当前位置:网站首页>Database postragesq role membership
Database postragesq role membership
2022-07-05 01:13:00 【wx5d0241bb88268】
21.3. Role membership
It's often convenient to group users together to manage permissions : like that , Permissions can be granted to or reclaimed from an entire group . stay PostgreSQL By creating a role that represents a group , And then the membership in that group role is granted to a separate user role .
To create a group role , First create the character :
CREATE ROLE name;
Roles that are usually used as a group do not need to have LOGIN attribute , But if you want to, you can also set it up . Once the group role exists , You can use GRANT and REVOKE Command to add and remove members :
GRANT group_role TO role1, ... ;
REVOKE group_role FROM role1, ... ;
- 1.
- 2.
You can also grant membership to other group roles ( Because there's no difference between a group role and a non group role ). The database will not let you set up ring Membership . in addition , Membership in a role is not allowed to be granted to PUBLIC.
Members of a group role can use role permissions in two ways . First of all , Each member of can be explicitly a group SET ROLE Coming “ Become ” Group roles . In this state , The database session can access the permissions of the group role instead of the original login role , And any database object created is considered to belong to the group role rather than the login role . second , Yes INHERIT Attribute's member roles automatically have the permissions of the role to which they belong , Include permissions inherited from any group role . As an example , Suppose we already have :
CREATE ROLE joe LOGIN INHERIT;
CREATE ROLE admin NOINHERIT;
CREATE ROLE wheel NOINHERIT;
GRANT admin TO joe;
GRANT wheel TO admin;
- 1.
- 2.
- 3.
- 4.
- 5.
As a character joe After connection , A database session will have immediate ownership granted directly to joe Authority , Plus any grant to admin Authority , because joe“ Inherited ” admin Authority . However , Granted to wheel Permission for is not available , Because even if joe yes wheel An indirect member of , But the membership is through the belt NOINHERIT Attribute admin Got . stay :
SET ROLE admin;
after , The session will only have the grant to admin Authority , But not to joe Authority . In execution :
SET ROLE wheel;
after , The session will only have the grant to wheel Authority , But not to joe or admin Authority . The initial permission state can be restored using one of the following commands :
SET ROLE joe;
SET ROLE NONE;
RESET ROLE;
- 1.
- 2.
- 3.
SET ROLE The command always allows you to select the direct or indirect group role of the original login role . therefore , In the example above , Is becoming wheel You don't have to be admin.
stay SQL In the standard , The difference between users and roles is clear , And users don't automatically inherit permissions, but roles do . This kind of behavior PostgreSQL Can also be achieved in : To be used for SQL The role of the character gives INHERIT attribute , To be used as SQL The role of the user is given NOINHERIT attribute .
however , For backward compatibility 8.1 Previous releases ( Where users always have the rights of their group ),PostgreSQL Default to all characters INHERIT attribute .
Character attributes LOGIN、SUPERUSER、CREATEDB and CREATEROLE It can be thought of as a special privilege , But they
It is never inherited like normal permissions on database objects . To use these properties , You have to be practical SET ROLE To a specific character with one of these attributes . Continue with the above example , We can choose to award CREATEDB and CREATEROLE to admin role . And then one with joe The session to which the role is connected will not immediately have these permissions , Only in execution SET ROLE admin Only after that will we have it .
To destroy a group character , Use DROP ROLE:
DROP ROLE name;
The membership of any role in the group is automatically revoked ( But the member role is not affected ).
边栏推荐
- Open3d uses GICP to register point clouds
- Redis master-slave replication cluster and recovery ideas for abnormal data loss # yyds dry goods inventory #
- Summary of the function and usage of const, volatile and restrict
- Basic operations of database and table ----- delete index
- Intel sapphire rapids SP Zhiqiang es processor cache memory split exposure
- 创新引领方向 华为智慧生活全场景新品齐发
- 如果消费互联网比喻成「湖泊」的话,产业互联网则是广阔的「海洋」
- 微信小程序:最新wordpress黑金壁纸微信小程序 二开修复版源码下载支持流量主收益
- RB technology stack
- The performance of major mainstream programming languages is PK, and the results are unexpected
猜你喜欢
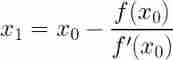
Visual explanation of Newton iteration method
SAP ui5 application development tutorial 106 - how to improve the readability of SAP ui5 application routing URL trial version

Inventory of more than 17 typical security incidents in January 2022

POAP:NFT的采用入口?
Single step debugging of master data reading of SAP commerce cloud products
Huawei employs millions of data governance experts! The 100 billion market behind it deserves attention
Expose testing outsourcing companies. You may have heard such a voice about outsourcing
微信小程序:微群人脉微信小程序源码下载全新社群系统优化版支持代理会员系统功能超高收益

Poap: the adoption entrance of NFT?

Remote control service
随机推荐
[pure tone hearing test] pure tone hearing test system based on MATLAB
Paxos 入门
Basic operations of database and table ----- delete index
SAP ui5 application development tutorial 107 - trial version of SAP ui5 overflow toolbar container control introduction
Poap: the adoption entrance of NFT?
程序员SQL数据脚本编码能力弱,BI做不出来怎么办?
Talking about JVM 4: class loading mechanism
Nebula Importer 数据导入实践
Implementation steps of master detail detail layout mode of SAP ui5 application
Senior Test / development programmers write no bugs? Qualifications (shackles) don't be afraid of mistakes
Expose testing outsourcing companies. You may have heard such a voice about outsourcing
抓包整理外篇——————状态栏[ 四]
Playwright recording
微信小程序:独立后台带分销功能月老办事处交友盲盒
6. Scala operator
Maximum number of "balloons"
Four pits in reentrantlock!
FEG founder rox:smartdefi will be the benchmark of the entire decentralized financial market
Discrete mathematics: Main Normal Form (main disjunctive normal form, main conjunctive normal form)
ROS command line tool