当前位置:网站首页>Deng Junhui's notes on data structure and algorithm learning - Chapter 9
Deng Junhui's notes on data structure and algorithm learning - Chapter 9
2020-11-09 08:20:00 【osc_0m0d4mbq】
List of articles
day58
Chapter nine The dictionary
9. The dictionary
9.b Hash principle
 Hashing- hash
Hashing- hash
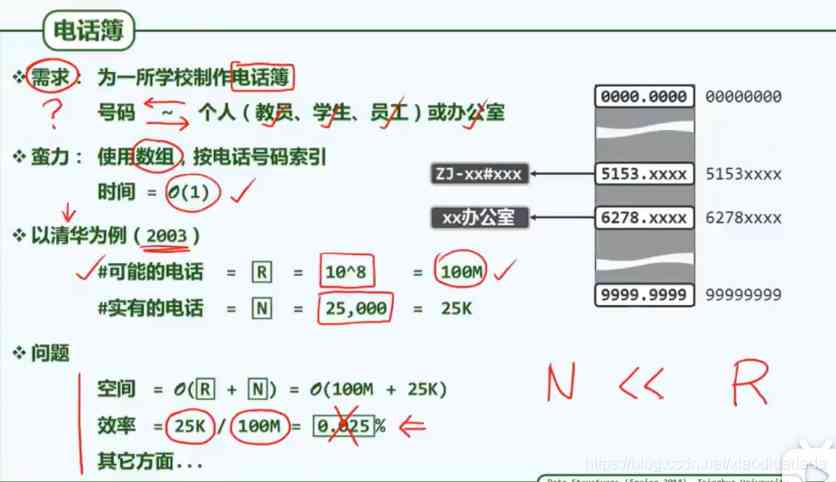 The data comes from a fairly large space , But the actual data to be stored and organized is a very small subset of it , Space efficiency is extremely low
The data comes from a fairly large space , But the actual data to be stored and organized is a very small subset of it , Space efficiency is extremely low
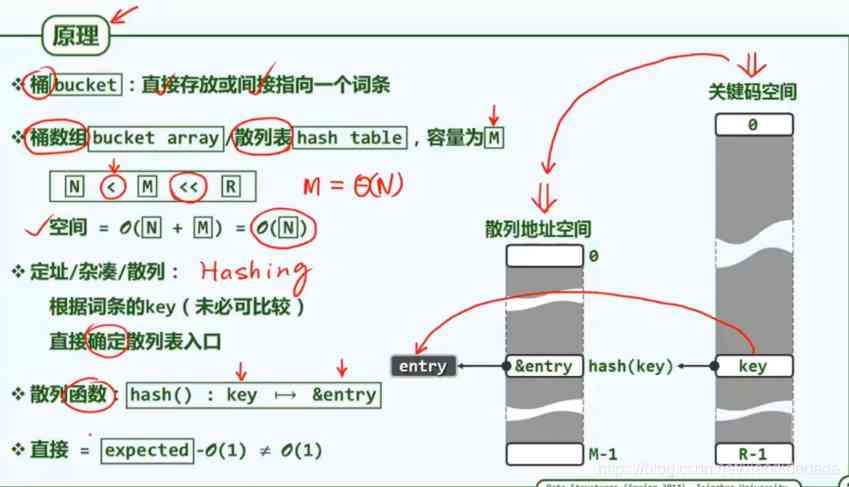 Compress space
Compress space
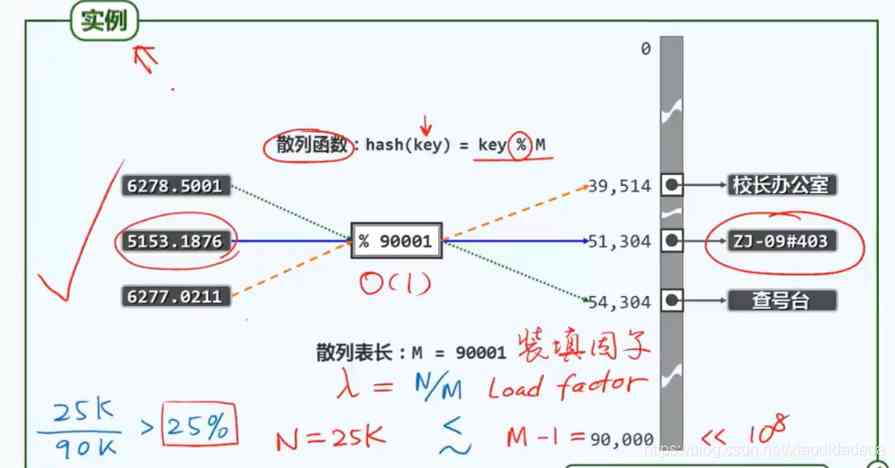
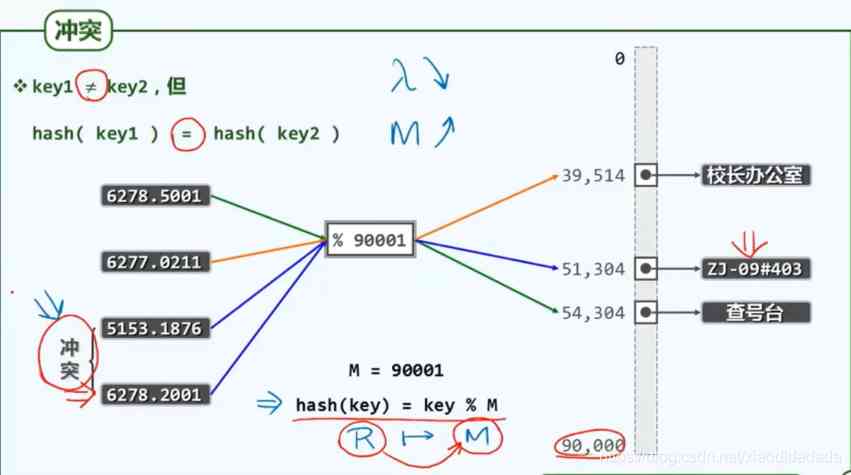 The pigeon nest problem , take x From a larger definition domain , Mapping to a smaller range of values , There are ways to reduce conflict ( Design better hash function or increase hash table length M), But it can't be avoided ( How to solve ?)
The pigeon nest problem , take x From a larger definition domain , Mapping to a smaller range of values , There are ways to reduce conflict ( Design better hash function or increase hash table length M), But it can't be avoided ( How to solve ?)
9.c Hash function
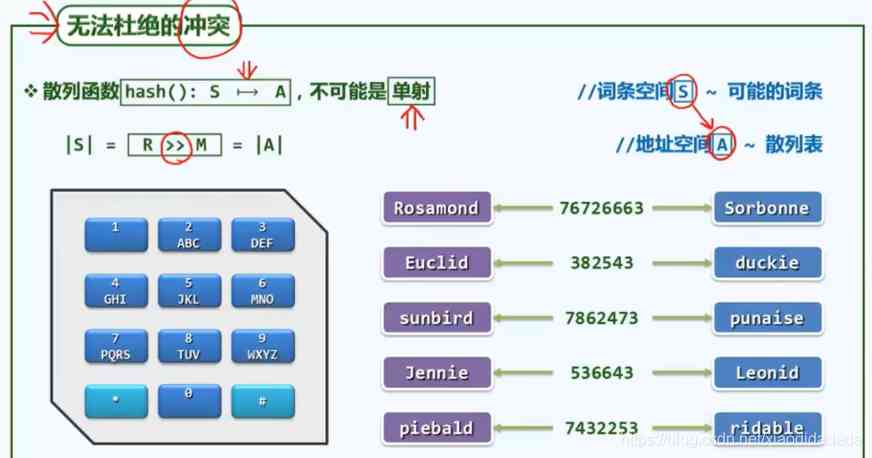
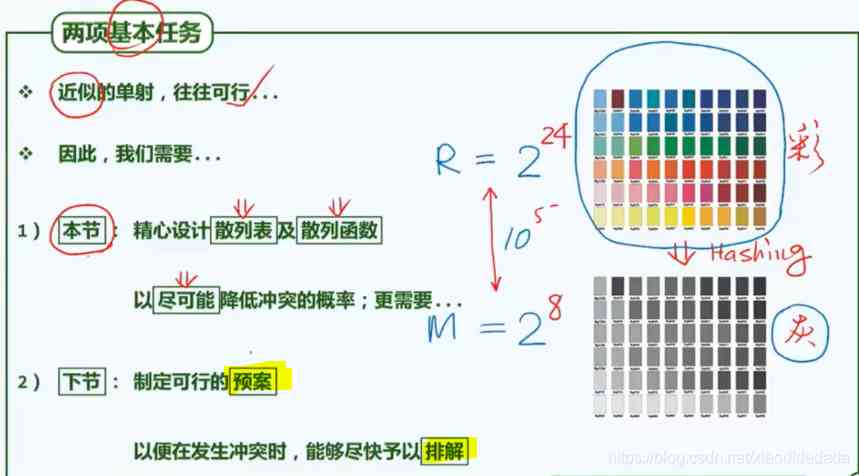
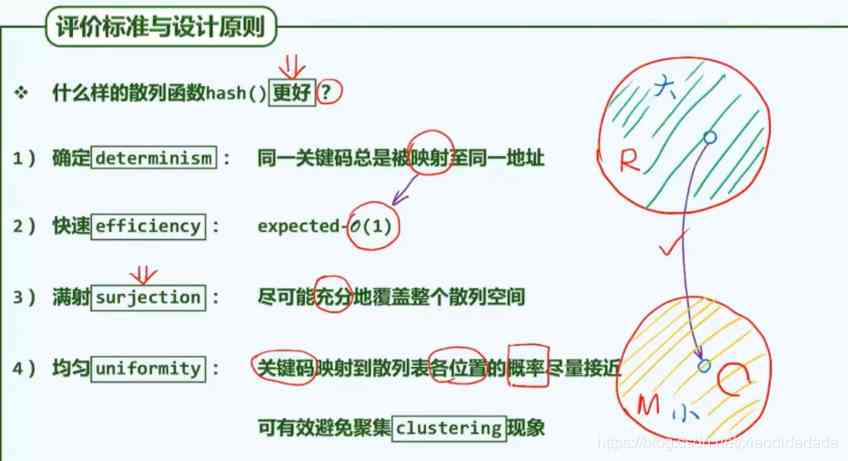
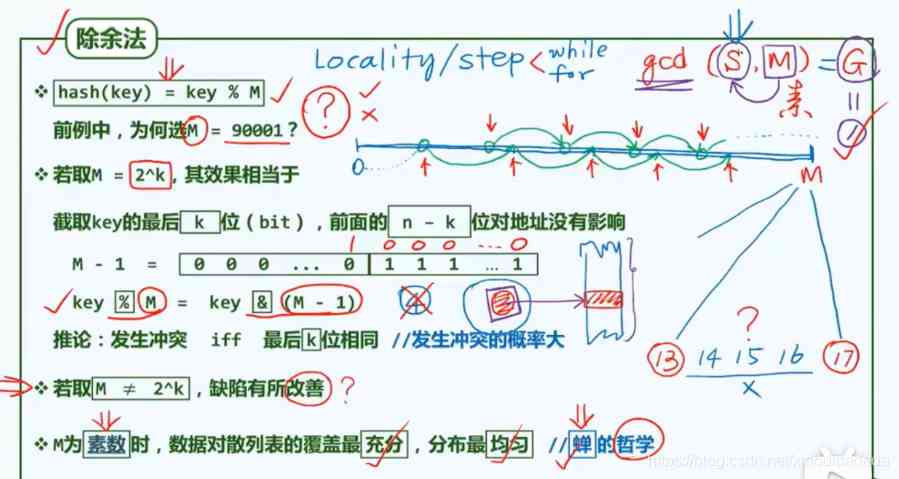 gcd: The greatest common factor is 1
gcd: The greatest common factor is 1
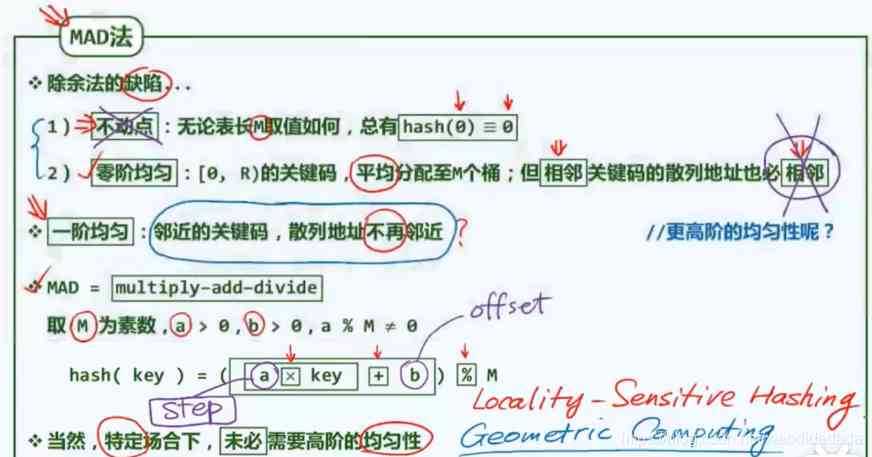
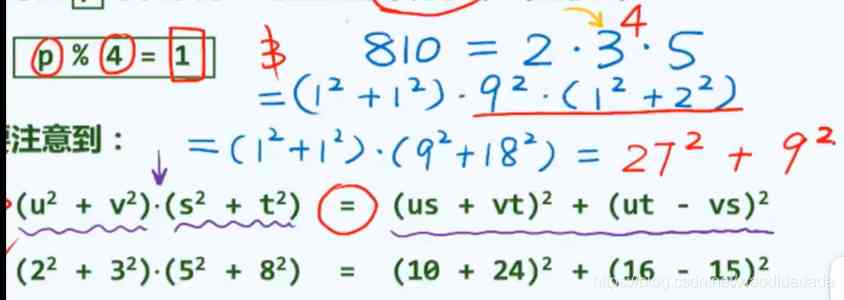
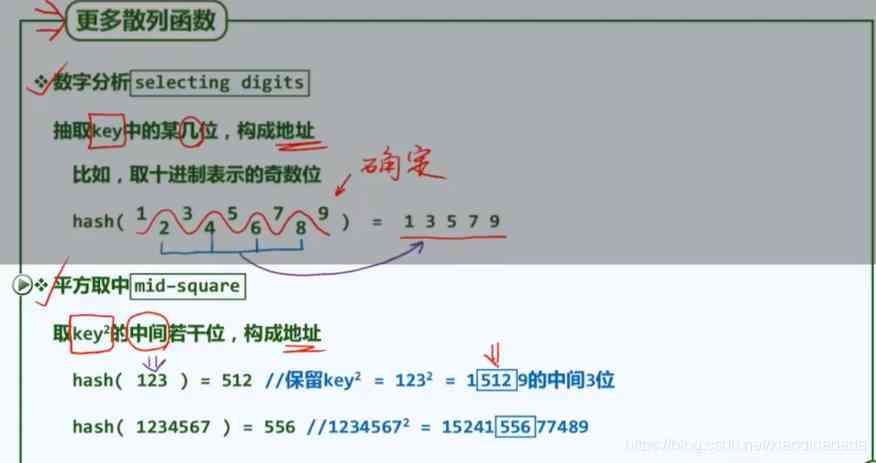 Take the middle bit , It can make the influence of each digit of the original key code closer to each other , Here's the picture , Square operations can be decomposed into addition operations
Take the middle bit , It can make the influence of each digit of the original key code closer to each other , Here's the picture , Square operations can be decomposed into addition operations
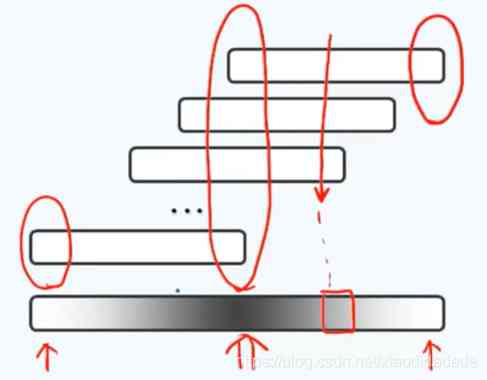
 The more random the hash function is , The more irregular , The better .
The more random the hash function is , The more irregular , The better .

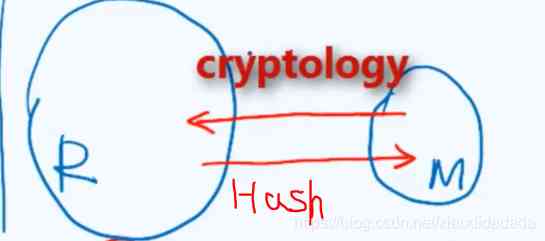
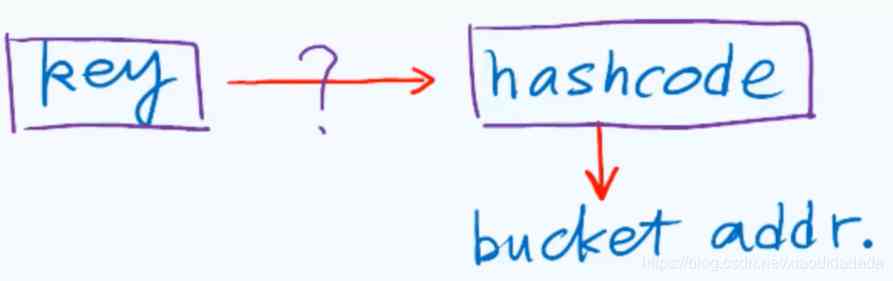
 key It may not be an integer , You need to convert it to hashcode, Do it again. , Here's the picture
key It may not be an integer , You need to convert it to hashcode, Do it again. , Here's the picture
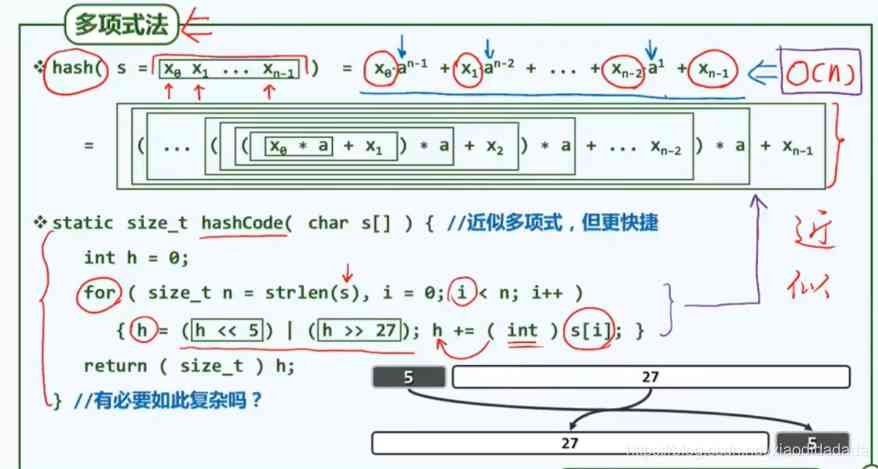 It is necessary to , If you use a simple calculation method , It's easy to have hash conflicts
It is necessary to , If you use a simple calculation method , It's easy to have hash conflicts
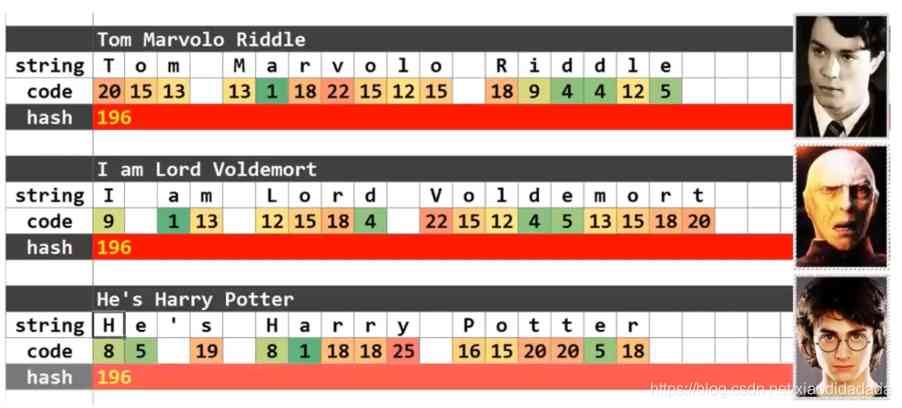
9.d Conflict
9.d1 Hash resolves conflicts 1
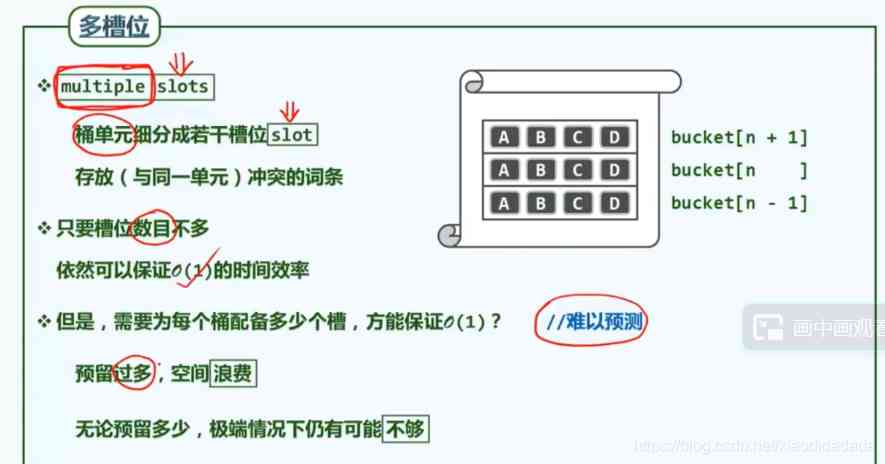
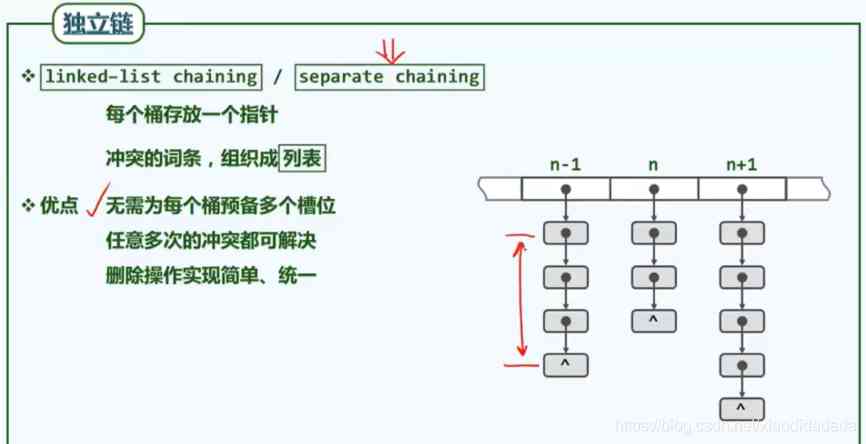
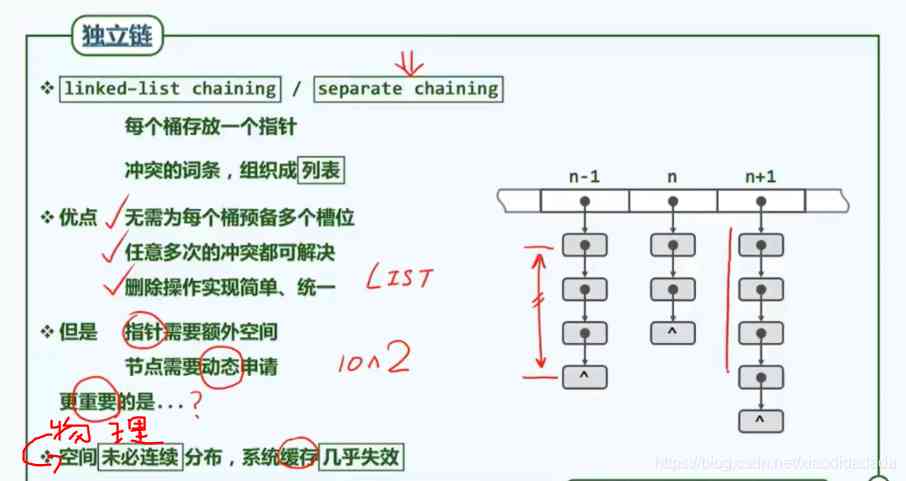
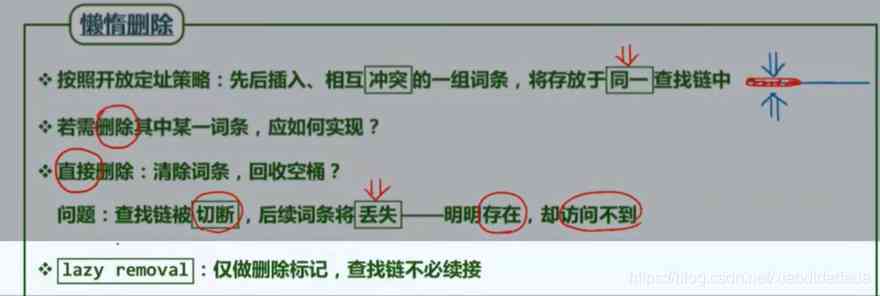
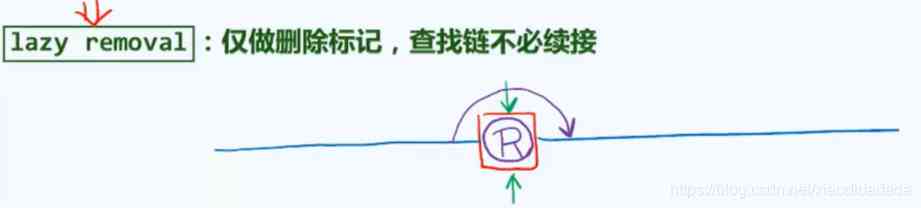 Skip when searching , Insert directly when inserting .
Skip when searching , Insert directly when inserting .
9.d2 Hash resolves conflicts 2
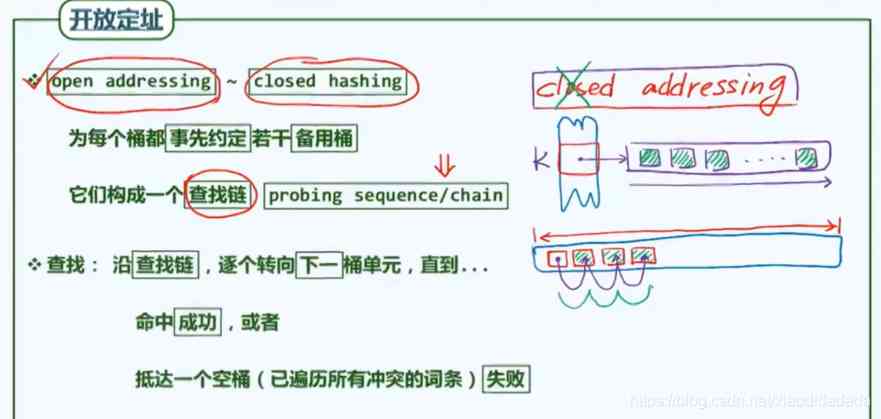
 Closed addressing vs Open addressing
Closed addressing vs Open addressing
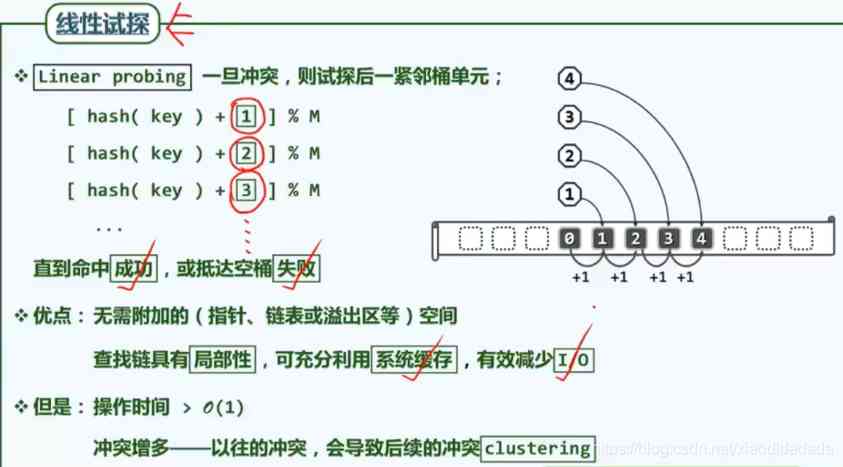
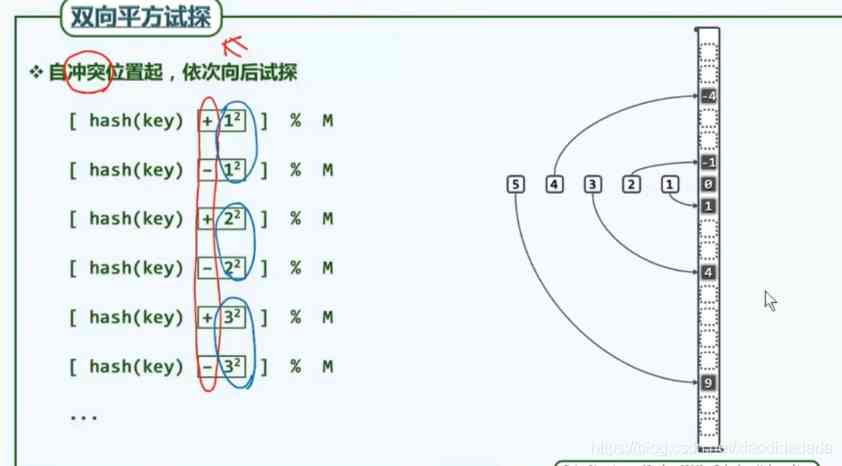
The linear heuristics described above , It's too close to each other , There will be a lot of unnecessary conflicts . You can open the space properly
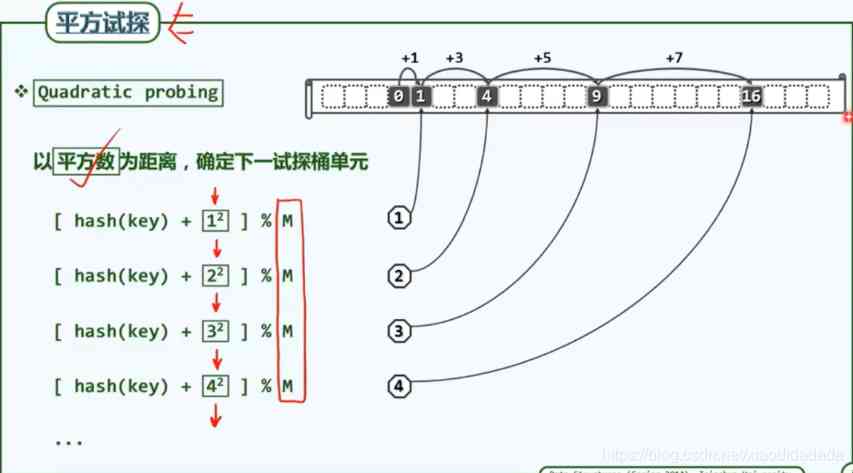
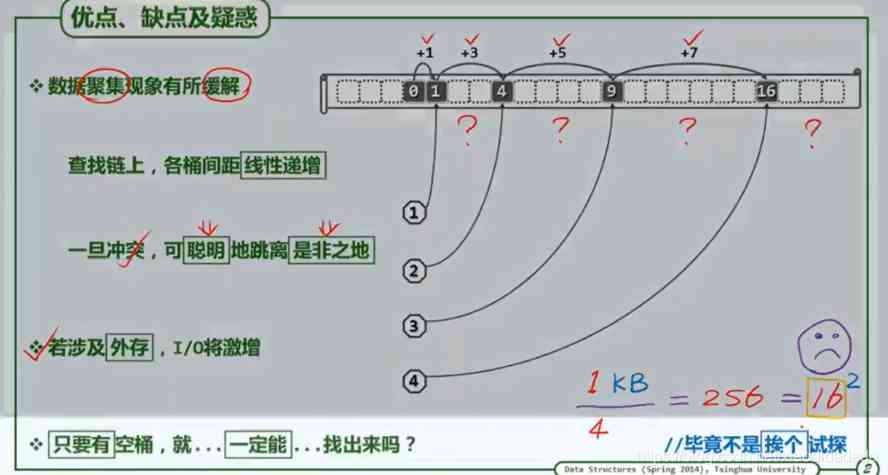 Suppose the size of a cache is 1KB, Only the pointer is stored in the bucket (4 byte ), Well, unless 16 Secondary hash conflict , To make the cache invalid , Need extra I/O.
Suppose the size of a cache is 1KB, Only the pointer is stored in the bucket (4 byte ), Well, unless 16 Secondary hash conflict , To make the cache invalid , Need extra I/O.
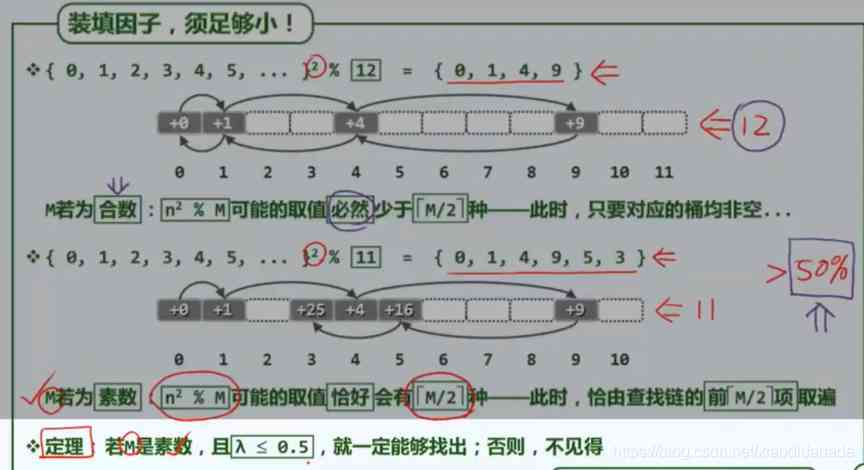
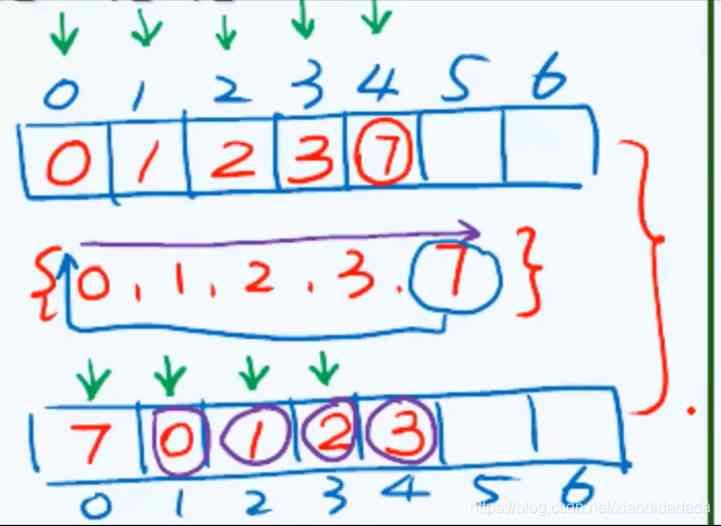
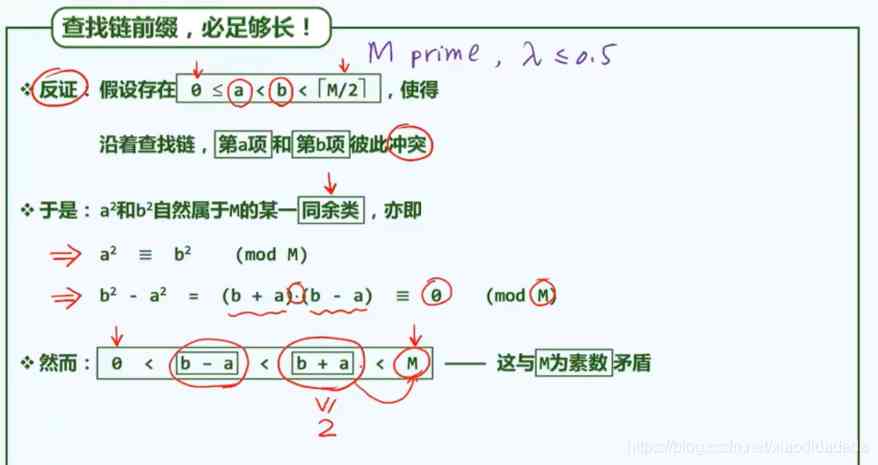 b+a≥2, yes M The nontrivial factor of , This is related to M Contradict prime numbers .
b+a≥2, yes M The nontrivial factor of , This is related to M Contradict prime numbers .
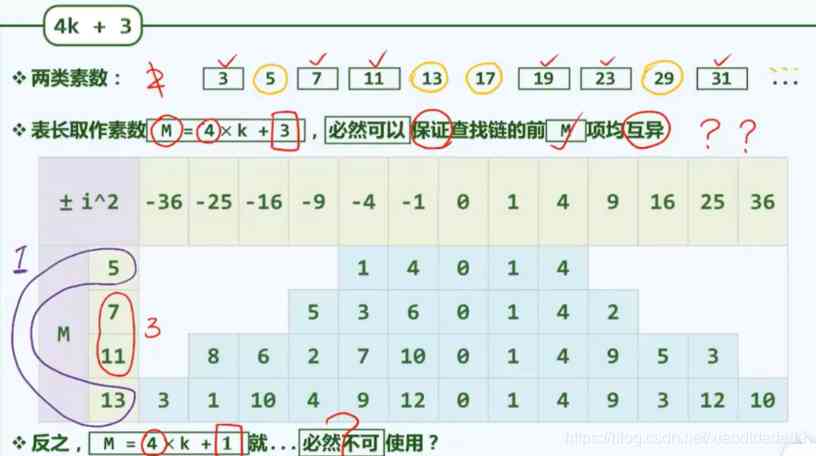
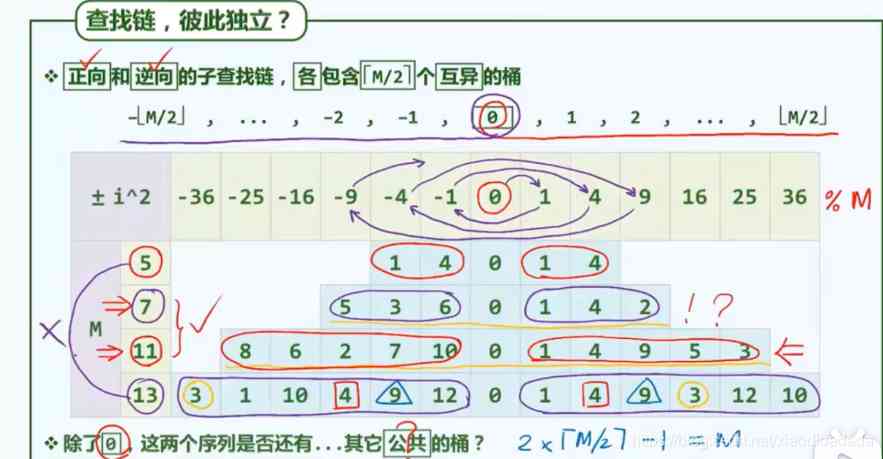 For some primes ( for example 7,11) The long table , The two-way search chain works , Some primes ( for example 5,13) The effect of the surface length is not good .
For some primes ( for example 7,11) The long table , The two-way search chain works , Some primes ( for example 5,13) The effect of the surface length is not good .

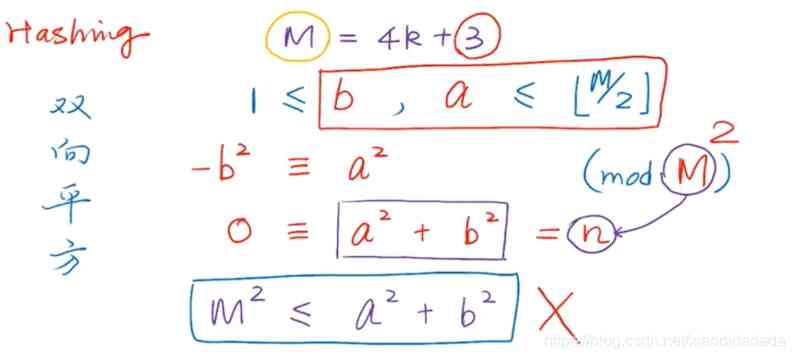
9.e bucket / Count sorting
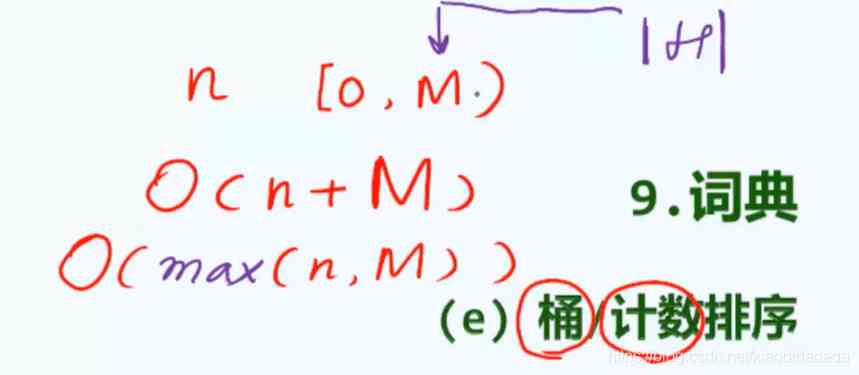 among n Is the number of elements ,[0,M) Is the element range
among n Is the number of elements ,[0,M) Is the element range

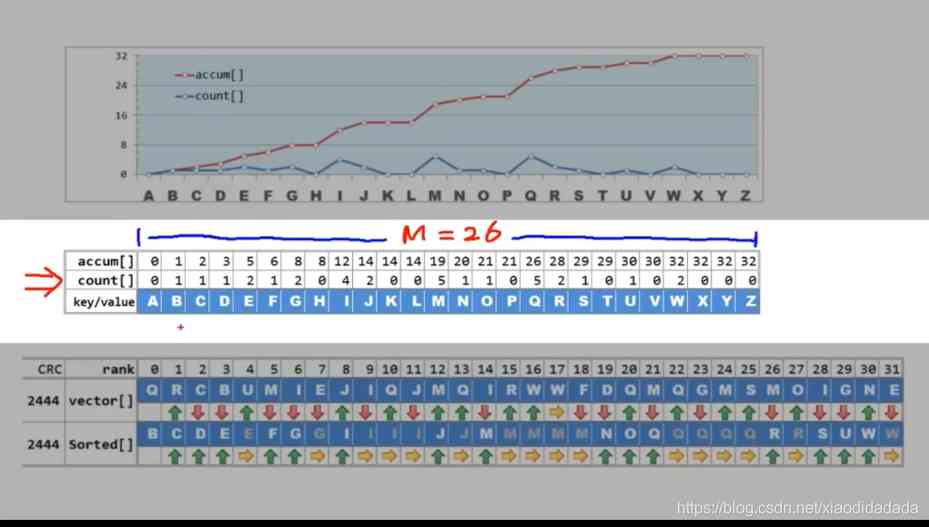
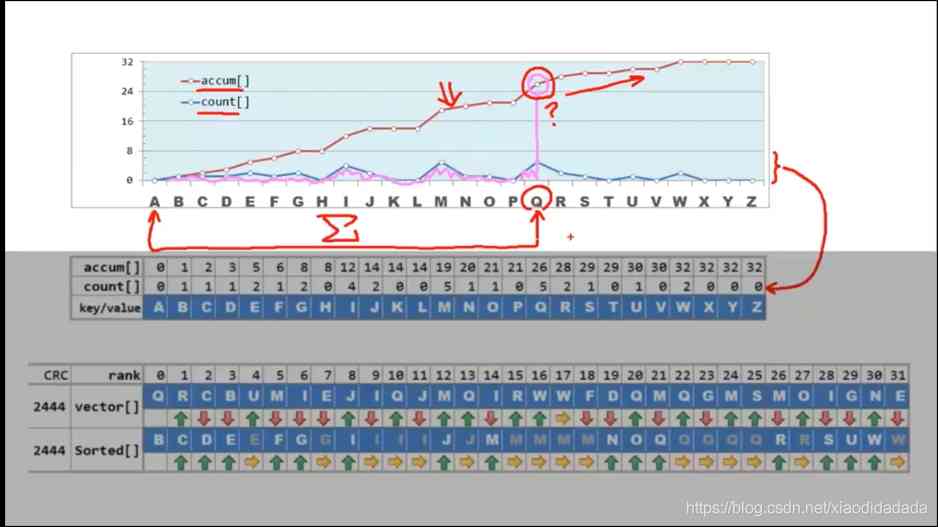 Where the red line is the integral of the blue line
Where the red line is the integral of the blue line
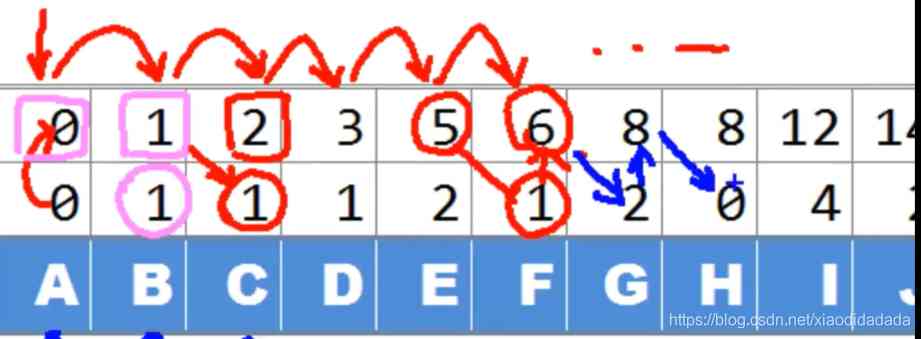 Linear scan over and over again count[], Scan again count[] obtain accum[], You can sort in linear time .
Linear scan over and over again count[], Scan again count[] obtain accum[], You can sort in linear time .
版权声明
本文为[osc_0m0d4mbq]所创,转载请带上原文链接,感谢
边栏推荐
- Operation 2020.11.7-8
- A few lines of code can easily transfer traceid across systems, so you don't have to worry about losing the log!
- LTM understanding and configuration notes
- Several rolling captions based on LabVIEW
- 图节点分类与消息传递 - 知乎
- centos7下安装iperf时出现 make: *** No targets specified and no makefile found. Stop.的解决方案
- WordPress Import 上传的文件尺寸超过php.ini中定义的upload_max_filesize值-->解决方法。
- Have you ever thought about why the transaction and refund have to be split into different tables
- Commodity management system -- the search function of SPU
- 作业2020.11.7-8
猜你喜欢

Several common playing methods of sub database and sub table and how to solve the problem of cross database query

Tips in Android Development: requires permission android.permission write_ Settings solution
理论与实践相结合彻底理解CORS

The file size uploaded by WordPress import exceeds php.ini Upload defined in_ max_ Filesize value -- & gt; solution.

Combine theory with practice to understand CORS thoroughly
结合阿里云 FC 谈谈我对 FaaS 的理解
APP 莫名崩溃,开始以为是 Header 中 name 大小写的锅,最后发现原来是容器的错!

2. Introduction to computer hardware

Exception capture and handling in C + +

Application of cloud gateway equipment on easynts in Xueliang project
随机推荐
2 普通模式
API部分的知识点复习
Concurrent linked queue: a non blocking unbounded thread safe queue
This program cannot be started because msvcp120.dll is missing from your computer. Try to install the program to fix the problem
第五章编程
Three ways to operate tables in Apache iceberg
Finally, the python project is released as exe executable program process
14.Kubenetes简介
六家公司CTO讲述曾经历的“宕机噩梦”
Commodity management system -- the search function of SPU
Introduction to nmon
Factory pattern pattern pattern (simple factory, factory method, abstract factory pattern)
LeetCode-15:三数之和
Five indispensable open source tools for me
基于链表的有界阻塞队列 —— LinkedBlockingQueue
Teacher Liang's small class
Introduction to nmon
The vowels in the inverted string of leetcode
C++之异常捕获和处理
Several common playing methods of sub database and sub table and how to solve the problem of cross database query