当前位置:网站首页>How to adjust bugs in general projects ----- take you through the whole process by hand
How to adjust bugs in general projects ----- take you through the whole process by hand
2022-07-05 05:40:00 【Falling spring is only inadvertently】
transfer bug technological process
- One 、 Run code , Find the error .
- Two 、 Find the error location .
- 3、 ... and 、 If the annotation works normally , Then there is an error in the commented part ( This is the most desired result );
- Four 、 So I thought it should not be the pot here , Then we will main The start of the call in the function .
- 5、 ... and 、 Generally, compilers have , View definition , Jump to the defined function , To a large extent, this allows us to quickly find bug.
- 6、 ... and 、 Similar to method 5 , Find the problem of calling functions in this function , Or the problem of the function itself
- 7、 ... and 、 Last question , Focus on one if In the sentence
- 8、 ... and 、 Because it's a file stream , I'll try if I read something , Or the file did not open successfully ,
- Nine 、 This analysis is over , I hope that helps
The example only tells you how to find bug, Will not be too specific bug The solution of the . because bug Too much , There are many solutions . The most important thing is to find bug.
Let's take a real case to lead you to experience .
One 、 Run code , Find the error .
( In this step , Understand the prompt to report an error , Generally, compilers are more or less , If you don't understand it, you can assign a value and paste it into CSDN Check to see if anyone has the same error report )
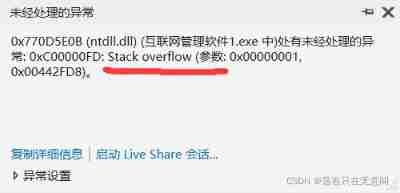
In this error report , I extracted the entry point ,( As shown in the above figure, the part with red lines ).
Two 、 Find the error location .
First, let's see if there are obvious grammatical errors , If you can't see . Try to comment out this part to see if there will be errors ( The key ).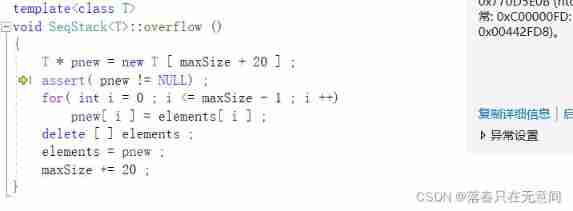
No obvious mistakes were found , So I tried to comment it out , Be careful not to make mistakes when commenting .( That is, comment out the root related to this code , Therefore, it also reflects that we should try to integrate the reused code into a function ).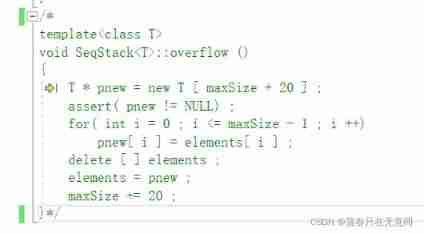
Associated with what it wants 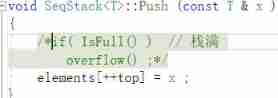
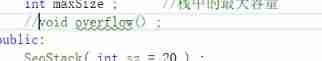
3、 ... and 、 If the annotation works normally , Then there is an error in the commented part ( This is the most desired result );
without , ( Here's the picture , The same mistake , I feel evil ...) So paste the wrong assignment , Search and see 
The search results are as follows , It would be best if we found the same , If not ....( This blogger just doesn't , Dry face )
However, it seems to be mentioned in these similar results new . At first, I thought the template class was written incorrectly ( After all, the template class is difficult for most heroes ). Then the whole header file and the corresponding cpp It's annotated ( Later, I found that this idea was wrong , Don't learn from bloggers )
People are tired of commenting , It's better to sleep for a while and clear your mind . (⊙o⊙)… Get down to business .
Four 、 So I thought it should not be the pot here , Then we will main The start of the call in the function .
First, comment out all , See if there's any more , There is also the compiler problem . Then liberate one by one to find the function in question .
Pictured above , After doing this , Found to be Here's the picture 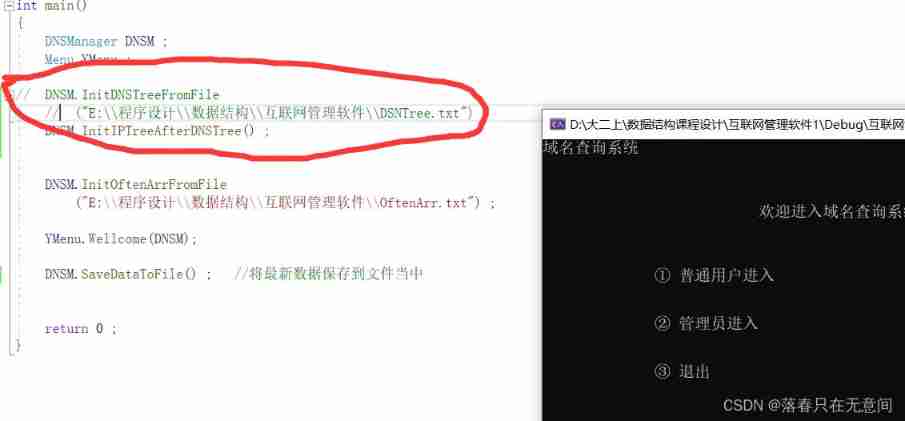
5、 ... and 、 Generally, compilers have , View definition , Jump to the defined function , To a large extent, this allows us to quickly find bug.
( Here's the picture )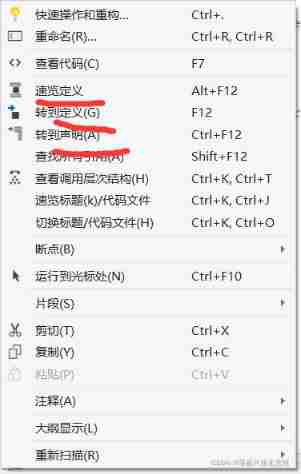
6、 ... and 、 Similar to method 5 , Find the problem of calling functions in this function , Or the problem of the function itself
( Did I mention the called function again here , Therefore, modularization of functions is conducive to our adjustment bug)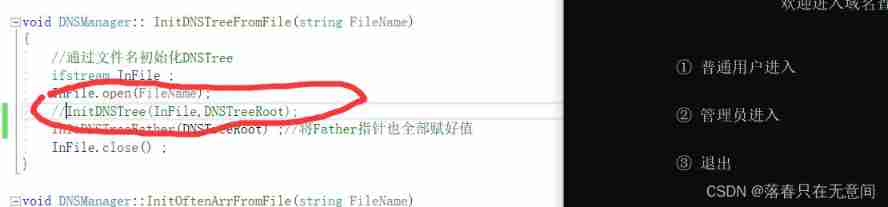
7、 ... and 、 Last question , Focus on one if In the sentence
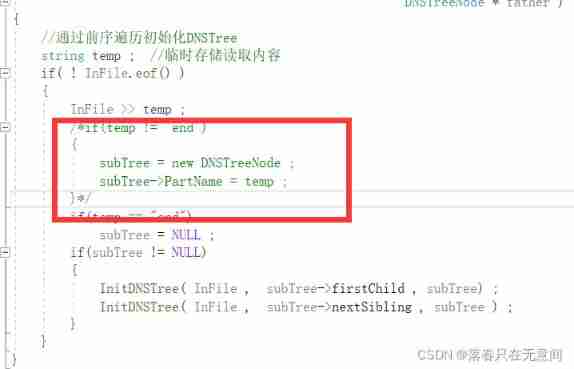
continue 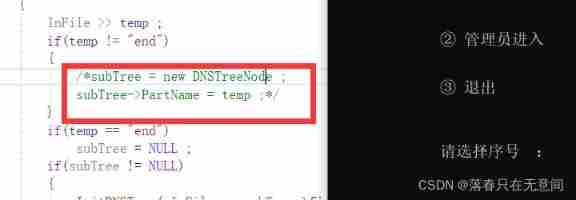
It's inside The problem of two sentences , Then analysis , It is definitely not the fault of the following statement alone , Because if there is no It must be wrong to assign a value when applying for space . And the first sentence has new , Think of the previous search results . I just wonder if new The question of .
First, I tried to become malloc . It turns out , Take a look at this blog and you will know that you can't do this , Also have to new . Why not malloc
After that ? I thought about it , Since it's right to apply for a space , After applying for space , The assignment of the second statement is wrong . assignment ( Is this sentence very simple ...), The operation process of assignment is no problem , that , There is only one truth , That's it Used for assignment temp There is a mistake .( Finally found , That's true )
8、 ... and 、 Because it's a file stream , I'll try if I read something , Or the file did not open successfully ,
Good guy, if you don't try, you don't know. Try and be surprised . It turned out that the file couldn't be opened () I'm impressed . This also tells us that we must add a command to check whether the file has been opened .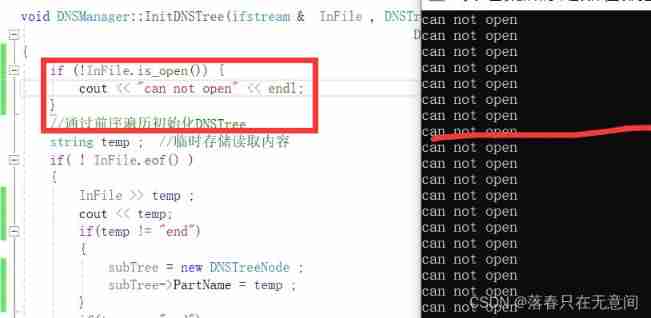
Nine 、 This analysis is over , I hope that helps

边栏推荐
- Implement a fixed capacity stack
- [cloud native] record of feign custom configuration of microservices
- 【云原生】微服务之Feign自定义配置的记录
- 【实战技能】如何做好技术培训?
- Analysis of backdoor vulnerability in remote code execution penetration test / / phpstudy of national game title of national secondary vocational network security B module
- Drawing dynamic 3D circle with pure C language
- 使用Electron开发桌面应用
- Daily question - longest substring without repeated characters
- Yolov5 adds attention mechanism
- Individual game 12
猜你喜欢

CCPC Weihai 2021m eight hundred and ten thousand nine hundred and seventy-five
Talking about JVM (frequent interview)
YOLOv5-Shufflenetv2
利用HashMap实现简单缓存
Pointnet++ learning
用STM32点个灯
剑指 Offer 05. 替换空格

Personal developed penetration testing tool Satania v1.2 update
Remote upgrade afraid of cutting beard? Explain FOTA safety upgrade in detail
Graduation project of game mall
随机推荐
第六章 数据流建模—课后习题
Brief introduction to tcp/ip protocol stack
2020ccpc Qinhuangdao J - Kingdom's power
Sword finger offer 58 - ii Rotate string left
Simple knapsack, queue and stack with deque
Warning using room database: schema export directory is not provided to the annotation processor so we cannot export
Improvement of pointnet++
全排列的代码 (递归写法)
Acwing 4300. Two operations
26、 File system API (device sharing between applications; directory and file API)
Personal developed penetration testing tool Satania v1.2 update
lxml. etree. XMLSyntaxError: Opening and ending tag mismatch: meta line 6 and head, line 8, column 8
读者写者模型
智慧工地“水电能耗在线监测系统”
软件测试 -- 0 序
个人开发的渗透测试工具Satania v1.2更新
Maximum number of "balloons"
Pointnet++学习
A misunderstanding about the console window
CF1637E Best Pair