当前位置:网站首页>September 9, 2020: naked writing algorithm: two threads print numbers 1-100 in turn.
September 9, 2020: naked writing algorithm: two threads print numbers 1-100 in turn.
2020-11-06 21:50:00 【Fuda Dajia architect's daily question】
Fogo's answer 2020-09-09:
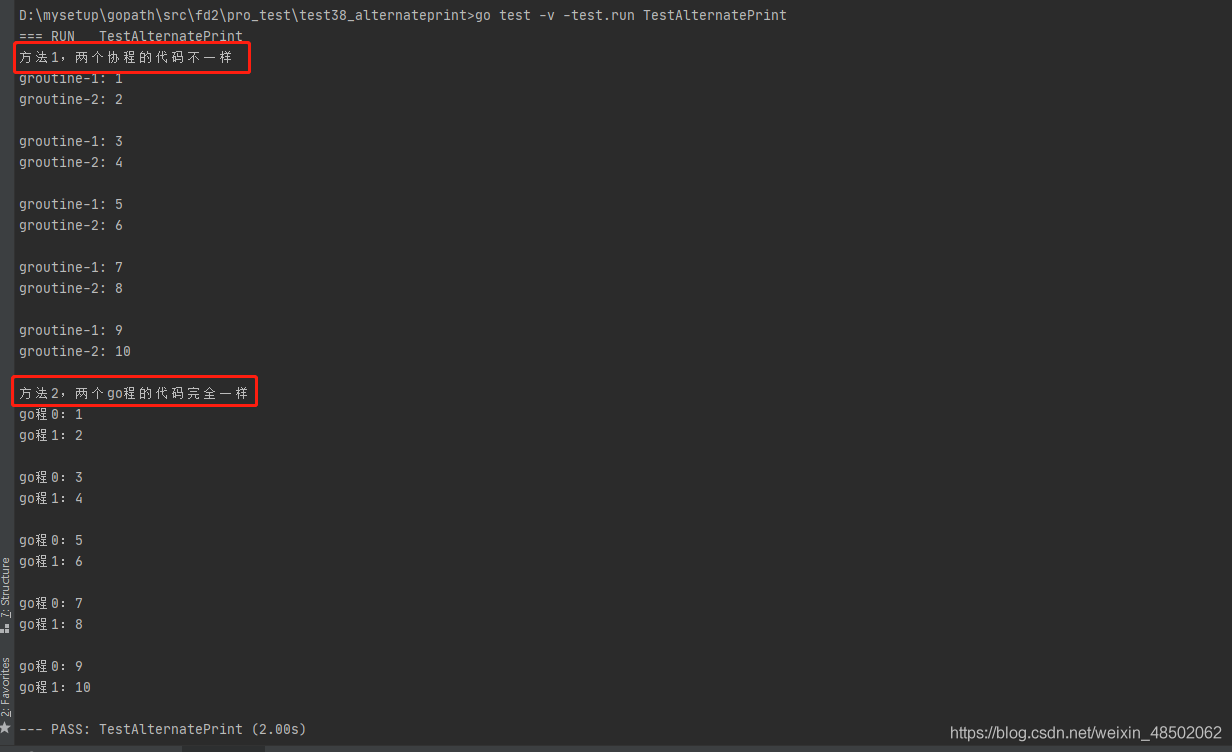
Method 1: With a channel , Two go The program code is different .
Method 2: Two channels , Two go The program code is exactly the same . It can be extended to N individual go Cheng takes turns printing .
The code to use golang To write , The code is as follows :
package test38_alternateprint
import (
"fmt"
"testing"
"time"
)
var POOL = 10
//go test -v -test.run TestAlternatePrint
func TestAlternatePrint(t *testing.T) {
AlternatePrint1()
AlternatePrint2()
}
// Method 1
func AlternatePrint1() {
fmt.Println(" Method 1, The codes of the two coroutines are different ")
msg := make(chan int)
go func(p chan int) {
for i := 1; i <= POOL; i++ {
p <- i
if i%2 == 1 {
fmt.Println("groutine-1:", i)
}
}
}(msg)
go func(p chan int) {
for i := 1; i <= POOL; i++ {
<-p
if i%2 == 0 {
fmt.Println("groutine-2:", i)
fmt.Println("")
}
}
}(msg)
// Wait for the execution of the cooperation process to complete
time.Sleep(time.Second * 1)
}
// Method 2
func AlternatePrint2() {
fmt.Println(" Method 2, Two go The program code is exactly the same ")
const N = 2
chs := make([]chan struct{}, N)
for i := 0; i < N; i++ {
chs[i] = make(chan struct{}, 0)
}
start := 1
for i := 0; i < N; i++ {
go func(i int) {
for start <= POOL-N+1 {
// Get executive power
<-chs[i]
// Execute code
fmt.Printf("go cheng %d:%d\r\n", i, start)
if (i+1)%N == 0 {
fmt.Println("")
}
start++
// Give other programs the right to execute
chs[(i+1)%N] <- struct{}{}
}
}(i)
}
// Give it to 1 The right to execute a contract , The first 1 The sequence number of the coroutines is 0
chs[0] <- struct{}{}
// Wait for the execution of the cooperation process to complete
time.Sleep(time.Second * 1)
// Take back the last 1 individual go The executive power of Cheng
<-chs[POOL%N]
} knock go test -v -test.run TestAlternatePrint command , give the result as follows :
版权声明
本文为[Fuda Dajia architect's daily question]所创,转载请带上原文链接,感谢
边栏推荐
- Using iceberg on kubernetes to create a new generation of cloud original data Lake
- ado.net and asp.net The relationship between
- Application insights application insights use application maps to build request link views
- The essence of transaction and the principle of deadlock
- An article takes you to understand CSS pagination examples
- 【涂鸦物联网足迹】涂鸦云平台全景介绍
- Interviewer: how about shardingsphere
- 迅为-iMX6ULL开发板上配置AP热点
- 2020-08-14:数据任务的执行引擎用的哪些?
- Windows 10 蓝牙管理页面'添加蓝牙或其他设备'选项点击无响应的解决方案
猜你喜欢

Can you do it with only six characters?

2020-08-18:介绍下MR过程?

What is the tensor in tensorflow?

Understanding formatting principles

An article will introduce you to CSS3 background knowledge

Some operations kept in mind by the front end foundation GitHub warehouse management

Pn8162 20W PD fast charging chip, PD fast charging charger scheme

ORA-02292: 违反完整约束条件 (MIDBJDEV2.SYS_C0020757) - 已找到子记录

Stickinengine architecture 11 message queue

An article will introduce you to HTML tables and their main attributes
随机推荐
ES6 learning notes (3): teach you to use js object-oriented thinking to realize the function of adding, deleting, modifying and checking tab column
Exclusive interview with Alibaba cloud database for 2020 PostgreSQL Asia Conference: Zeng Wenjing
Vue communication and cross component listening state Vue communication
小熊派开发板实践:智慧路灯沙箱实验之真实设备接入
Common syntax corresponding table of mongodb and SQL
GitHub: the foundation of the front end
Summary of front-end interview questions (C, s, s) that front-end engineers need to understand (2)
Using an example to understand the underlying processing mechanism of JS function
Zero basis to build a web search engine of its own
Common mathematical basic formulas of recursive and backtracking algorithms
A concise tutorial for Nacos, ribbon and feign
打工人好物——磨炼钢铁意志就要这样高效的电脑
轻量型 GPU 应用首选 京东智联云推出 NVIDIA vGPU 实例
实验一
Hdu3974 assign the task segment tree DFS order
ES6 learning notes (4): easy to understand the new grammar of ES6
Zero basis to build a web search engine of its own
An article taught you to download cool dog music using Python web crawler
Jenkins installation and deployment process
Ora-02292: complete constraint violation (midbjdev2.sys_ C0020757) - subrecord found