当前位置:网站首页>什么是弱引用?es6中有哪些弱引用数据类型?js中的弱引用是什么?
什么是弱引用?es6中有哪些弱引用数据类型?js中的弱引用是什么?
2022-07-06 01:13:00 【imkaifan】
弱引用:
WeakSet 中的对象都是弱引用,垃圾回收机制不考虑 WeakSet 对该对象的引用,也就是说,如果其他对象都不再引用该对象,那么垃圾回收机制会自动回收该对象所占用的内存,不考虑该对象还存在于 WeakSet 之中。
这是因为垃圾回收机制根据对象的可达性(reachability)来判断回收,如果对象还能被访问到,垃圾回收机制就不会释放这块内存。结束使用该值之后,有时会忘记取消引用,导致内存无法释放,进而可能会引发内存泄漏。WeakSet 里面的引用,都不计入垃圾回收机制,所以就不存在这个问题。因此,WeakSet 适合临时存放一组对象,以及存放跟对象绑定的信息。只要这些对象在外部消失,它在 WeakSet 里面的引用就会自动消失。
由于上面这个特点,WeakSet 的成员是不适合引用的,因为它会随时消失。另外,由于 WeakSet 内部有多少个成员,取决于垃圾回收机制有没有运行,运行前后很可能成员个数是不一样的,而垃圾回收机制何时运行是不可预测的,因此 ES6 规定 WeakSet 不可遍历。而且自然也就没有size属性,因为有多少数据量也是不确定的。
这些特点同样适用于 WeakMap 结构
边栏推荐
- Mlsys 2020 | fedprox: Federation optimization of heterogeneous networks
- Opinions on softmax function
- Who knows how to modify the data type accuracy of the columns in the database table of Damon
- Hundreds of lines of code to implement a JSON parser
- 基于DVWA的文件上传漏洞测试
- VMware Tools安装报错:无法自动安装VSock驱动程序
- 有谁知道 达梦数据库表的列的数据类型 精度怎么修改呀
- After 95, the CV engineer posted the payroll and made up this. It's really fragrant
- Paging of a scratch (page turning processing)
- Cglib dynamic agent -- example / principle
猜你喜欢
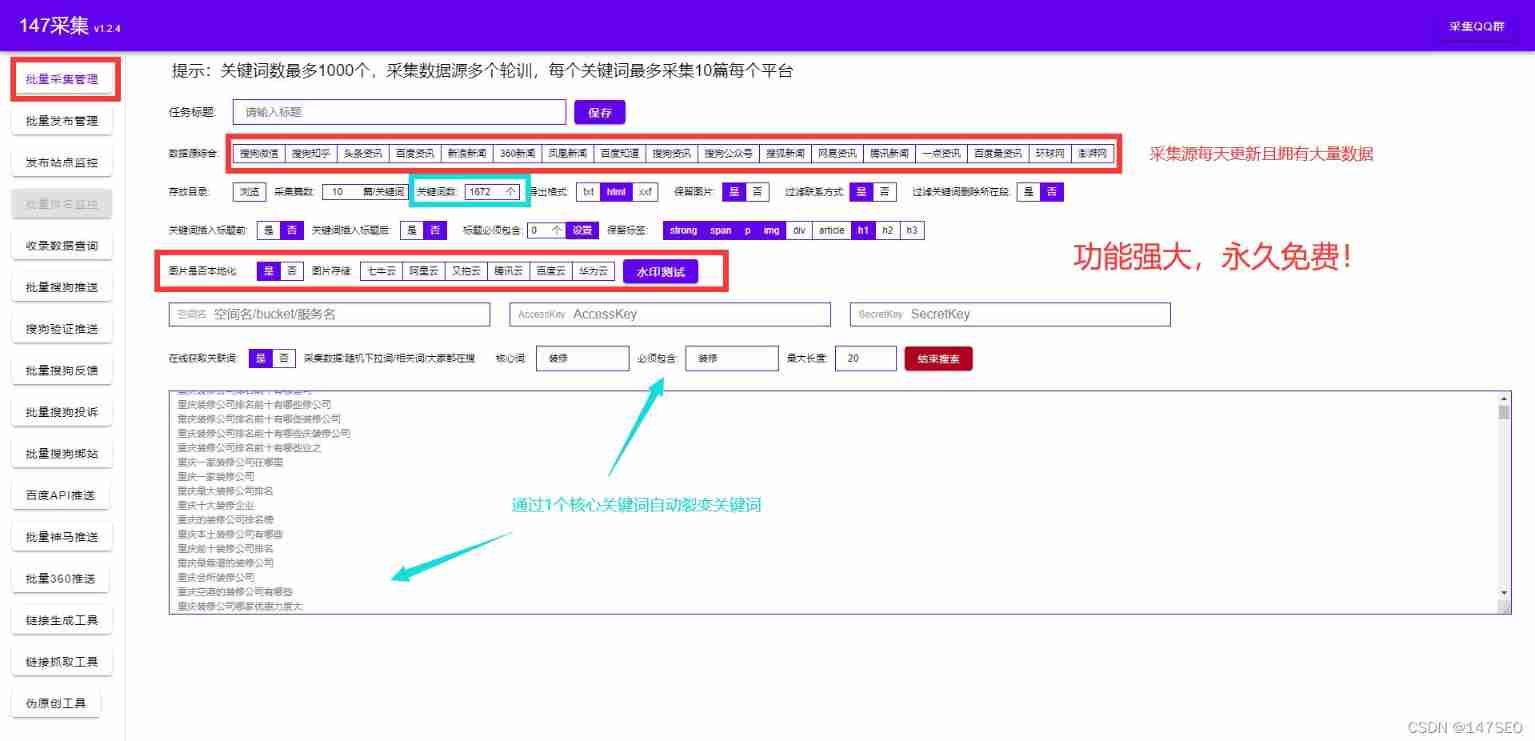
Dede collection plug-in free collection release push plug-in
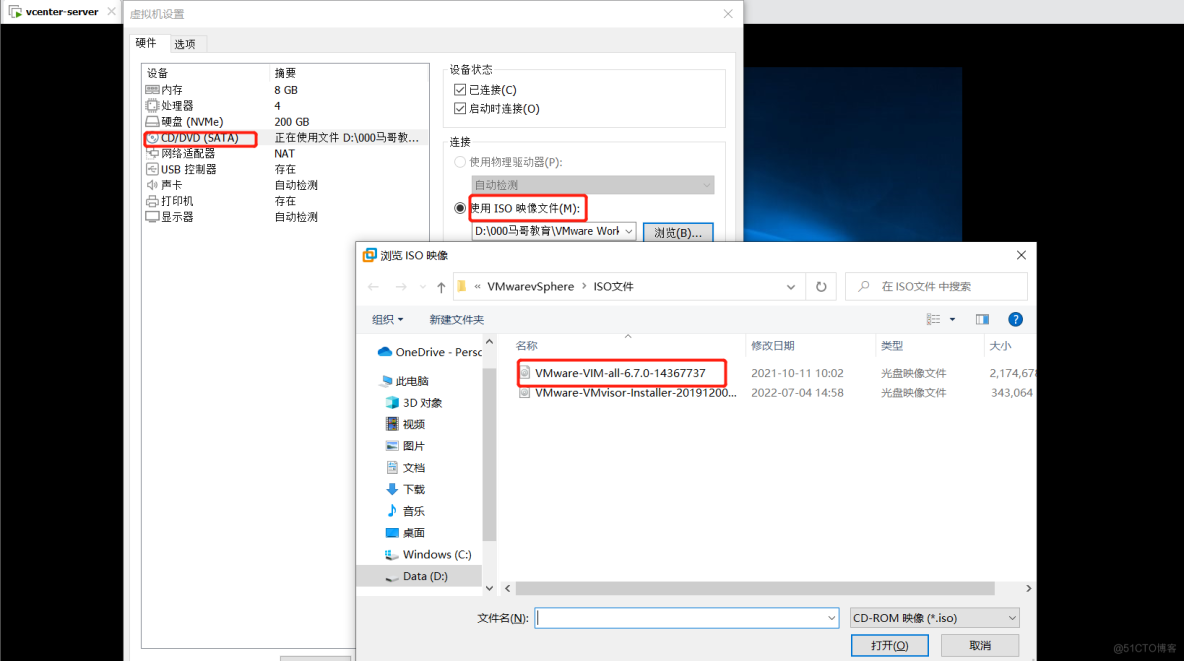
VSphere implements virtual machine migration
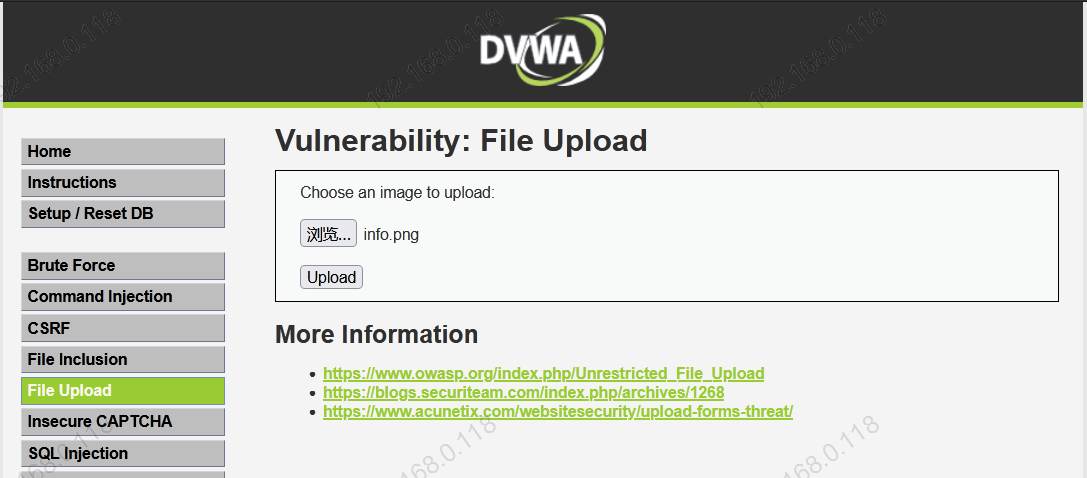
基于DVWA的文件上传漏洞测试
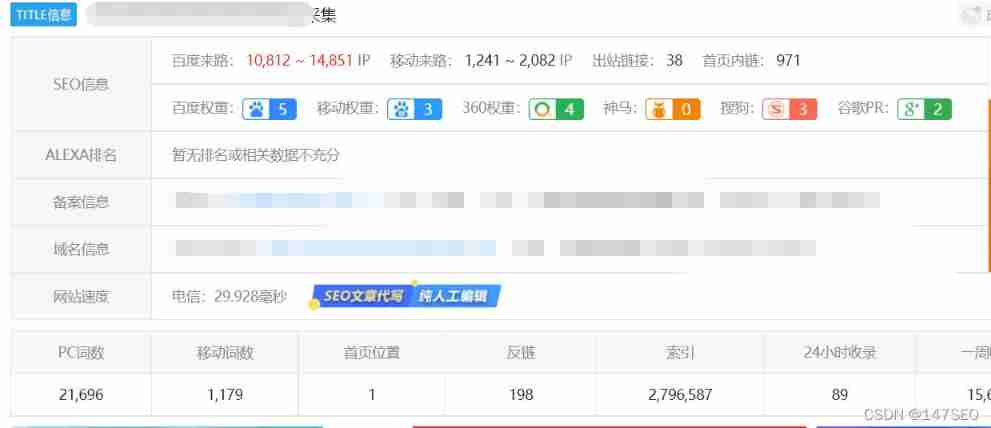
WordPress collection plug-in automatically collects fake original free plug-ins
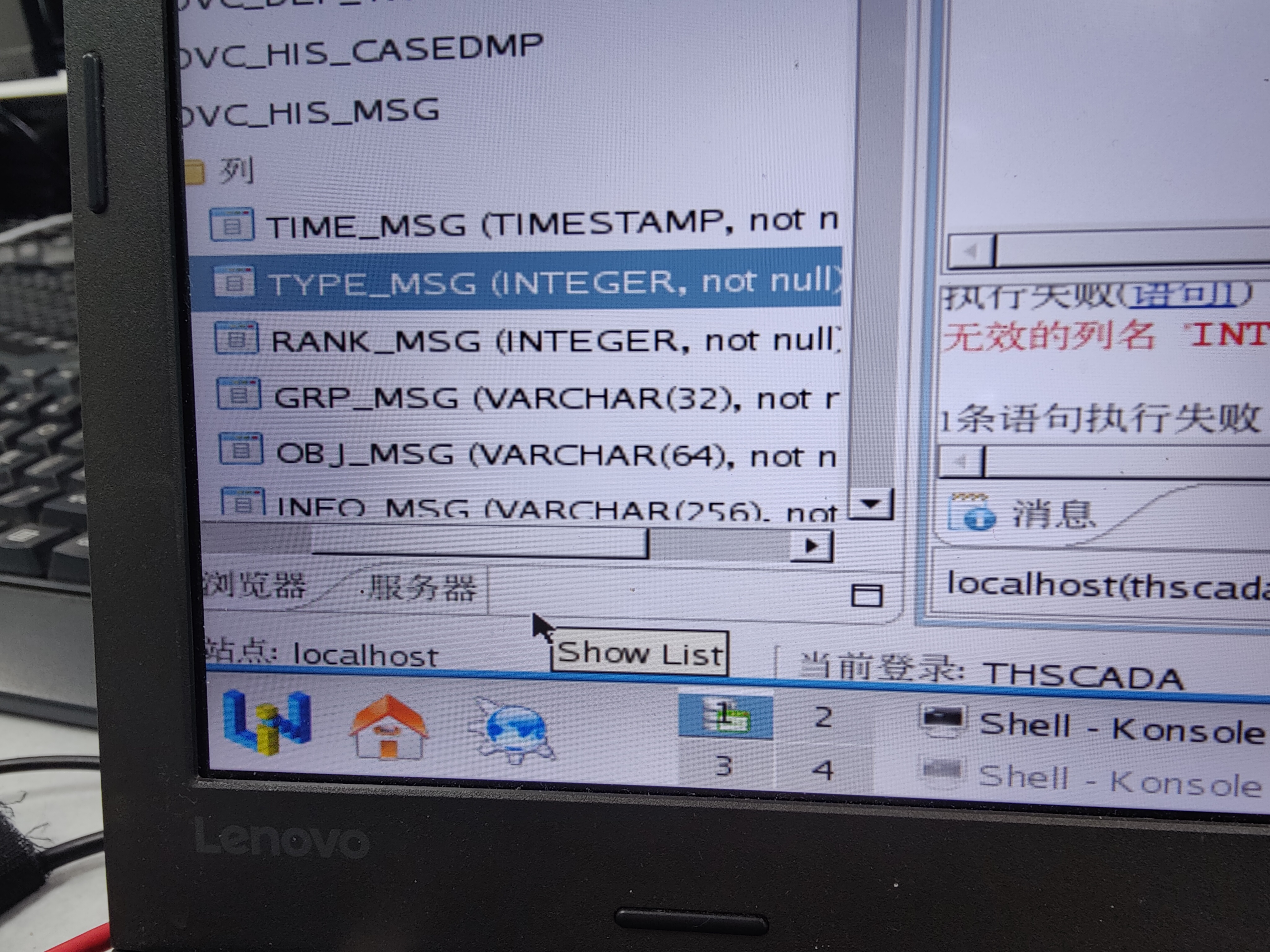
Who knows how to modify the data type accuracy of the columns in the database table of Damon

How to see the K-line chart of gold price trend?
Hcip---ipv6 experiment

Pbootcms plug-in automatically collects fake original free plug-ins
ThreeDPoseTracker项目解析

Questions about database: (5) query the barcode, location and reader number of each book in the inventory table
随机推荐
ORA-00030
Three methods of script about login and cookies
程序员成长第九篇:真实项目中的注意事项
VMware Tools installation error: unable to automatically install vsock driver
程序员搞开源,读什么书最合适?
现货白银的一般操作方法
Distributed base theory
1791. Find the central node of the star diagram / 1790 Can two strings be equal by performing string exchange only once
Beginner redis
C language programming (Chapter 6 functions)
About error 2003 (HY000): can't connect to MySQL server on 'localhost' (10061)
Cglib dynamic agent -- example / principle
Nmap: network detection tool and security / port scanner
在产业互联网时代,将会凭借大的产业范畴,实现足够多的发展
Zhuhai laboratory ventilation system construction and installation instructions
ubantu 查看cudnn和cuda的版本
Cf:c. the third problem
Study diary: February 13, 2022
Is chaozhaojin safe? Will it lose its principal
Lone brave man