当前位置:网站首页>Rip notes [rip message security authentication, increase of rip interface measurement]
Rip notes [rip message security authentication, increase of rip interface measurement]
2022-07-05 04:47:00 【Purer than pure passers-by】
Catalog
RIP Message security authentication [ The experimental diagram is as follows ]
rip Increase in interface metrics
RIP Message security authentication [ The experimental diagram is as follows ]
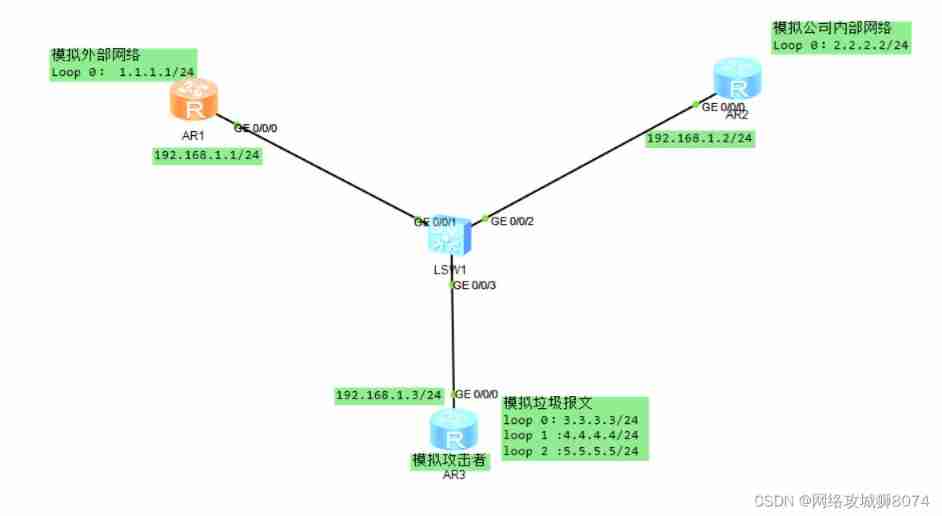
Basic configuration
First, complete the interface ip To configure [R3 It simulates the spam message of the attacker , These messages are a burden for the link, including equipment , but rip However, it is impossible to identify whether these messages are garbage messages, so it is impossible to intercept them , For these garbage messages rip Other devices in the will still be loaded into the routing table . It's not hard to imagine if R3 The garbage message of is generated in batch , Its impact on the whole network ]:
R1:
[Huawei]interface GigabitEthernet 0/0/0
[Huawei-GigabitEthernet0/0/0]ip address 192.168.1.1 24
[Huawei-GigabitEthernet0/0/0]q
[Huawei]interface LoopBack 0
[Huawei-LoopBack0]ip address 1.1.1.1 24
[Huawei]rip
[Huawei-rip-1]network 192.168.1.0
[Huawei-rip-1]network 1.0.0.0R2
[Huawei]interface GigabitEthernet 0/0/0
[Huawei-GigabitEthernet0/0/0]ip address 192.168.1.2 24
[Huawei-GigabitEthernet0/0/0]q
[Huawei]interface LoopBack 0
[Huawei-LoopBack0]ip address 2.2.2.2 24
[Huawei-LoopBack0]q
[Huawei]rip
[Huawei-rip-1]version 2
[Huawei-rip-1]network 192.168.1.0
[Huawei-rip-1]network 2.0.0.0R3
[Huawei]interface GigabitEthernet 0/0/0
[Huawei-GigabitEthernet0/0/0]ip address 192.168.1.3 24
[Huawei-GigabitEthernet0/0/0]q
[Huawei]interface LoopBack 0
[Huawei-LoopBack0]ip address 3.3.3.3 24
[Huawei-LoopBack0]q
[Huawei]interface LoopBack 1
[Huawei-LoopBack1]ip address 4.4.4.4 24
[Huawei-LoopBack1]q
[Huawei]interface LoopBack 2
[Huawei-LoopBack2]ip address 5.5.5.5 24
[Huawei-LoopBack2]q
[Huawei]rip
[Huawei-rip-1]version 2
[Huawei-rip-1]network 192.168.1.0
[Huawei-rip-1]network 3.0.0.0
[Huawei-rip-1]network 4.0.0.0
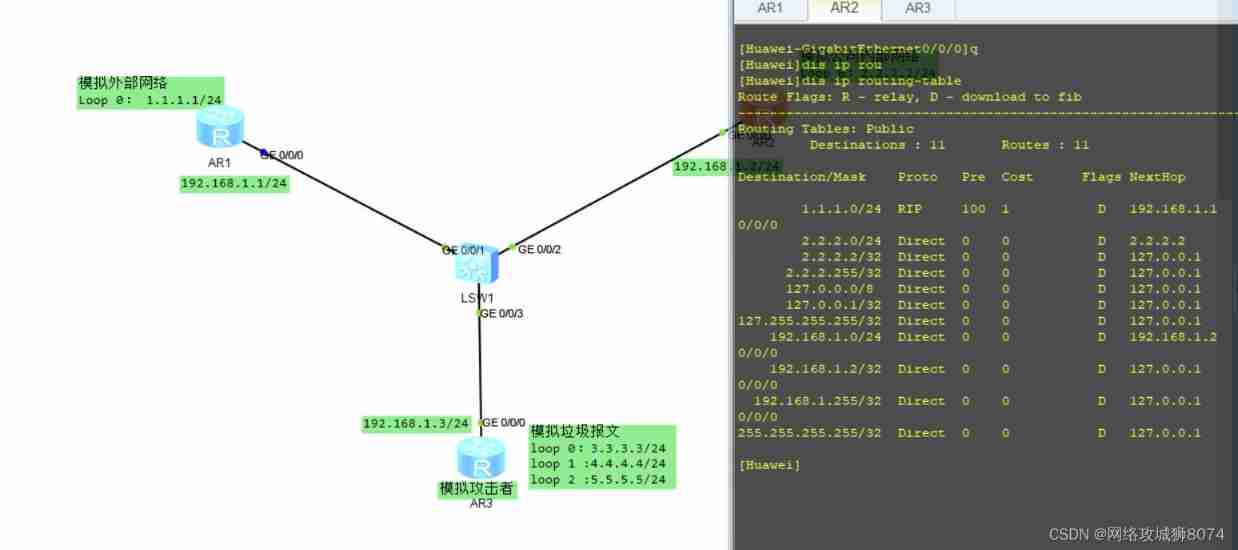
[Huawei-rip-1]network 5.0.0.0Now the basic configuration has been completed , see R1 The routing table of verifies whether the above idea is accurate , You can see R1 There is R3 All garbage messages , This is undoubtedly a burden for the equipment .
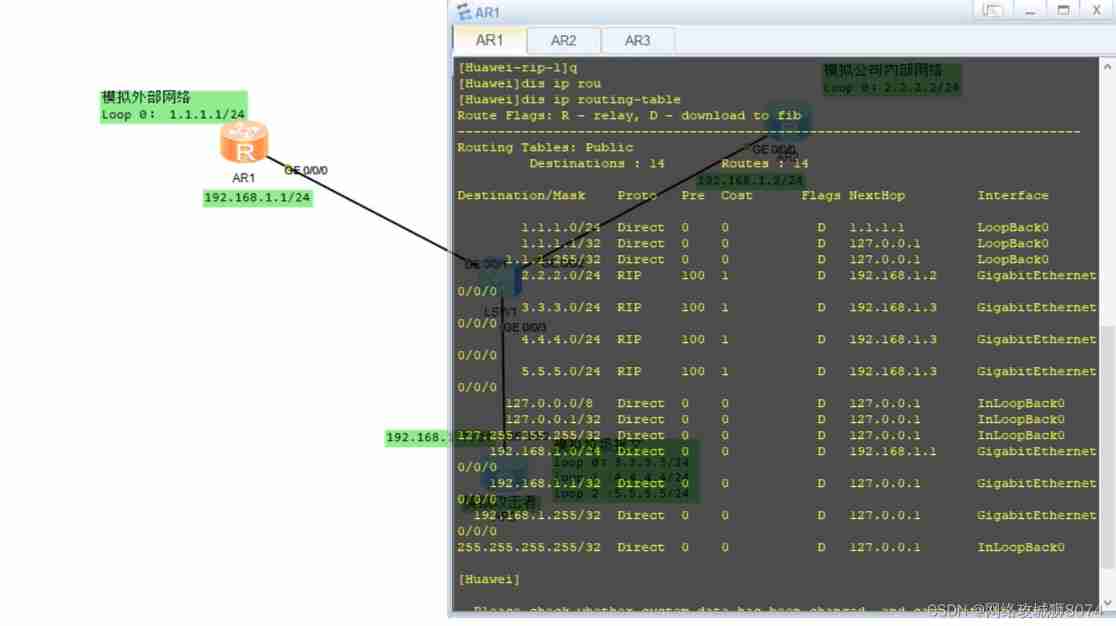
RIP authentication
R1【 among simple It is the authentication method of the message : Plaintext Authentication ; That is, the authentication password is clear text in message transmission , Verification diagram 1-5;
plain It means that the configuration file is in clear text , It can be done by dis th View the configuration information to get password information , Verification diagram 1-6】
[Huawei]interface GigabitEthernet 0/0/0
[Huawei-GigabitEthernet0/0/0]rip authentication-mode simple plain 123
chart 1-5【Src: primary ip Address ;Authentication: authentication ;Password: password 】
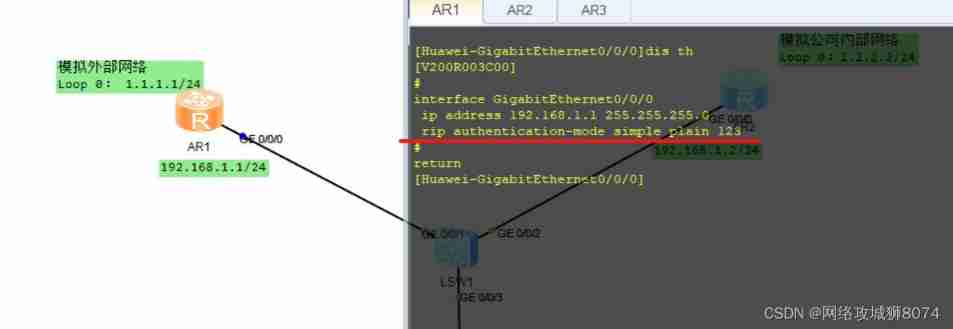
chart 1-6[ It can be seen that the configuration is clear text and will plain Switch to cipher It turns the configuration file into ciphertext ]
Now let's look at R2 The routing table for , According to the above idea, now R2 The routing table cannot be viewed 1.1.1.0/24 Of :
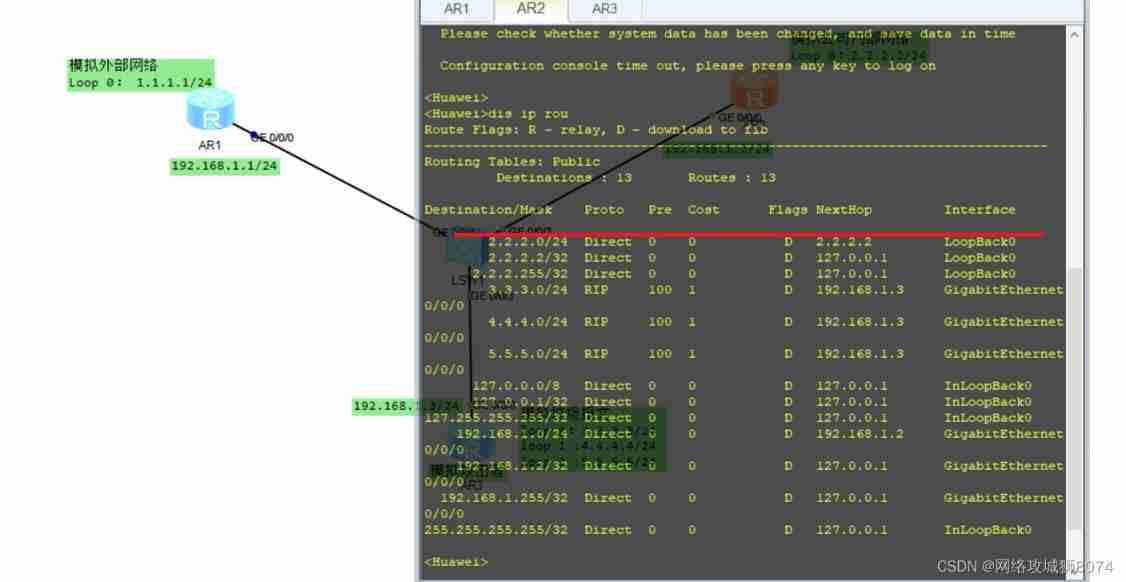
Sure enough R1 Of 1.1.1.0/24 Not in R2 In the routing table of , So just for R2 Also on the configuration RIP Verification is enough :
R2:
[Huawei]interface GigabitEthernet 0/0/0
[Huawei-GigabitEthernet0/0/0]rip authentication-mode simple plain 123Now look at R2 The routing table for 【 You can see R2 There's no more R3 Garbage message 】
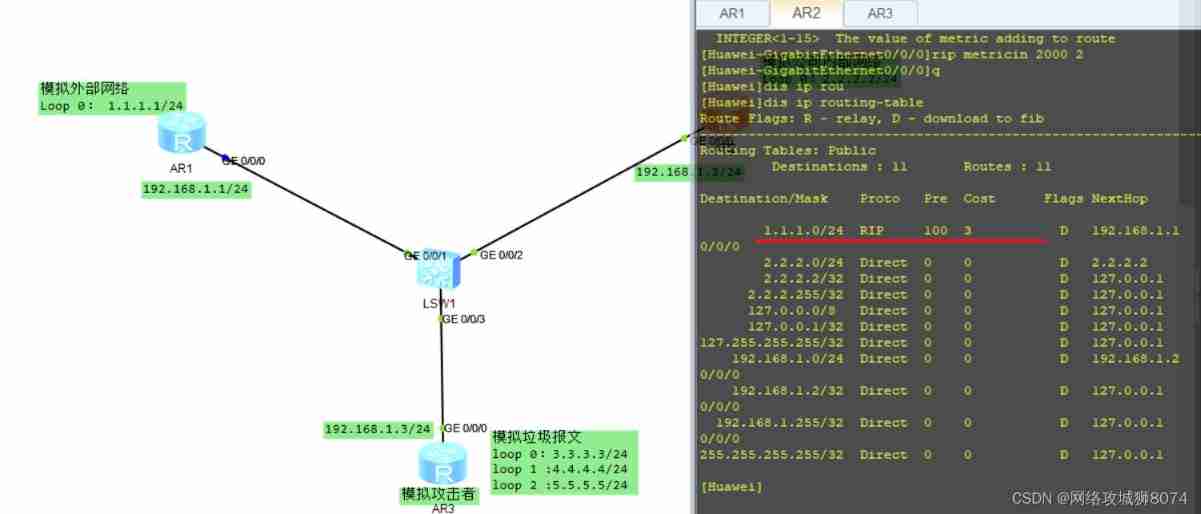
rip Increase in interface metrics
【 Use the above experiment to complete , here R2 On the routing table 1.1.1.0/24 The measure of is 1】
R2:
matching 1.1.1.0/24 The routing entry for :
[Huawei]acl 2000
[Huawei-acl-basic-2000]rule 5 permit source 1.1.1.0 0.0.0.255
[Huawei-acl-basic-2000]qConfiguration code , by 1.1.1.0/24 Routing increases 1 Measures
[Huawei]interface g0/0/0
[Huawei-GigabitEthernet0/0/0]rip metricin 2000 2see R1 The routing table for 【 You can see 1.0.0.0/24 The measure of the entry has become 3】:
边栏推荐
- 2021 electrician cup (the 12th "China Society of electrical engineering Cup" National Undergraduate electrician mathematical modeling) detailed ideas + codes + references
- level17
- Minor spanning tree
- Raki's notes on reading paper: code and named entity recognition in stackoverflow
- Pointer function (basic)
- 2022-2028 global and Chinese video coding and transcoding Market Research Report
- 【acwing】528. cheese
- windows下Redis-cluster集群搭建
- A survey of automatic speech recognition (ASR) research
- 49 pictures and 26 questions explain in detail what is WiFi?
猜你喜欢
假设检验——《概率论与数理统计》第八章学习笔记
【科普】热设计基础知识:5G光器件之散热分析

防护电路中的元器件
![[groovy] closure (closure call is associated with call method | call () method is defined in interface | call () method is defined in class | code example)](/img/03/329adb314606f29c8a4cb2260e84c8.jpg)
[groovy] closure (closure call is associated with call method | call () method is defined in interface | call () method is defined in class | code example)
![[AI bulletin 20220211] the hard core up owner has built a lidar and detailed AI accelerator](/img/cc/06580ce7b553182968d273841a78b4.jpg)
[AI bulletin 20220211] the hard core up owner has built a lidar and detailed AI accelerator
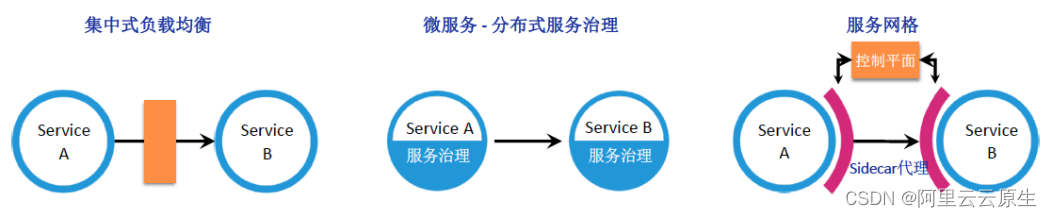
Managed service network: application architecture evolution in the cloud native Era
質量體系建設之路的分分合合
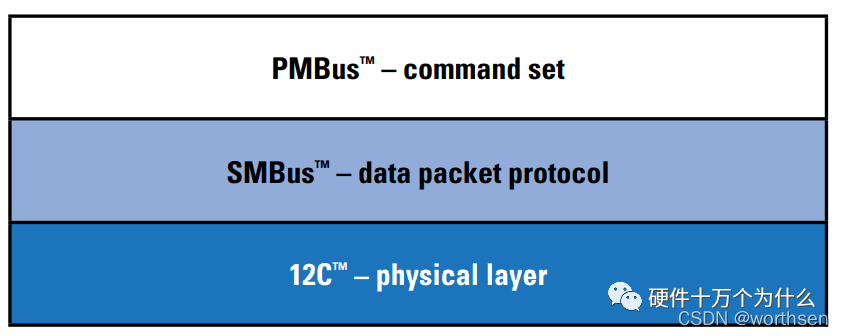
电源管理总线 (PMBus)
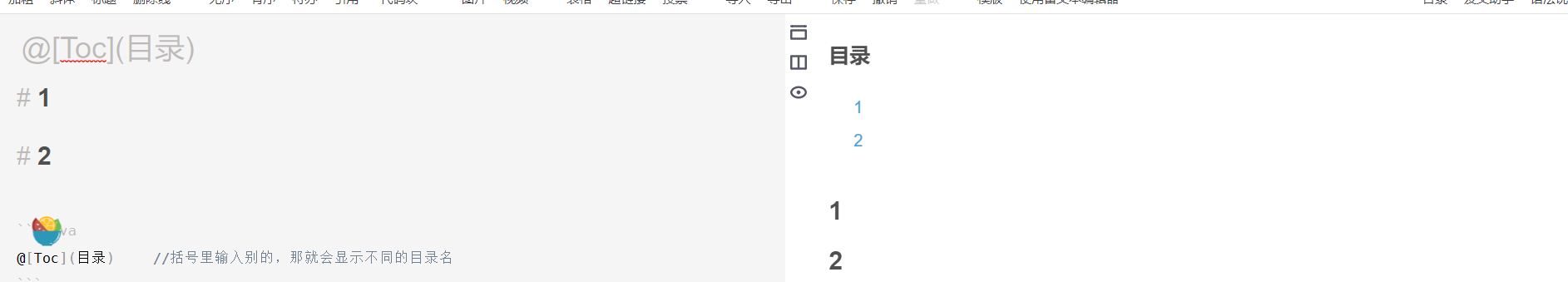
CSDN正文自动生成目录

Components in protective circuit
随机推荐
Power management bus (pmbus)
托管式服务网络:云原生时代的应用体系架构进化
History of web page requests
Official announcement! The third cloud native programming challenge is officially launched!
[groovy] closure (closure as function parameter | code example)
质量体系建设之路的分分合合
2021 Higher Education Club Cup mathematical modeling national tournament ABCD problem - problem solving ideas
Download the details and sequence of the original data access from the ENA database in EBI
JMeter -- distributed pressure measurement
Stage experience
[goweb development] Introduction to authentication modes based on cookies, sessions and JWT tokens
次小生成树
Advanced length of redis -- deletion strategy, master-slave replication, sentinel mode
windows下Redis-cluster集群搭建
jmeter -- 分布式压测
Minor spanning tree
Basic analysis of IIC SPI protocol
windows下Redis-cluster集群搭建
函数(易错)
2022-2028 global and Chinese FPGA prototype system Market Research Report