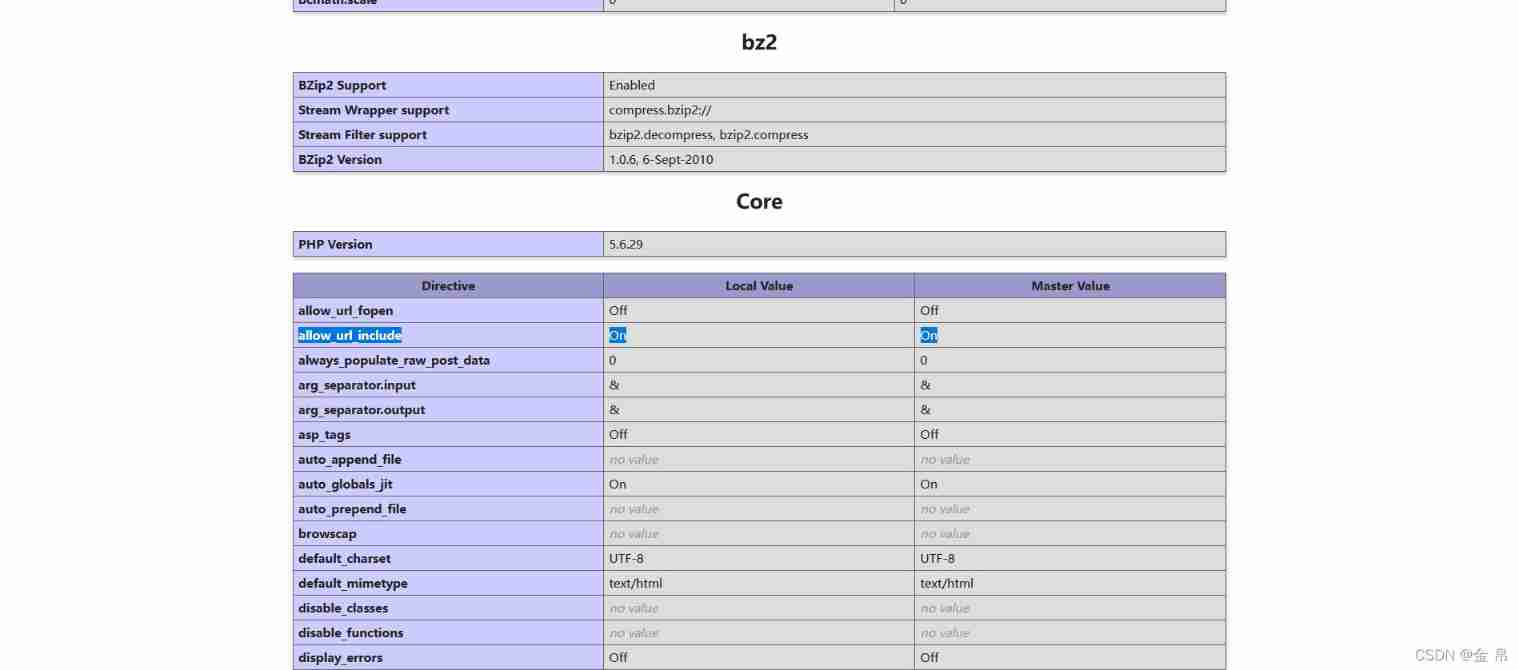
I include of spring and Autumn
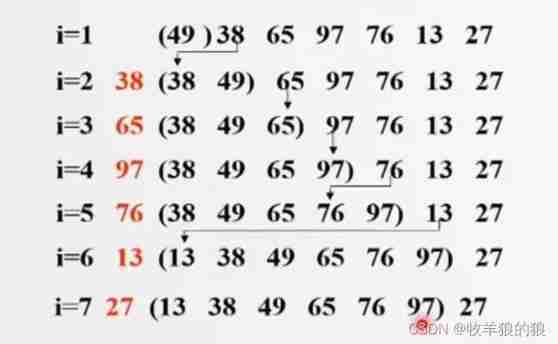
Bubble sort, insert sort
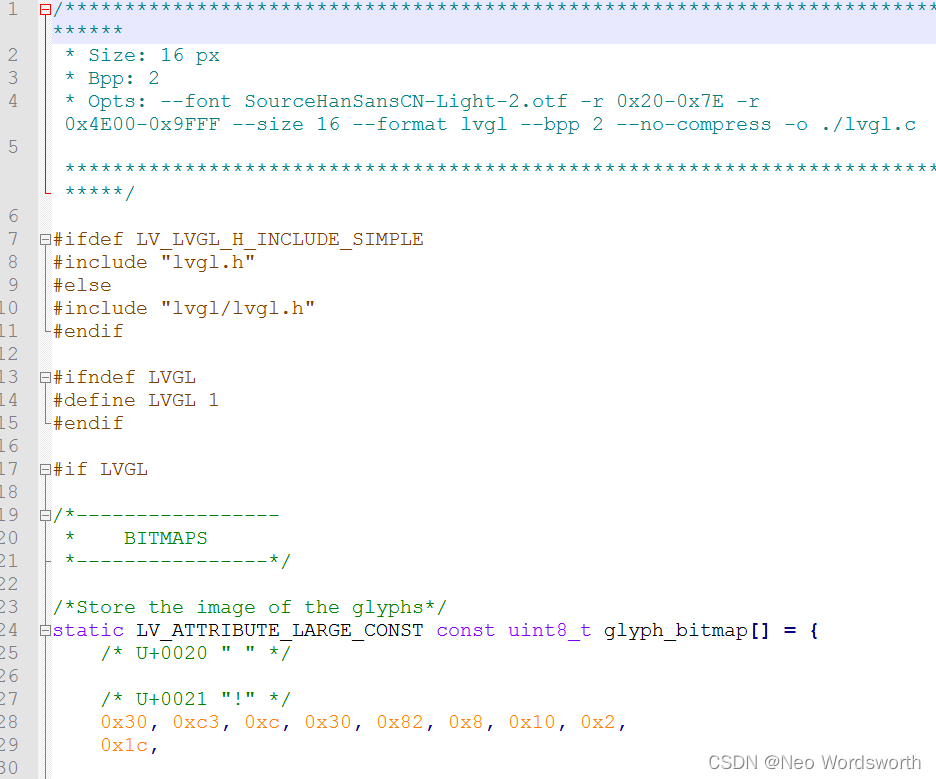
lv_ font_ Conv offline conversion

Huiyuan, 30, is going to have a new owner
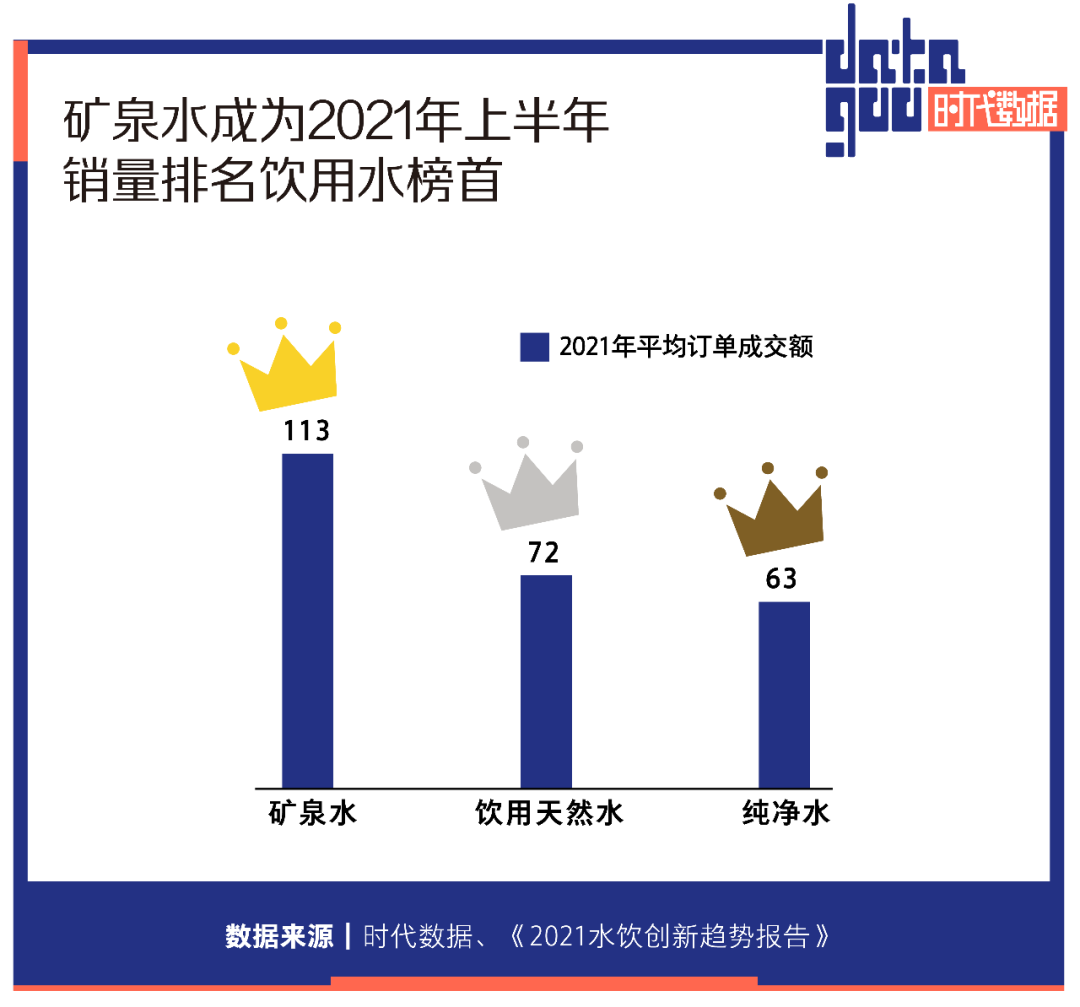
当代人的水焦虑:好水究竟在哪里?
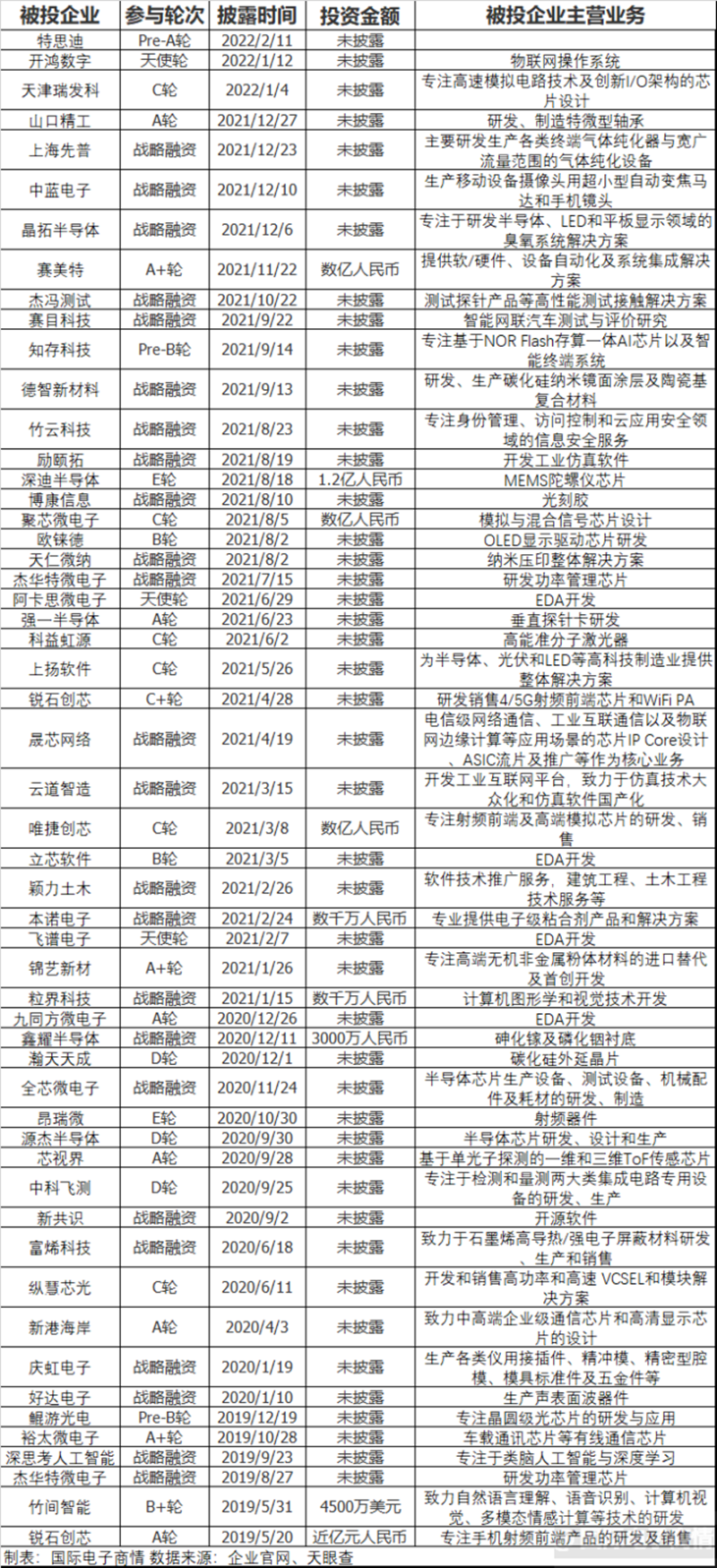
Huawei Hubble incarnation hard technology IPO harvester
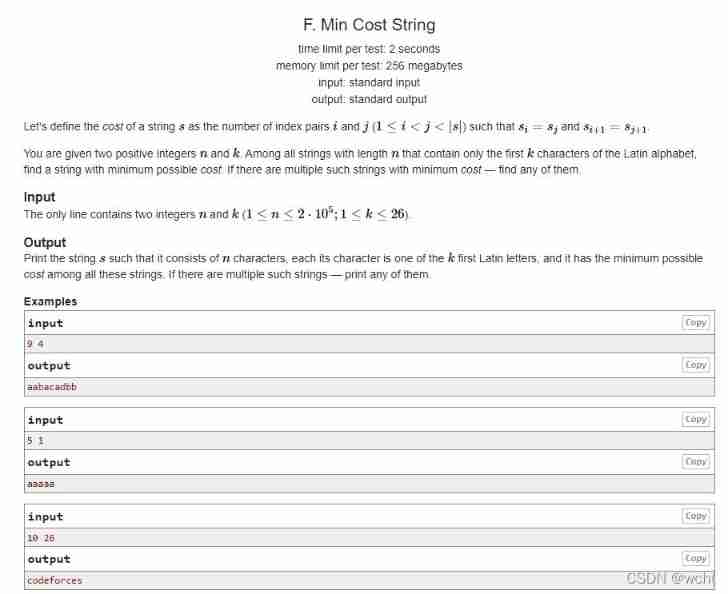
F. Min cost string problem solving Report
随机推荐
【简记】解决IDE golang 代码飘红报错
The elimination strategy of redis
What are CSRF, XSS, SQL injection, DDoS attack and timing attack respectively and how to prevent them (PHP interview theory question)
mapper. Comments in XML files
Ecotone technology has passed ISO27001 and iso21434 safety management system certification
Common PHP interview questions (1) (written PHP interview questions)
Appium automation test foundation - appium basic operation API (II)
RepLKNet:不是大卷积不好,而是卷积不够大,31x31卷积了解一下 | CVPR 2022
Value series solution report
Severlet learning foundation
数学建模之层次分析法(含MATLAB代码)
go学习 ------jwt的相关知识
Common redis data types and application scenarios
Write a go program with vscode in one article
String modification problem solving Report
【簡記】解决IDE golang 代碼飄紅報錯
爱可可AI前沿推介(7.5)
Bugku's eyes are not real
I'm fat, huh
keep-alive