当前位置:网站首页>BUUCTF MISC
BUUCTF MISC
2022-07-05 04:59:00 【zh0u9527】
BUUCTF MISC
[GXYCTF2019]gakki
- Download the attachment and get a picture , Use binwalk To separate , Get a compressed package .
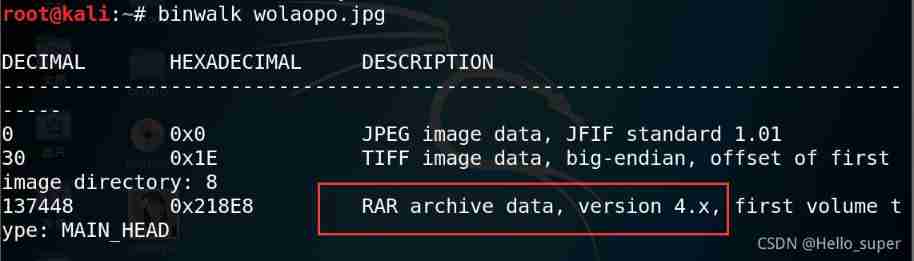
- Use ARCPHR The compressed bag blasting tool is used for blasting , Successfully get the password .
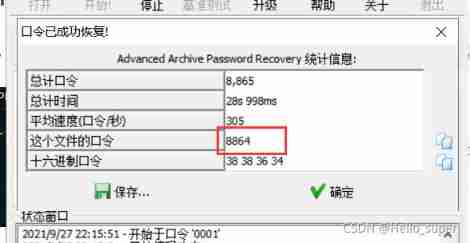
- Get it in the compressed package flag.txt file , Found a large number of disordered characters , Use Python Script tool for statistics .

# -*- coding:utf-8 -*-
#Author: mochu7
alphabet = "[email protected]#$%^&*()_+- =\\{\\}[]"
strings = open('./flag.txt').read()
result = {
}
for i in alphabet:
counts = strings.count(i)
i = '{0}'.format(i)
result[i] = counts
res = sorted(result.items(),key=lambda item:item[1],reverse=True)
for data in res:
print(data)
for i in res:
flag = str(i[0])
print(flag[0],end="")
[ACTF Freshman competition 2020]base64 Steganography
1. Download the attachment , Get a text file , Full of base64 Encrypted data .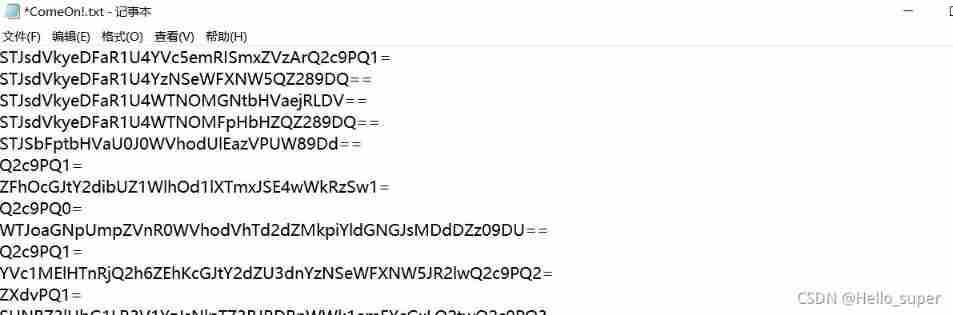
2. To write Python The script decrypts .
def get_base64_diff_value(s1, s2):
base64chars = 'ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/'
res = 0
for i in xrange(len(s2)):
if s1[i] != s2[i]:
return abs(base64chars.index(s1[i]) - base64chars.index(s2[i]))
return res
def solve_stego():
with open('ComeOn!.txt', 'rb') as f:
file_lines = f.readlines()
bin_str = ''
for line in file_lines:
steg_line = line.replace('\n', '')
norm_line = line.replace('\n', '').decode('base64').encode('base64').replace('\n', '')
diff = get_base64_diff_value(steg_line, norm_line)
print diff
pads_num = steg_line.count('=')
if diff:
bin_str += bin(diff)[2:].zfill(pads_num * 2)
else:
bin_str += '0' * pads_num * 2
print goflag(bin_str)
def goflag(bin_str):
res_str = ''
for i in xrange(0, len(bin_str), 8):
res_str += chr(int(bin_str[i:i + 8], 2))
return res_str
if __name__ == '__main__':
solve_stego()
[WUSTCTF2020]find_me
Download and find a picture , View the properties of the picture , Find a string of symbols that you can't understand , Based on previous experience , Judgment is Braille , Online website decryption succeeded flag.
https://www.qqxiuzi.cn/bianma/wenbenjiami.php?s=mangwen
[ACTF Freshman competition 2020] Plaintext attack
- Download the attachment , Get a compressed package , The package nested this other package , After decompressing , Get a picture and a res.zip Compressed package , But decompress the password .
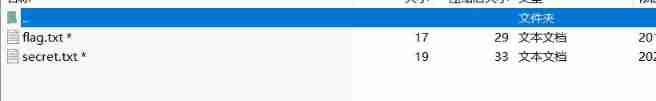
- Read the files inside with the decompression software , Found two files , Respectively flag.txt And secret.txt. The title says plaintext attack , Let's start with the drawing .
- Use winhex Open the picture , Found at the end of the file flag.txt Document type , So happy to use binwalk Command to extract , But I found that I couldn't extract anything , Silly ! Why? ?
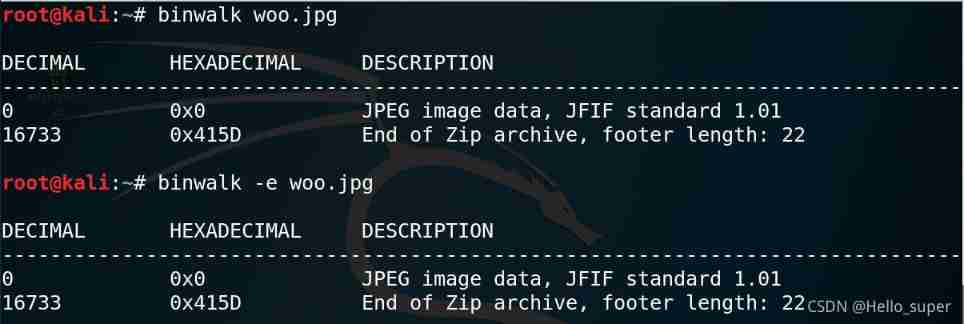
- By examining the file carefully hex value , Found that the file header is incomplete .
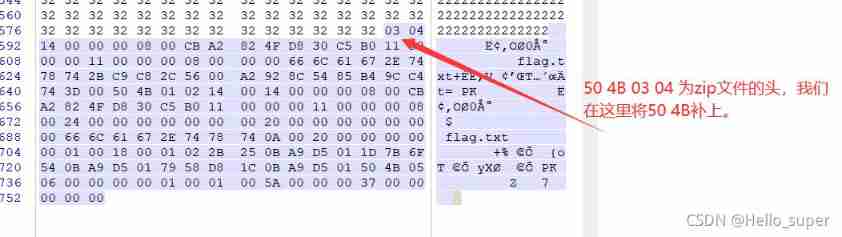
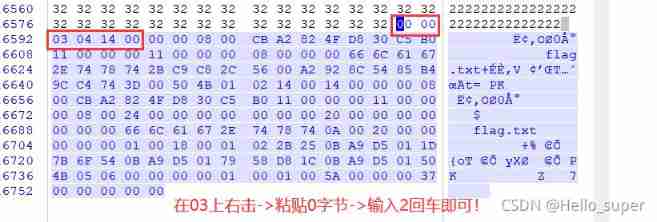
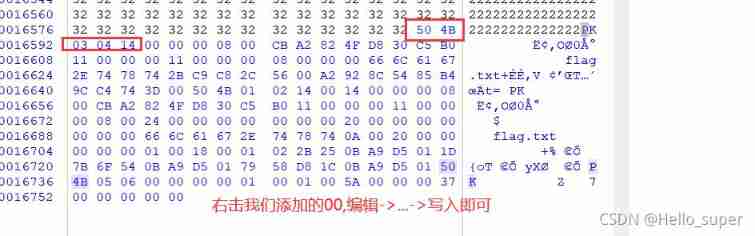
- Then change the suffix of the image file to zip, decompression , Successfully get flag.txt file , But that's not real flag. Combined with the plaintext attack of the title , We'll get flag.txt The file is compressed to zip Format , Use ARCHPR Blast attack attack .
Simple encryption
- Download the attachment to get a ciphertext and encryption script .
==jEgWTn8kJrRyRFBuKJLuzH1LmDTAzs
function encode( $str = '' ){
$strrev = strrev( $str );
$string = '';
for( $i=0; $i < strlen($strrev);$i++ ){
$char = substr( $strrev, $i, 1 );
$ordChar = ord( $char ) + 1;
$char = chr( $ordChar );
$string = $string.$char;
}
$string = base64_encode( $string );
$string = strrev( $string );
$string = str_rot13( $string );
return $string;
}
- In fact, the encryption script is quite simple , But because of my weak foundation , It took hours to write it out , But it's worth remembering .
function decode( $str = ''){
$strrev = strrev($str);
$strrev = str_rot13($strrev);
$strrev = base64_decode($strrev);
$string = '';
for ( $i=0; $i < strlen($strrev);$i++ ){
$char = substr( $strrev, $i, 1 );
$ordChar = ord( $char ) - 1;
$char = chr( $ordChar );
$string = $string.$char;
}
return $string;
}
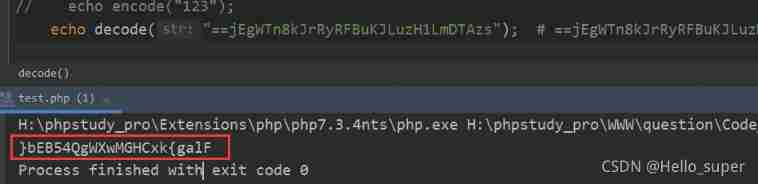 Use python Just invert the string in the middle section of :
Use python Just invert the string in the middle section of :
>>>string = '}bEB54QgWXwMGHCxk{galF'
>>> print(string[::-1]);
Flag{
kxCHGMwXWgQ45BEb}
The matrix
- Download the attachment , Get a file , Use winhex View discovery yes zip file , Unzip to get a text file , The contents of the file are all hexadecimal , And the beginning of the file is 52617221, It is preliminarily judged that this is a rar file , Use python Write hex to another file in binary form .
import binascii
content = ''
with open('resource.txt') as file_obj:
content = file_obj.read()
out=open('res.txt','wb')
out.write(binascii.unhexlify(content))
out.close()
- Unzip the file again , But you need a password , Mask blasting with blasting tools , Successfully get the password 3690.
- When opening a file , It is found that it cannot be displayed normally png picture , Start using winhex I didn't find anything when I checked , Look at the big guy's wp Just know that this is a jpg file ,jpg The file header of the picture is replaced with png The file header of cannot be displayed normally .
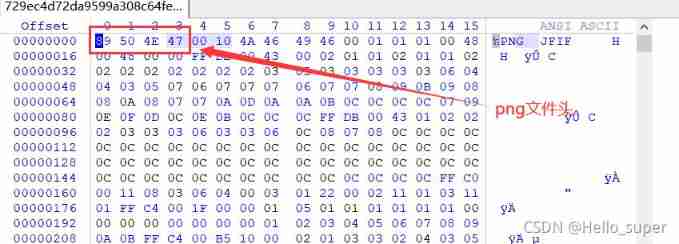
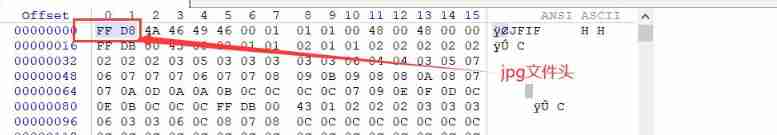 After being changed , The picture can be displayed normally , I succeeded in getting flag.
After being changed , The picture can be displayed normally , I succeeded in getting flag.
[MRCTF2020] You can understand the notes
- Download the attachment , Get one rar Compressed package , But it cannot be opened normally , Use winhex After checking, I know that the first two bytes of the original file header have been replaced , Just slow down .
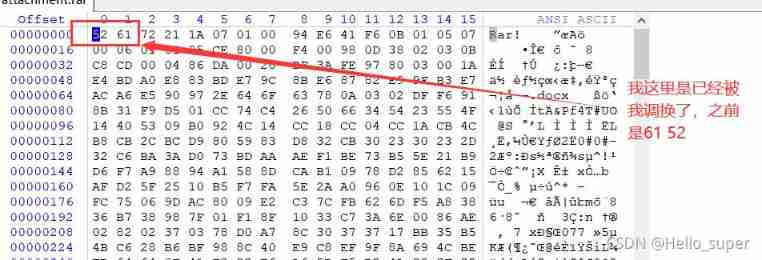
- To succeed in getting one word file , Open it and find nothing , Use binwalk Scan a wave of , It was found that zip file , Direct will word Change the file suffix to zip To extract .
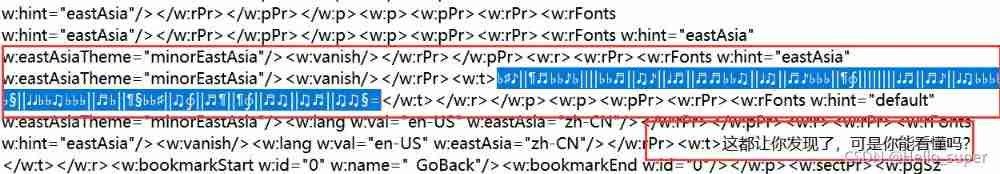
- Open it with notepad document.xml file , Found the note usage in it Online website decryption Successfully get flag!

[GUET-CTF2019]KO
[MRCTF2020]ezmisc
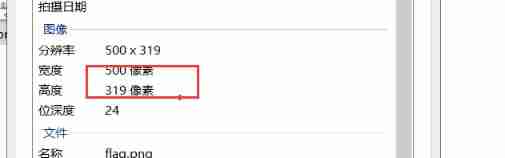
- Download the attachment to get a picture , When I first opened the picture, I found that the pixels of the picture were a little wrong 500x319. Think about whether the height of the picture has been tampered with .
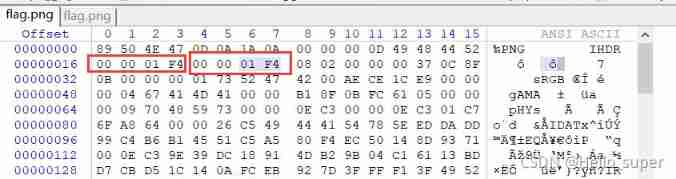
- Use winhex open , Change the height of the picture , Be careful , Since the width of the picture is 500, Then let's change the height to 500,500 The corresponding hexadecimal code is 1f4.

 preservation , The bottom of the picture successfully shows flag.
preservation , The bottom of the picture successfully shows flag.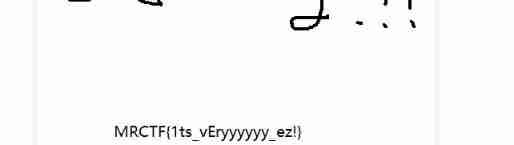
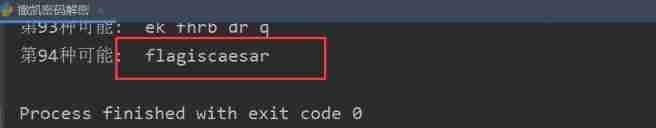
[HBNIS2018]caesar
Download the attachment to get a text file .

There was no clue at that time , Only after reading the boss's blog did I know , Directly use the script to decrypt .
def change(c, i):
num = ord(c)
if (num >= 33 and num <= 126):
num = 33 + (num + i - 33) % (94) # 126-33=93
return chr(num)
def kaisa_jiAmi(string, i):
string_new = ''
for s in string:
string_new += change(s, i)
print(string_new)
return string_new
# This topic has a feeling of violent decryption
def kaisa_jiEmi(string):
for i in range(0, 94):
print(' The first ' + str(i + 1) + ' Maybe :', end=' ')
# The difference lies in string Yes, the object is originally of string type , and str() Is to convert the object to string type .
kaisa_jiAmi(string, i)
# You need to know input The input data types are string
def main():
print(' Please input the operation , Attention is not usual 26 Kind of :')
choice = input('1: Caesar encrypted ,2: Caesar deciphered it exhaustively . Please enter 1 or 2:')
if choice == '1':
string = input(' Please enter the encrypted string : ')
num = int(input(' Please enter the to be encrypted KEY: '))
kaisa_jiAmi(string, num)
elif choice == '2':
string = input(' Please enter the string that needs to be decrypted : ')
kaisa_jiEmi(string)
else:
print(' Input error , Please try again ')
main()
if __name__ == '__main__':
main()
边栏推荐
猜你喜欢
![[groovy] closure (closure as function parameter | code example)](/img/a6/a4ed401acfb61f85eb08daa15a8a80.jpg)
[groovy] closure (closure as function parameter | code example)

Redis has four methods for checking big keys, which are necessary for optimization
【acwing】528. cheese
AutoCAD - lengthening
Autocad-- dynamic zoom
54. 螺旋矩阵 & 59. 螺旋矩阵 II ●●
AutoCAD - graphic input and output

2022 thinking of mathematical modeling C problem of American college students / analysis of 2022 American competition C problem
![[groovy] closure closure (customize closure parameters | customize a single closure parameter | customize multiple closure parameters | specify the default value of closure parameters)](/img/92/937122b059b6f3a91ae0e0858685e7.jpg)
[groovy] closure closure (customize closure parameters | customize a single closure parameter | customize multiple closure parameters | specify the default value of closure parameters)
AutoCAD - full screen display
随机推荐
How much do you know about 3DMAX rendering skills and HDRI light sources? Dry goods sharing
2022/7/2做题总结
AutoCAD - graphic input and output
2022 thinking of mathematical modeling a problem of American college students / analysis of 2022 American competition a problem
Common technologies of unity
【Leetcode】1352. 最后 K 个数的乘积
Recherche de mots pour leetcode (solution rétrospective)
Animation
Vs2015 secret key
2022/7/1學習總結
2022 U.S. college students' mathematical modeling e problem ideas / 2022 U.S. game e problem analysis
The first topic of ape Anthropology
2020-10-27
AutoCAD - continuous annotation
質量體系建設之路的分分合合
Unity ugui source code graphic
"Measuring curve length" of CAD dream drawing
2022/7/1学习总结
2022/7/2 question summary
Emlog博客主题模板源码简约好看响应式