当前位置:网站首页>A complete attack chain
A complete attack chain
2022-07-05 04:57:00 【zh0u9527】
A complete attack chain
The complete attack chain includes information collection 、 Exploit 、 Build a stronghold 、 Elevated privileges 、 Authority maintenance 、 Move horizontally 、 Seven steps with clear traces , Although this site has only experienced the first four steps , But it is also highly representative , Combine vulnerabilities to form an attack chain , Take down the administrative authority .
Full band stop : Remember an authorized network attack and defense drill ( On )
Full band stop : Remember an authorized network attack and defense drill ( Next )
边栏推荐
- [Business Research Report] Research Report on male consumption trends in other economic times -- with download link
- 775 Div.1 C. Tyler and strings combinatorial mathematics
- 猿人学第一题
- Special information | finance, accounting, audit - 22.1.23
- Flutter tips: various fancy nesting of listview and pageview
- China needle coke industry development research and investment value report (2022 Edition)
- Unity sends messages and blocks indecent words
- 3dsmax2018 common operations and some shortcut keys of editable polygons
- Forecast report on research and investment prospects of Chinese wormwood industry (2022 Edition)
- 2021 electrician cup idea + code - photovoltaic building integration plate index development trend analysis and prediction: prediction planning issues
猜你喜欢
PostgreSQL 超越 MySQL,“世界上最好的编程语言”薪水偏低
54. Spiral matrix & 59 Spiral matrix II ●●
Thinking of 2022 American College Students' mathematical modeling competition
AutoCAD - lengthening
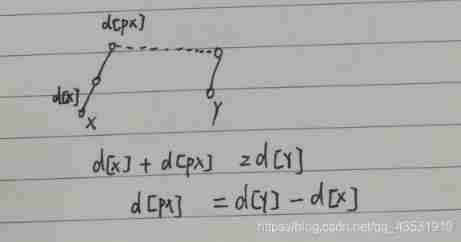
【acwing】240. food chain
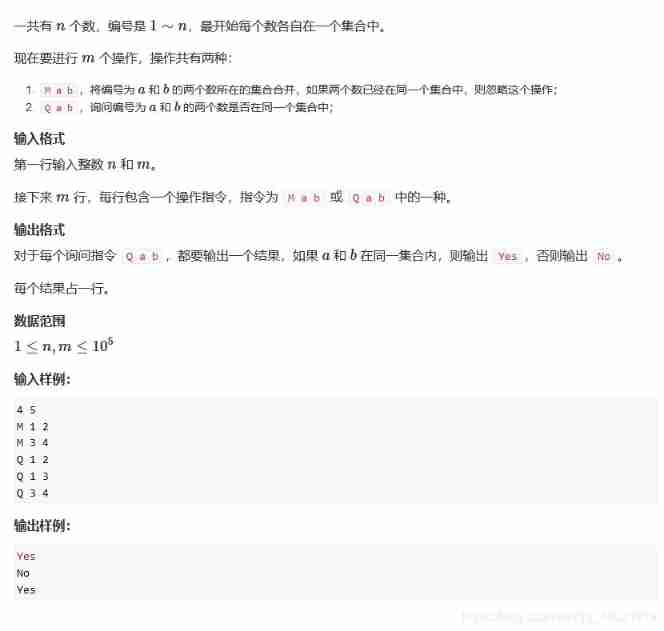
【acwing】836. Merge sets
UE4/UE5 虚幻引擎,材质篇(三),不同距离的材质优化
![[groovy] closure closure (customize closure parameters | customize a single closure parameter | customize multiple closure parameters | specify the default value of closure parameters)](/img/92/937122b059b6f3a91ae0e0858685e7.jpg)
[groovy] closure closure (customize closure parameters | customize a single closure parameter | customize multiple closure parameters | specify the default value of closure parameters)

Redis 排查大 key 的4种方法,优化必备
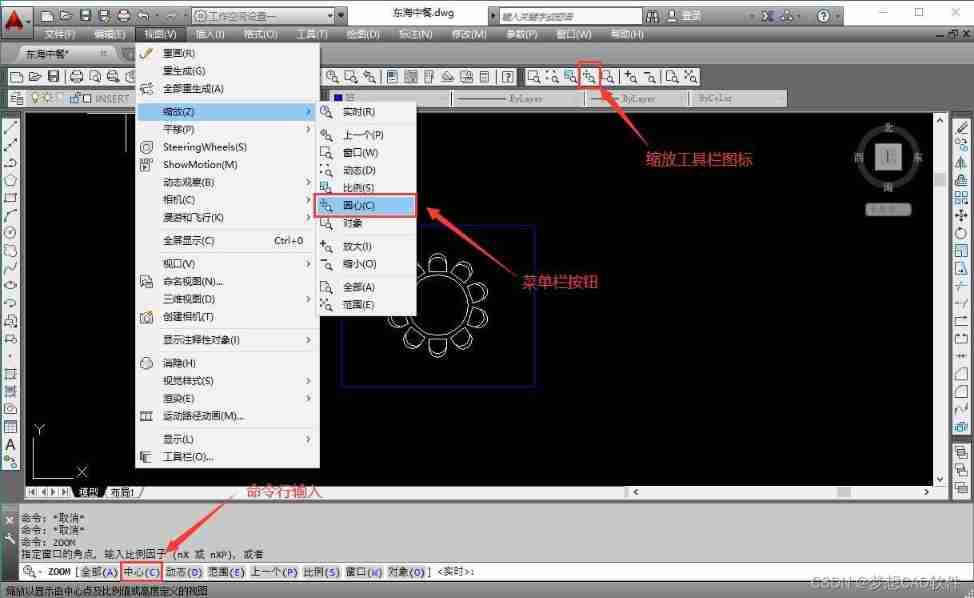
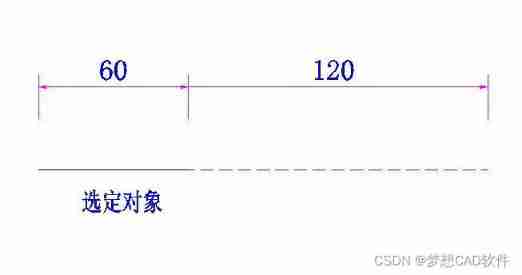
AutoCAD - Center zoom
随机推荐
中国金刚烷行业研究与投资预测报告(2022版)
Common database statements in unity
Lua determines whether the current time is the time of the day
Unity check whether the two objects have obstacles by ray
54. 螺旋矩阵 & 59. 螺旋矩阵 II ●●
stm32Cubemx(8):RTC和RTC唤醒中断
2021 higher education social cup mathematical modeling national tournament ABCD questions - problem solving ideas - Mathematical Modeling
[Chongqing Guangdong education] National Open University 2047t commercial bank operation and management reference test in autumn 2018
2020-10-27
Unity synergy
猿人学第一题
2022 thinking of mathematical modeling D problem of American college students / analysis of 2022 American competition D problem
用 Jmeter 工具做个小型压力测试
Listview pull-down loading function
China needle coke industry development research and investment value report (2022 Edition)
Unity find the coordinates of a point on the circle
669. 修剪二叉搜索树 ●●
How to choose a panoramic camera that suits you?
[groovy] closure (closure call is associated with call method | call () method is defined in interface | call () method is defined in class | code example)
Introduce Hamming distance and calculation examples